Traditionally, cybersecurity has focused on external threats like hackers, malware, and unseen dangers beyond digital defenses. However, internal threats can cause significant disruption to sensitive data and compromise security just as much as external attacks. So, organizations need to prioritize insider risks and address these often-underestimated ones. Here’s where the Insider Risk in Conditional Access policy comes in!
Security is not just about protecting against external threats but also about managing the risks that come from within.
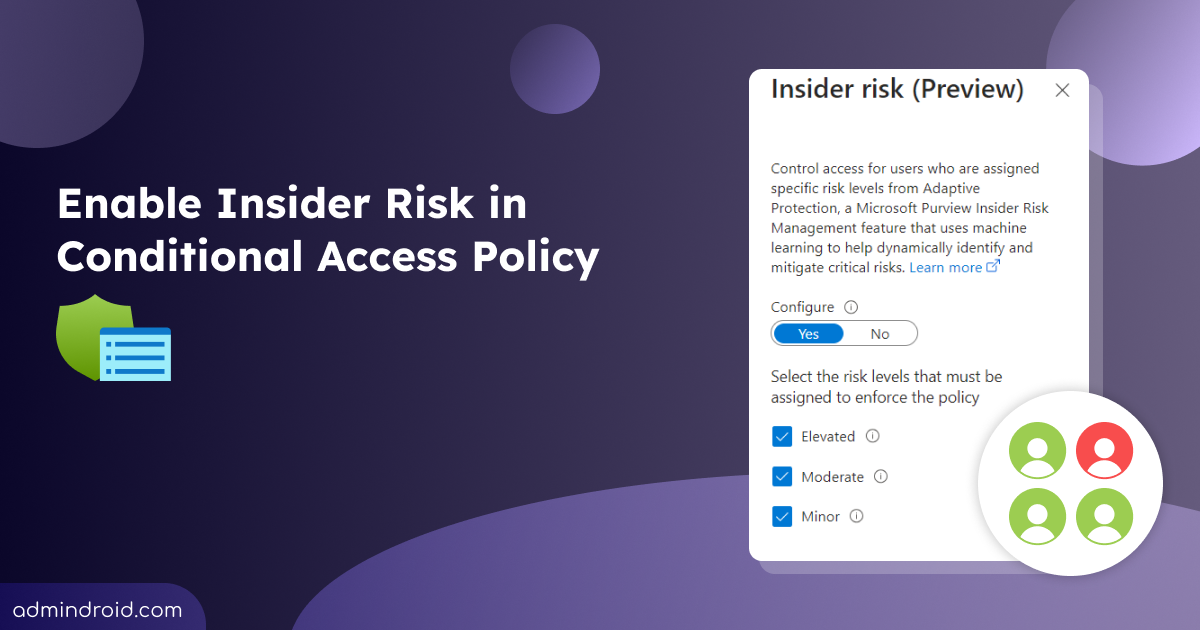
Microsoft Entra Conditional Access policies now include a preview feature ‘insider risk’ to automatically block access to critical assets based on insider risk levels, ensuring data security. Basically, insider risk in Conditional Access is the integration of Microsoft Purview adaptive protection and Entra ID Conditional Access. To learn more, let’s dive deeper into it! 🚀
Insider Risk Management in Microsoft 365
Microsoft Purview Insider Risk Management (IRM) workflow helps organizations identify, investigate, and respond to malicious and unintentional user activities. As part of insider risk management, adaptive protection uses machine learning to identify patterns of user behavior that indicate increased risk. To set up adaptive protection in Microsoft Purview, users need to be assigned to insider risk management role groups and have the necessary licenses, including:
- Microsoft 365 E5
- Microsoft E5 compliance add-on
- Insider Risk add-on for Microsoft 365
Note – Before getting started with insider risk in the Conditional Access policy, it is essential to activate IRM and implement adaptive protection within Microsoft Purview.
How Does Insider Risk in Conditional Access Work?
To start with the basics, Conditional Access policies in Microsoft Entra ID serve as a powerful tool for organizations to enforce strict security requirements and access controls based on specific conditions. To determine access to resources, it evaluates signals such as user identity, location, device, user-risk, and sign-in risk. Based on identity’s risk assessment, a variety of controls like configuring MFA, block access, etc., are deployed.
Let’s take a closer look at how ‘insider risk’ in Conditional Access policies works:
- Firstly, adaptive protection in Microsoft Purview analyzes user activity for indicators of potential insider threats. This can include things like downloading large amounts of data, accessing unauthorized files, or unusual login attempts.
- Based on the analysis, adaptive protection categorizes users into three risk levels – Elevated, Moderate, and Minor. As users’ risk level fluctuates, it automatically switches them between policies, ensuring data protection over time.
- Following the adaptive protection implementation, you can configure Conditional Access policies to automatically add users in response to insider risk levels. For example:
- Block access: Deny access to critical resources for users with an elevated risk level.
- Require Multi-Factor Authentication (MFA): Restrict access to specific resources or ask to configure multi-factor authentication for moderate-risk users.
- Limit access: Limit access to specific applications or data for users with minor risk levels.
How to Configure Insider Risk in Conditional Access Policy?
To create a Conditional Access policy, you need Global/Security/Conditional Access administrator permission along with Microsoft Entra ID P1 and P2 licensing options. You can also create CA policies by using pre-defined Conditional Access policy templates.
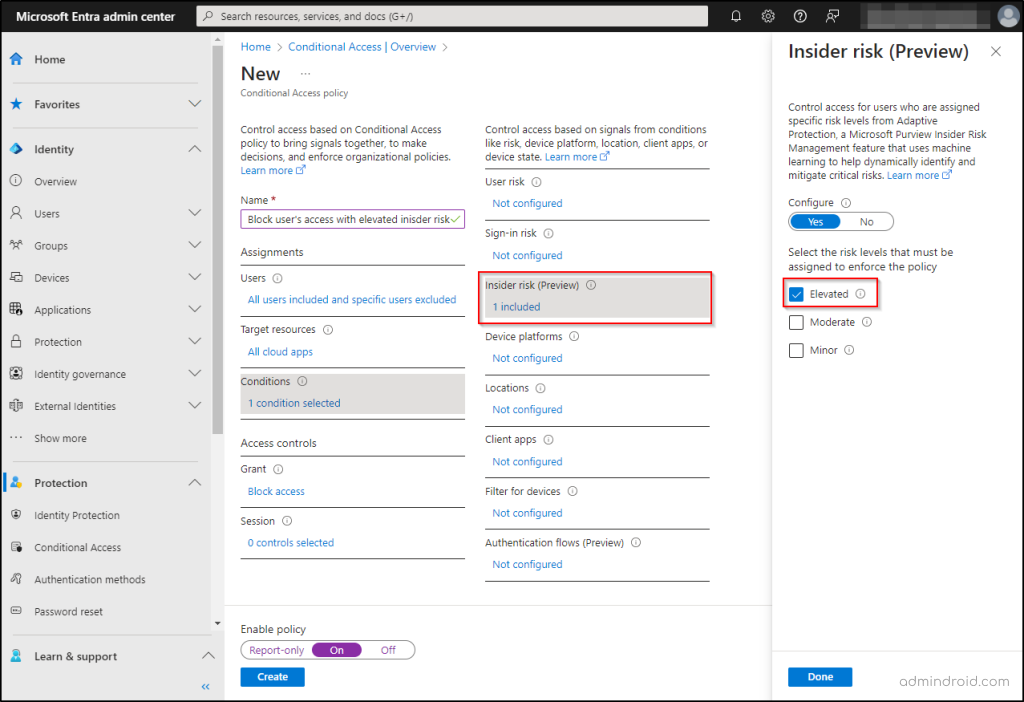
Follow the below-mentioned steps to enable insider risk in the Conditional Access policy.
- Sign into Microsoft Entra admin center.
- Navigate to Identity –> Protection –> Conditional Access.
- Click on Create a new policy.
- Provide a suitable name for your policy.
- In the Assignment section, choose Users. In the Include category, select All users and exclude required users or break glass accounts.
- Navigate to Target and resources and select All cloud apps.
- Select Conditions and you will notice a newly added condition named ‘Insider risk’ which is currently in preview. Click on Insider risk (Preview).
- Turn the toggle to Yes under Configure in the right pane and choose any of the following options based on requirements. Select Done. Here I am opting for ‘Elevated’.
🔴 Elevated – Users identified as Elevated risk levels are entirely blocked from using any applications.
🟠 Moderate – Access to certain applications is restricted for users classified as medium risk level.
🟡 Minor – Users categorized under the Minor risk level must acknowledge the Terms of Use before accessing an application.
- Since the insider risk is chosen as Elevated, under the Grant section, opt for Block Access.
- Confirm your settings and flip the Enable policy toggle from ‘Report-only’ to On.
- Click Create to create your CA policy.
By following these steps, organizations can fortify their defenses against insider threats, bolstering their cybersecurity posture comprehensively.
In conclusion, insider risk management bridges the gap between external and internal threats in cybersecurity. By integrating Entra Conditional Access with Purview Adaptive Protection, organizations can proactively safeguard against potential risks.
More importantly, it is also essential to stay aware of the CA policy changes. So, you can monitor Conditional Access policies with M365DSC. It will help you to get alerts instantly about policy changes, and you can make use of it to auto-correct the modified policy. Additionally, consider activating the security features in Microsoft Entra to tighten overall protection. 🎯
If you need more support or have further queries, please contact us in the comments section.