On Day 22 of Cybersecurity Awareness Month, let’s learn how Safe Links in Microsoft 365 Defender safeguards your users from malicious links in emails, Microsoft Teams, and other Office 365 applications. Stay tuned for additional informative blogs in our M365 Cybersecurity blog series.
In the digital realm of Microsoft 365, a world full of business secrets and uncertainties, there’s a sneaky trick that draws people into a risky trap. Gift vouchers and enticing prizes may seem appealing with promises of rewards, but what we often fail to realize is the lurking danger beneath these attractive offers.
Imagine this scenario: Your Microsoft 365 users receive meticulously crafted emails enticing them with fake login pages or deceptive business offers. It’s an unsuspecting pull that grabs their focus. In that split second, most will click the link, unknowingly risking your organization’s resources.
However, it’s not always feasible to prevent each user from clicking malicious links. This is where the Safe Links in Microsoft 365 Defender comes into play. Microsoft 365 Defender’s Safe Links is a pivotal feature to proactively address cybersecurity threats tied to malicious links. Let’s delve into this blog to learn how Safe Links policies can enhance your organization’s digital security.
Safe Links in Microsoft 365 Defender
Safe Links in Microsoft Defender for Office 365 is a robust feature designed to safeguard your environment against malicious links commonly found in phishing and other cyberattacks. Safe Links offers comprehensive URL scanning, and as part of its functionality, it rewrites the URL of inbound email messages during mail flow. It also performs real-time verification of URLs and links when users click on them. It’s worth noting that Safe Links operates alongside the existing anti-spam and anti-malware protections.
Safe Links Protection is available across various key areas, including:
- Safe Links protection for email messages
- Safe Links protection for Microsoft Teams
- Safe Links protection for Office apps
These different dimensions of Safe Links ensure that your organization enjoys enhanced security across various communication channels.
1. Safe Links Protection for Email Messages
Microsoft 365 Defender’s Safe Links significantly boosts email security, guarding against spam, malware, and phishing threats. In the realm of cybersecurity, attackers often send deceptive emails with seemingly trustworthy URLs, even impersonating reputable sites like Microsoft. But here’s where Microsoft’s Safe Links steps in: it scans all incoming message URLs, irrespective of whether rewritten or not, and even checks unwrapped ones in supported Outlook versions (Windows, Mac, and Outlook on the web) when clicked.
However, scanned URLs are rewritten with the standard Microsoft URL prefix (https://nam01.safelinks.protection.com) and undergo thorough threat analysis.
- Once rewritten, the change persists even when messages are manually forwarded or replied to, regardless of internal or external recipients. Additional links in forwarded or replied messages remain unchanged.
- In cases of automatic forwarding through Inbox rules or SMTP forwarding, the URL is not rewritten for the recipient, unless it has been previously rewritten, or the recipient is protected by Safe Links.
Considering the evolving cyber threats and business email compromise (BEC) attacks, Microsoft advises enabling Safe Links protection for email messages when setting up custom Safe Links policies in Microsoft 365 Defender. Creating Safe Links policies is crucial not only to defend against these threats but also to increase your Microsoft Secure Score. In fact, Microsoft makes these settings the default when creating custom Safe Links policies in Microsoft 365 Defender.
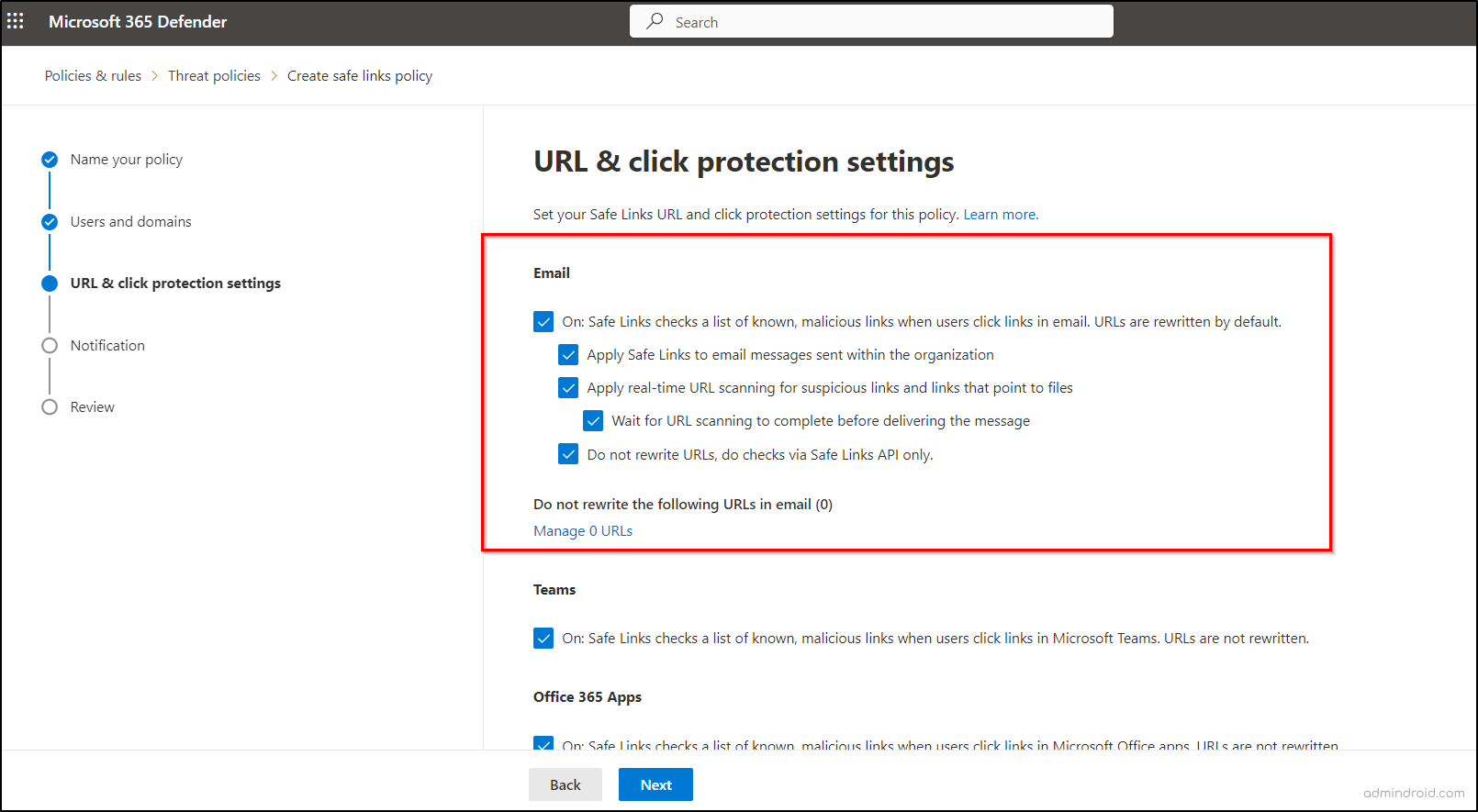
Initially, turn on the “On: Safe Links checks a list of known, malicious links when users click links in email. URLs are rewritten by default” option in Safe Links policies for email protection. Then, proceed with the desired configurations which are discussed below.
- In an organization where both Jess and Tasha work and are subject to Safe Links policies, safeguarding Tasha’s security is crucial, especially if Jess inadvertently sends an email containing a malicious URL. Thus, Microsoft recommends enabling the “Apply Safe Links to email messages within the organization” setting to ensure internal communication safety, thereby protecting it from both external and internal threats.
- Nowadays, cyber threat actors have adapted their tactics to evade email scanning and protection measures. They now employ URLs that trigger potentially harmful content downloads, challenging traditional security methods. Therefore, Microsoft offers the “Apply real-time URL scanning for suspicious links and file-pointing links” setting in Safe Links policies to enhance protection.
- Despite robust Safe Links policies, there are instances where the scanning process is interrupted. To prevent harmful links from entering your organization due to interrupted scanning, Microsoft recommends enabling the ‘Wait for URL scanning to complete before delivering the message’ setting, which operates as a subset of the ‘Apply real-time URL scanning’ feature.”
- In situations where you need to disable email rewriting but maintain protection, Microsoft provides the “Do not rewrite URLs, do checks via Safe Links API only” option. This bypasses URL wrapping, and the reputation check in the mail flow, using Safe Links exclusively through APIs when a URL is clicked by supported Outlook clients.
- This setting is the default in new Safe Link policies created in Microsoft 365 Defender. However, in Exchange Online PowerShell, it’s not the default (the ‘DisableURLRewrite’ parameter is set to false).
- For known secure URLs that shouldn’t be disrupted, there’s an option in Safe Links policies called “Do not rewrite the following URLs in email.” This is particularly useful for organizations using on-premises Skype for Business or SharePoint, allowing exclusion of these links from scanning and rewriting.
2. Safe Links Protection for Microsoft Teams
In the wake of the increased use of Microsoft Teams following the pandemic, the situation involving Midnight Blizzard’s social engineering attacks within Microsoft Teams is noteworthy. Hackers are taking advantage of this trend by attempting to impersonate guest users or trusted entities within Teams, deceiving users, and sharing malicious URLs in chats, group conversations, or channels. In response to these evolving threats, Microsoft has introduced Safe Link policies for Microsoft Teams.
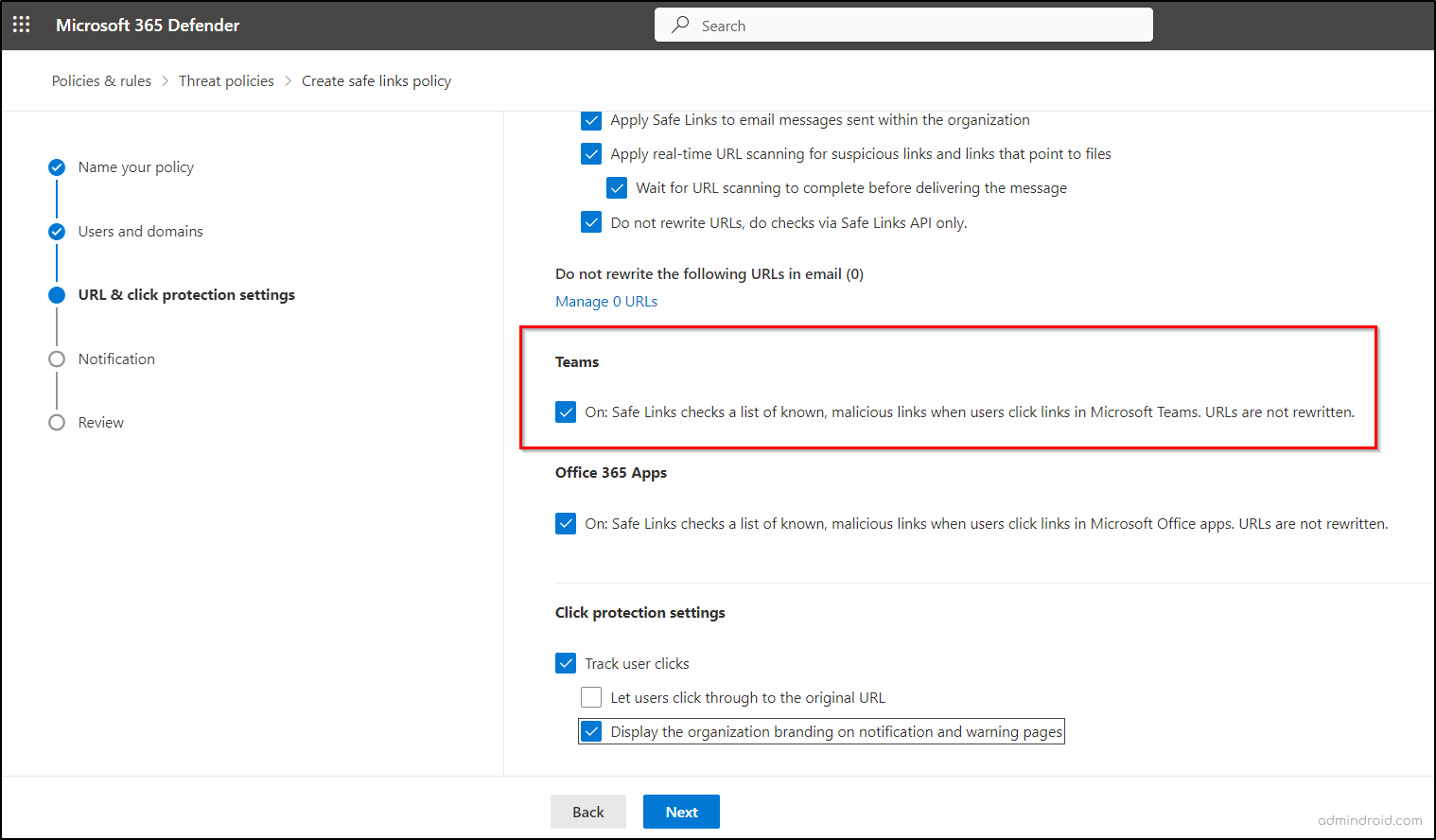
Enable the “On: Safe Links checks a list of known, malicious links when users click links in Microsoft Teams. URLs are not rewritten” setting under the Teams section in Safe Link policies for MS Teams protection. This feature applies to both desktop and web versions of Teams.
NOTE: Please be aware that changes may take up to 24 hours to become fully effective, ensuring a seamless transition to enhanced security.
To grasp the functionality of Safe Links protection for Microsoft Teams and how it secures your organization, let’s explore these scenarios:
- Consider a case where a project manager might have pinned tabs to SharePoint sites in Teams for easy access to project information. If a team member shares a malicious link, Safe Links in Teams blocks access within the tab and displays a warning, ensuring your project’s security and efficient collaboration. This feature also disables opening the link in a web browser from a pinned tab for added security, safeguarding your project’s tabs in Teams.
- As a popular collaboration platform, Teams is frequently employed for coordinating and conversing about training sessions and webinars. Safe Links guarantees the security of links shared for event registration or access, reducing the chances of participants ending up on malicious websites. This, in turn, safeguards your organization’s assets and reputation while promoting reliable communication.
- In Microsoft Teams chats, when an employee shares links to industry news articles or reports, the act of inadvertently sharing a malicious link can be concerning for your organization’s security. However, with Safe Links, real-time URL verification is in action. If a link is identified as malicious, Safe Links instantly displays a warning page in the web browser, ensuring that potential threats are promptly addressed.
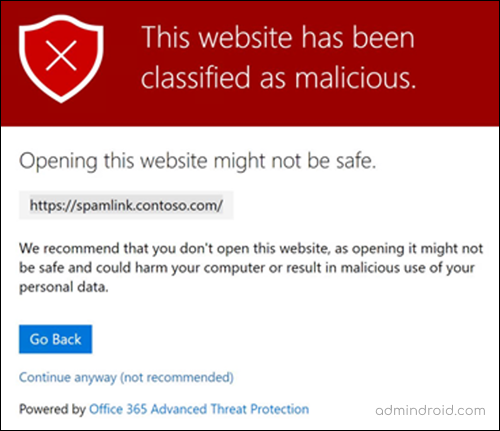
NOTE: The user’s access to the original URL depends on the “Let users click through to the original URL” setting in the Safe Links policy under ‘Click Protection Settings.’ It’s recommended not to allow bypassing the warning for enhanced security. In addition, if the Safe Links policy is enabled for Teams protection, and the user who sent the link is not covered by this policy, the user is allowed to click through to the original URL on their device.
3. Safe Links Protection for Office Apps
Safe Links protection in Office apps enhances security for URLs within Office documents, offering real-time verification for apps like Word, Excel, PowerPoint, Visio, etc., and scans links within attached Office documents in email messages for comprehensive protection
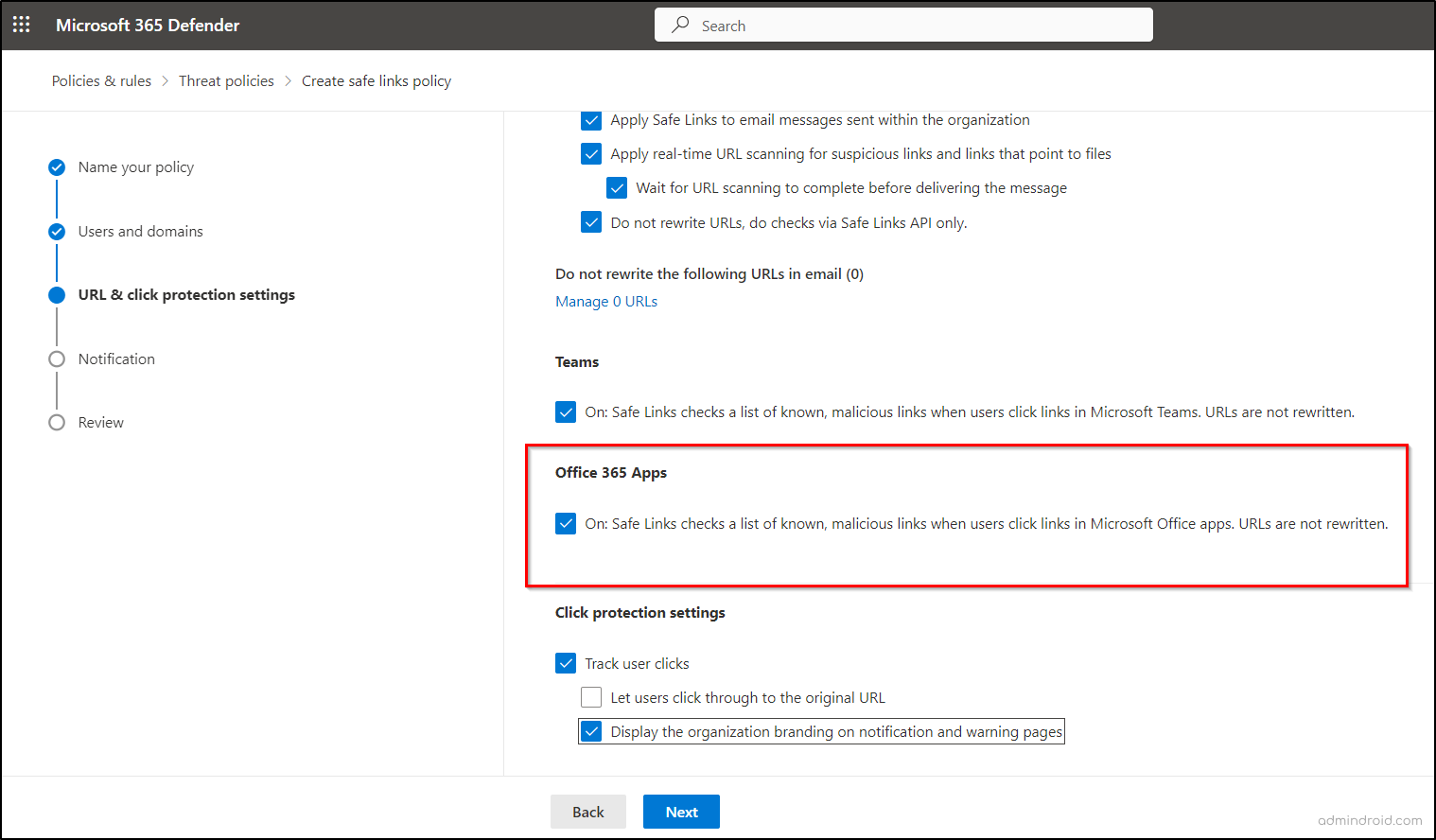
To enable Safe Links policies for Office apps, turn on the “On: Safe Links checks a list of known, malicious links when users click links in Microsoft Office apps. URLs are not rewritten” setting within the Office 365 apps section of Safe Link policies. This enhanced security feature requires:
- Microsoft 365 Apps or Microsoft 365 Business Premium, covering current versions of Word, Excel, and PowerPoint on Windows, Mac, or in a web browser.
- Office apps on iOS or Android devices.
- Visio on Windows.
- OneNote in a web browser.
- Outlook for Windows when opening saved EML or MSG files.
- Configure modern authentication for compatible Office apps & Microsoft 365 services and require users to sign in with work or school accounts.
Discover how Safe Links for Office apps enhances your Microsoft 365 security through these real-world examples:
- When a marketing team collaborates on a PowerPoint presentation for an upcoming product launch, Safe Links diligently scans external website links for compromise. If any linked site becomes malicious, access is promptly blocked for all collaborators, preserving the presentation’s integrity.
- In the finance department’s critical Excel spreadsheet, links to financial data sources are maintained. Safe Links ensures the safety of these financial website links. If any source is compromised, unauthorized access is prevented, preserving financial data security.
- Imagine a scenario where an organization’s user opens a document shared by an external source, the document may contain potentially malicious URLs leading to downloadable files, all without the user’s awareness. This poses a significant security threat to the organization. Safe Links for Office apps proactively checks the URL and files for security. If any malicious content is found, Safe Links swiftly blocks access, safeguarding the organization’s integrity.
Priority for Safe Links Policies in Microsoft 365 Defender
Enabling Safe Link policies is just the first step; effective management is crucial to maximize security. To manage multiple Safe Links policies, Microsoft offers the flexibility to prioritize custom Safe Link policies for enhanced control. These policies are consistently applied, with the Standard and Strict preset security policies in Exchange Online Protection taking precedence. The built-in protection policy acts as the security foundation. Unique priority levels for each policy are essential for clarity and control.
Limitations of Safe Links in Microsoft 365 Defender
- Safe Links for Email messages is not compatible with mail-enabled public folders and exclusively supports URLs using HTTPS and FTP formats.
- Employing an external service to wrap links before Defender for Office 365 may interfere with Safe Links’ ability to process, wrap, inspect, or determine the security of links, potentially impacting its effectiveness in detecting malicious links.
- Safe Links for Office apps may take a few seconds to verify its availability for a user at the start of each session.
- In Office desktop clients, if the Safe Links scanning process encounters any issues or delays, the protection won’t trigger immediate actions. Instead, it provides users with a warning before they proceed to the destination website, allowing them to make informed decisions about their online safety.
- Custom Safe Link policies follow an inclusive, not additive, approach. This means that for the policy to apply, the recipient must meet all the specified conditions of the recipient filters, rather than having multiple conditions stacked together.
In conclusion, enabling the Microsoft 365 Defender Safe Links policy in your organization is a valuable step to protect your users and strengthen Microsoft 365 security, despite some limitations. Additionally, explore and implement best security practices for email and Microsoft Teams security practices to further enhance your overall environment’s safety.
In the world of cybersecurity, clicking without thinking is like opening a door without checking who’s on the other side.
– Adrien Gendre
Hope this blog has clarified how Safe Links in Microsoft Defender protects your organization. Please share your thoughts and queries in the comments section.






