Third-party apps can be powerful productivity boosters in Microsoft 365, but they also introduce real security risks. When users grant these apps broad permissions, they can unintentionally expose sensitive emails, chats, or calendar events to unauthorized access. Attackers often exploit this by disguising malicious apps as legitimate ones and tricking users into consenting.
To address this, Microsoft has updated the Microsoft-managed default policy to require admin consent for third-party apps accessing Exchange Online and Microsoft Teams APIs. Let’s explore how this update strengthens app security and what it means for your organization.
Overview of Admin Consent for Third-Party Apps to Access Exchange and Teams
If your organization uses the Microsoft-managed default policy, this update allows only admins to grant consent for new third-party apps accessing Exchange Online and Teams. It also applies to apps requesting new or extended permissions to access Exchange and Teams. This rollout is part of Microsoft’s Secure Future Initiative (SFI) and its ‘Secure by Default’ approach to strengthen default permissions.
This update builds on the earlier SharePoint and OneDrive update that blocked legacy protocols and required admin consent for third-party apps accessing files and sites. By extending this control to Exchange and Teams, Microsoft aims to give administrators greater oversight of which apps connecting to organizational data.
Note: You don’t need an additional license to apply this rollout.
Rollout Timeline
🗓️ Microsoft will roll-out the admin consent update for Exchange and Teams APIs between the end of October and late November 2025.
How the Update Affects User Consent in Exchange and Teams?
For organizations using the Microsoft-managed default consent policy, third-party apps can access Exchange and Teams only after receiving admin approval. This admin consent will be applied to third-party apps connecting through Microsoft Graph, legacy protocols like Exchange Web Services (EWS), Exchange ActiveSync (EAS), POP3, and IMAP4. Previously consented apps will continue to function normally, while any new or existing apps requesting additional permissions will now require admin consent.
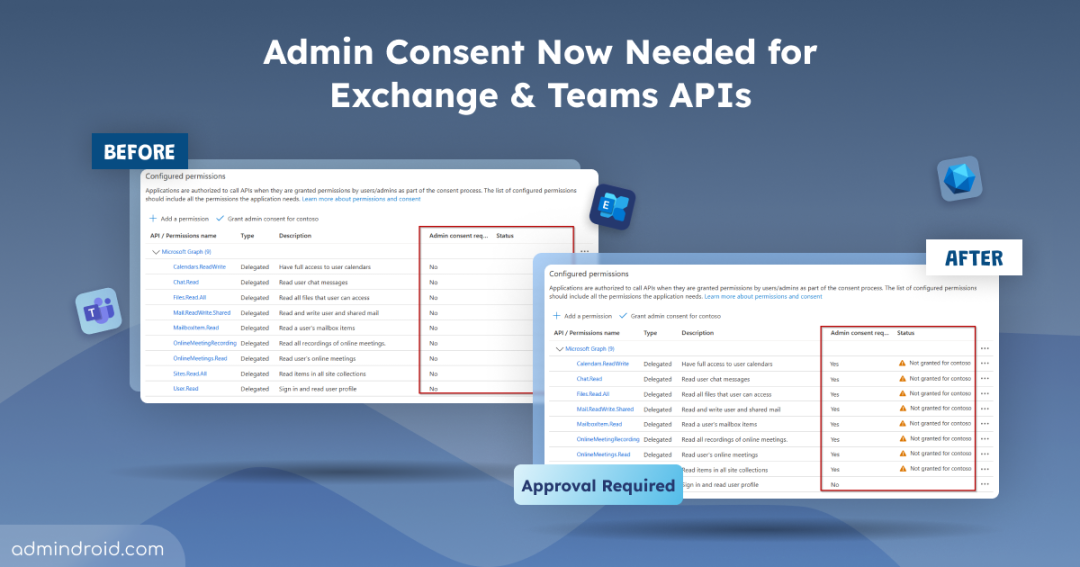
The following permissions are affected by this change.
| API | Permissions |
| Microsoft Graph | Mail.Read, Mail.ReadWrite, Mail.ReadBasic, Mail.Read.Shared, Mail.ReadBasic.Shared, Mail.ReadWrite.Shared, MailboxItem.Read, Calendars.Read, Calendars.ReadBasic, Calendars.ReadWrite, Calendars.Read.Shared, Calendars.ReadBasic.Shared, Calendars.ReadWrite.Shared, Chat.Read, Chat.ReadWrite, ChannelMessage.Read.All, OnlineMeetings.Read, OnlineMeetings.ReadWrite, OnlineMeetingTranscript.Read.All OnlineMeetingRecording.Read.All |
| Legacy Protocols (Exchange Web Services (EWS), Exchange ActiveSync (EAS), POP3, and IMAP4) | EAS.AccessAsUser.All, EWS.AccessAsUser.All, IMAP.AccessAsUser.All POP.AccessAsUser.All |
After the policy rollout, above listed permissions will require admin consent like shown in the image below.
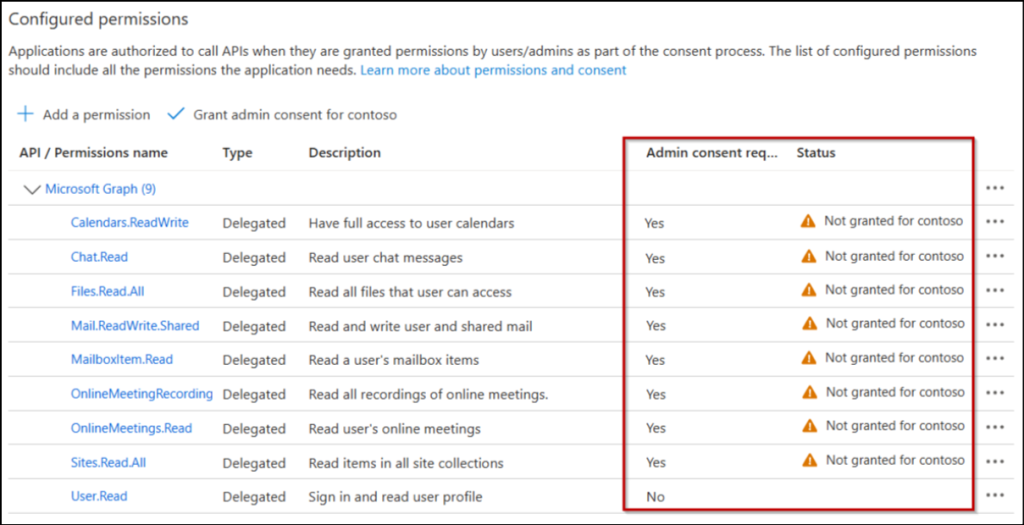
It’s also important to note that this update does not change how your data is processed. Instead, it ensures only admins can now approve specific app permissions, stopping users from granting third-party access to Exchange and Teams. However, to enhance the end-user experience, some Exchange email clients are exempted from this change.
How to Prepare for the Update?
With admin-only consent taking effect, prepare your organization to ensure uninterrupted access for approved apps. Here’s how:
| Recommended actions | Implementation |
| Review existing app permissions | View all app permissions to identify third-party apps and the specific permissions they use to access Exchange and Teams. |
| Plan granular consent policies | If you’re using user-consent for certain trusted apps, create granular app access policies ahead of time so users can continue using them without disruption. |
| Enable admin consent workflows | Configure admin consent workflows that let users request administrator approval for third-party apps requiring access to Exchange and Teams. |
Along with this, notify IT admins, app owners, and security teams about these changes so they can adjust their workflows and app management plans accordingly. Also, ensure your internal policies are updated to reflect that users can no longer grant consent for Exchange and Teams apps independently.
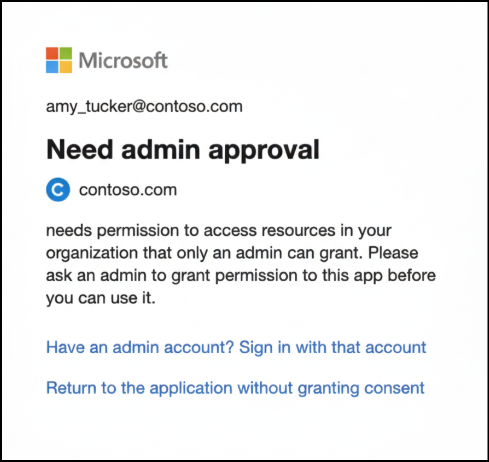
End User Experience
After policy change has been rolled out, users attempt to connect the app with affected delegated permissions scope will see the following message. This prompt may differ if the admin consent workflow is enabled in your organization.
That’s all about the update! We hope this blog helped you understand how Microsoft’s update requiring admin consent for Exchange and Teams APIs enhances your organization’s data security. Stay tuned for more insights, and feel free to share your questions or feedback in the comments below!