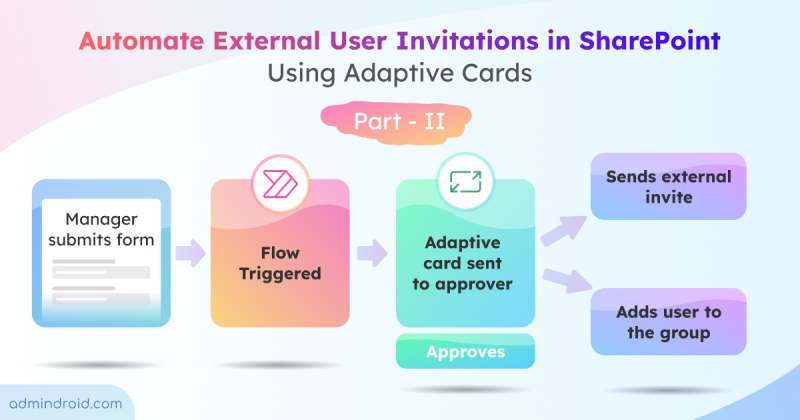
On Day 7 of Cybersecurity awareness month, learn to remove unused applications in MS Entra ID for protection against token theft attacks. Stay active for the upcoming blogs in our M365 Cybersecurity blog series.
Is your Microsoft 365 environment truly secure? Well, that’s good if you’ve already implemented measures like MFA and Conditional Access policies to enhance security. What if I say there are still possibilities hidden that cyberattacks can compromise your organization?
Surprisingly, it’s a real possibility, if you have unused applications in Microsoft Entra ID. Because unused apps are like entry cards for the attackers which help them effectively loot your sensitive information in Microsoft 365.
Therefore, Microsoft emphasizes the importance of routine audit and deleting of such applications via Entra ID recommendation: Remove unused applications (Which is currently in preview). If you have numerous unused applications in your organization, you should be the first to take note of this recommendation!
Let’s delve into how this recommendation enhances Microsoft 365 security and then implement the necessary steps to address it within your organization.
Attention Needed: Remove Unused Applications in Microsoft Entra ID
Admins have the capability to register applications in Azure AD, establish a trusted relationship that simplifies the authentication and authorization procedures for the applications to gain access to Microsoft 365 resources.
As there are numerous benefits that Azure AD app registrations bring to the table, it becomes abundantly clear that they deserve our utmost attention. Especially when it comes to managing unused apps in Microsoft Entra ID.
You might think why do the unused enterprise apps need our attention? Here are the reasons for why:
- Attacker’s loophole: When any unused apps are caught in the eyes of the attackers via social engineering or pass-the-cookie attack, they can employ these as entry points to illicitly obtain authentication tokens. This will result in unauthorized data access, service disruptions, and system compromise.
- Reduced Entra ID performance: If your tenant is crowded with numerous unused apps, then undoubtedly clutter will be around the corner. As clutter piles up, it will result in a drop in Azure AD performance.
- Lack of Effective Management: Sometimes, we end up persistently monitoring applications that have fallen out of active use! This situation arises due to a lack of visibility into their usage status, leading to significant time and effort consumption. Plus, this oversight may cause us to miss some critical applications.
- Efficient Cost Management: By removing unused/unutilized applications from your Azure AD, you can avoid paying for licenses that are essentially wasted on those applications.
To put an end card to the drawbacks associated with the unused apps, Microsoft advises “If an application is not needed, it should not be left inactive; it should be removed from Entra ID”.
When Do Microsoft 365 Admins Receive Notifications to Delete Unused Apps?
- First, Entra ID scans the Azure app registrations in your organization. If it identifies any apps that haven’t been used for the past 30 days, it takes a proactive approach by recommending the removal of those registered apps within MS Entra ID.
- Furthermore, if you’ve registered an app but haven’t put it to use, then Entra ID will recommend you delete those stale apps.
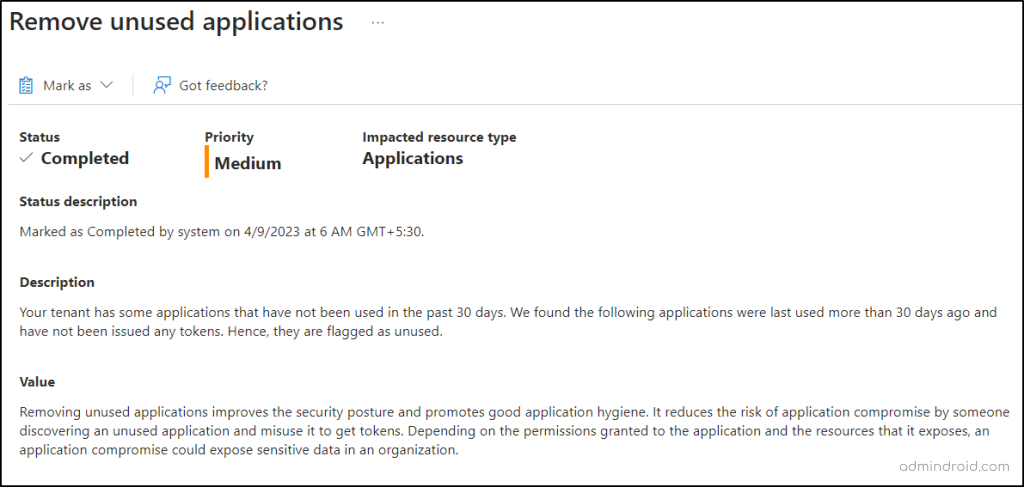
It’s not a thing to just to make a note! You should take further steps by removing unused registered applications from Entra ID. So, let’s see how to delete an unused application in Entra ID.
How to Remove Unused Applications in Microsoft Entra ID?
Now, let’s delve into the process of deleting unwanted apps in Entra ID. But wait! How do you recognize the unused apps alone among the plethora of applications? Well 🤔, no need to be concerned! Because Microsoft has streamlined the process!
Alongside the recommendation, you’re presented with a list of stale apps categorized under the “Impacted resource” section. This makes it a breeze to identify them and take the necessary steps to remove those stale apps from Azure app registration.
- Then, take note of the application name and ID of the identified unused apps.
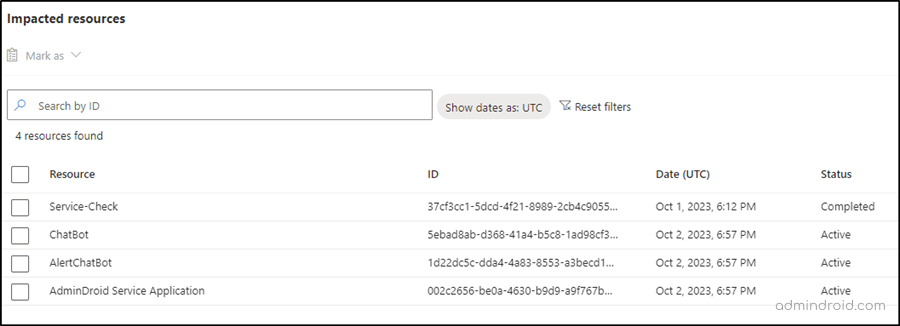
💡Tip: Furthermore, you can also see the recommendations on migrating apps and service principals to Microsoft Graph since Azure AD Graph is retiring. This helps ensure that you’re aware of any additional changes needed.
Point to Consider Before Deleting an Azure AD App Registration:
Before you get into cleaning up applications in Azure AD, it is essential to undertake a thorough review. So, here are some things to think about.
- Is the app still in use with the least usage? Make sure that the app is no longer needed before you delete it. You can use the Azure AD audit logs and application usage analytics to see if the app is being used at all and identify any unused devices, ensuring only unnecessary apps are removed.
- Are there any security concerns? If the app has access to sensitive data or resources, you should take steps to mitigate any security risks before you delete it. For example, you may want to revoke the app’s permissions or transfer the data to another app.
- Do you have a backup of the app’s configuration? If you need to restore the app in the future, you will need a backup of its configuration. You can export the app’s configuration from the Azure portal.
- Are any other apps or services dependent on the app? If other apps or services are dependent on the app, deleting it may cause them to stop working! So, before deleting an app, ensure no other apps are relying on it, and check that it doesn’t depend on another app either.
If there’s a possibility that you’ll require them, then consider retaining them and try to utilize those Azure AD apps within intervals of less than 30 days.
To remove unwanted/unused applications registered in Microsoft Entra ID, follow the navigation below.
Microsoft Entra admin Center→ Applications → App registrations → Select the respective unused app → Delete (Select the “Delete’ prior to ‘Endpoints’ in the top left corner) → Delete
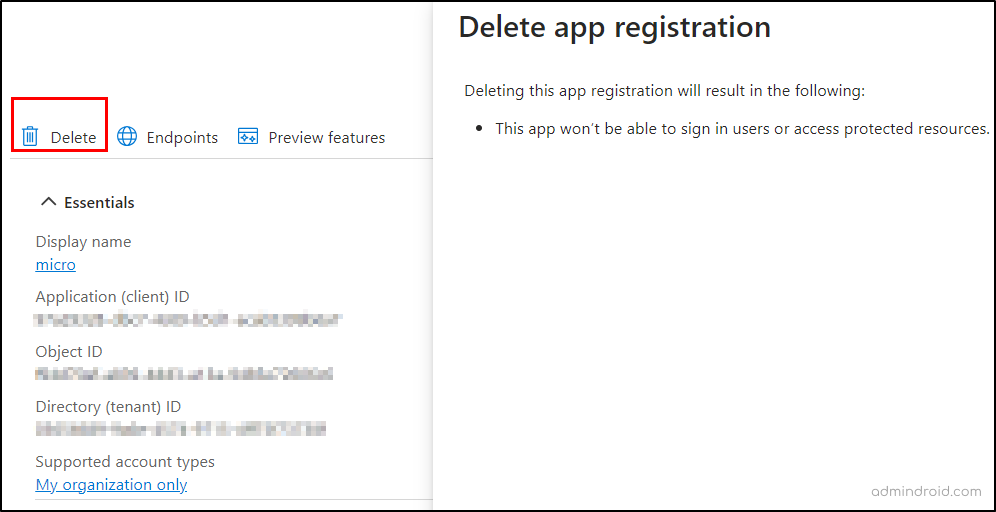
It is also possible to restore a deleted application registration within 30 days of its deletion from ‘Deleted applications’ tab.
It’s like giving your Azure AD a good app hygiene! Because It’s like giving your Azure AD a good app hygiene! Because clearing out those unused client apps not only revamps your directory but also helps you mitigate the risk of account takeover attacks. When you delete those unused apps, you’re essentially closing off potential entry points that attackers could exploit to break into your users’ accounts.
By the way, it’s cool to delete one or two applications via Microsoft Entra admin center, but when you are presented with bulk stale apps in Entra ID recommendation what would you do? 😥 Don’t worry! We’ve got a way! 😎
Tip: Similarly, you can consider removing unused credentials from apps to reduce attack surface.
Delete Bulk Azure AD Application Registrations Using PowerShell
If you have multiple unused apps to delete, then removing them one by one can undoubtedly become a headache and a time-consuming process! 😫 But you can leave this complex task in the hands of PowerShell.
To bulk delete stale devices in Entra ID, make use of the PowerShell script below. Before that,
- Make sure you connect to Microsoft Graph PowerShell with “Application.ReadWrite.All” scope.
- Also, you need to create a CSV file, with the header “ApplicationId” that contains the Object IDs of all the unused apps.
Sample CSV:
PowerShell Script:
|
1 |
$applications = Import-Csv –Path <CSV file path> #Replace with the respective file path foreach ($app in $applications) { $applicationId = $app."ApplicationId" Remove-MgApplication -ApplicationId $applicationId } |
Note: If you have encountered the “one or more error occurred” message while running the script, try it out again after deleting all the older module versions.
Must-know Limitation of Remove Unused Apps Recommendation
- You can’t set the time frame for Entra ID application usage that triggers this recommendation. For example, you won’t set the recommendation to raise when apps or not used for 50 days instead of 30.
- Currently the following apps are not shown under this recommendation, but we can expect this to be covered in future enhancements.
- Microsoft-owned applications
- Password single sign-on
- Linked single sign-on
- App proxy
- Add-in apps
- The unused apps processor may occasionally label newly created apps as unused. So, Microsoft is in the process of excluding apps created within the last 60 days from appearing on the list of unused apps.
Final Thoughts:
In closing, the “remove unused apps” recommendation within Azure AD is the linchpin of M365 application security. Timely action on this flag is pivotal, as it effectively minimizes potential security vulnerabilities linked to inactive applications.
At the end of the day, the goals are simple: Safety and Security
-Jodi Rell
I hope you understood the recommendation better via this blog. If you have any queries, drop them out in the comment section. Furthermore, we are some to have for you, just wait!