Microsoft Entra Health (preview) helps you monitor the Microsoft Entra tenant health efficiently. It includes a report of Service Level Agreement (SLA) attainment and the ability to review sign-in reporting scenarios using scenario monitoring. In an organization, monitoring user sign-ins is crucial to identify suspicious logins and prevent unauthorized access. There are usually many additional checks available during authentication before a successful user login. Though organizations utilize them, IT admins often verify various sign-in scenarios to ensure none of the loopholes are left unmonitored. Here comes Scenario Monitoring in Entra, currently in public preview, to simplify sign-in monitoring and save time.
Let’s explore how Scenario monitoring and SLA attainment report in Microsoft Entra Health works.
Enable Scenario Monitoring Preview for Sign-in Reporting
The scenario monitoring preview feature is disabled by default, and you must enable it to track sign-in reporting scenarios. You can also disable the preview at any time, if not required. Follow the steps below to enable scenario monitoring preview in Microsoft Entra.
- Sign in to the Microsoft Entra admin center as at least a Reports Reader.
- Navigate to Identity –> Settings –> Preview hub.
- Turn on the scenario monitoring toggle to enable the preview feature.
Note: After enabling, it might take up to 24 hours to populate. Enabling this preview feature changes only your view, not the entire tenant.
License Requirement for Microsoft Entra Health
To access Microsoft Entra Health features like Scenario monitoring and SLA attainment report, you must have a Microsoft Entra P1 license.
Track Sign-in Activity Trends Using Scenario Monitoring Preview
Scenario monitoring in Entra provides sign-in trends at the tenant level. To access this feature, navigate to Identity –> Monitoring & Health –> Health (Preview) –> Scenario Monitoring in the Entra admin center. You will have separate tiles for each sign-in reporting scenario and by clicking on ‘View Details’ option, you can visualize the metrics specific to that scenario. The sign-in trends for the last 30 days will be available for each scenario. You can also set the date range from 24 hours to 1 month.
Let’s dive deep into the four crucial scenarios monitored frequently by organizations.
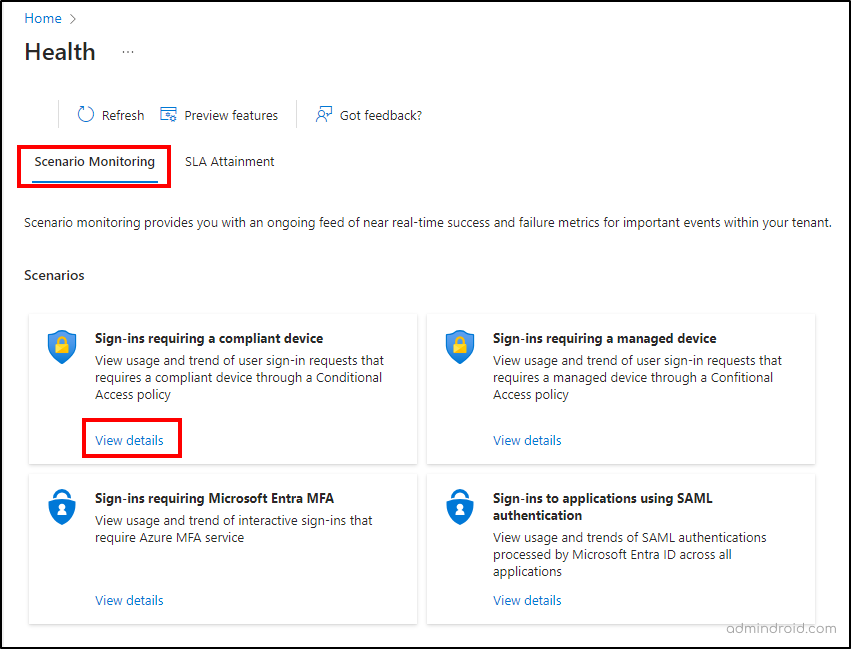
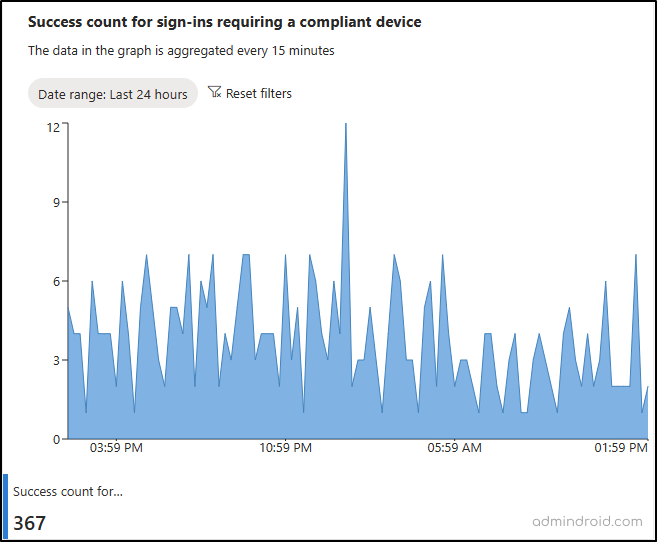
1. Review Sign-ins Requiring Device Compliance Using Scenario Monitoring in Entra
If your organization’s Conditional Access requires users to be signed in from a compliant device, the successful sign-in count satisfying this condition will be shown in this scenario. The data provided here is aggregated every 15 minutes. It clearly shows the number of user authentication requests successfully logged in using a compliant device. A compliant device can be an iOS/Android device, tablet, or Microsoft Entra joined computers (not hybrid) and is managed by Microsoft Intune.
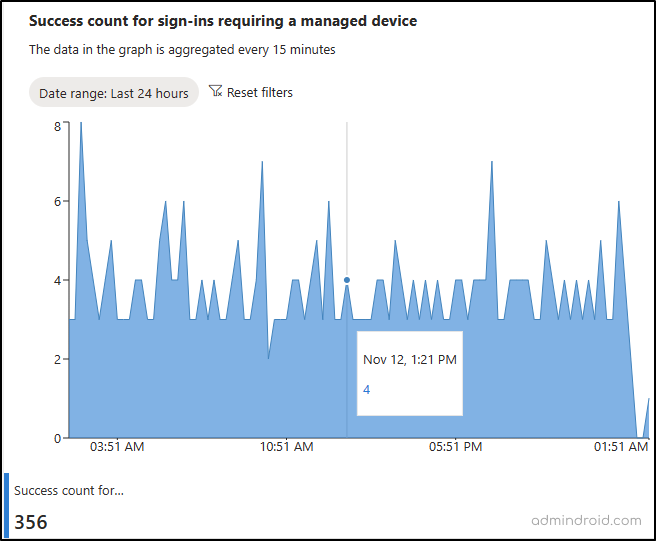
2. Monitor Sign-in Scenarios Requiring a Managed Device
This scenario shows the successful sign-in count that satisfies a CA policy requiring user sign-ins from a managed device. On-premises managed or joined computers and Entra ID hybrid joined computers are considered as managed devices.
3. Monitor Interactive Sign-in Scenarios Requiring Azure MFA
Successful and failed interactive user sign-ins that require Microsoft Entra MFA authentication are provided with clear spikes here. Admins can easily identify the failed sign-ins that don’t satisfy the MFA authentication process and take necessary actions.
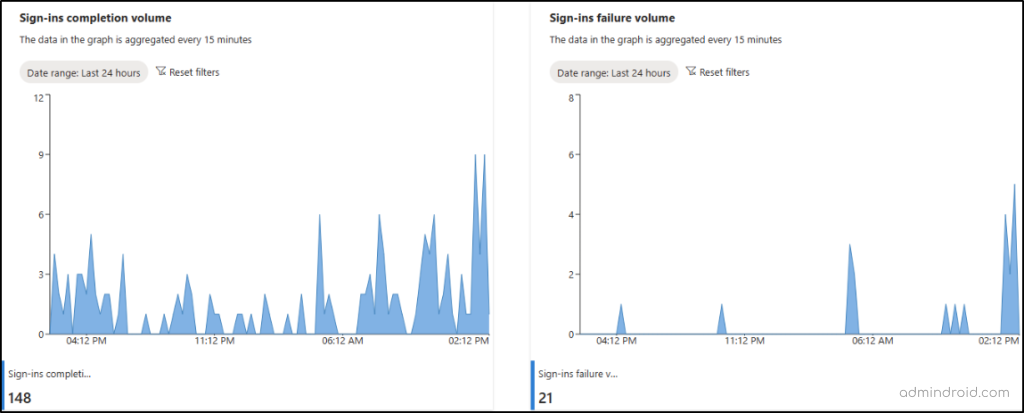
Note: Instances where a user refreshes the session without completing the interactive MFA or using passwordless sign-in methods are not included in these metrics.
4. Monitor Application Sign-ins Using SAML Authentication
This scenario shows the number of sign-in attempts to applications using SAML 2.0 authentication successfully processed by the Microsoft Entra cloud service for your tenant.
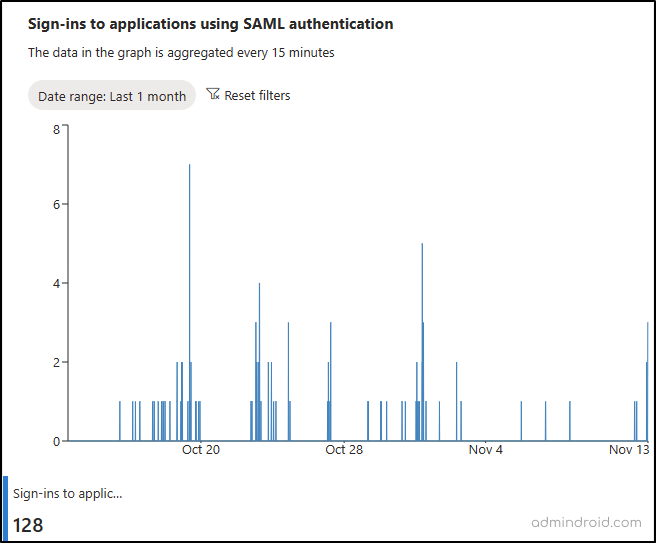
Note: Currently, WS-FED/SAML 1.1 apps integrated with Microsoft Entra ID are excluded from this metric.
Scenario Monitoring in Entra Using Graph Explorer
You can also view the above sign-in scenario metrics using Microsoft Graph Explorer effectively. Using various cmdlets for each sign-in scenario, you can effectively monitor the following.
- Successful sign-ins of compliant devices.
- Successful sign-ins of managed devices.
- Successful application sign-ins using SAML authentication.
- Successful & failed Entra MFA sign-in attempts.
Investigate Microsoft Entra Health Monitoring Alerts and Notify Users
Updated on (2/17/2025): Recently, Microsoft has provided the ability to track alerts for the Entra health scenarios to identify and mitigate potential risks in the tenant. The Entra health metrics are fed into the anomaly detection service to understand and identify any significant change in the tenant’s pattern using machine learning. After detecting changes in the pattern, it triggers an alert.
What to investigate when Alert Triggers?
- The data stream, or health signal, that triggered an alert.
- Total affected entities, including users, applications, etc.
- Sign-in logs and audit logs to identify details on affected users and application configuration changes.
- Information from different services based on the scenario. For example, a device-based scenario needs investigation on Intune device policies.
Prerequisites for investigating and modifying alerts:
- A tenant with Microsoft Entra ID P1 or P2 is required to view the signal metrics.
- A tenant with both non-trial Microsoft Entra ID P1 or P2 and a minimum of 100 monthly active users is required to view alerts and send alert notifications.
- At least a Report Reader role is required to view and configure alerts and at least the Helpdesk Administrator role is required to update alerts and alert notification settings.
- To view alerts using Graph API, the HealthMonitoringAlert.Read.All permission is required.
- To view and modify alerts using Graph API, the HealthMonitoringAlert.ReadWrite.All permission is required.
Steps to Investigate Entra Health Monitoring Alerts
- Navigate to Microsoft Entra –> Protection –> Monitoring & Health –> Health Monitoring tab.
- Select any of the scenarios for alert investigation.
- Select an active alert to investigate.
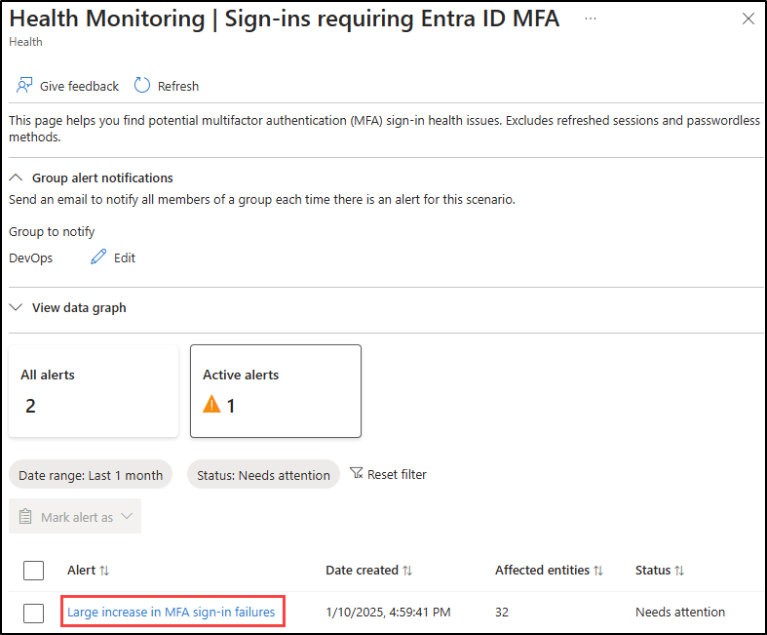
4. After selecting, you can find the creation date and alert status. In the affected entities section, choose the ‘View‘ option to investigate the affected entity like users and applications. Also, a link will be available for scenario-specific resources to investigate more details effectively.
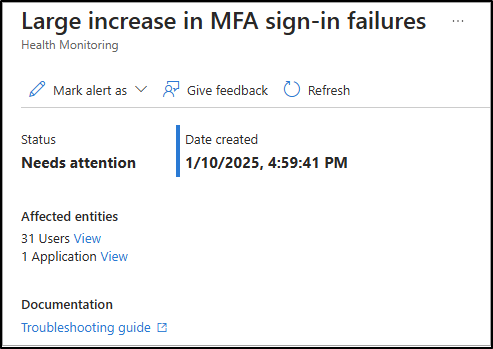
5. After choosing an affected entity, you will see the top 10 entities list from which you can choose a specific entity to find out more details. Choosing an entity navigates to their profile page.
6. Under the Signal section, you can review the alert signal to identify usage patterns and anomalies for a specific period.
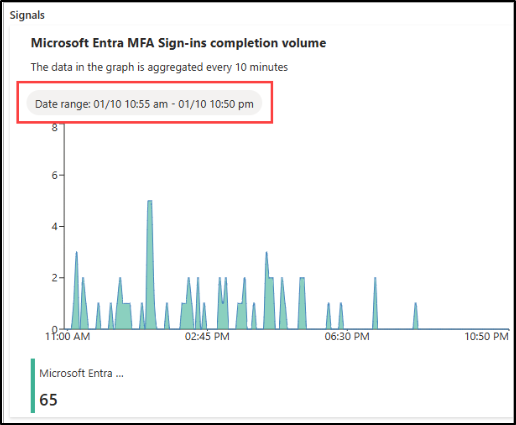
7. After investigating and resolving the issue, you can dismiss the alert by clicking on the ‘Mark Alert As dropdown –> Dismissed‘.
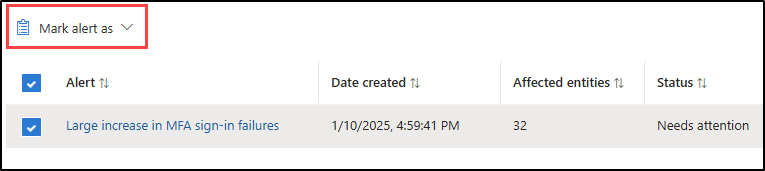
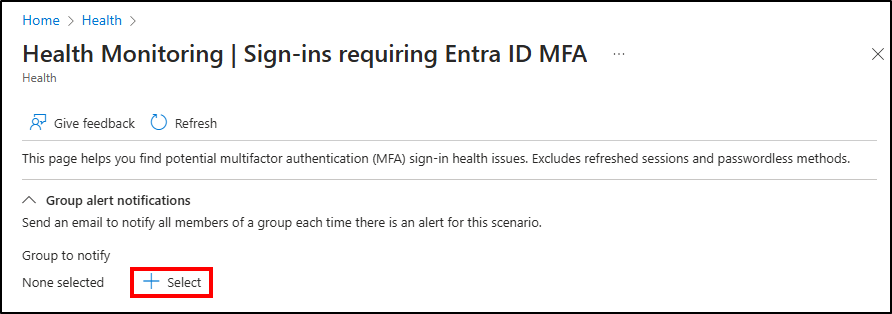
Apart from the investigation, Microsoft also provides the ability to notify specific groups whenever an alert is triggered. To configure alert notifications, click on ‘Select‘ under the ‘Group alert notifications’ section on the top of the scenario page. Choose the required groups, and the alert notification will be sent to the group members.
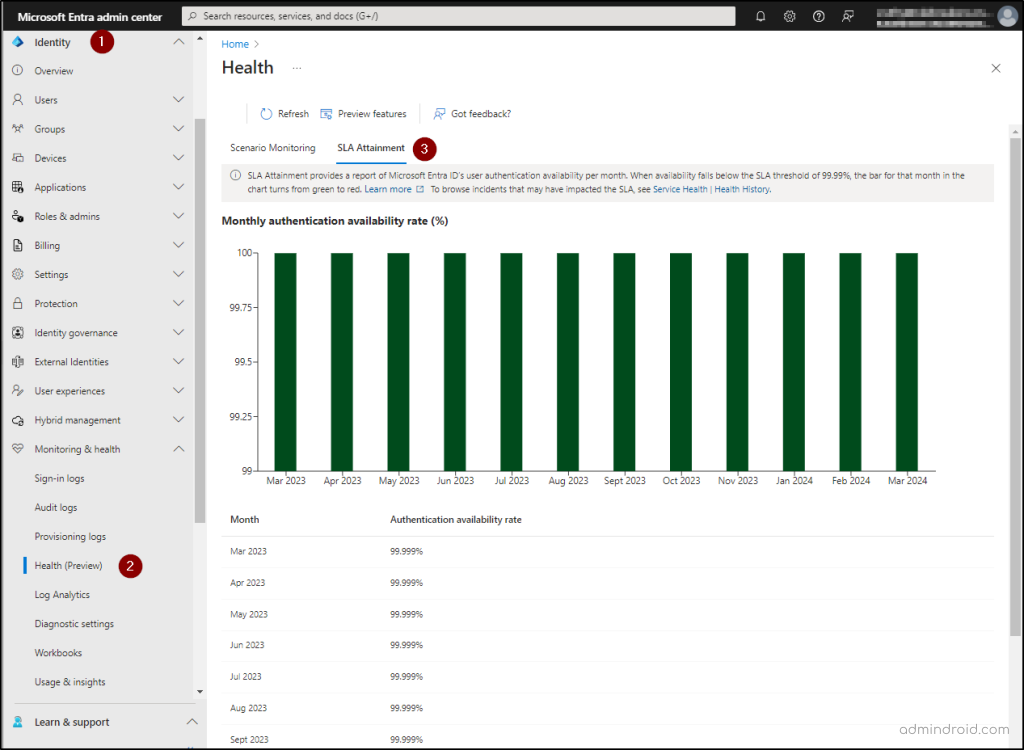
Monitor Tenant Health Using SLA Attainment
A Service Level Agreement (SLA) provides details about the services provided like service uptime, available duration, etc. In Microsoft Entra Health, the SLA attainment report is available by default. Using this report, you can check the authentication availability rate for each month for your tenant. Apart from global SLA performance, Microsoft Entra now provides a tenant-level SLA report with precise details for organizations having at least 5000 monthly active users.
I hope this blog helps to learn about Microsoft Entra Health features to manage your tenant health efficiently and save your time. Reach out to us through the comment section for any queries. Have a healthy tenant!