On Day 21 of Cybersecurity awareness month, learn how to fix a compromised Microsoft 365 account. Stay tuned for more blogs in the Cybersecurity blog series.
As a matter of fact, compromised accounts remain one of the most significant cybersecurity risks in the enterprise. Having the credentials to access your Microsoft 365 account gives an attacker tremendous power to cause damage.
Credentials are the glazed donut of data types.
Well, this was a quote stated in Data Breach Investigations Report (DBIR) in 2021. According to the report, more than 80% of the data breaches were due to compromised credentials. It is also seen that compromise remediation is one of the most common security support requests raised among Microsoft 365 users. Hence, we are here to explain what actions you need to take to regain control over your compromised Microsoft 365 account and prevent it from being hacked in the first place.
What is a Compromised Account in Microsoft 365?
Access to a Microsoft 365 account is done using credentials that include a username and a password. Credentials are considered compromised when they get stolen by attackers, which can be done in diverse ways. The cause may be due to weaker passwords, clicking of malicious link, phishing scam, or downloading an app or file with malicious scripts. If you notice unfamiliar activity on your Microsoft 365 email account, someone else might have taken over your account without your permission.
How to Identify if an Account is Compromised?
If you’re wondering whether your Microsoft 365 account has been compromised, here are some red flags that may indicate it.
- Your usual password no longer works to prevent you from logging in.
- Sometimes, hackers may not change your password instead, they send phishing and spoofing emails to others from your account.
- Unusual changes to critical security changes such as recovery phone numbers and email addresses will be seen.
- You may notice unusual financial requests.
- Elevated failed authentication requests will be seen.
- Suspicious notifications like unusual sign-in on a new device, multiple password changes, and other activities you didn’t perform.
- You can notice newly created folders and mailbox forwarding rules.
- Contacts emailing you about messages you don’t recognize.
- Strange network requests from foreign countries.
- A suspicious pattern of disappearance has been observed in emails.
- You may notice different IP addresses when you log in.
- You may find suspicious signature changes to impersonate a senior executive or some other trusted individual.
By the verifying the above, you can identify compromised Microsoft 365 accounts.
What To Do When an Account Is Compromised?
As soon as you become aware that your account has been compromised, even if you are not sure, you should act quickly and carefully to mitigate undesired consequences. Here are some recommended steps to fix a compromised Microsoft 365 account.
Be quick with your investigation to minimize the damage!
- Reset the password – Change your password into a complex one. You should also reset the passwords in all relevant places. After changing passwords, sign out of all sessions on all devices.
- Enable multi-factor authentication – Implementing Multi-factor authentication will add an additional layer of security to Microsoft 365 environment.
- Run antivirus program – Run antivirus scan to eliminate malware including trojans, computer worms, spyware, rootkit, keystroke logging, etc.
- Disable suspicious inbox rules – Take a look at your mailbox to see if there are any rules you haven’t previously created. If you spot any, remove them immediately. If you spot any, remove them immediately to help secure the compromised email account in Exchange Online.
- Block external forwarding – Review the recently created external forwarding rules to prevent your emails from being leaked out without your notice.
- Change your security questions – Attackers can breach an account after answering security questions during the hack. So, modify the security questions that can be answered only by you.
- Remove mailbox delegates – At times, delegation leads to misusage and leakage of sensitive business information.
- Analyze the audit log – Audit logs provide deeper insights of events, so keep track of suspicious activity to avoid security flaws.
- Configure threshold alerts – Threshold alerts will keep you informed of suspicious activities done in unusual numbers such as deletion, moving, copying, etc.
- Notify the people that you’re hacked – Once your account is hacked, your contacts may have received several malware emails from your account. You can alert them that your account is hacked.
- Contact Microsoft Support – Microsoft Support will troubleshoot the issue and guide you on how to recover hacked Microsoft 365 accounts.
Handy tip: You can use the pre-built PowerShell script to automate compromised account remediation with 8 best practices.
How To Prevent an Account from Being Compromised?
In order to minimize the risk of compromised Microsoft 365 accounts, the first step is to make it harder to compromise.
- Always set up a strong and unique password.
- Avoid accessing your mailbox from the personal device using public Wi-Fi.
- Regularly upgrade your antivirus protection to safeguard your devices.
- Watch out for unexpected emails that contain links and/or attachments. Before clicking the link, hover over the address of the website you want to visit.
- Make use of the password manager to store complex passwords.
- Tag and Protect Priority Accounts as they are the main targets.
- Enable Multi-factor Authentication to enhance security.
- Configure email authentication methods such as SPF, DKIM, and DMARC to avoid impersonation attacks like phishing, spoofing, etc.
- Set up Microsoft Defender for user accounts which is an email filtering service that protects you against advanced threats.
- Enable Azure AD Password Protection to eliminate weaker passwords in the organization.
Implement the above steps for a safe and secure Microsoft 365 environment.
As we have seen, it’s crucial to stay vigilant and take necessary measures to safeguard your organization’s data before getting compromised. One way to do this is by regularly checking if users have enabled multifactor authentication, disabled suspicious inbox rules, blocked external forwarding, configured threshold alerts, and much more. However, it will not be an easy task, having so many activities to monitor. Here is where AdminDroid comes in.
Safeguard Accounts from getting Compromised with AdminDroid
AdminDroid is a comprehensive tool that can help admins keep track of all Microsoft 365 activities and stay on top of potential security threats. 📊🔒 With AdminDroid, admins can find various reports to monitor every bit of detail on Multi-factor authentication, inbox rules, email forwarding, and more. A few of them are listed below.
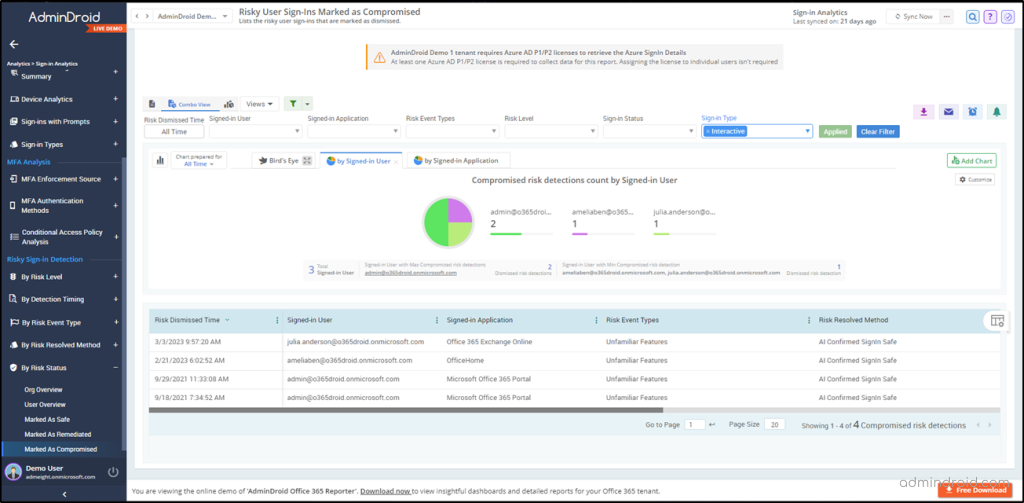
- Risky user sign-ins marked as compromised
- Admins resolved compromised risky sign-ins
- Generic admin confirmed compromised sign-ins
- MFA activated/ non-activated users
- Users with/without MFA
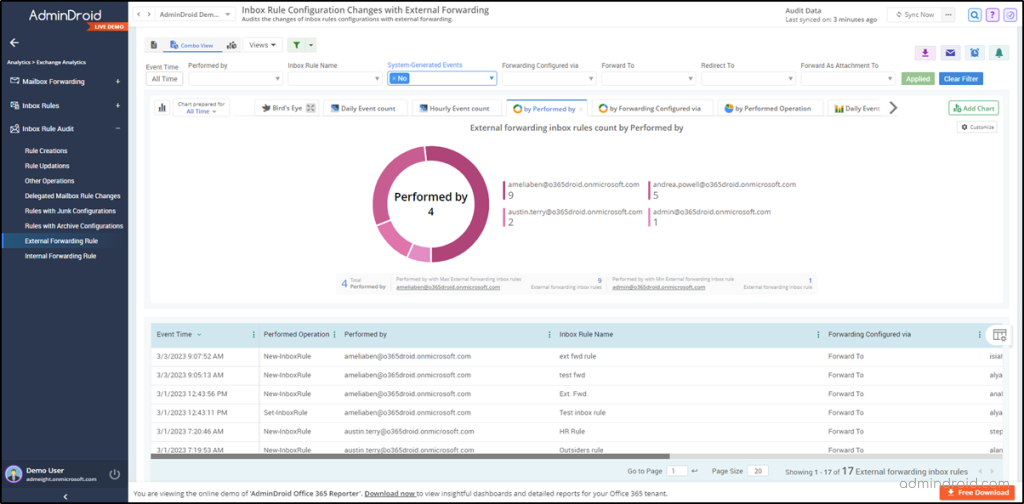
- All inbox rule configurations
- Mailbox with internal and external forwarding inbox rules
- Mailbox forwarding detailed summary
- Mailbox forwarding to external domains
- Mailbox with SMTP forwarding
Why AdminDroid?
With 1800+ reports and in-depth details, AdminDroid provides the insights required to effectively manage every service, including Azure AD, Exchange Online, SharePoint Online, Microsoft Teams, Power BI, Secure Score, and more.
Insightful 30+ dashboards are designed to provide compelling visuals and insights that make admins monitor the organization’s activity at a glance. Further, the Admindroid alerting tool provides a comprehensive solution to monitor and receive real-time alerts for suspicious activities in the Microsoft 365 tenant.
With AdminDroid Microsoft 365 reporting and auditing tool, admins can easily track the performance of M365 services, identify potential issues, and take proactive measures to ensure the organization’s data is secure. 🔒💡From managing user accounts to configuring policies, our tool has everything admins need to simplify their day-to-day tasks, saving time and hassle. 🕒
Hope this blog will help you improve your understanding of compromised accounts and how to solve them! If you have any queries, feel free to reach us through our platforms for further assistance.






