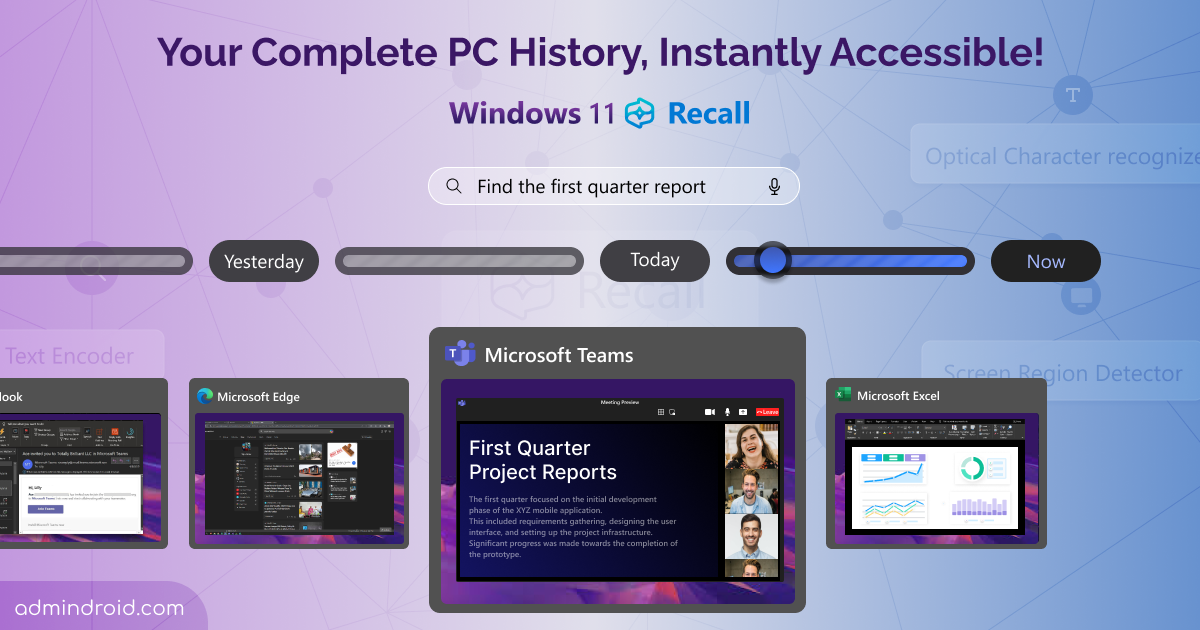
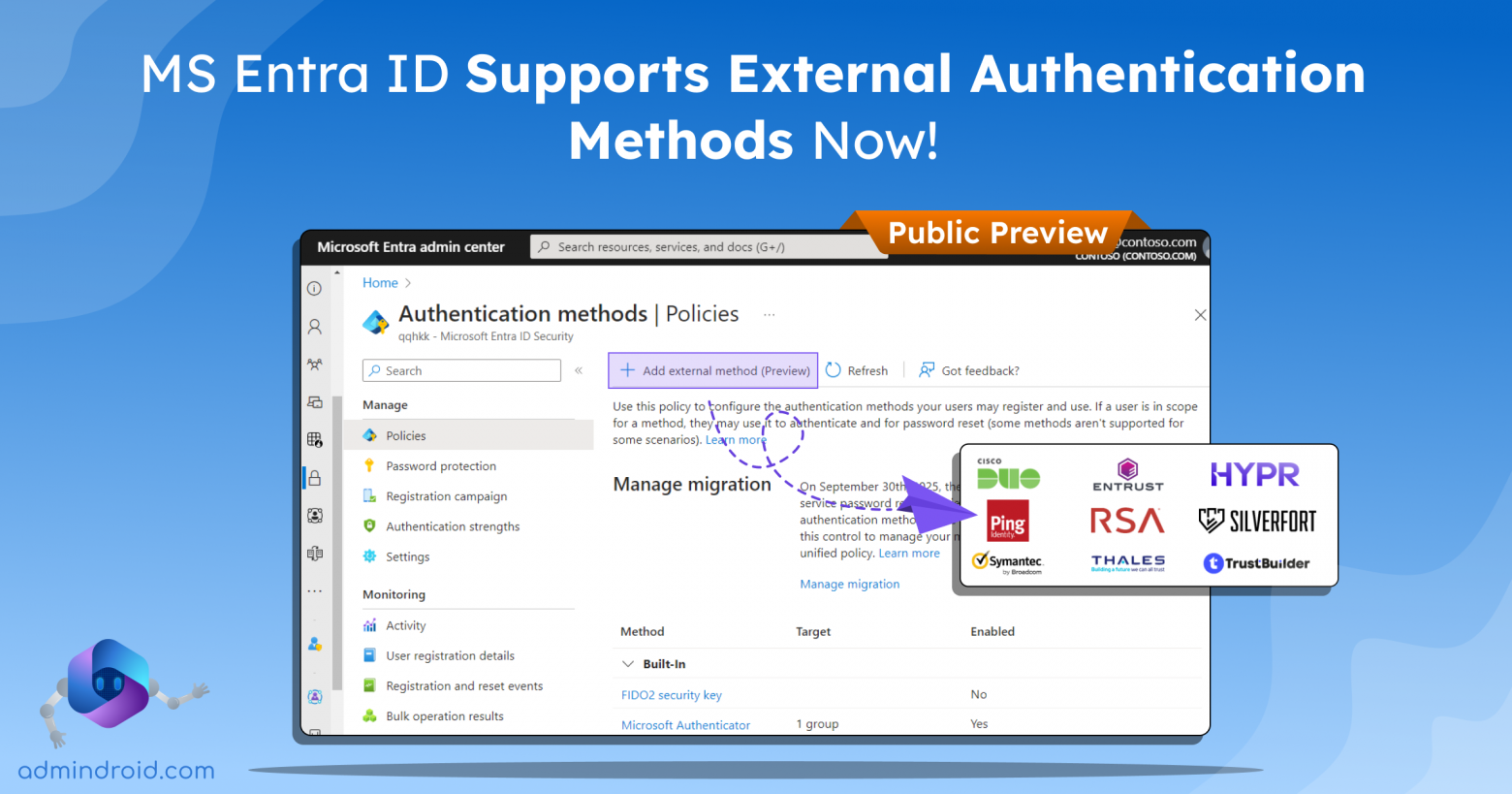
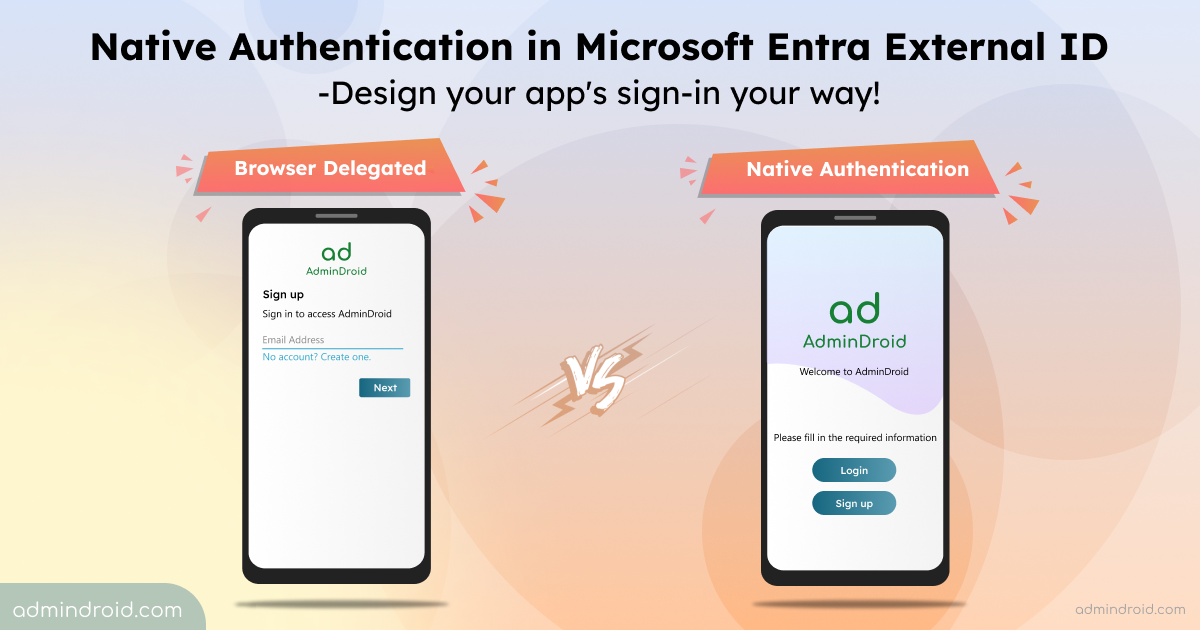
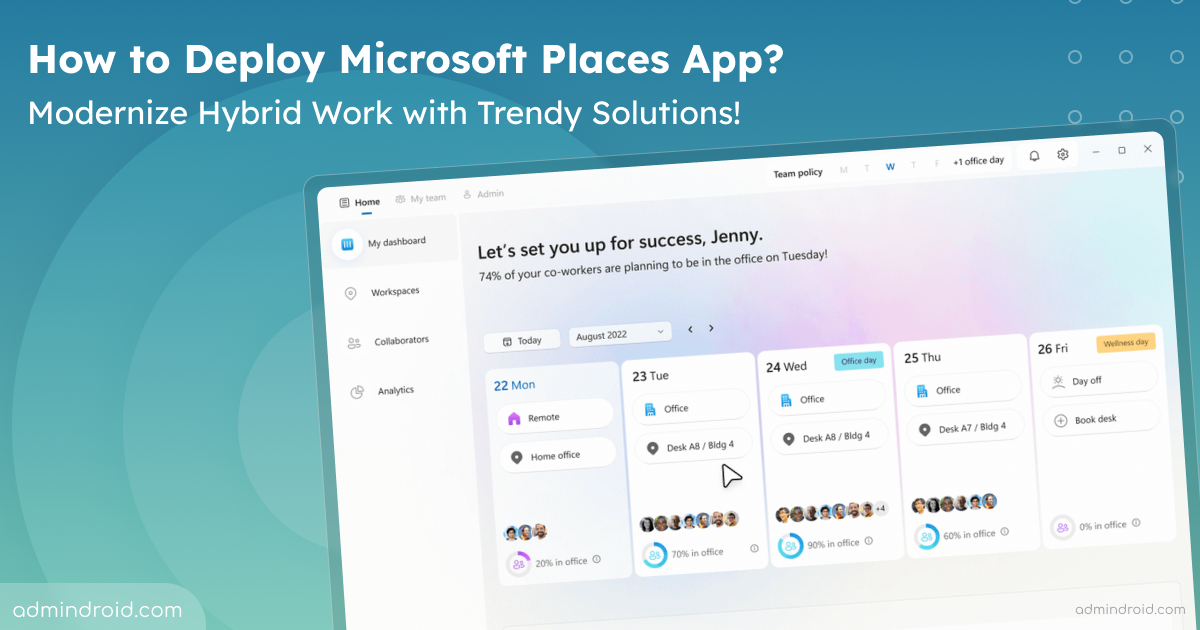
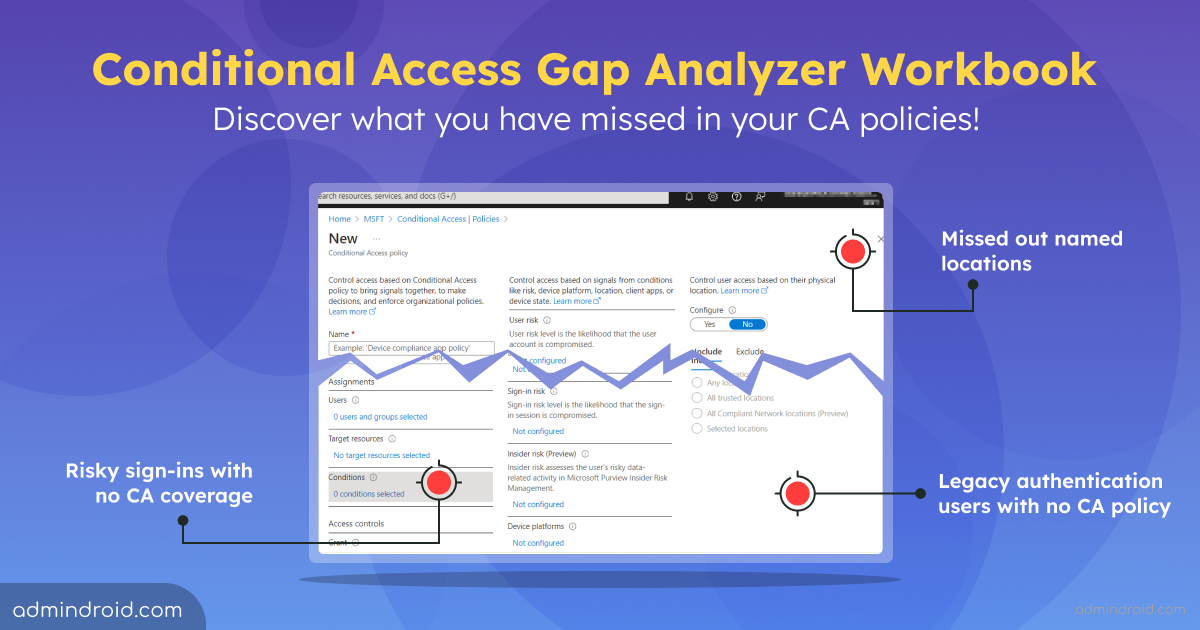
As cyber threats rapidly increase, monitoring every aspect of your Microsoft 365 environment is crucial. While securing an organization, preventing unwanted access to resources is a prominent concern as we identify suspicious actions. The real challenge arises when users still retain access to sensitive resources even after completing their tasks. It’s essential to revoke this…