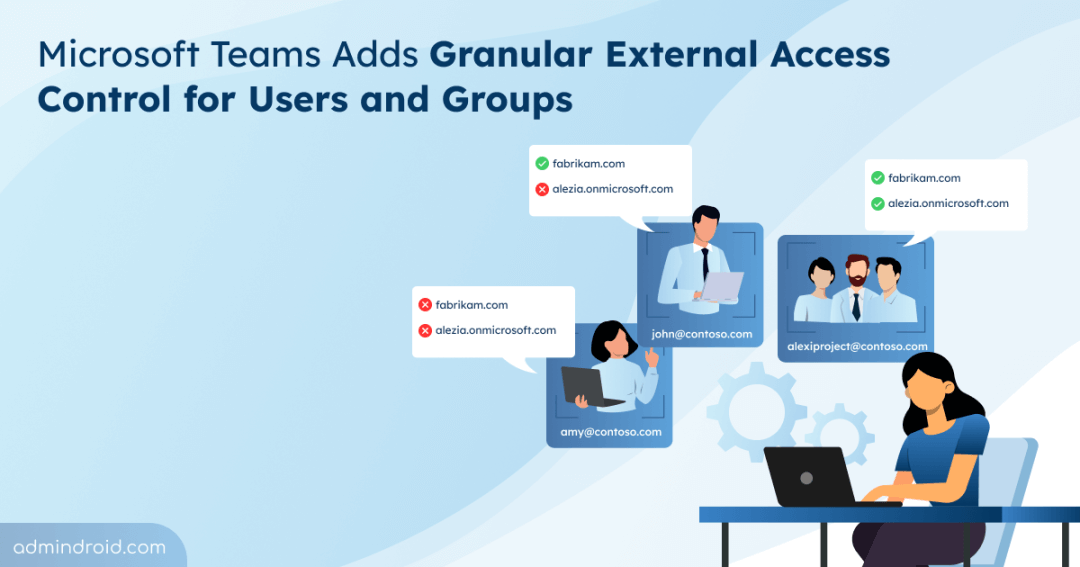
External access in Microsoft Teams has always been a key part of collaboration, allowing your organization to communicate with users outside your tenant. Until now, admins managed this access at the tenant-wide, either allowing all users to communicate externally or blocking all external interactions. Even with policy-level settings, admins could only choose to inherit the tenant-wide settings or block all external domains for specific users.
Now, Microsoft Teams takes external access control a step further. Admins can set granular external access policies for specific users and groups, specifying exactly which external domains they can interact with. Curious to learn more? Keep reading, this blog explores the new granular external access by domain for specific users and groups in MS Teams.
A Closer Look at Granular External Policy by Domain in Microsoft Teams
Previously, the external user access configuration in MS Teams had to be applied across the entire organization. Now, you can create and assign custom external access policies to specific users. This means certain users can interact with different external domains than those defined in the organization-wide settings.
For example, your organization might allow only two external domains at the tenant level. With a custom external access policy, you could grant a specific user or group permission to communicate with all external domains.
This flexibility opens up a range of practical scenarios:
- Pilot projects: Allow a particular department or team to collaborate with specific external partners.
- High-risk roles: Restrict external communication for users in sensitive positions, reducing potential security risks.
- Selective collaboration: Grant broader access to users who need to interact with multiple external domains, while keeping others restricted.
Configuration of Custom External Policy in Microsoft Teams
When creating a custom external access policy in Microsoft Teams, admins can choose from five configuration options. Each defines how users or groups assigned to the policy interact with external domains:
- Use organization settings
The user or group simply follows the organization-wide external access configuration. No exceptions or overrides are applied. - Allow all external domains
Users can communicate with anyone outside the organization. All external domains are trusted by default. - Allow only specific external domains
Communication is restricted to a defined allow list. Users can only collaborate with external organizations on that list. - Block only specific external domains
Users can communicate with all external domains, except those explicitly defined on a block list. - Block all external domains
All external communication is completely blocked for the user or group, regardless of the organization’s wider settings.
Timeline for the New Teams External Access Experience
Microsoft began rolling out Targeted Release in early September 2025 and expects to finish it by mid-September 2025.
General Availability is planned to start in late October 2025 and should be fully rolled out worldwide by mid-December 2025.
Note: During the target release, admins must perform configurations through PowerShell. Once the feature reaches general availability, the Teams admin center UI will support these settings as well. This will make it easier to assign policies without relying on code.
How to Configure Granular Microsoft Teams External Access Management Using PowerShell
Once the target release is available for your tenant, you can use the following approach to configure granular Microsoft Teams external access for specific users and groups.
1. Allow Custom External Access Domain Policy
To break the inheritance from the tenant-wide external configurations, connect to Microsoft Teams and run the following cmdlet.
|
1 |
Set-CsTenantFederationConfiguration -CustomizeFederation $true |
Now, you can create and assign as many custom policies as needed to users or groups in your tenant.
2. Create Custom External Access Policies in MS Teams
To create external access policies in Microsoft Teams, you can use the New-CsExternalAccessPolicy cmdlet with the -CommunicationWithExternalOrgs parameter. The following configurations show how to create policies with different external access conditions.
- Allow All External Domains: To create a custom policy that allows all external tenants to collaborate with your organization’s users, execute the following cmdlet.
|
1 |
New-CsExternalAccessPolicy -Identity <CustomPolicyName> -CommunicationWithExternalOrgs "AllowAllExternalDomains" |
- Allow Only Specific External Domains: Run the following cmdlet to create an external access policy which allows users to communicate only with specific external tenants.
|
1 |
New-CsExternalAccessPolicy -Identity <CustomPolicyName> -CommunicationWithExternalOrgs "AllowSpecificExternalDomains" -AllowedExternalDomains @("domain1", "domain2") |
- Block Specific External Domains: To create a custom policy for blocking collaboration with specific external domains, execute the cmdlet below.
|
1 |
New-CsExternalAccessPolicy -Identity <CustomPolicyName> -CommunicationWithExternalOrgs "BlockSpecificExternalDomains" -BlockedExternalDomains @("domain1", "domain2") |
- Block All External Collaboration in Teams: Execute the following cmdlet to create a custom external access policy that blocks users from communicating with any external users in Microsoft 365.
|
1 |
New-CsExternalAccessPolicy -Identity <CustomPolicyName> -CommunicationWithExternalOrgs "BlockAllExternalDomains" |
- Follow Tenant-Wide Teams External Access Settings: If you want to create a policy that inherits the tenant-wide external access settings, use the cmdlet below.
|
1 |
New-CsExternalAccessPolicy -Identity <CustomPolicyName> -CommunicationWithExternalOrgs "OrganizationDefault" |
Note: You can later update any custom policy using Set-CsExternalAccessPolicy if your external access requirements change.
3. Assign Policies to Users or Groups
After creating the policies, you can assign them to specific Entra ID users and groups using the New-CsBatchPolicyAssignmentOperation cmdlet for targeted external access.
|
1 2 |
$Users = @("user1@domain.com", "user2@domain.com","group1@domain.com") New-CsBatchPolicyAssignmentOperation -PolicyType ExternalAccessPolicy -PolicyName "<CustomPolicyName>" -Identity $Users |
We hope this blog helped you understand how granular external access policies in Microsoft Teams can transform the way you manage collaboration. By tailoring access at the user or group level, your organization gains precision, strengthens security, reduces risks, and ensures collaboration stays aligned with the unique needs of each team.
If you have any doubts or questions, feel free to share them in the comment section. We’re here to help.