📢 Heads up! Now MS Graph has the ability to retrieve legacy per-user MFA status.
Here’s the inside story on our find
With MSOnline & Azure AD PowerShell modules on their way out, we’re migrating AdminDroid’s Microsoft 365 reporting tool to MS Graph. As part of this migration process, we are maintaining close communication with MS support and keeping a vigilant eye on the Microsoft Graph changelog. As a result, our development team discovered a significant update: Microsoft Graph now supports retrieving legacy per-user MFA status.
This noteworthy enhancement is one we’re eager to highlight for our readers. To complement our existing script for exporting MFA status using MSOnline, we’ve developed a new script that uses MS Graph PowerShell to export per-user MFA status.
Note: Retrieving per-user MFA status is currently only available through the beta endpoint
⬇️Download Script: CheckMFAStatus.ps1
Script Highlights:
- Generates 5+ MFA status reports.
- Helps to filter and find MFA enabled users.
- Identifies MFA disabled users.
- Helps to track MFA enforced users.
- Exports MFA status report for licensed users alone.
- Checks MFA status for sign-in allowed users alone.
- Helps to generate more granular MFA reports by combining multiple filtering params.
- The script uses MS Graph PowerShell and installs MS Graph Beta PowerShell SDK (if not installed already) upon your confirmation.
- The script can be executed with an MFA enabled account too.
- Exports report results as a CSV file.
- The script is scheduler friendly.
- It can be executed with certificate-based authentication (CBA) too.
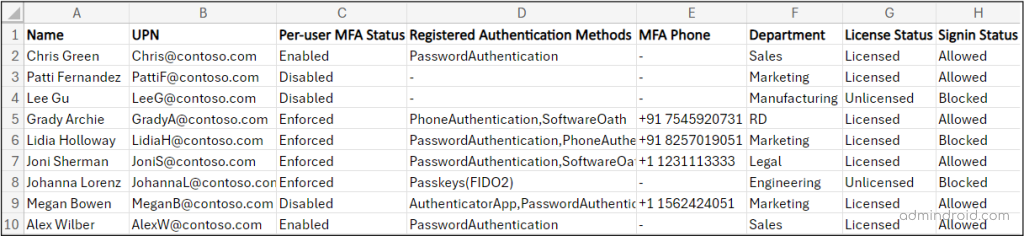
Per-user MFA Status Report – Sample Output:
The exported MFA status report contains the following properties: Display Name, UPN, Per-user MFA Status, Department, License Status, Sign-in Status, Registered Authentication Methods, MFA Phone, Microsoft Authenticator Configured Device, Usage of 3rd-party Authenticator App.
How to Export MFA Status Report for Azure AD (Entra) Users?
After downloading the PowerShell script, run the script using one of the following methods based on your requirement.
Method 1: Get MFA status report using interactive logins.
You can choose this method for both MFA and non-MFA accounts.
|
1 |
.\CheckMFAStatus.ps1 |
The script will export all Entra ID users and their per-user MFA status along with the most required properties.
Method 2: Run or schedule MFA report using certificate-based authentication.
To run the script unattended or with Certificate-Based Authentication (CBA), you can use this method:
|
1 |
.\CheckMFAStatus.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <CertThumbprint> |
Before executing the script, you must register an application in Entra ID. You can use either a CA-signed certificate or create a self-signed certificate.
Get Per-user MFA Status Reports Using Microsoft Graph PowerShell
As previously mentioned, the script supports multiple built-in filtering parameters to generate more granular MFA reports for Azure AD (Entra) accounts.
1. Export MFA Enabled Users Report:
To export MFA enabled users report to CSV file, run the script with ‘MFAEnabledUsersOnly’ switch param.
|
1 |
.\CheckMFAStatus.ps1 -MFAEnabledUsersOnly |
After exporting the report, review the users’ registered MFA authentication methods to determine if they are secure enough to combat MFA attacks. If you identify any less secure authentication methods, such as Phone Number, you can reset MFA for the specific user.
2. Find Users Without MFA:
To find users who do not have MFA enabled, use the ‘MFADisabledUsersOnly‘ switch parameter:
|
1 |
.\CheckMFAStatus.ps1 -MFADisabledUsersOnly |
3. Identify MFA Enforced Users:
To get a report of users with enforced MFA, execute the script with the ‘MFAEnforcedUsersOnly‘ switch parameter:
|
1 |
.\CheckMFAStatus.ps1 -MFAEnforcedUsersOnly |
4. Get MFA Status Report for Licensed Users:
To check the MFA status for licensed users and exclude unlicensed users, run the script with the ‘LicensedUsersOnly‘ switch parameter:
|
1 |
.\CheckMFAStatus.ps1 -LicensedUsersOnly |
5. Check MFA Status Report for Sign-in Enabled Users:
As part of the Microsoft 365 offboarding process, former employee accounts are often disabled. To exclude these accounts and check the MFA status for active users, use the ‘SigninAllowedUsersOnly‘ parameter:
|
1 |
.\CheckMFAStatus.ps1 -SigninAllowedUsersOnly |
6. Export More Granular MFA Reports:
You can combine multiple parameters to generate and export fine-grained MFA reports. For example:
|
1 |
.\CheckMFAStatus.ps1 -MFADisabledUsersOnly -SigninAllowedUsersOnly |
The above format helps identify sign-in-allowed users who do not have MFA enabled. These users pose a significant security risk. With this report, you can take steps to configure MFA for those users. for those users.
💡Tip: MS recommends transitioning from per-user MFA to Conditional Access MFA to enhance security for sensitive resources and to free up less critical ones.
Closing lines:
The ability to retrieve per-user MFA status through MS Graph is a significant and welcome addition. We hope this script makes it easier for you to get the MFA status report and streamline your Microsoft 365 security management.