Two pieces of news about Azure AD have been circulating the internet for the past few days, causing quite a stir. They say:
MFA by text and voice calls seems to be going away on July 10 2023.
However, there seems to be a lack of clear information from Microsoft regarding the elimination of SMS and voice calls auth methods using registration campaign in Azure AD. But the message center news has not provided any definitive statements! Adding to the confusion – there bombed another contrasting news from Microsoft that,
Introducing Voice One Time Password (OTP) – An improved version of our voice call method starting in August 2023!
Looks like great confusion, right? Two contrasting news (MC584364 & MC611686) from Microsoft, but not even well and clear! So, I just got my hands on the initial claim and analyzed whether it is indeed true or not? 🤔 Therefore, I have done an analysis to shed some light on the matter, and here’s the breakdown.
Changes to the Registration Campaign in Azure AD
What really is “registration campaign in Azure AD”? Confused? Let’s see a clear breakdown below.
Basically, registration campaign in Azure AD are all about pushing your Microsoft 365 users to set up Microsoft Authenticator during the sign-in process. When a user authenticates with weak auth methods such as SMS/voice calls, they will be immediately prompted to set up Microsoft Authenticator if they are under this campaign.
It’s like a digital wake-up call, pushing them toward a more secure authentication experience!
⚠️Big news, Now Microsoft is shaking things up with an update! In the message center news numbered MC584364, Microsoft has made an update to the registration campaign in the Azure AD feature.
Starting from July 10th, 2023, the registration campaign enables the support to move from SMS and voice call authentication methods.
- With this update, users within your organization who currently rely on SMS and voice calls for MFA will be prompted to set up Microsoft Authenticator during the sign-in process. If you have a favorite third-party identity provider, you can now use it to meet MFA requirements with the new external authentication method support in Microsoft Entra.
Note: But wait, I must give you a heads-up. Microsoft has recently removed specific news from the message center. But MS has confirmed this news about registration campaign in Azure AD in their official doc. Trustworthy sources, right? (Image attached below)
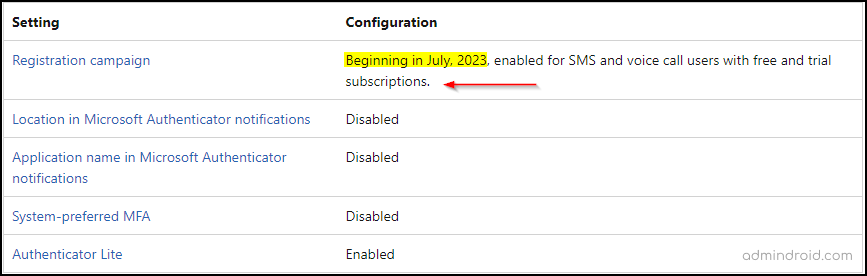
🙄So, what’s the buzz all about? Well, Microsoft aims to completely eliminate weak authentication methods and encourage the adoption of stronger MFA methods, such as system-preferred MFA via this campaign! This initiative seeks to enhance security, protect sensitive data, and provide a more robust authentication mechanism for users.
Overall, this is such a good move from Microsoft, kudos! 👏
Push Users to Set up Microsoft Authenticator for MFA Authentication:
Admins can enable the registration campaign policy in the Azure portal and specify which users or groups should be included or excluded from the campaign. Not only can admins force, but they can also determine how many days a user can postpone or snooze this nudge.
Point to Remember: Users can only delay the app setup three times.

Voice One Time Password (OTP) in MFA:
Now coming to the second claim, voice one-time passwords. Does this really a needed change? Yeah, probably for a few users. 💯For users whose mobile phones cannot support the Authenticator app, voice calls are the go-to! While voice calls may have had a reputation for being a weaker auth method, Microsoft has swooped in with a fantastic update to enhance its security!
Instead of relying on users to confirm their authentication by pressing the pound key, a unique one-time passcode (OTP) will now be verbally provided to them during the voice call.
This exciting update introduces the concept of voice OTP as part of the new “Phone OTP” authentication method, which represents a significant improvement over the current SMS authentication method. In light of this, Microsoft recommends users migrate from traditional voice to voice OTP, as traditional voice will be deprecated in the near future.
Now, let’s address the big question: Should admins be worried about this change? 🤔
Well, my answer is NO! As we move towards stronger security strategies, it’s high time we bid farewell to those weaker multi-factor authentication methods to avoid potential risks such as MFA fatigue attacks, sim-swapping attacks, and more.
Though Microsoft has played a little hide-and-seek with this message center update, rest assured, there’s nothing to worry about. This change is for the better!
Let’s focus on enforcing strong authentication methods like phishing-resistant MFA and more to take our security game to the next level! 🛡️






