The COVID-19 pandemic changed the way we work, introducing the “work from home” culture🏠. Even as the pandemic subsides, a hybrid work culture is emerging and so are the cyber threats in Microsoft 365 over the internet.
Now, you might think, “Isn’t VPN a solution🤔?” While VPNs provide a secure internet connection, they mask the original IPs which is a significant drawback causing security risks.
So, what can you do to protect Microsoft 365 users from potential threats when accessing Microsoft 365 resources, internet traffic, and SaaS applications? Here’s a secure gateway- “Microsoft Entra Internet Access,” which is currently in public preview. It’s like a security bodyguard who follows you wherever you go online.
Let’s dive into the blog to learn more about this new Microsoft Entra Internet Access in detail.
Global Secure Access in Microsoft Entra
Global Secure Access is a Secure Service Edge (SSE) solution for effective network, identity, and endpoint access controls. It is built on the principles of Zero Trust to use least privilege, verify explicitly, and assume breach. This approach allows Global Secure Access to deliver secure connection to any applications or resource, regardless of where you are.
Global Secure Access is a centralized hub where you can monitor and oversee all the features of the two latest products: Microsoft Entra Internet Access and Microsoft Entra Private Access.
| Microsoft Entra Internet Access | Microsoft Entra Private Access |
| Microsoft Entra Internet Access is used to provide secure access to public internet resources. Ex: Access to SaaS apps. | Microsoft Entra Private Access is used to provide secure access to private, corporate resources. Ex: Access to Private web apps. |
Let’s see about the first product “Microsoft Entra Internet Access” in detail now.
What is Microsoft Entra Internet Access?
Microsoft Entra Internet Access is a secure web gateway that ensures the protection of users, devices, and data by monitoring and controlling online activities. This solution simplifies decision-making for organizations by combining identity and network access solutions. Now, there’s no need to navigate the complexities of choosing tools for each app or aligning policies between identity and networking teams.
In clear, Microsoft Entra Internet Access offers secure access to public internet apps through its identity-centric, device-aware, and cloud-delivered secure web gateway. This not only enhances visibility and security over user access but also provides a fast and seamless experience when accessing internet contents.
Initially, Microsoft Entra Internet Access was in public preview exclusively for Microsoft 365 resources. However, it has now expanded its public preview to include SaaS applications and cover all internet traffic.
Note:
- To access the preview, you’ll need a Microsoft Entra ID P1 license. In case you don’t have one, you can either purchase licenses or opt for trial licenses.
- For utilizing the Microsoft 365 traffic forwarding profile, you need to have Microsoft 365 E3 license.
- Keep in mind that after general availability, Microsoft Entra Private Access and Microsoft Entra Internet Access may require different licenses!
Unique Capabilities of Microsoft Entra Internet Access
Here are some of the key capabilities of the identity centric internet access protection- “Microsoft Entra Internet Access”.
1. Seamless Integration with Conditional Access Policies:
Microsoft Entra Internet Access can work hand-in-hand with Conditional Access policies to finely control access to any website or domain on the internet using Web content filtering.
To enhance security while accessing internet content, consider configuring a “compliance device” condition within your Conditional Access (CA) policies for all internet traffic. This measure boosts overall security by adding additional checks to your access controls.
This integration also helps you in a way to monitor Conditional Access policies for proactive threat detection and response
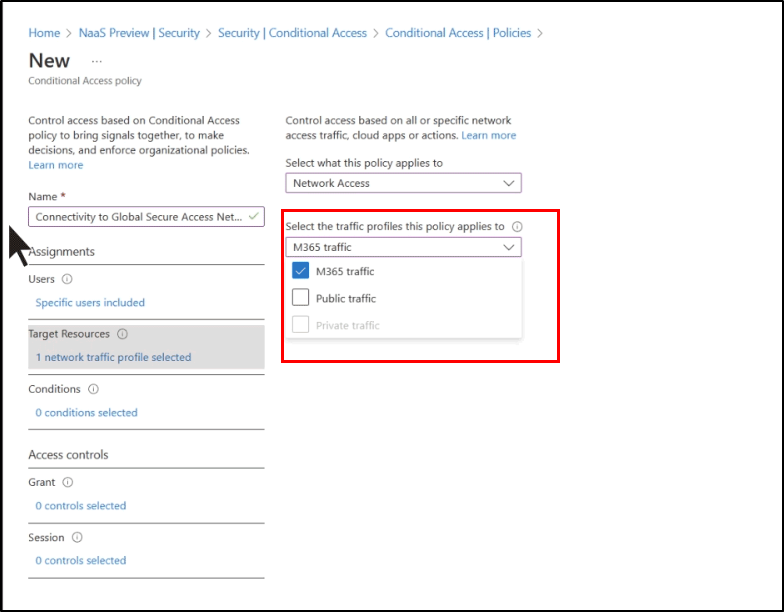
2. Prevent Data Leakage with Tenant Restrictions:
With tenant restriction v2, you can gain control over your user access to external tenants and applications. Simply configure an allow or block list of external applications using Tenant restriction v2 to safeguard against the looming threat of data exfiltration.
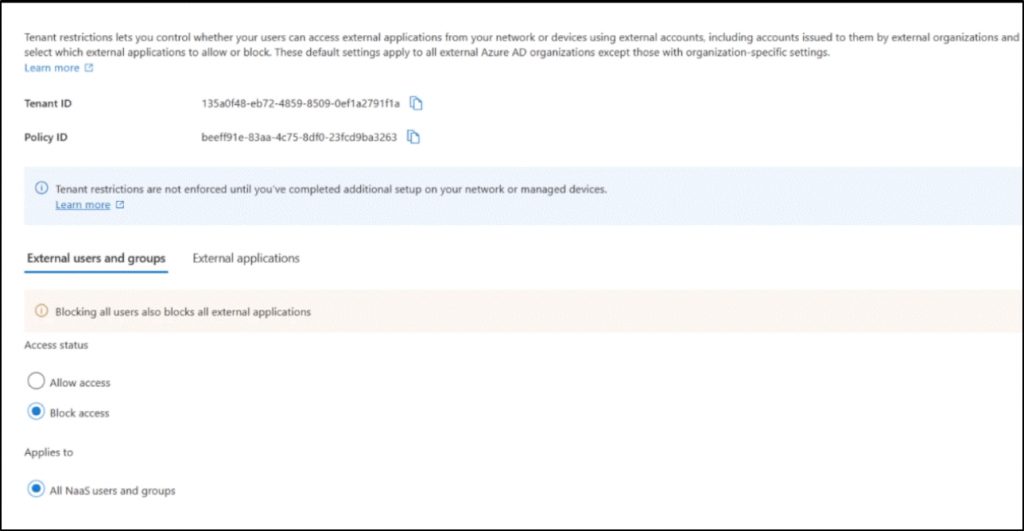
3. Preserve Original IPs of Microsoft 365 Users:
Traditional proxies, for example, VPNs, hide the user’s original IP address. This makes named location Conditional Access policies ineffective as they hinge on users’ IP addresses. However, Microsoft Entra Internet Access provides you with the original IPs of the users and enables the successful implementation of networking conditions in CA policies.
Coming to the best part, Microsoft has recently announced a key introductory feature “Web content filtering” for Microsoft Entra Internet Access. Let’s see about it in detail in the upcoming section.
Web Content Filtering for Microsoft Entra Internet Access
Web content filtering is a security feature integrated into Microsoft Entra Internet Access, offering granular internet access controls by considering web categories and FQDNs (Fully Qualified Domain Name).
This Microsoft 365 feature enables users to steer clear of malicious, unnecessary websites and domains by seamlessly integrating with Conditional Access policies. It achieves a balance by blocking access to risky domains while ensuring unrestricted access to necessary websites.
- Overview of how Web content filtering works
- Prerequisites to implement Web content filtering
- Limitations of Web content filtering configuration
- Configure Web content filtering for Microsoft Entra Internet Access
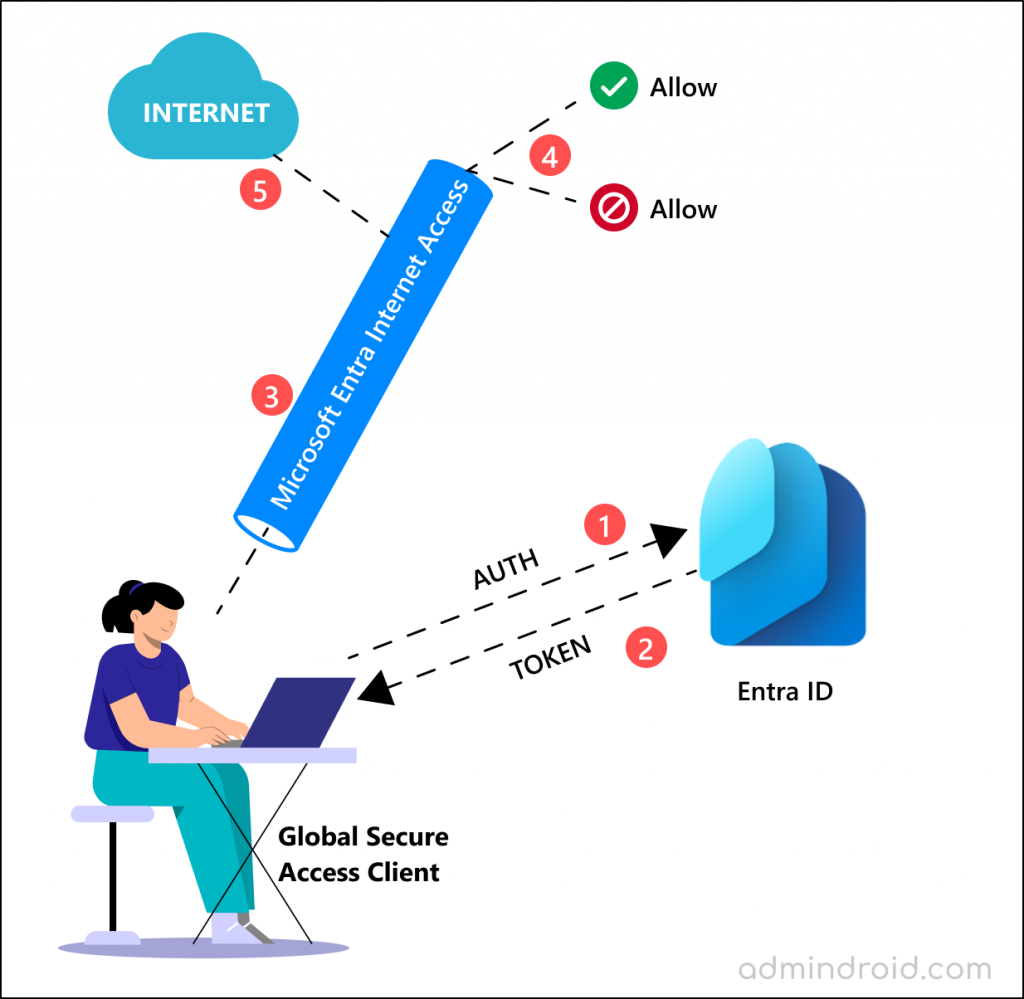
1. Overview of How Web Content Filtering Works
First, a Global Secure Access client gets installed on the end-user devices. When a user requests a website, the Global Secure Access client forwards the traffic to the Secure Service Edge (SSE) proxy. The SSE proxy then checks with the configured CA policy (with Web content filtering) and decides access to the website based on the configured allow/deny list.
To integrate Web content filtering in Microsoft Entra Conditional Access, several configurations need to be done. Let’s see that in detail in the below sections. But before that, make sure to know the prerequisites and limitations for configuring Web content filtering.
2. Prerequisites to Implement Web Content Filtering for Microsoft Entra Internet Access
- To manage Global Secure Access features like Web content filtering, you should be a Global Secure Access Administrator. To integrate filtering policies with Conditional Access, you should be a Conditional Access Administrator or Security Administrator.
- The most important step is that end users must install Global Secure Access clients on the devices.
- Admins need to disable the built-in DNS client on Chrome and Edge.
- It is essential to deactivate DNS over HTTPS (Secure DNS) to enforce traffic forwarding rules based on (FQDNs) in the traffic forwarding profile.
- The current preview does not support UDP traffic. If you intend to tunnel Exchange Online traffic, it is necessary to deactivate the QUIC protocol (443 UDP).
3. Limitations of Web Content Filtering for Microsoft Entra Internet Access
- Users are not notified about their blocks either from the client or browser.
- As of now, only the standard ports (Ports 80 and 443) are currently assumed for HTTP/S traffic.
- Traffic to “microsoft.com” is automatically routed to SSE as part of the Microsoft 365 access profile.
- Lack of support for IPv6 networks.
- Currently, Hyper-V isn’t supported by the client.
- OSI layer 3/4 (Network layer) filtering isn’t supported.
- Decrypting HTTPS for deeper inspection (TLS termination) is not yet available. It is under development.
- No support for URL-based filtering or categorization for HTTP/HTTPS traffic.
- You can create up to 100 Web content filtering policies and up to 1000 rules.
- Admins can create only 800 FQDNs and 265 security profiles.
- Admins can’t configure the internet traffic acquisition profiles for the client beyond the default TCP 80/443.
- The client traffic acquisition policy includes TCP ports 80/443.
Let’s enter the steps to configure Web content filtering for secure internet access for Microsoft 365 users.
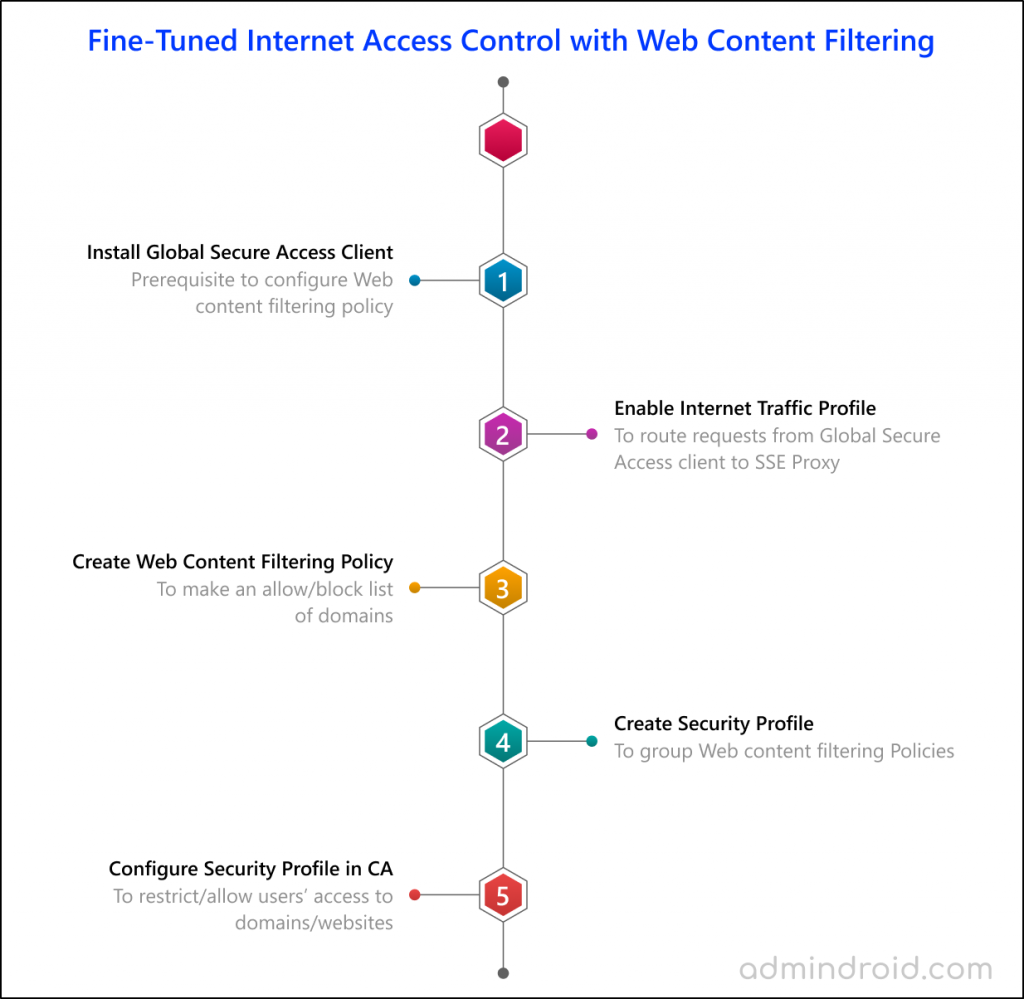
4. Configure Web Content Filtering for Microsoft Entra Internet Access
Think you want to restrict users’ access to the entertainment platform “www.hotstar.com“. To accomplish this, we delve into the process of creating a Web content filtering policy. Let’s explore the details of how to achieve this restriction.
- Install Global Secure Access client.
- Enable internet traffic forwarding in Microsoft Entra admin center.
- Create a Web content filtering policy in Microsoft Entra.
- Create security profiles to group Web content filtering policies.
- Configure security profile in Conditional Access policies.
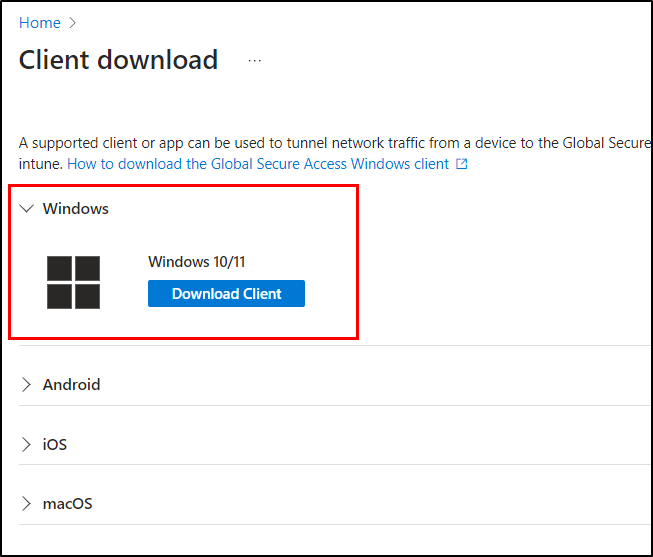
1. Install Global Secure Access client
To install the Global Secure Access Client, which is a prerequisite to configure Web content filtering, follow the below steps.
- Sign into the Microsoft Entra admin center as a Global Secure Access Administrator.
- Navigate to Global Secure Access (Preview) and select “Client download” from the Connect section.
- Now, click “Download client”, and Global secure Access will get downloaded.
Once done, move to install the Global Secure Access client.
2. Enable Internet Traffic Forwarding in Microsoft Entra Admin Center
In order to ensure that all internet traffic is routed to the SSE proxy, you must enable an internet traffic forwarding profile. This acts as a central checkpoint where security policies like Web content filtering are applied. To enable it, follow the steps here:
- Sign into the Microsoft Entra admin center.
- Scroll down to “Global Secure Access (Preview)” and click “Connect” from the dropdown.
- Then click Traffic forwarding and enable the Internet access profile by confirming the prompt.
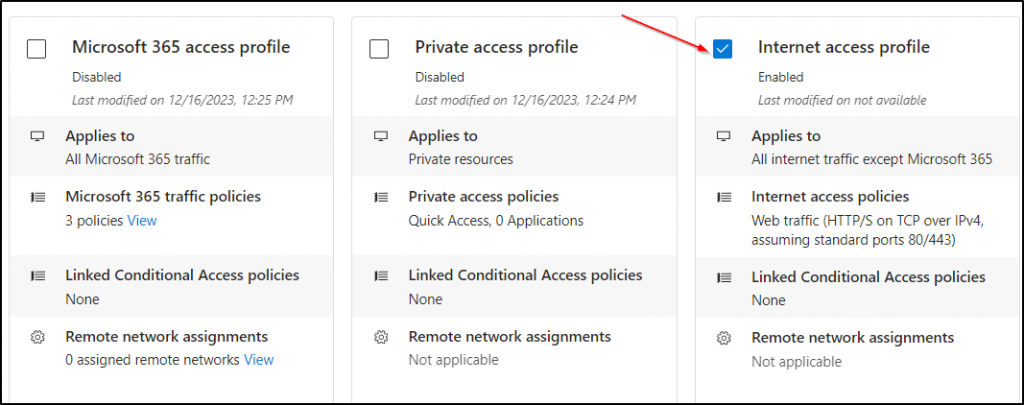
3. Create a Web Content Filtering Policy in Microsoft Entra
Here comes the hero – Web content filtering, the driving force behind deciding which domains /websites users can access and which ones they are blocked from. To configure a Web content filtering policy, follow the steps below.
- Navigate to Global Secure Access (Preview) from the Microsoft Entra admin center.
- Click “Web content filtering policies” from the Secure dropdown.
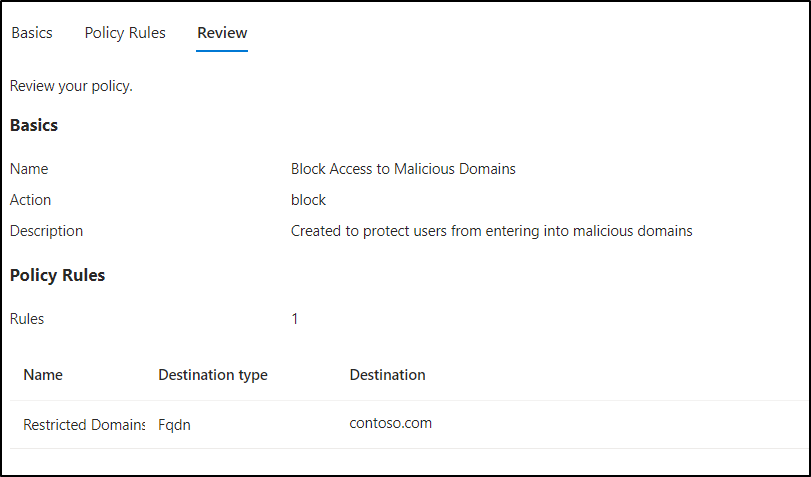
- Give suitable name and description for the policy and select “Block” in Action dropdown.
- Click “Next” and select +Add rule.
- Then, enter a name and select “webCategory” or “Fqdn” from the Destination type dropdown.
- If you select WebCategory, add the respective category from the options given below. Ex: Alcohol And Tobacco, Criminal Activity, and more.
- In case for fqdn, enter the domain in the box. Ex: fabrikam.com, contoso.com, amazon.com, etc.
Now, to block the hotstar.com domain, go ahead and select “Fqdn”, then simply type in hotstar.com.
- Click next to review the policy and finally select “Create policy”.
4. Create Security Profiles to Group Web Content Filtering Policies
The security profile serves as a centralized hub for grouping filtering policies, streamlining the management of our security measures. Once established, the security profile becomes a pivotal component that can be seamlessly configured within Conditional Access policies.
- Navigate to Global Secure Access (Preview) from the Microsoft Entra admin center.
- Click “Security profiles” from the Secure dropdown and click + Create profile.
- Give a suitable name and description for the security profile.
- And set the priority level. By default, it is set as “100”.
- We need to set the priority level in the security profile to determine the enforcement order. The values can range between 100(highest priority) to 65,000 (lowest priority).
- Once done, set the State as “Enabled” and click “Next”.
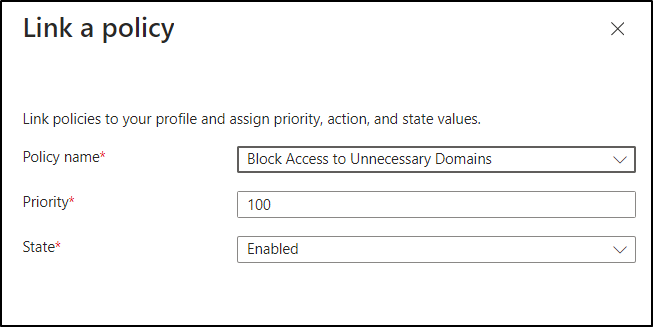
- Click “+ Link a policy” and then select Existing policy.
- Now, link the created Web content filtering policy in the Policy name option.
- After clicking Next, review the security profile and create a profile.
5. Configure Security Profile in Conditional Access Policies
The next crucial step is to integrate the configured security profile with the Conditional Access policy to block users’ access to hotstar.com. To do so, follow the steps below.
- First, sign in to the Microsoft Entra admin center.
- Then, navigate to the Protection drop-down box and select the “Conditional Access” option.
- Click on “+ Create new policy” to create a new policy and give a suitable name for your policy.
- Under Assignments, add the respective users/groups in the ‘Users’ blade.
- Click Select what this policy applies to in the target resources blade and select Global Secure Access (Preview)..
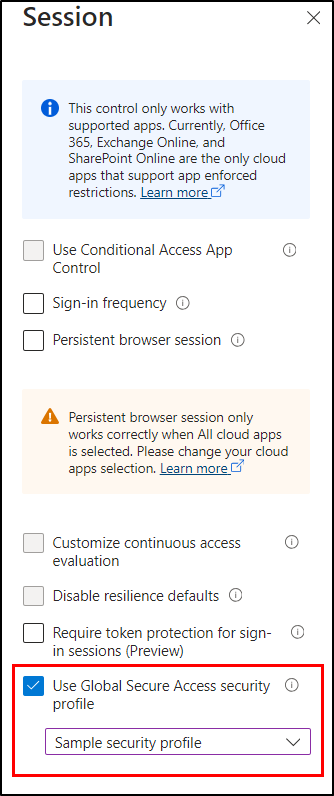
- Choose “Internet traffic” from the drop-down menu shown below.
- Under Session, enable Use Global Secure Access security profile to integrate our configured web link policy and choose the created security profile.
- Finally, enable the policy and proceed to create the policy.
Real-time Test: What Happens When a User Tries to Access Blocked Domain?
When a user initiates a website request, the Global Secure Access client directs the traffic to the Secure Service Edge (SSE) proxy. Subsequently, the SSE proxy verifies the request against the configured CA policy, specifically checking if the destination is hotstar.com. If the policy confirms a match, the user is then restricted from accessing the site.
This is how the respective user will be shown with, once they try to access hotstar.

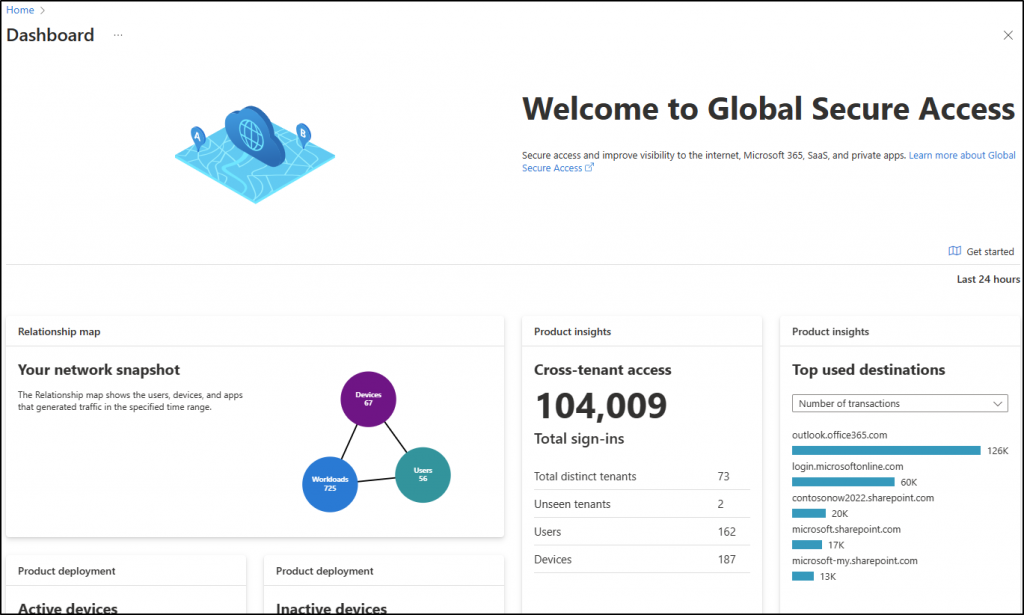
Global Secure Access Dashboard in Microsoft Entra Admin Center
You’ve got your web categories and Fqdn configurations all set up for allowing or blocking. But when does it really help is when you start to monitor the destinations users are hitting. To keep an eye on where users are venturing online and maintain control over their internet activities, head over to “Global Secure Access(preview) → Dashboard.”
There, you’ll find a Web category filtering card that lets you review all the destinations accessed by users. And that’s not all! You can also view cards with insights on
- Cross-tenant access
- Top-used destinations, and more.
It’s your one-stop control center for a secure and informed online environment.
Simplifying Secure Identities and Access Experiences with Entra Internet Access!
It’s our responsibility to defend against cyberattacks over the internet, instead of simply worrying about it. To achieve it, configure web content filtering for secure internet access for your users. This proactive approach not only enhances the Microsoft 365 security posture but also empowers users to navigate the internet confidently and freely.
Hope this blog brings you a good idea about the Microsoft Entra Internet Access. Furthermore, feel free to reach out to us in the comment section for further assistance.