On Day 26 of Cybersecurity Awareness Month, learn how to enable the ‘remember multi-factor authentication’ setting for trusted devices in Microsoft 365. Don’t miss the rest of our Microsoft 365 Cybersecurity blog series for more tips and insights!
Microsoft recommends enabling multi-factor authentication (MFA) to safeguard your user accounts and reduce the risk of hacking. However, MFA alone doesn’t guarantee complete safety! As David Bernstein wisely said,
“For every lock, there is someone out there trying to pick it or break in.”
Even with MFA, vulnerabilities can arise due to the default 90-day bypass window for authentication. This extended period increases the risk of threats such as session hijacking and unauthorized access. To truly secure your Microsoft 365, it’s essential to customize the ‘remember multi-factor authentication’ setting for reducing this reauthentication period.
In this blog, we’ll show you how to enable the ‘remember MFA’ feature and customize the ‘Don’t ask for MFA again for X days’ setting to achieve a balance between convenience and security.
What is ‘Remember Multi-factor Authentication on Trusted Device’ Feature?
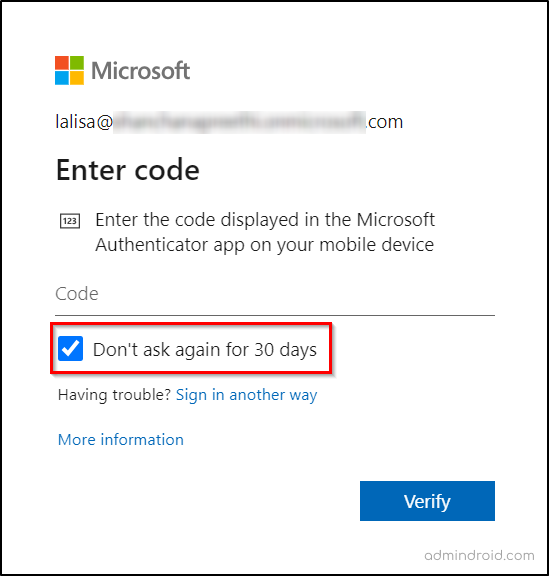
The ‘Remember Multi-factor Authentication on Trusted Device’ feature in Microsoft 365 allows users to bypass MFA for a set period on devices they trust. When this feature is enabled, users who successfully sign in with MFA can select the option ‘Don’t ask again for X days’.
This action sets a persistent cookie in the browser. As a result, they won’t be prompted for MFA again on that device until the cookie expires, which by default is set to 90 days. However, if the user signs into a different browser on the same device or clears their cookies, they will be prompted to verify their identity again.
But is it truly safe to leave the default 90-day period unchanged? Absolutely not! Let’s explore why customizing and reducing this period is crucial for your security.
Importance of Optimizing the ‘Remember MFA’ Setting in Microsoft 365
Setting the “Don’t ask again for X days” option to a longer period in Microsoft 365 can introduce various security issues, including:
- Session Hijacking: Longer reauthentication durations increase the likelihood of malicious actors hijacking user sessions. This risk is particularly pronounced when sensitive information is accessed on public or shared devices.
- Risk of Stolen or Lost Trusted Devices: A prolonged MFA grace period may prevent necessary prompts when trusted devices are stolen or lost, increasing the risk of unauthorized access to sensitive data. In such cases, it’s essential to revoke MFA sessions in Microsoft 365.
To mitigate these risks, organizations should strike a balance between user convenience and security needs. That’s why enabling remember multi-factor authentication in Microsoft Entra and customizing the number of days is essential. Let’s see how to enable it.
How to Enable Remember Multi-factor Authentication in Microsoft 365?
To adjust the ‘remember MFA’ setting and reduce the number of days users can trust their devices, follow the steps outlined below.
- Sign in to the Microsoft Entra admin center.
- Navigate to the Identity > Protection > Multifactor authentication (If you don’t see this option, click Show more at the bottom of the left pane).
- On the Multi-factor authentication page, under the Configure section, click on Additional cloud-based multifactor authentication settings.
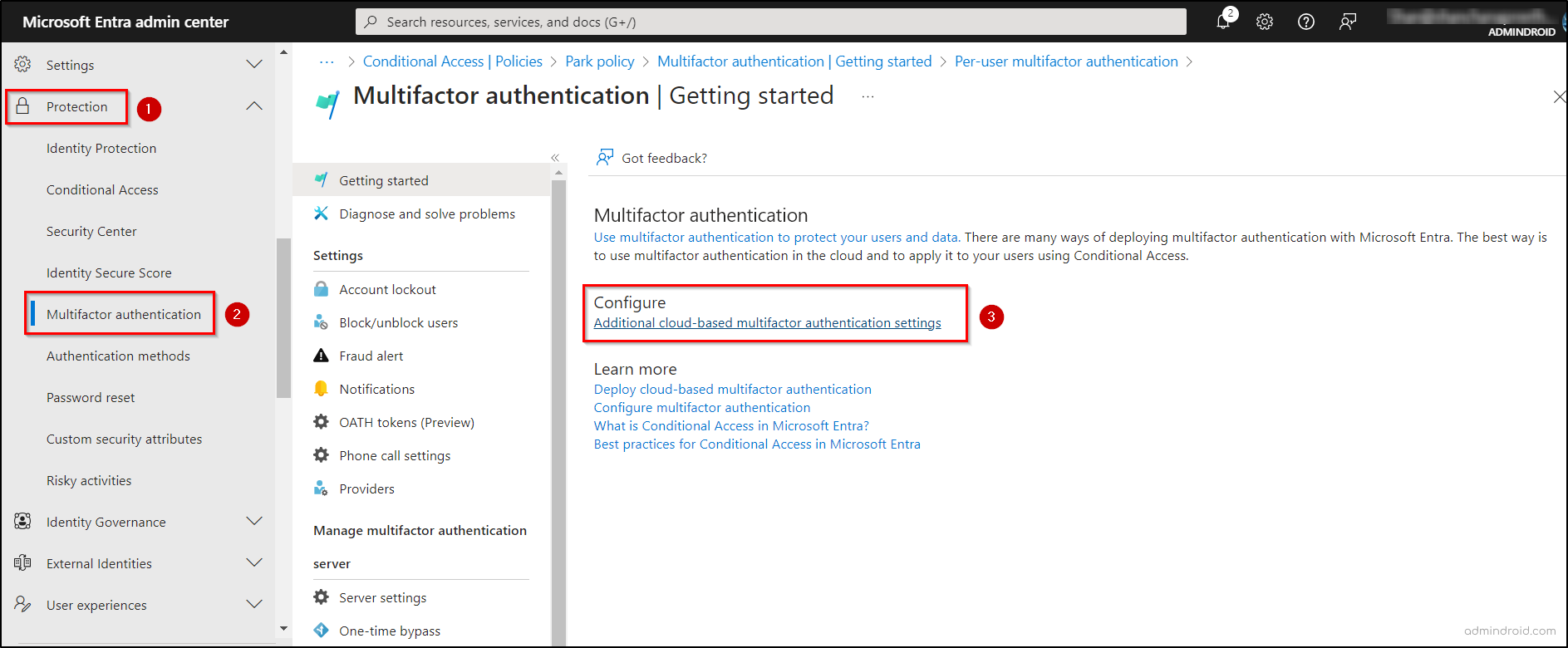
- Switch to the Service Settings tab and scroll down to the Remember multifactor authentication on trusted device section.
- Check the box for Allow users to remember multifactor authentication on devices they trust.
- Enter a value in the Number of days users can trust devices for field. Ensure this value is less than 90 days.
- Finally, click ‘Save’ to apply your configurations.
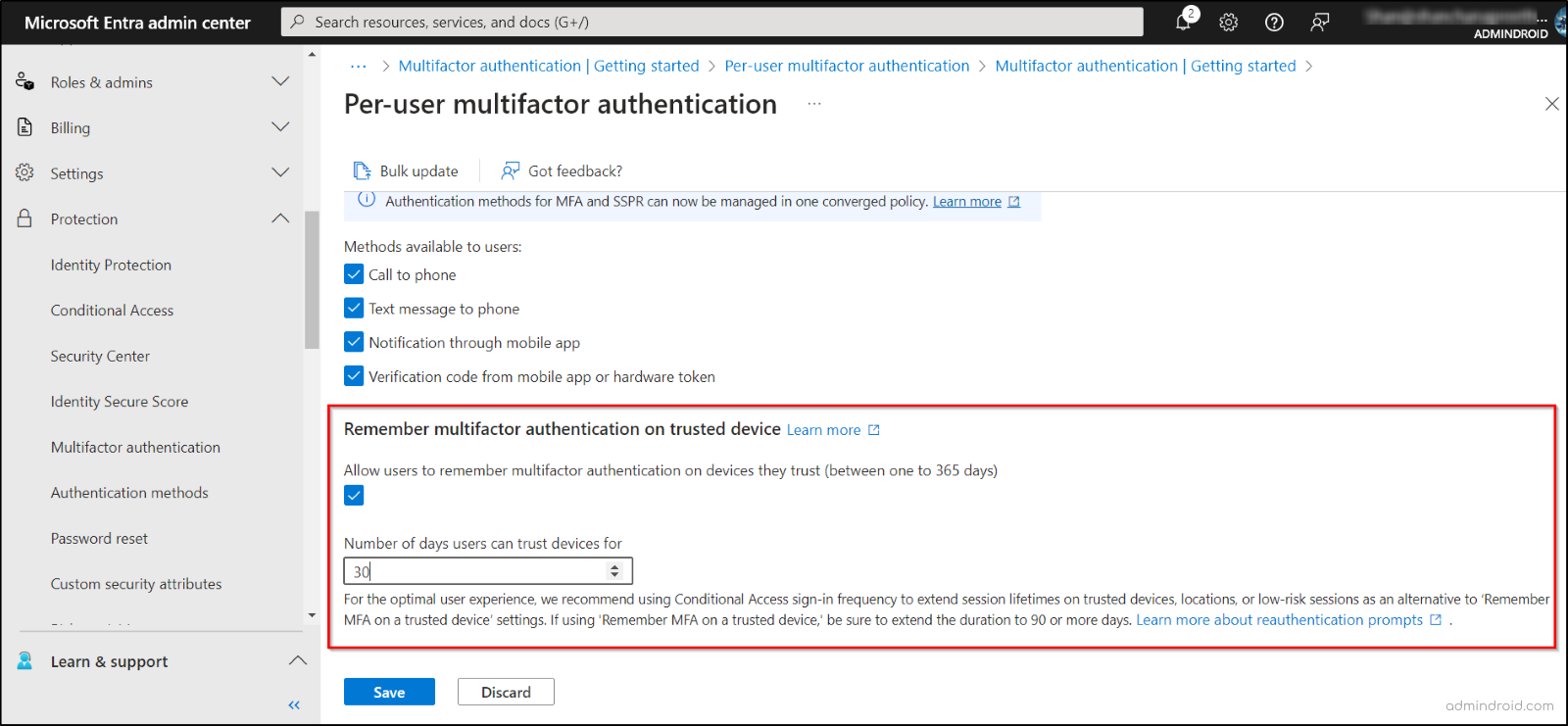
Note: You can enter a value between 1 and 365 days, but it’s recommended to keep it under 90 days for added security on sensitive resources. However, Microsoft recommends not setting it to less than 30 days if you want to minimize MFA prompts from known devices.
By following these steps, you allow users to remember their multi-factor authentication on trusted devices, which improves security while simplifying the authentication process.
How Can Users Mark a Device as Trusted?
After configuring the ‘remember multi-factor authentication’ feature, users can mark a device as trusted during sign-in. To do this, they should select ‘Don’t ask again for X days’.
Points to Remember:
- The ‘Don’t ask again for X days‘ option is unavailable in non-browser applications, which use refresh tokens that provide new access tokens hourly.
- This feature reduces MFA prompts for web apps. However, if a shorter duration is set, it may increase prompts for modern authentication clients, especially with Conditional Access policies.
- The ‘remember MFA’ feature is incompatible with AD FS’s ‘Keep me signed in’ option, leading to potential verification loops. Users who select ‘Keep me signed in’ on AD FS and mark their device as trusted won’t be automatically verified after the expiration period.
- The ‘remember MFA’ feature is not available for B2B users when they sign in to the invited tenants.
- This setting is incompatible with the Sign-in frequency Conditional Access control and using them together may result in unexpected prompts for users.
In summary, customizing the ‘remember MFA’ setting in Microsoft 365 helps balance convenience and security. By adjusting this setting, organizations can lower the risk of unauthorized access while maintaining a smooth user experience. Regular adjustments enhance Microsoft 365 security and protect sensitive data.
We’d love to hear your thoughts! Feel free to leave your comments in the section below.