As we all know, Microsoft Entra ID empowers organizations with centralized identity and access management. However, amidst the convenience and efficiency it offers, Entra ID still carries the risk of human errors like accidental deletions, malicious attacks, etc. So, it becomes crucial for admins to learn the strategies for managing object deletions in Entra ID, ensuring critical data recovery whenever needed.
This blog post explores Microsoft 365 object deletion dynamics and outlines recovery methods in Microsoft 365.
What are Objects in Microsoft Entra?
Let’s begin with the basics. In Microsoft Entra ID, objects are like building blocks. They represent things like users, groups, contacts, etc. When you create a new user or contact, you’re basically creating a new object in the system. It’s a way to organize and manage different types of information within the Microsoft 365 environment.
Microsoft 365 Object Deletions
Object deletions in Entra ID are classified into soft deletion and hard deletion. Here’s the key distinction to understand.
Soft Deletion – When an object undergoes soft deletion, it will be moved to a recycle bin and remain accessible for 30 days. Thus, admins can retrieve the deleted objects within the period along with their original configuration and dependencies. Objects such as users, Microsoft 365 groups, application registrations, service principals, and administrative units support soft deletion.
Hard Deletion – In contrast, once an object undergoes hard deletion in Entra ID, it cannot be restored by any means. Therefore, hard deletions should be handled with caution.
Where to Track Object Deletions in Microsoft 365?
To track object deletions in Microsoft 365, you can use any one of the following methods.
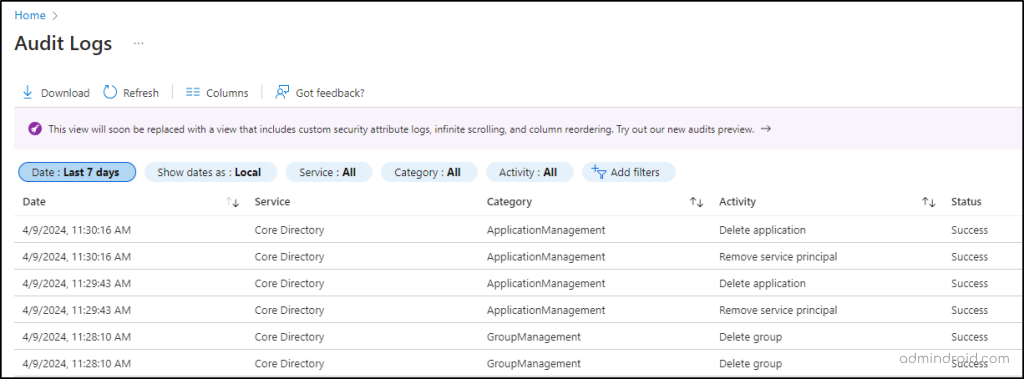
1. Keep Track of Object Deletions Using Microsoft Entra audit logs
The Microsoft Entra audit log contains information on all deleted operations performed in your tenant. These logs include three log types: Sign-in Logs, Audit Logs, and Provisioning Logs. Audit logs accurately record the history of all tasks executed within your tenant. Using ‘Add filters’ option, you can filter any one of the fields such as target, initiated by, user agent, and status.
2. Audit Entra ID Object Deletions Using Microsoft Graph
Microsoft Graph (MG) serves as a valuable tool for keeping tabs on object deletions within Microsoft Entra. With Graph Explorer, you can easily interact with Microsoft Graph APIs to get, add, remove, and modify data as needed.
3. Recover Objects from Deletions Using Microsoft Sentinel
Microsoft Sentinel is the alternative method for retrieving similar information via the unified audit log. The cost of Microsoft Sentinel depends on the amount of data you analyze and store in Azure Monitor Log Analytics workspace.
Recover Soft-deleted Objects in Microsoft 365
Not all objects within Microsoft Entra ID support soft deletion. Here’s a breakdown of soft deletion supported items and their respective recovery methods.
| Supported Objects | Recovery Methods |
| Users, Microsoft 365 Groups (not security and distribution groups), Application registrations | Microsoft Entra admin center or Microsoft Graph API |
| Service principals, Administrative units | Microsoft Graph API |
Note – Apart from the mentioned objects, other item types like distribution groups, Conditional Access policies, etc., support hard deletion. Once hard-deleted, items can only be re-created. Neither admins nor Microsoft can restore hard-deleted items.
If one of the objects like users, Microsoft 365 groups, etc., is inadvertently deleted or intentionally removed, it can disrupt workflows and compromise security. That’s why it is necessary to learn the Microsoft 365 recovery methods to mitigate risks associated with accidental deletions. Explore the process to restore essential objects effortlessly.
- Restore a deleted user in Microsoft 365
- Restore a deleted Microsoft 365 group
- Restore a deleted application registration
- Restore a deleted service principal
- Restore a deleted administrative unit
1. Restore a Deleted User in Microsoft 365
Soft-deleted users can be conveniently restored using the Entra ID portal or Microsoft Graph PowerShell.
To recover a deleted user in Microsoft Entra,
- Sign in to the Microsoft Entra admin center.
- Navigate to Identity –> Users –> Deleted users.
- Go through the list of deleted users and select the one you want to restore.
- Select Restore user.
To restore a deleted user using Microsoft Graph, run the Restore-MgDirectoryDeletedItem cmdlet and pass the account’s identifier.
Note– To permanently delete a user from your organization, select the desired user and click on the “Delete permanently” option. For hard deletions using MS Graph, execute the Remove-MgDirectoryDeletedItem cmdlet and pass the respective object identifier in Microsoft Graph PowerShell.
Bulk Restore Deleted Users in Microsoft Entra
- To bulk restore deleted users in Entra ID, on the same Deleted users page, select Bulk restore option. You can either directly upload a valid CSV file or go with CSV template.
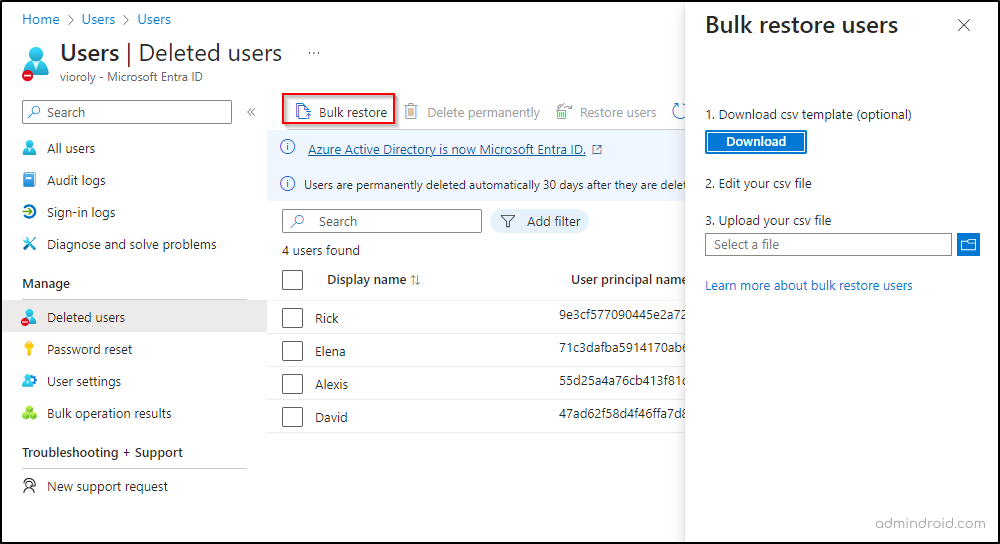
- Then, upload your filled CSV file and click “Submit.”
- Wait for validation to complete. If successful, you’ll see a confirmation message. If there are errors, fix them before proceeding.
- Once validated, click “Submit” again to start the bulk restore operation.
- After the operation is complete, you’ll receive a notification confirming the success of the bulk restore.
To restore bulk users using MS Graph, create a CSV file with the list of deleted user IDs. Then, execute the forthcoming cmdlet.
|
1 |
Import-Csv -Path <FileLocation> | Foreach {Restore-MgDirectoryDeletedItem -DirectoryObjectId <UserID>} |
2. Restore a Deleted Microsoft 365 Group
Recovering deleted Microsoft 365 groups in Entra ID can be easily done. However, it doesn’t extend to security groups or distribution groups.
To recover a deleted Microsoft 365 group in Entra admin center,
- Navigate to Identity –> Groups –> Deleted groups.
Choose the Microsoft 365 group you want to restore and click Restore Group.
To restore a deleted Microsoft 365 Group using MS Graph, execute the following cmdlet along with the group identifier.
|
1 |
Restore-MgDirectoryDeletedItem -DirectoryObjectId $directoryObjectId |
Note – You can also permanently delete a Microsoft 365 group by selecting the “Delete permanently” option.
Bulk Restore Deleted Microsoft 365 Groups
Prepare a CSV file listing the group IDs to restore multiple groups using MS Graph. Following that, proceed to run the following cmdlet.
|
1 2 3 |
Import-Csv -Path <FileLocation> | Foreach {Restore-MgDirectoryDeletedItem -DirectoryObjectId <GroupID>} |
3. Restore a Deleted Application Registration
Applications have two objects such as application registration and service principles.
To recover a deleted application registration from Microsoft Entra,
- Navigate to Identity –> Applications –> App registrations.
Now, click on Deleted applications to review the removed application registrations. Once you choose the application registration you want to restore, select Restore app registration.
To restore a deleted application registration using Microsoft Graph, use the cmdlet below and pass the application’s identifier.
|
1 |
Restore-MgDirectoryDeletedItem cmdlet -DirectoryObjectId $directoryObjectId |
Note – If you choose “Delete permanently,” option the selected application will be hard deleted and can’t be retrieved.
Bulk Restoration of Deleted Application Registrations
Prior to initiating the restoration of bulk applications via MS Graph, compile a CSV file listing their user IDs.
|
1 |
Import-Csv -Path <FileLocation> | Foreach {Restore-MgDirectoryDeletedItem -DirectoryObjectId <ApplicationID>} |
4. Restore a Deleted Service Principal
To restore a deleted application or service principal, you must be an application administrator, a cloud application administrator, or a hybrid identity administrator.
Firstly, connect to MS Graph PowerShell with the corresponding scope.
|
1 |
Connect-MgGraph –Scopes "Application.ReadWrite.All" |
Then, run the following cmdlet by replacing the ‘DirectoryObjectID’ with service principal ID.
|
1 |
Restore-MgDirectoryDeletedItem -DirectoryObjectId $directoryObjectId |
Bulk Restoration of Deleted Service Principals
To bulk restore deleted service prinicpals using MS Graph, execute the following cmdlet by listing service principals IDs in a CSV file.
|
1 |
Import-Csv -Path <FileLocation> | Foreach {Restore-MgDirectoryDeletedItem -DirectoryObjectId <ServicePrincipalID>} |
Note – For hard deleting service principals using MS Graph, execute the Remove-MgDirectoryDeletedItem cmdlet and pass the respective object identifier.
5. Restore a Deleted Administrative Unit
To recover a deleted administrative unit, you must use Microsoft Graph.
Connect to MS Graph PowerShell with the required scope.
|
1 |
Connect-MgGraph –Scopes "AdministrativeUnit.ReadWrite.All" |
Then, run the following cmdlet by replacing the ‘DirectoryObjectID’ with the respective administrative unit.
|
1 |
Restore-MgDirectoryDeletedItem -DirectoryObjectId $directoryObjectId |
Bulk Restoration of Deleted Administrative Units
If you need to restore bulk administrative units with MS Graph, start by putting their IDs in a CSV file. Then, just run the upcoming command to get them back.
|
1 |
Import-Csv –Path <FileLocation> | Foreach {Restore-MgDirectoryDeletedItem -DirectoryObjectId <AdministrativeUnitID>} |
Note– Hard Deletion is not possible for Application Registrations.
How to Prevent Unwanted Hard Deletions?
To minimize the risk of unwanted hard deletions, organizations should implement proactive measures. Some of the essential strategies include,
- Regularly reviewing soft-deleted items
- Defining specific criteria for restoration
- Delegate roles for evaluation and restoration tasks
Additionally, educating administrators and users on deletion best practices can help mitigate accidental deletions.
In conclusion, managing Microsoft 365 object deletions in Entra ID demands a proactive approach, careful monitoring, and following best practices. By adopting these strategies, organizations can confidently navigate object deletions in Entra ID with resilience. Feel free to reach us in the comment section for any queries.