Cybersecurity threats are increasing in every organization, often due to unintentional user actions. A single employee falling into the trap like clicking a malicious URL, suspicious emails, or a fake login page can open the door to a phishing attack. These threats can strike at any time, from anywhere, leading to major data breaches and compromised accounts. 😥
This happens mainly because many users struggle to recognize phishing attempts, as they are often difficult to detect. 🚫 This is why proactive user education is so important to help users understand what it looks like and avoid such threats. Hence, training users is the first step toward prevention.
What we truly need is smart, targeted training that reflects real-world phishing threats. 🥷That’s exactly what Microsoft Defender’s dynamic attack simulation delivers, ensuring the right users get the right training at the right time.
In this blog, we will explore how to create targeted attack simulation training with dynamic groups using Microsoft Defender for Office 365. This will help you to get started using attack simulation training and train the users effectively.
Targeted Attack Simulation Training with Dynamic Groups
Microsoft Attack Simulation Training in Defender for Office 365 is a phishing risk reduction tool that mimics real-world phishing attacks to help users recognize and respond to such threats effectively.
Once a simulation is launched, users receive emails with malicious links, attachments, or QR codes that closely resembles real phishing emails. These phishing elements are known as payloads in attack simulation training.
Microsoft provides a list of built-in payloads that represent various social engineering techniques, such as:
- Credential Harvest: Fake login pages to capture user credentials
- Malware Attachment: Simulated malicious documents (PDFs, Word files, etc.)
- Link in Attachment: A document containing a phishing link
- Link to Malware: Direct links simulating malware downloads
- Drive by URL: Links that auto-download files when clicked
- OAuth Consent Grant: Fake applications requesting access permissions
To be truly effective, training needs to be tailored to each user, because different roles face different types of risks. For example, finance team might see invoice scams, HR could receive fake resumes, and new employees lack awareness of phishing attempts.
That’s why a single attack simulation isn’t enough! Admins need to design multiple simulations that focus on different categories tailored to different user roles, departments, hire dates, and more. But managing all this manually and simulating attack training is something none of us can think of! This is where dynamic user groups in Entra ID comes to effect.
What are Dynamic Groups in Microsoft 365?
Instead of manually managing group membership, dynamic groups in Entra ID allow you to automate the process. By defining rules based on user attributes like role, department, hire date, location, and more – the right users are added automatically.
For example, if you’re running a phishing simulation for new hires, you can create a dynamic group using the “employee hire date” attribute. As new employees join, they’re automatically added to the group.
By integrating dynamic groups into your attack simulation training, you enable more efficient and effective way to manage target users for simulations and trainings, without manual group membership management.
Points to Remember:
- A dynamic rule runs continuously until the group is deleted.
- If you need to update membership, just modify the dynamic group rules instead of deleting the group.
- When a dynamic rule is updated, group membership is automatically re-evaluated. Users who no longer match are removed, and new matching users are added.
- Dynamic groups in M365 can be created for either users or devices, but both cannot be combined in the same group.
Prerequisites to Create Attack Simulation Training with Dynamic Groups
Before initiating an attack simulation training with Microsoft, ensure the following prerequisites are in place:
Roles and Permissions: (At least one of the following roles is required)
- Global Administrator – Required for high-level configuration access.
- Security Administrator – Manages security settings and insights.
- Attack Simulation Administrator – Responsible for creating and managing all aspects of attack simulation campaigns.
Licensing Requirement: (Mandatory)
- Microsoft Defender for Office 365 Plan 2 – Included with subscriptions like Microsoft 365 E5 or available as an add-on license.
How to Run Targeted Attack Simulation Training with Dynamic Groups
Below are the steps to implement Microsoft 365 attack simulation training with dynamic groups:
- Create a dynamic membership user group in Microsoft Entra admin center
- How to use dynamic groups in attack simulation training
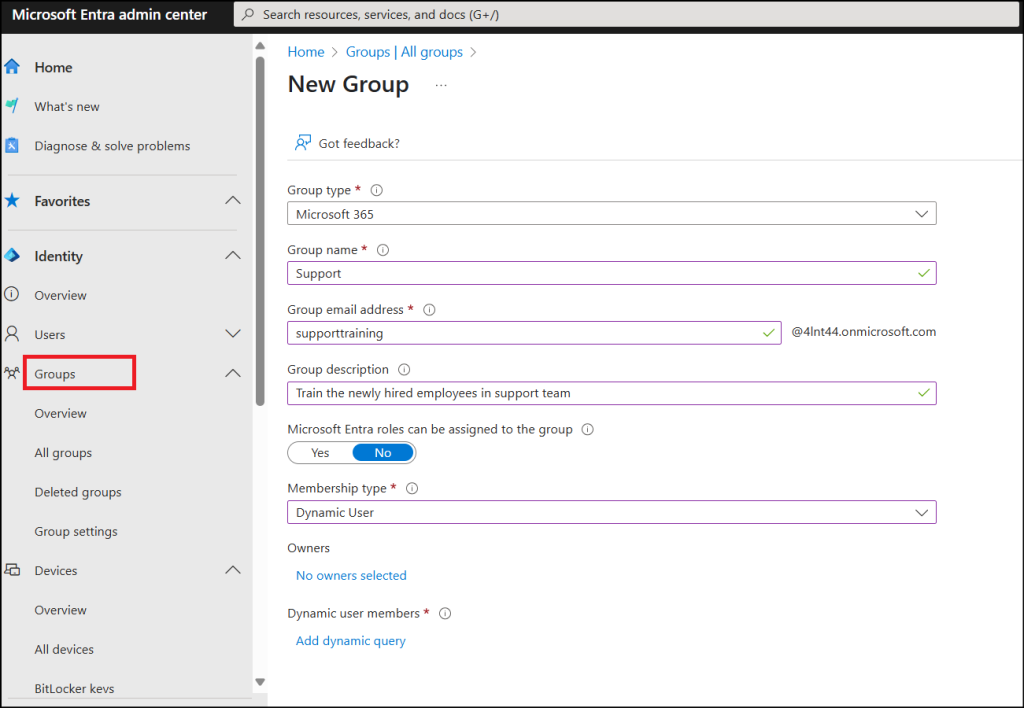
1. Create a Dynamic Membership User in Microsoft Entra admin center
Follow these steps to create a dynamic membership group. In this example, I’m planning to train newly hired users on phishing attack simulations based on their joining date. Let’s walk through how to create a dynamic group for these new hires and set up targeted phishing simulations for them. You can modify the rule based on your specific requirements.
- Sign in to Microsoft Entra admin center.
- Navigate to Groups >> All groups >> New group.
- Select the Group type as ‘Microsoft 365’ to assign training for the target dynamic group.
Note: Dynamic groups are supported only for Microsoft 365 Groups in attack simulation training, not for security groups.
- Provide a Group name and a unique Group email address to the group. Add a Group description to identify its purpose.
- Choose the Membership type as ‘Dynamic User’.
1.1 Create Dynamic Rule for Dynamic Membership Group
After setting the group type and membership type, you need to define rules that will automatically include users based on specific attributes. In this example, we set rules for users who have already been hired as well as those who will be hired in the future.
- In the New Group tab, assign one or more Owners and click Add dynamic query to open the rule builder.
- Use either the rule builder interface or the rule syntax textbox to define rules for the dynamic query. You can combine multiple conditions using AND / OR operators.
- In our case, we are deploying the training for the newly hired employees and hence use the attribute ‘employeeHireDate’. Below are some of the examples:
- To target employees hired on or after a specific date, use a rule like the one below:
|
1 |
(user.employeeHireDate -ge June 26, 2025) and (user.department -eq "IT") and (user.accountEnabled -eq true) |
- To automate simulation emails for users who will be hired within the next 30 days, the dynamic membership rule can be written as:
|
1 |
(user.employeeHireDate -le system.now -plus P30D) -and (user.employeeHireDate -ge system.now) |
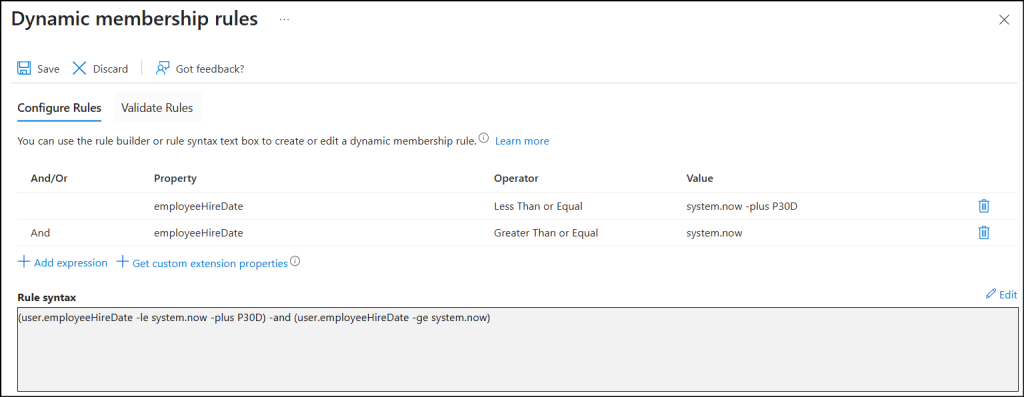
- You can also use additional attributes or custom extension properties from your applications.
- Click Validate Rules to check for errors, then select Save and click Create.
2. How to Use Dynamic Groups in Attack Simulation Training
Now that the dynamic group for newly hired employees is ready! The next step is to simulate phishing attacks and train them to respond effectively. To link this dynamic group to an attack simulation training, follow the steps below.
- Sign in to the Attack simulation training in the Defender portal.
- Go to Simulations and Launch a simulation.
- Select technique from the social engineering methods listed in the MITRE ATT&CK framework Depending on your selection, you will be able to use certain types of payloads.
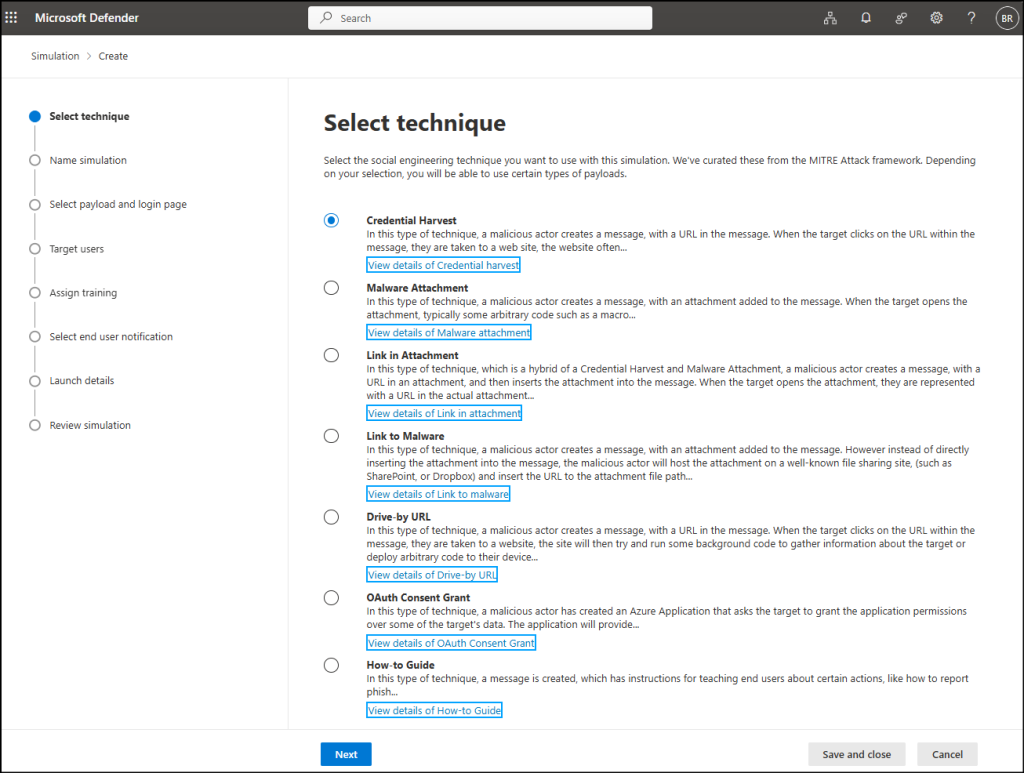
- Name your simulation and add a brief description.
- In the Select Payload and Login Page section, choose one of the two payload types:
- Global Payload: Uses a ready-made Microsoft template designed to mimic real-world phishing attacks. It automatically applies an estimated language based on user settings and includes a predicted compromise rate to help assess risk levels.
- Tenant Payload: Allows you to create a fully customized phishing email, tailored to your organization’s branding, tone, and threat scenarios, giving you more control over the simulation experience.
- Now comes the crucial step, linking the dynamic group to the attack simulation training. On the Target Users page, select Include only specific users and groups, then search and add the dynamic group you created. You can also apply filters as or optionally exclude specific users or groups.
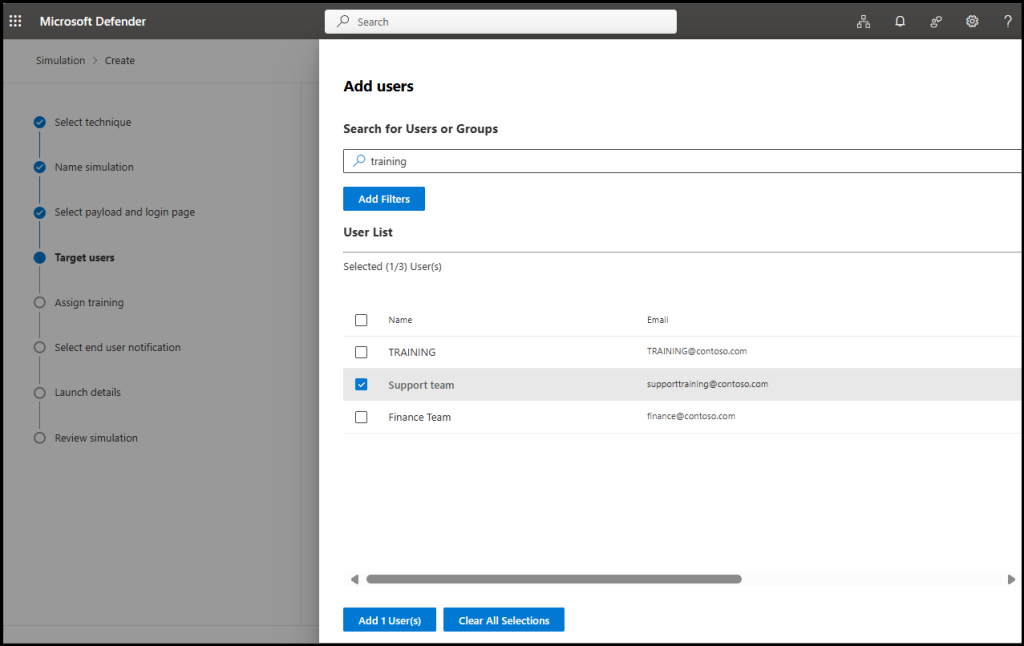
- Then, under Assign Training, select the training content preference, due date for the training and phish landing page.
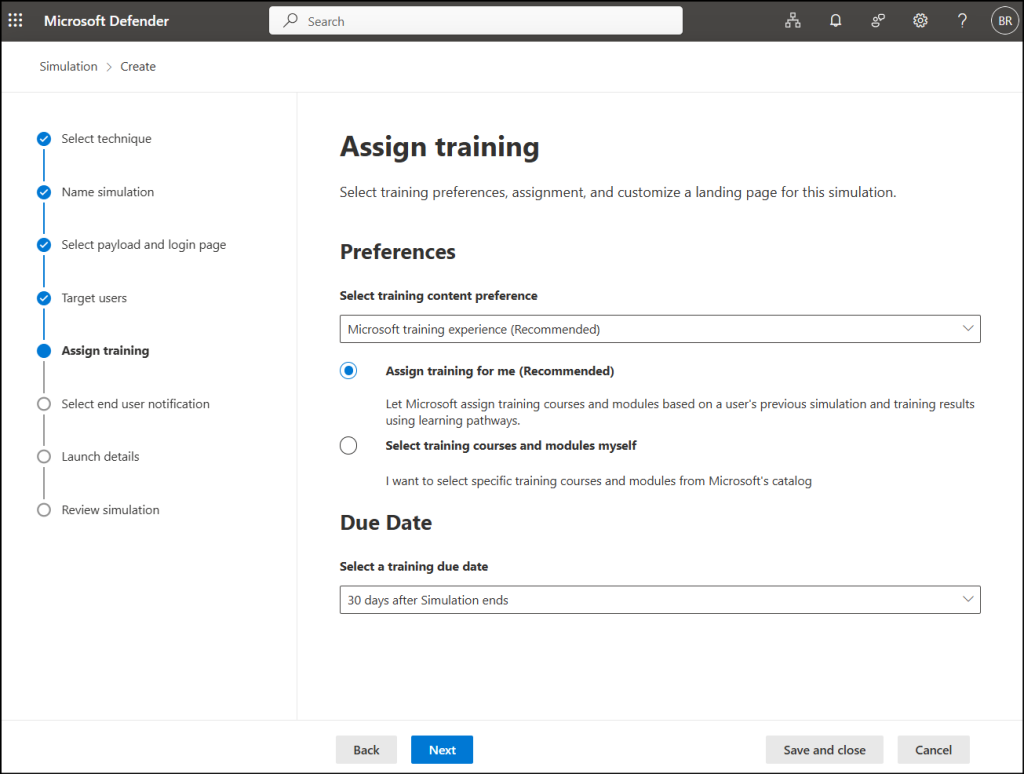
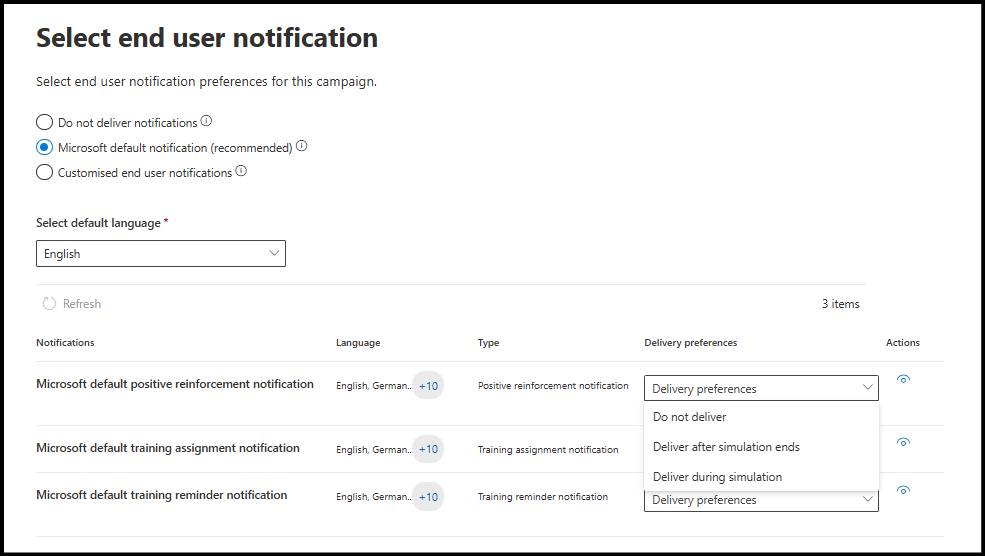
- In the Select end user notification page, you can choose the notification language, configure when users are notified (before, during, or after the simulation) and can set up reminder notifications.
- Under Launch simulation, set the start time for your campaign.
- Review all settings and optionally send a test email to validate.
- Click Submit to launch the simulation using dynamic group targeting.
View Simulation Training Reports:
Now that the simulation is complete, you’re probably eager to see how users make use of the training and assess their actions. This evaluation can be done across three key areas:
- View overall reports of attack simulation
- Export user activity for a simulation
- Detailed overview of simulation features
1. View Reports for Attack Simulation Training
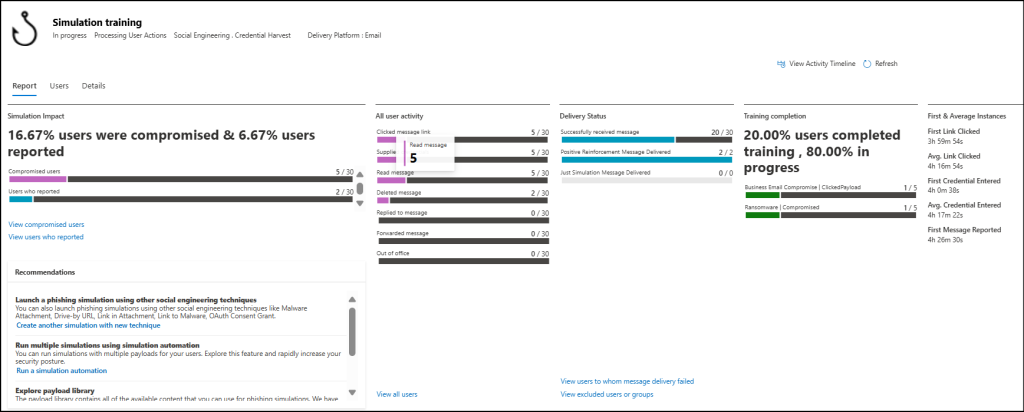
The Reports tab offers a comprehensive analysis of the attack simulation, covering the following key areas:
- Simulation Impact: Number of users compromised and those who reported the phishing attempt.
- User Activity: This section shows user responses such as clicking links, entering credentials, reading, deleting, replying to, or forwarding messages, and enabling out-of-office.
- Delivery Status: This includes number of messages that are successfully delivery, ‘Positive Reinforcement’ messages for those who reported and ‘Just a Simulation’ for those who interacted with the phishing content.
- Training Completion: Tracks users who completed or are still progressing through the assigned training.
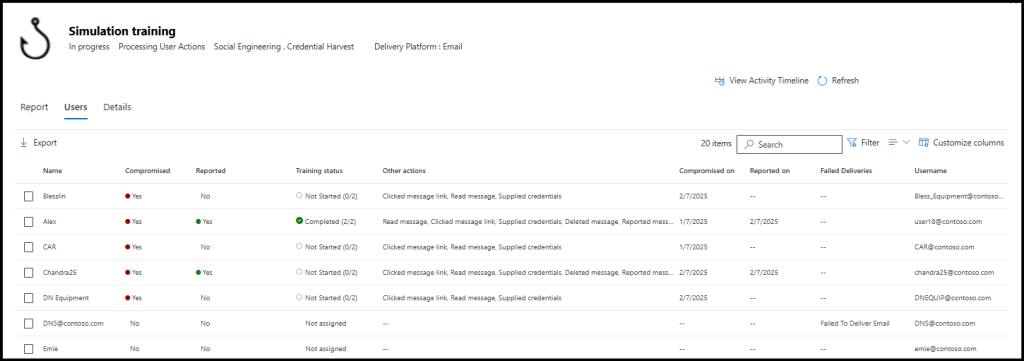
2. Export User Activity Data from a Phishing Attack Simulation
The Users tab of the simulation dashboard provides a detailed breakdown of each user’s response to the attack simulation. It displays the username, compromise and report status, the corresponding dates, user actions, and training status. You can also customize columns, apply filters, and export the data for further analysis.
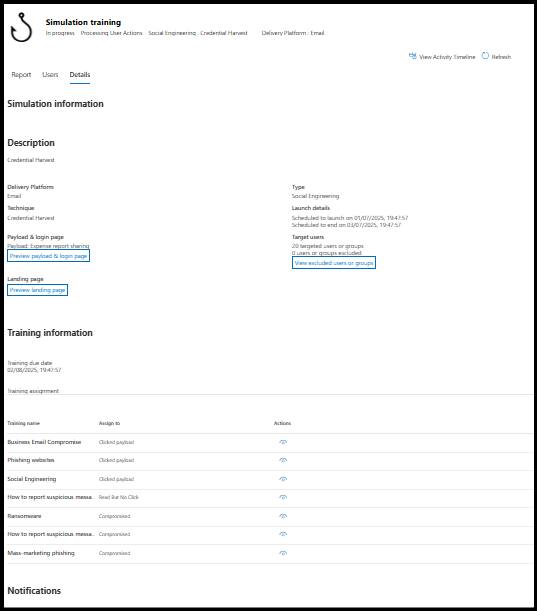
3. Detailed Attack Simulation Training Information
In the Details tab, you can access a full overview of the simulation setup and training assignments.
- It displays Simulation information such as the type, technique used, target users, launch date, and training due dates.
- This section also displays the Training information, including the due date, assigned courses, and the actions taken by users during the training.
- The tab also includes details on End-user notifications covering the notification name, type, delivery frequency, and user actions ensuring users are guided throughout the training.
Important Key Points:
- If a user is removed from a dynamic group after taking part in a simulation, this user will still appear in simulation reports and continue with assigned trainings.
- Users added to the dynamic group after a simulation has ended will not be included in that simulation, as it is already marked complete.
- At the start of an automation, users are divided across different simulations. If new users are added after some simulations have run, these users will be distributed across the remaining simulations.
End-User Perspective of Attack Simulation Training
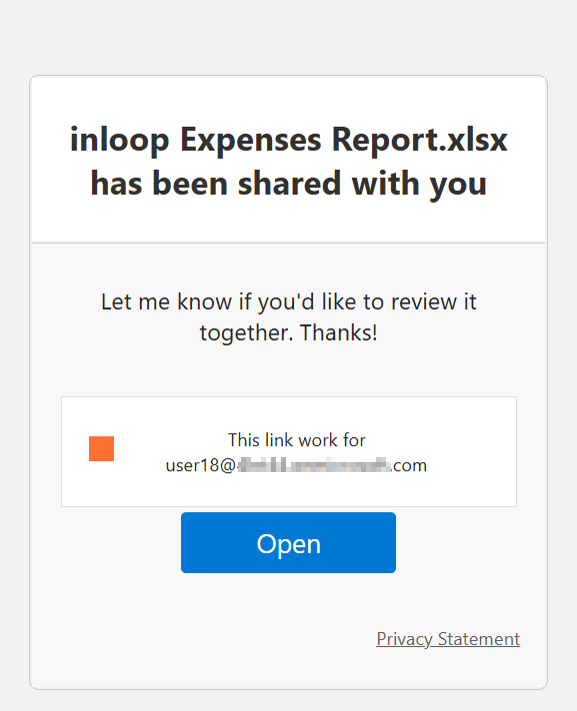
Once everything is set up, users are assigned their training and can begin immediately. Users those who are undergoing this training will receive an attack simulation training email designed to mirror real‑world phishing messages in both format and appearance (see example below). These realistic simulations teach users to recognize and report phishing attempts across a range of payloads and tactics, strengthening their ability to spot and respond to real threats.
We hope that, this blog has helped you with implementing targeted attack simulations with dynamic groups allows your organization to deliver the right training to the right users at the right time automatically. This not only boosts user awareness but also ensures Microsoft 365 email security through intelligent, hands-free simulations.






