On Day 23 of Cybersecurity Awareness Month, learn how to get a list of Entra ID applications with expiring client secrets and certificates effectively. Stay tuned for more blogs in our M365 Cybersecurity Blog Series.
In Microsoft 365 organizations, various applications, including third-party apps, are integrated and used for completing various tasks, projects, etc. Developers also have the option to register their own applications in Entra ID for organizational use. These applications use app client secrets and certificates to authenticate their identity when requesting a token. However, for all registered applications, these client secrets and certificates will expire after a certain period. So, it is essential for admins to identify applications with expiring client secrets & certificates and take actions accordingly for efficient and seamless usage of applications in M365.
Let’s explore how to get all Azure applications with expiring client secrets and certificates in Microsoft 365.
How to Get All Entra ID Applications with Expiring Client Secrets & Certificates?
To find out the expiry details of client secrets and certificates for an application, admins can use either the Microsoft Entra Admin Center or Microsoft Graph PowerShell.
- Find expiration date of app client secrets and certificates using Entra admin center
- Export app registrations with expiring client secrets and certificates using PowerShell
Note: Admins can also implement secure score recommendations to secure third-party apps.
Find Expiration Date of App Client Secrets and Certificates Using Entra Admin Center
- Navigate to the Microsoft Entra Admin Center.
- Go to Applications –> App registrations –> All applications tab.
- Select a specific application for which you want to find out the expiry details.
- Select ‘Certificates & Secrets’.
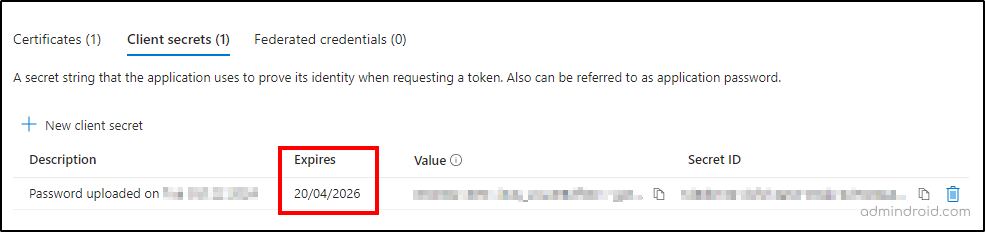
- In the ‘Client secrets’ tab, you will find the expiry date of the app’s client secret as shown below.
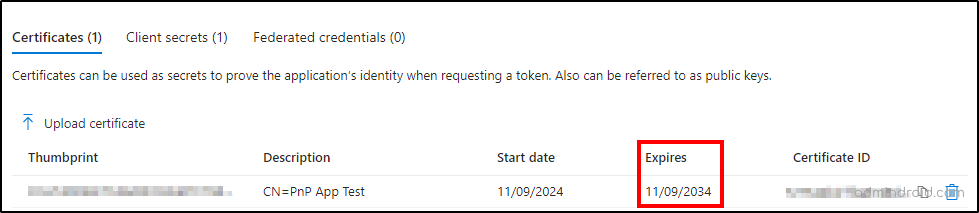
- Click on ‘Certificates’ tab to find the expiry date of the app certificate as shown below.
Note: To avoid app security risks, admins can manage user consents and remove unused credentials.
Export App Registrations with Expiring Client Secrets and Certificates Using PowerShell
In the Entra admin center, obtaining expiry details for client secrets and certificates might be challenging as you must navigate to each application individually. To efficiently identify the expiration details, you can go with the Microsoft Graph PowerShell method. For achieving this, we have developed a script to solve different use cases and minimize your hurdle!
Download Script: AppRegistrationsWithExpiringCertAndSecrets.ps1
Let’s see the use cases that this PowerShell script solve effectively in detail.
- Get all Azure AD apps with expiring client secrets and certificates
- Retrieve all Entra ID apps with expiring client secrets
- Find a list of all Azure AD apps with expiring certificates
- Retrieve a list of all Azure AD apps with certificates and secrets expiring in 30 days
1. Get All Azure AD Apps with Expiring Client Secrets and Certificates
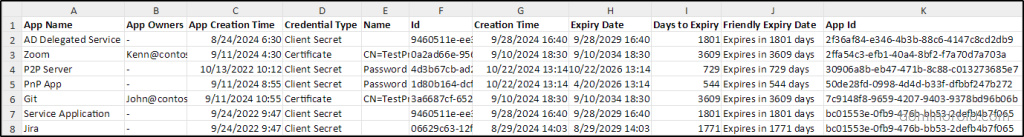
Verifying the expiry date of client secrets and certificates for all the applications helps to take actions for seamless app usage. Running this script will export all the applications in Entra ID with expiry details of their client secrets and certificates.
|
1 |
.\AppRegistrationsWithExpiringCertAndSecrets.ps1 |
This report will contain the list of all apps with expiring certificates and client secrets along with app name, owner, creation time, etc., as shown below.
2. Retrieve All Entra ID Apps with Expiring Client Secrets
Some of the app registrations contain only client secrets. In such cases, if you want to retrieve apps with client secret expiration details alone, run the script with the ‘-ClientSecretsOnly’ parameter as below.
|
1 |
.\AppRegistrationsWithExpiringCertAndSecrets.ps1 -ClientSecretsOnly |
The above cmdlet exports the apps with their client secret expiry details in your Entra ID environment.
Handy Tip: You can use Microsoft Entra application management policies to manage client secrets. This allows you to set the expiry lifetime for client secrets, either tenant-wide or individually at the time of creation.
3. Find a List of All Azure AD Apps with Expiring Certificates
If you want to find out only the expiration details of the app certificates, you can run the script with the ‘-CertificatesOnly’ parameter as shown below.
|
1 |
.\AppRegistrationsWithExpiringCertandSecrets -CertificatesOnly |
This shows the list of Entra ID apps with their certificate expiration details.
4. Retrieve a List of All Azure AD Apps with Certificates and Secrets Expiring in 30 Days
To get a more granular report like apps with certificates and secrets expiring in n days (i.e., 30, 90, etc.), you can run the script as below.
|
1 |
.\AppRegistrationsWithExpiringCertAndSecrets -SoonToExpireInDays “30” |
The above cmdlet retrieves a list of all applications with certificates and secrets expiring in 30 days.
You can also use the parameter ‘SoonToExpireInDays’ with ‘-ClientSecretsOnly’ or ‘-CertificatesOnly’ parameter to get detailed reports like apps with client secrets expiring in n days or apps with certificates expiring in n days.
Handy Tip: To reduce your workload, we’ve created a PowerShell script to automate app credential expiry notifications for credentials expiring in n days. It sends an email to admins with details like the app name, credential type and name, creation date, expiry date, and days remaining.
I hope this blog helps with the PS script to retrieve the Entra ID applications with their certificates and secrets expiry details efficiently. Utilize this script to avoid downtime and secure your M365 applications. For more queries, feel free to reach us through the comment section. Happy scripting!