Day 2 of the Microsoft Entra Suite camp started with the announcement of surprising new features in Entra ID. The session then moved on to how Entra Suite helps ensure least privilege access through access packages, seamless onboarding with lifecycle workflows, automatic access updates using dynamic role attributes, and more.
If you need to know about all the sessions, you can refer here:
Day 1: Unify access with Microsoft Entra Suite
Day 3: Secure access to on-premises apps with Entra Suite
Day 4: Detect shadow AI usage and protect Internet access with Entra Suite
Key Highlights from Day 2
Microsoft announced several new innovations in Entra, now available in public preview, including:
1. Group Source of Authority (SOA) Conversion
Manage on-prem Active Directory (AD) groups directly from Entra ID using access packages, lifecycle workflows, and more. (Full Explanation below)
2. Shadow AI and IT Visibility
Get real-time insights into SaaS and AI apps accessed by your users. Microsoft enables this by monitoring network activity in real-time.
3. Threat Intelligence Filtering
Prevent users from accessing malicious destinations using Microsoft’s threat intelligence feeds, including data from over 40 third-party sources.
4. Netskope One Integration
Advanced Security Service Edge (SSE) integration provides unified protection against malware, zero-day threats, and data leaks.
The session gave a hint about the Group SOA conversion, and we may learn about the other innovations in detail in the upcoming sessions.
Group SOA Conversion: Bringing Cloud Governance to Legacy Groups
Many organizations still depend on Active Directory (AD) security groups to manage access to critical on-premises resources. However, these legacy groups lack visibility and modern governance. There’s no way to run access reviews, automate membership changes, or enforce approval workflows.
This is where Group Source of Authority (SOA) Conversion steps in to transform the game.
With this new capability, you can shift the authority of your on-premises AD security groups to the cloud and manage them using modern, cloud-native governance tools.
Once converted:
- Group memberships can be fully managed through Entra ID.
- You can apply governance policies like access requests, expiration rules, and AI-powered access reviews.
- Even if the group still controls access to on-premises apps, governance is now enforced from the cloud.
👉Example:
Let’s say you have a legacy AD security group called “Finance” that controls access to specific on-premises resources. Right now, there’s no way to review who still has access, no lifecycle automation, and no approval process.
With Group SOA Conversion, you can:
- Convert the Finance group to Entra ID.
- Manage it more effectively with advanced cloud governance features.
After a crisp introduction, the session moved on to the main topics:
1. Achieve Least privilege Access to Users Using Access Packages
One of the key capabilities is access packages, part of Microsoft Entra Entitlement Management. Access packages allow organizations to provide the right access to the right people at the right time, without delays or administrative bottlenecks.
Access packages allow admins to define exactly what resources a user should get access to based on their role, department, or business need. Instead of assigning broad access manually (which often leads to over-permissioning), admins can pre-define a curated set of resources that align with specific job functions.
- To strengthen the security further, the request process can be integrated with Entra Verified ID Face Check. This ensures the identity of the requester is validated before access is granted, making sure only the right person receives access to the necessary resources.
📌 Example:
Let’s say your organization bulk onboarded external users for a project collaboration. Instead of granting access individually, you can create an access package that includes all the necessary resources for the users. Once configured, users can simply:
- Go to “My Access” in their account.
- View the available Access Packages.
- Request access to the relevant package.
- Complete Face Check verification.
- Upon approval, they receive only the access they need.
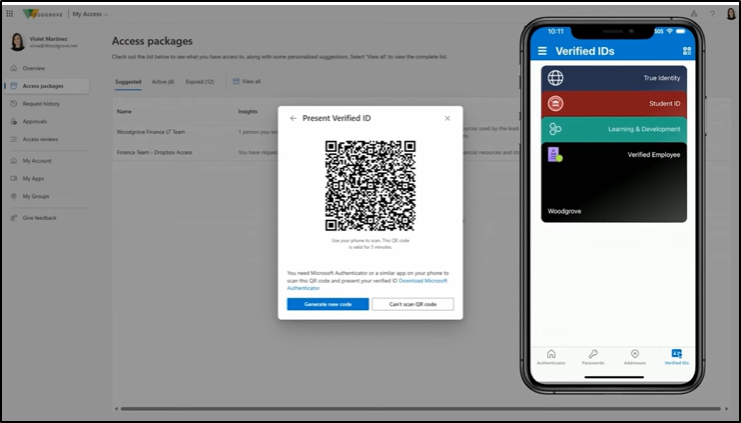
Hope you got the idea of implementing least privilege access using access packages. Now, let’s turn to lifecycle workflows.
2. Automate Access Transition with Precision Using Lifecycle Workflows
When a user’s role changes, their access needs should change too. But in many organizations, this process is still handled manually, often delayed or overlooked entirely.
Microsoft Entra solves this with Lifecycle workflows that automate access transitions based on real-time changes to user attributes. These workflows detect role changes and automatically remove outdated access and grant new permissions, ensuring access always aligns with the user’s current responsibilities.
📌 Example:
Imagine Diego works in the Marketing team and recently got promoted to Product Manager.
- As soon as Diego’s role attribute in Entra ID changes to “Product Manager”, he’s automatically added to the dynamic group for product managers.
- This triggers a role change workflow, which removes him from marketing groups, revokes all refresh tokens to enforce updated policies, and grants him access to all product team resources.
Not just that, admins can simplify Microsoft 365 user onboarding and offboarding by automating key tasks through lifecycle workflows.
That’s a wrap on Day 2 of the Entra Suite Camp! Stay tuned for more updates from the upcoming sessions—there’s plenty more to explore.