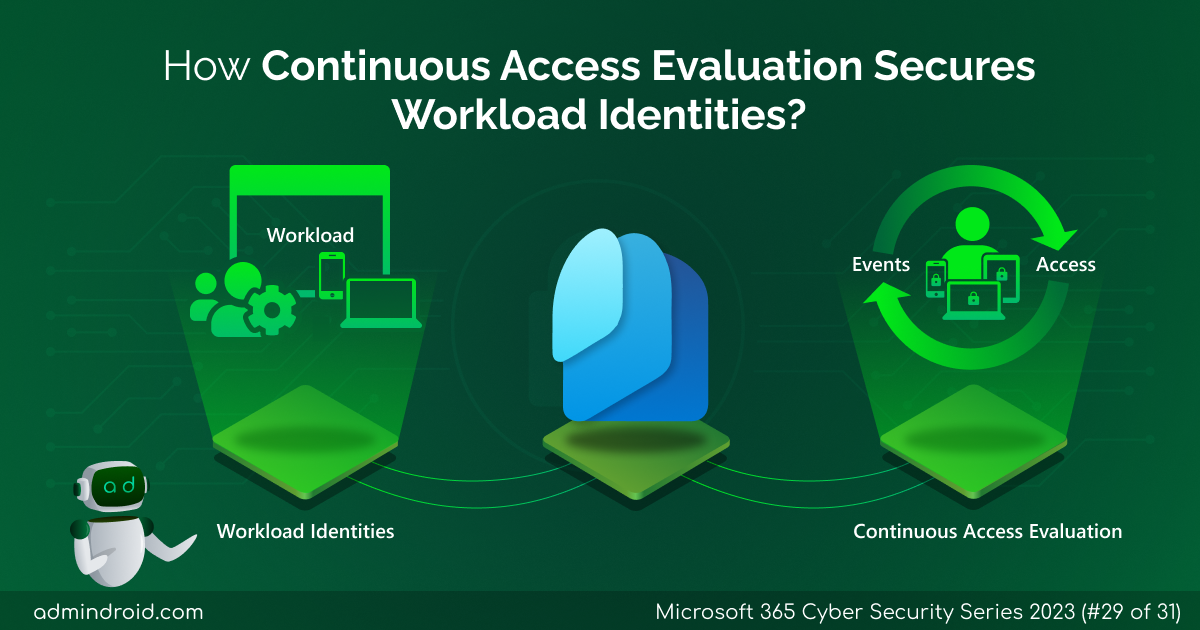
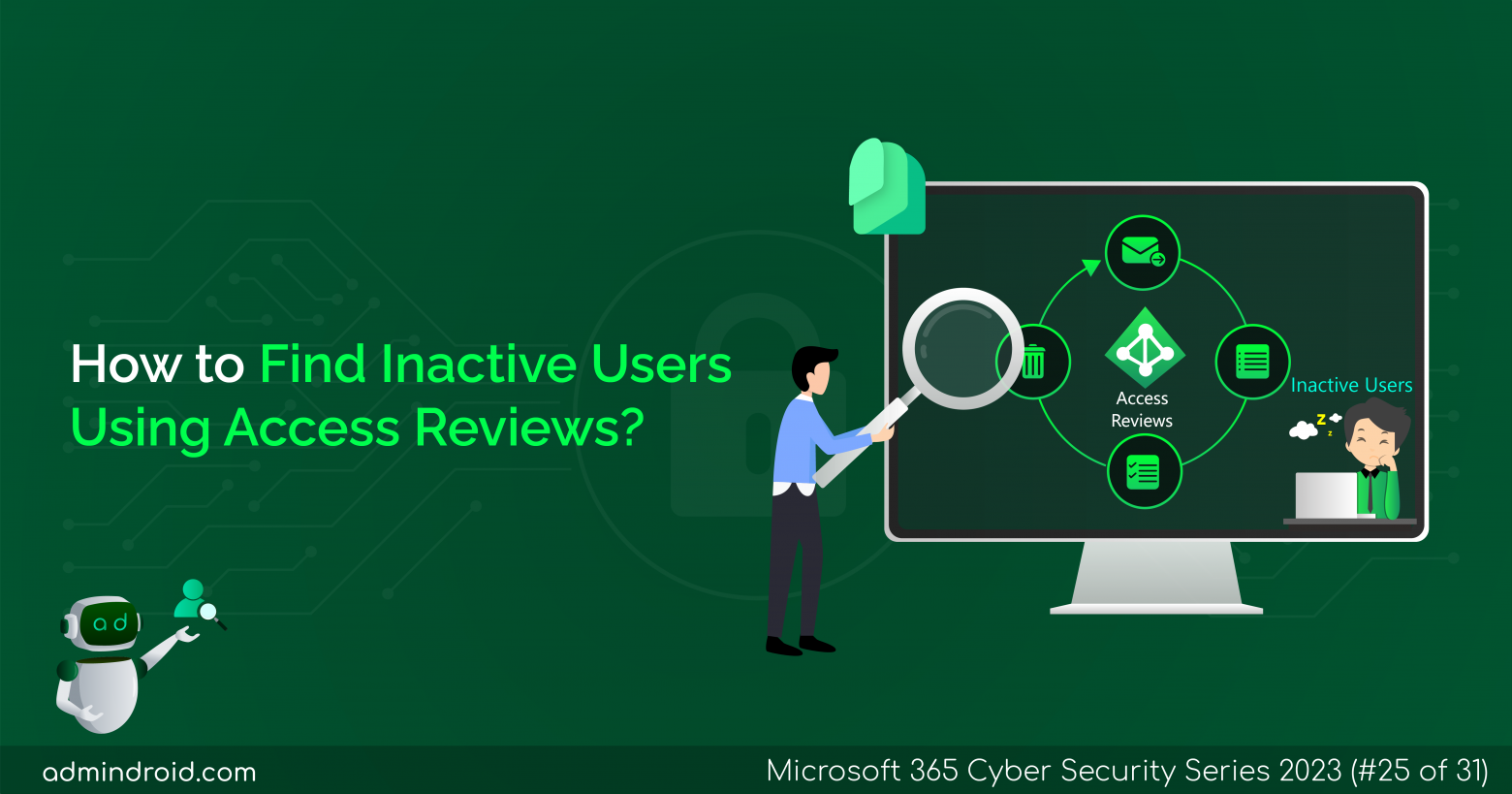
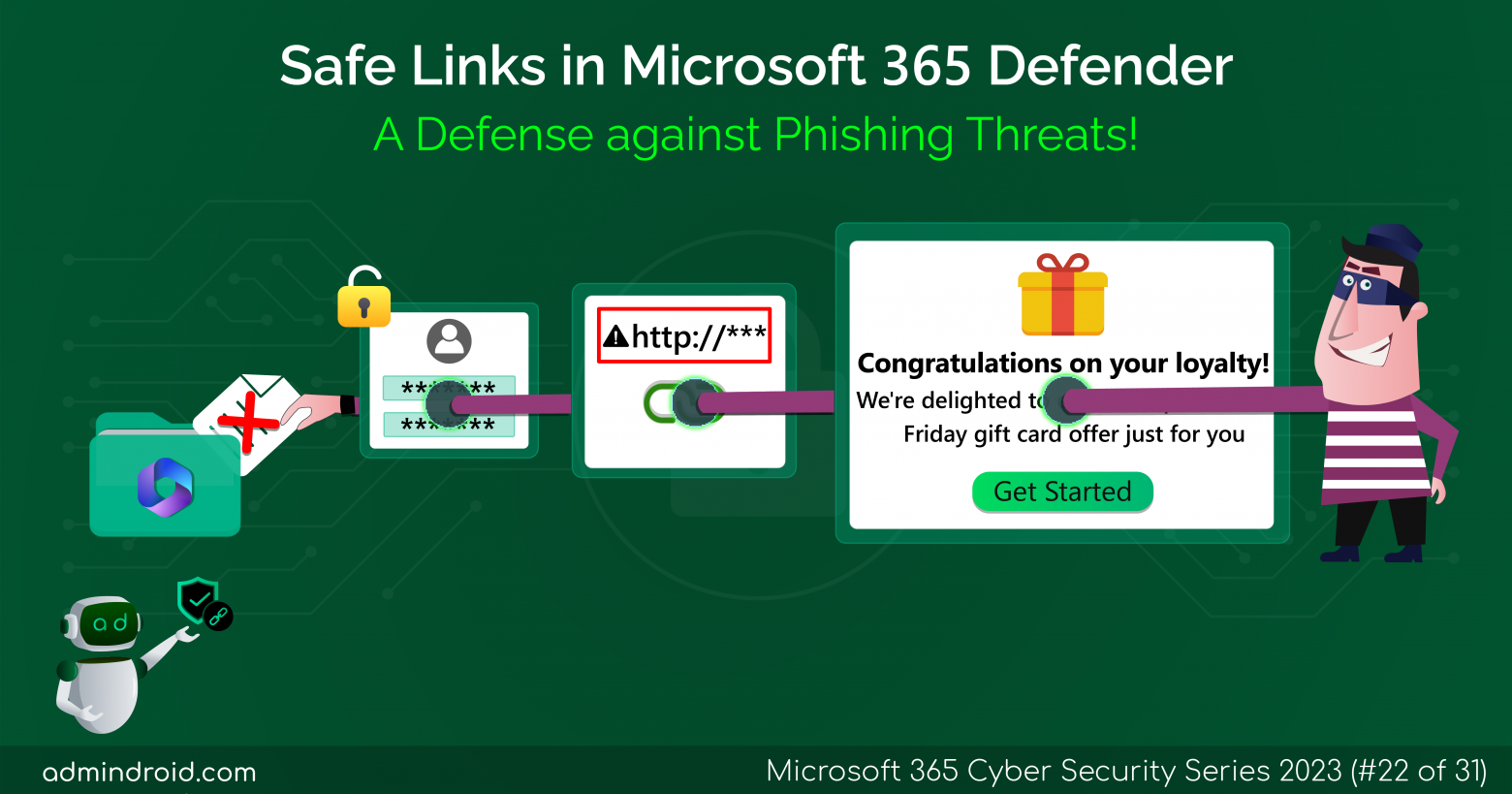
On Day 31 of Cybersecurity Awareness Month, learn how to configure teams with highly sensitive protection, allowing you to grow your external collaborations without worrying about security. Dive into our captivating M365 Cybersecurity blog series, packed with valuable tips to keep your organization secure! In today’s world of remote work, many of us rely on…