Zero Trust has become one of the most preferred security approaches for modern Microsoft 365 organizations. At its core, Zero Trust is a security model that shifts from the old assumption of “trust once inside the network” to a modern principle of “never trust, always verify.”
Despite this clarity, many organizations still face challenges in knowing where to start or how to achieve Zero Trust effectively. To address this, Microsoft offers a free Zero Trust workshop that provides an assessment tool, a practical strategy, and a clear roadmap to adoption. Let’s take a closer look at what this workshop is all about.
An Overview of Microsoft’s Zero Trust Workshop
Zero Trust is built on the idea that threats can exist both inside and outside the network. As a result, every access request is treated as untrusted until verified, no matter where it comes from or what resources it tries to access. The Microsoft Zero Trust workshop helps organizations turn this principle into practice with a structured and simplified approach.
Built on insights from thousands of customer engagements, the workshop helps organizations assess their current environment. It then provides a clear, step-by-step roadmap to strengthen their overall security posture. Through this workshop, organizations can learn to apply the three core Zero Trust principles:
- Verify explicitly: Always authenticate and authorize based on identity, device health, location, and other risk factors.
- Use least privilege access: Provide only the minimum required permissions, using just-in-time and just-enough access to minimize the attack surface.
- Assume breach: Operate under the premise that breaches can and will occur. Design your Microsoft 365 environment to detect, respond, and remediate quickly. Reduce the blast radius and segment access to limit potential damage.
By embracing Zero Trust, organizations can build a stronger, more resilient security posture that adapts to cloud adoption, remote work, and increasingly sophisticated cyber threats.
How to Use Microsoft’s Zero Trust Plan
The Zero Trust workshop enables organizations to build a practical and structured strategy for adopting a strong Zero Trust security posture. This workshop typically involves two key steps:
1. Execute the Zero Trust Assessment Tool
Microsoft provides the Zero Trust assessment tool, a PowerShell cmdlet that assesses essential configurations of your organization to verify the security baseline. This check currently covers only two Zero Trust pillars, namely Identity and Devices. The Data, Network, Infrastructure, and Security Operations pillars are not included at this time.
If this is your first time accessing the Zero Trust assessment tool, execute the snippet below.
|
1 2 |
Install-Module ZeroTrustAssessment Invoke-ZTAssessment |
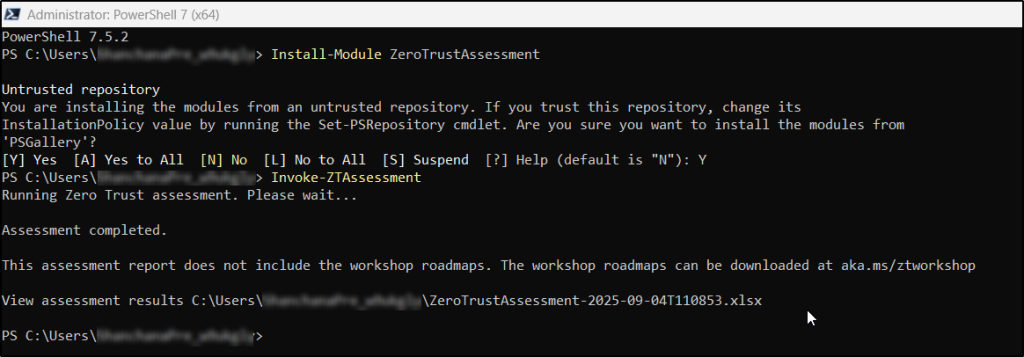
For all subsequent assessment runs, you can simply use Import-Module as shown.
|
1 2 |
Import-Module ZeroTrustAssessment Invoke-ZTAssessment |
This tool requires PowerShell 7 or higher and uses Microsoft Graph to read your tenant configuration. When executing the cmdlet, it is recommended to log in with a non-guest account from your Entra ID tenant.
Upon execution, it provides a file path leading to a spreadsheet with the assessment results for Identity and Devices in your tenant.
The results show all Zero Trust configurations, both completed and not started, along with details such as their risk level and user impact.
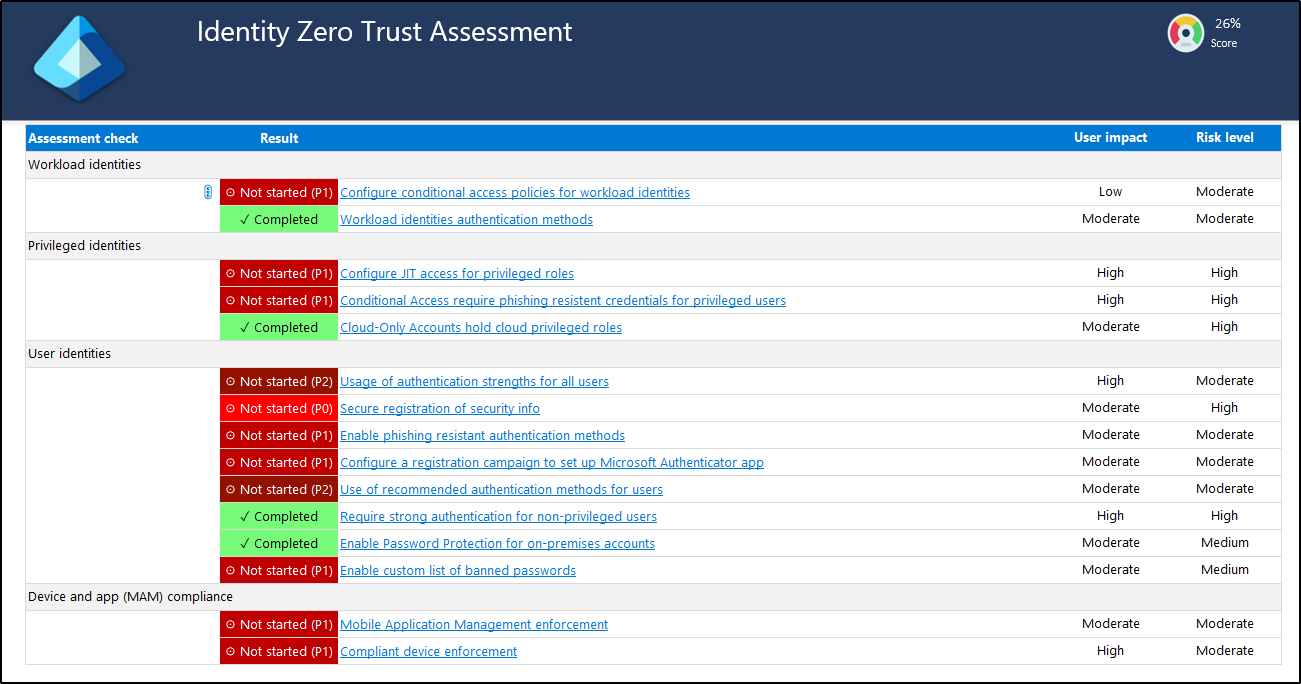
By clicking on each configuration, you can access information about the assessment, including the threats addressed, potential impact, and additional guidance. Identify the stakeholders for each pillar and notify them about the workshop and assessment results so they can review their relevant configurations.
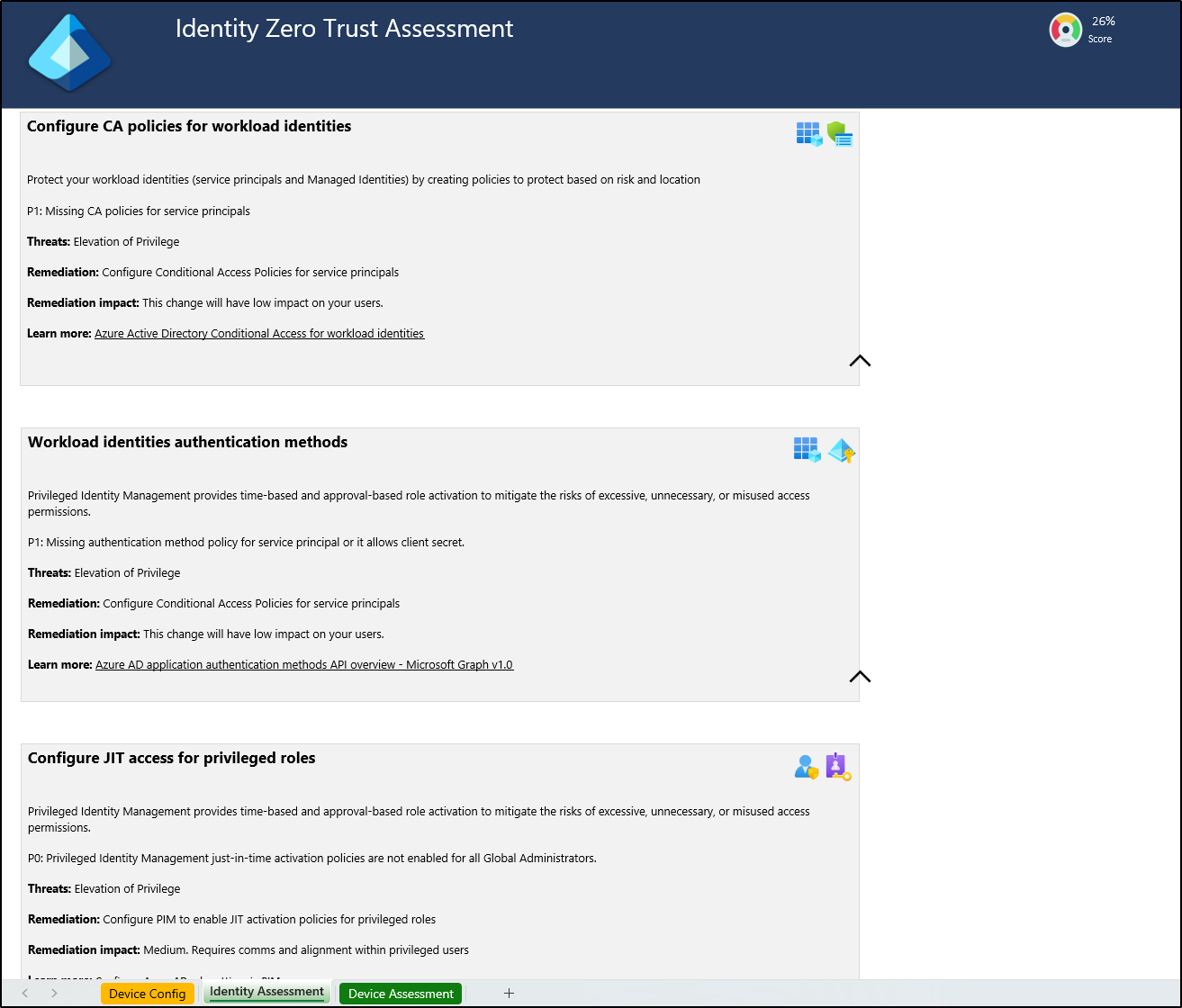
2. Run the Zero Trust Strategy Workshop
Download the workshop tool and conduct the workshop for each Zero Trust pillar with the relevant stakeholders. You can follow the suggested order or choose the pillar that aligns with your current focus area:
- Identity
- Devices
- Data
- Network
- Infrastructure
- Security Operations
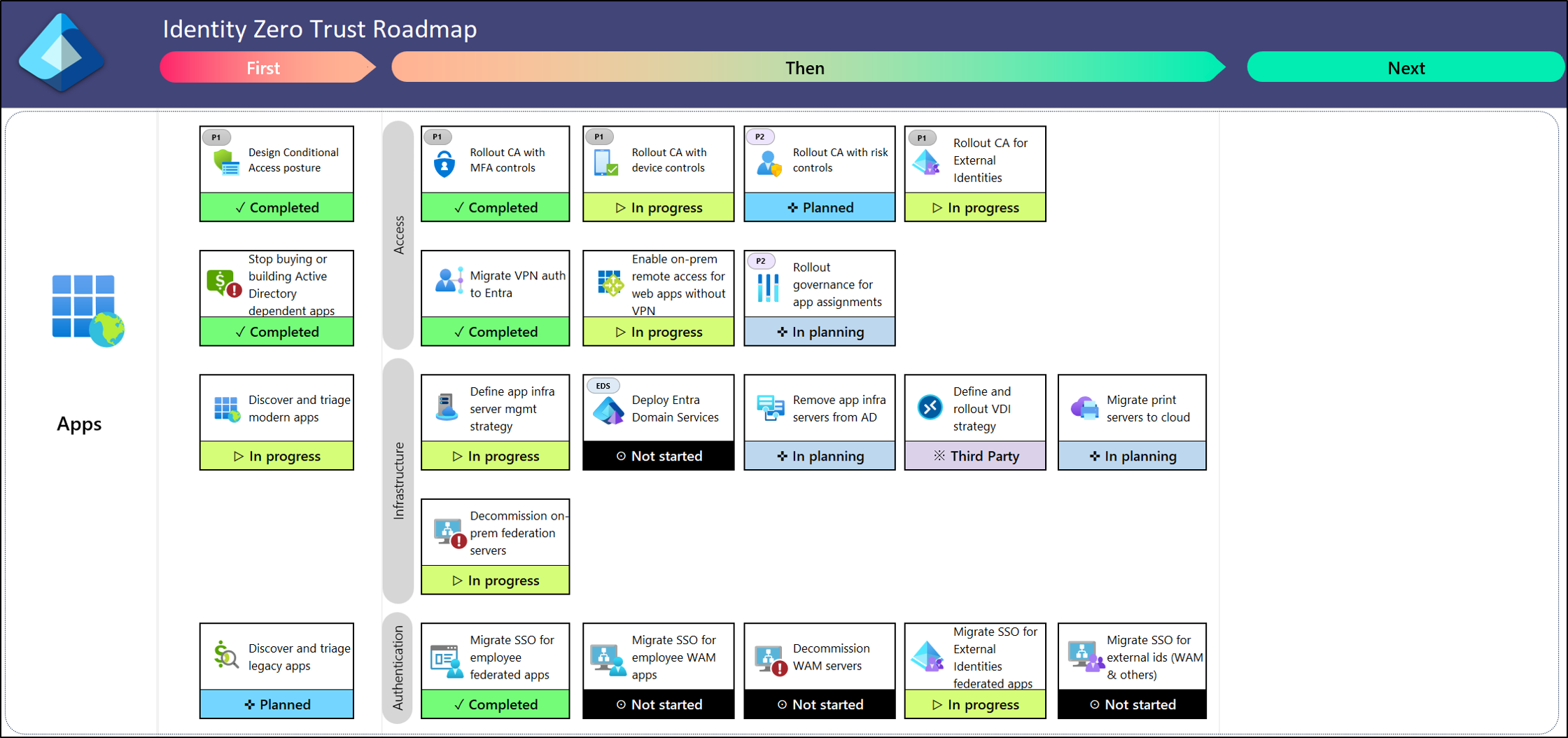
When you click the workshop tool, it generates a downloadable spreadsheet. On this spreadsheet, all Zero Trust roadmap items are neatly organized in horizontal swim lanes to show which actions should be carried out first, next, and later. Each item includes labels for implementation effort and user impact. Teams can click any item to access a detailed guide, follow the steps, and complete the actions.
Once done, they can update the status as In Planning, In Progress, Completed, Blocked, and so on. This allows cybersecurity teams and relevant stakeholders to track the progress of each essential configuration.
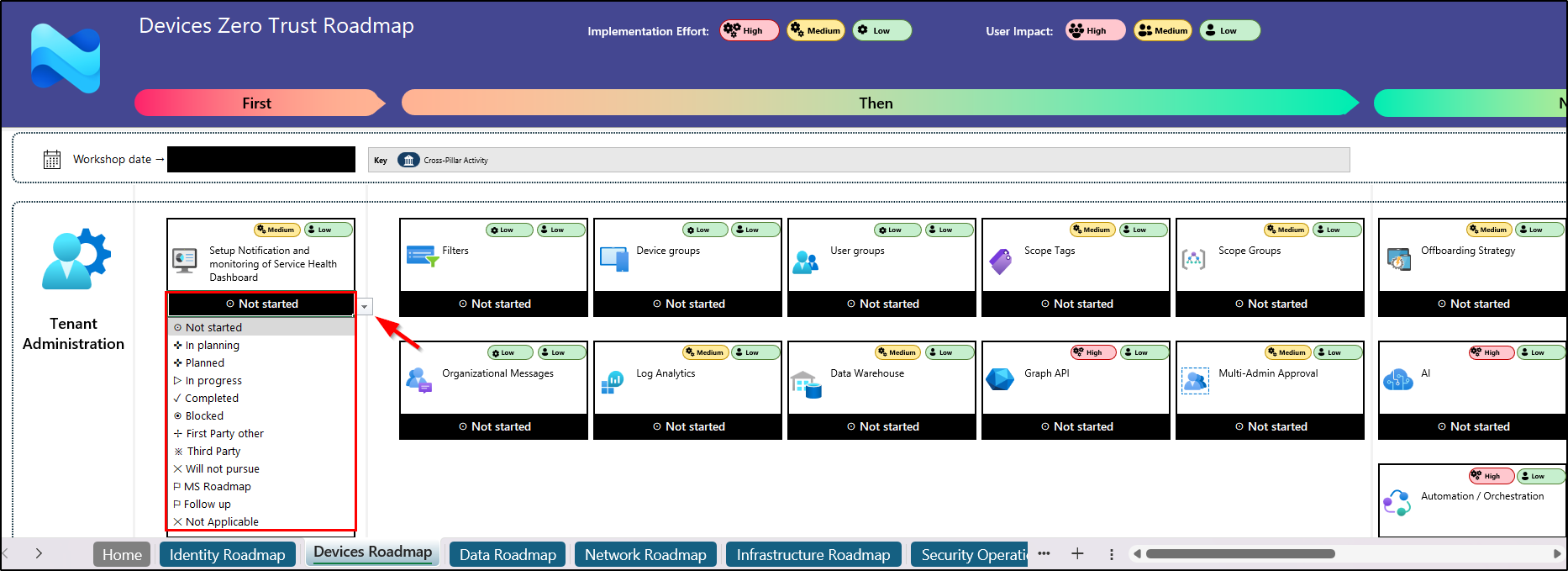
Then, they can identify areas that need improvement, adjust the security plan, and track progress with regular assessments every six months. Finally, the assessment and workshop results can be uploaded to a project management tool, such as ADO or JIRA, to maintain visibility and accountability.
Conclusion
The Microsoft Zero Trust workshop is a joint effort between customers and the Microsoft team to develop a 12–24 month Zero Trust Strategy and Deployment Plan. It helps organizations address the core pillars of Zero Trust architecture and make measurable progress toward implementation. Microsoft is continuously enhancing the workshop with tools and guidance to strengthen security posture and build a more resilient, modern environment.






