On Day 8 of Cybersecurity awareness month, learn to migrate apps to Microsoft Entra ID for enhanced app security. Stay tuned for the upcoming blogs in M365 Cybersecurity blog series.
Do you have applications integrated with AD FS? Then, it’s almost like sending out an invitation to cyber attackers! 😲How so, you ask? And here, the issue lies in AD FS lacking advanced security features, which creates a wide-open door for those malicious actors.
Then, you might be wondering, “Where can we securely manage all our applications?” Well, fear not! Because we have the perfect solution: Move applications to Microsoft Entra ID (Azure Active Directory), the one that elevates your defenses and safeguards your sensitive data from potential attacks.
In fact, it’s not just us who think so; even Microsoft recommends it via Entra ID recommendation: Migrate from AD FS to MS Entra ID. You won’t be sorry, as it comes packed with improved security features, simplified identity management features, and more! Definitely, it’ll be a smart move to ensure your apps and data stay safe.
So, let’s delve into this blog to know why it is necessary to make the shift and the steps to migrate to Entra ID in detail.
Move Apps from AD FS to Microsoft Entra ID
Active Directory Federated Services (AD FS) is a Windows server OS feature that facilitates Single Sign-On (SSO) access for users across all applications. However, it can be prone to attacks because it lags in modern authentication, granular access control, and more, which can aid attackers in carrying out malicious actions.
This puts the onus on administrators to manage applications effectively and implement robust security measures effectively to protect against malicious actions.
Given these concerns, Microsoft strongly recommends the transition from Active Directory Federation Services (AD FS) to Azure Active Directory (Azure AD).
Overall, Azure AD is a more modern and secure IAM solution than AD FS. This move not only addresses the security gaps but also unlocks a plethora of advanced features within Azure AD, offering a robust and secure environment for your organization’s authentication needs. A few of the advanced security features are:
- MFA number matching and geographic location display
- Conditional access authentication strength
- Suspicious activity reporting
- User consent to applications
- B2B and B2C collaboration
- Privileged access management
No need to worry if that’s not enough! Below, we’ve showcased the importance of transitioning to Azure Active Directory.
Bundle of Benefits: Manage Apps in Microsoft Entra ID
For a better understanding of the necessity of Migrating to Microsoft Entra ID, we’ve outlined the key shortcomings of ADFS. Following that, we have illustrated how Azure AD effectively addresses these issues. Let’s delve into it!
The Drawbacks of Maintaining Apps in AD FS
- Security vulnerabilities: AD FS has been known to have security vulnerabilities in the past. These vulnerabilities could be exploited by attackers to gain access to your applications and data. For example, in 2017, a vulnerability in AD FS was exploited by attackers to steal passwords from users.
- Lack of access control: AD FS complicates access restrictions for specific user groups or roles, based on factors such as group memberships, device types, or geographical locations. This fine-grain control limitation can pose unauthorized access to sensitive resources.
- Limited Support for Old Applications: AD FS may not seamlessly authenticate certain “older” web applications, especially those that rely on outdated authentication protocols.
- Increased cost: Organizations using AD FS need to maintain and manage on-premises servers, which can significantly increase maintenance costs.
But don’t fret! Because Microsoft Entra ID (Azure AD) bridges the limitations with its versatile features.
Why is Azure AD the Number 1 Choice for Application Security?
Azure AD stands first over AD FS for the following reasons:
- Reduced Credential-Based Attacks: Unauthorized access to AD FS server can lead to compromised user credentials, granting attackers illicit entry to various resources. But this can be avoided with Azure AD advanced security features.
- Simplified Identity Management: Azure AD simplifies identity management by providing a single identity platform that works across on-premises and cloud environments.
- B2B and B2C Collaboration: Azure AD supports secure collaboration with external partners and customers through Azure AD B2B and Azure AD B2C features.
- Automation Ability: Azure AD provides automated app provisioning making it easier to manage user lifecycles in cloud SaaS apps.
- Cost Savings and Efficiency: Azure AD saves on cost spending for setting up AD FS, as it comes along with the M365 subscription.
Really a beneficial one, right? The next question that might come to your mind is when will this recommendation hit your tenant? If you have all the apps integrated in AD FS, this recommendation will prominently appear in your tenant. Also, Microsoft itself will provide actionable steps for moving your apps from AD FS (Active Directory Federation Services) to the enhanced security and convenience of Entra ID. Let’s delve into these action plans in detail below.
How to Migrate Apps from AD FS to Microsoft Entra ID?
To address this Entra ID recommendation, admins can follow the steps outlined below to transition from AD FS to Azure Active Directory (AAD), effectively resolving it.
- Install Azure AD Connect Heath on AD FS Server for detailed application analytics
- Review AD FS application report in Microsoft Entra ID
- Migrate application authentication to Azure AD
1. Install Entra AD Connect Heath on the AD FS Server
To kickstart the process of addressing the Entra ID recommendation, the first step is to install Entra ID Connect Health. Because the subsequent step in the process involves reviewing the AD FS application activity report, and to access that report, the installation of Azure AD Connect Health is a must.
Additionally, it’s important to note that before proceeding with the installation, you should verify and meet the hardware prerequisites.
2. Review AD FS application report in Microsoft Entra ID
The AD FS application report is an essential tool for anyone who is planning to migrate their applications from AD FS to Microsoft Entra ID. AD FS application report seems useful for the following reasons.
- Conduct a Readiness Check: This check offers a comprehensive list of all AD FS applications along with their migration readiness status. This information can help you identify applications that are ready to be migrated, as well as applications that may require additional configuration or testing before they can be migrated.
- Issue Identification: By closely examining this report, you can proactively detect and address potential issues that might arise during migration.
- Issue Resolution with Guidelines: The report service automatically runs tests and provides migration status updates. If any configuration conflicts arise, you receive specific guidance on making the application compatible for migration. This ensures a smoother transition process.
The report is updated regularly, so it is important to review the report before each phase of the migration process. This will help you to stay informed of any changes to the migration readiness of your applications. And now, to access the AD FS application activity report, follow this navigation below.
Note: you need to have one of the following roles to access the AD FS report: Global administrator, report reader, security reader, application administrator, or cloud application administrator.
Microsoft Entra admin center → Identity → Applications → Enterprise applications → Activity → Usage & Insights → AD FS application activity.
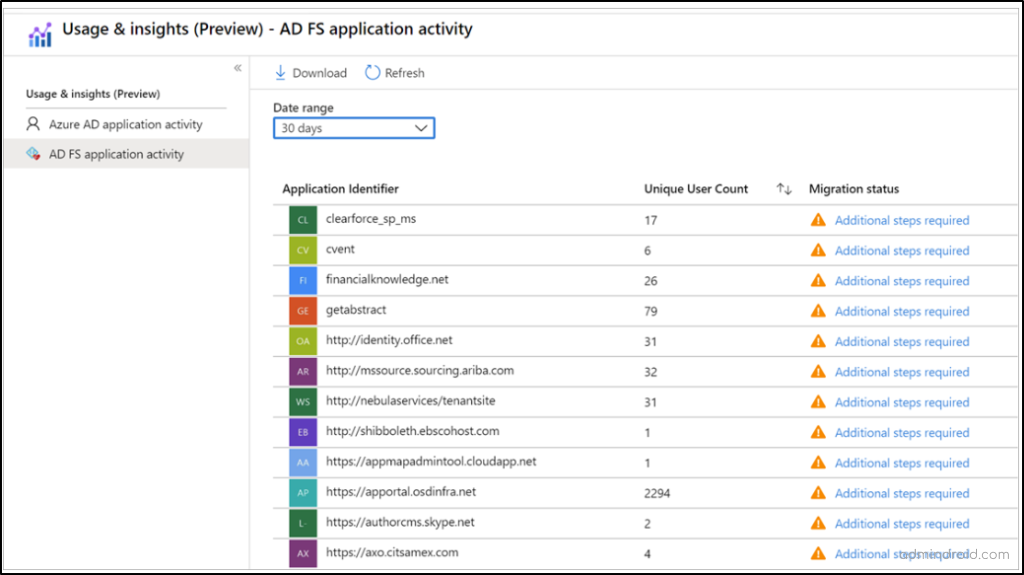
You will be shown with any of the three below migration status.
- Ready to Migrate: This status indicates that the application is fully supported for migration to Azure AD. It serves as a green signal, signifying that the app can be migrated without significant issues.
- Needs Review: Applications marked with this status require further attention. You should review their settings and configurations to identify any potential issues or adjustments needed for a successful migration.
- Additional Steps Required: This status indicates that some of the application’s settings are not supported by Azure AD. As a result, it cannot be migrated to Azure AD. Further steps or modifications may be necessary to make the application compatible with Azure AD.
Overall, the insights provided by this report can help you to make informed decisions about which applications can be successfully migrated to Entra ID, ensuring a smoother transition.
3. Migrate Application Authentication to Microsoft Entra ID
As the next step, you need to plan the migration process to cloud authentication. It is important to note that the Microsoft 365 apps in AD FS may use modern and legacy protocols for authentication.
- Therefore, it’s advisable to start the migration process by focusing on apps that use modern authentication protocols (SAML and OpenID Connect) only! To seamlessly enable these applications to authenticate through Azure AD, you have two primary options. You can either use built-in connectors from the Azure app gallery or register a custom application directly within Azure AD.
- Then, you can integrate apps with legacy authentication protocol using the application proxy or secure hybrid access.
Tip: Before migrating your configurations to production, it is highly advisable to conduct comprehensive testing of the configurations within a test tenant environment. This testing phase is crucial because it allows you to identify and address any potential issues or challenges associated with migration.
By rectifying these problems in the test environment, you can ensure a smoother transition when migrating to your production Entra environment.
Switch Users from Federated to Cloud Authentications
Security doesn’t hinge on app authentications alone; it also lies in user authentications too! So, once you have successfully migrated your applications to Azure AD, you can consider migrating your users’ authentication from federated to cloud authentication for added flexibility and management ease. To achieve this, make sure you have the following prerequisites first.
A) Prerequisites:
1. Install Entra ID Connect: You should install Entra ID Connect on your AD FS server. Because Entra Connect application is used to sync users to Microsoft Entra ID.
2. Review Federation Settings: You ought to review the current federation settings using the below cmdlet.
|
1 |
Get-MgDomainFederationConfiguration –DomainID <DomainID> |
3. Backup Federation Settings: You need to take the backup copy of your federation settings using the AD FS Rapid Restore Tool. Also, you can use the below PowerShell cmdlet to export Microsoft 365 Identity Platform relying party trust and any associated custom claim rules associated with the domain.
|
1 |
(Get-AdfsRelyingPartyTrust -Name "Microsoft Office 365 Identity Platform") | Export-CliXML "<FilePath>" |
B) Deploy Cloud Authentication:
Once done with the prerequisites, you can deploy cloud authentication either using Password Hash Synchronization or Pass-Through Authentication (PTA).
Password Hash Synchronization: Synchronizes password hashes from on-premises Active Directory to Azure AD for seamless SSO
Pass- Through Authentication: Validates user passwords directly against on-premises Active Directory.
By the way, you can use PTA and PHS sign-in methods in two different ways.
1. Migrate with Staged Rollout in Azure AD
2. Switch to Cloud User Authentication Without Staged Rollout
Migrate to Cloud Authentication Using Staged Rollout in Azure AD
It’s advisable to begin by testing Azure AD cloud authentication methods with a subset of users before implementing these changes across your entire users. To achieve this, you can make of the staged rollout feature.
The staged rollout enabling you to selectively evaluate cloud authentication methods with a specific group of users.
In this approach, you can gradually migrate users to cloud authentication. This method is suitable for organizations that prefer a phased transition.
Actual Working: Here, you can make use of the staged rollout feature to test out the cloud authentication methods PHS and PTS. So, the selected group members alone undergo cloud authentication, while others are authenticated via AD FS.
To leverage the staged rollout feature for any of the mentioned cloud authentication methods, you can follow the steps outlined below.
Note: To use this staged rollout feature, you should be a Hybrid Identity Administrator of your tenant.
Step 1: Enable Staged Rollout
- Navigate to Azure portal → Microsoft Entra ID → Azure AD Connect.
- Under the Staged rollout of cloud authentication, click the “Enable staged rollout for managed sign-in” link.
Step 2: Choose Authentication Methods
- Now enable either Password Hash Synchronization (PHS) or Pass-Through Authentication (PTA). Also, after enabling any one of them, you can enable SSO if you need to.
- Then, include groups as part of the features you’ve chosen.
Step 3: Convert Domains to Cloud Identity
- Until this step, federated authentication is still applicable for your domains. So, you need to convert each of your domains from federated to cloud identity. To convert it, follow the steps below.
- Connect to Microsoft Graph PowerShell with the following scopes Domain.ReadWrite.All”, “Directory.AccessAsUser.All”.
- Execute the following cmdlet, replacing “<domain name>” with the respective domain name:
|
1 |
Update-MgDomain -DomainId <domain name> -AuthenticationType "Managed" |
By following these steps, you can safely test cloud authentication methods like PTA or PHS with a select group of users while maintaining federated authentication for others. This staged approach ensures a smooth transition and allows for thorough testing before applying changes company-wide.
Deploy Cloud User Authentication without Staged Rollout
If you prefer not to test it with specific users, you can skip the staged rollout feature. Instead employ Azure AD Connect or Azure AD Connect with PowerShell as alternative methods to deploy cloud user authentication without the need for staged rollout.
Once done with the migration, the tenant is now configured to utilize the new sign-in method instead of federated authentication & users will no longer be redirected to AD FS.
Closing lines
Thus, don’t take chances with your organization’s security. Make the smart choice today—migrate to Microsoft Entra ID (Azure AD) and enhance your Microsoft365 security. Your data deserves the best protection available! You can also use the generally available migration tool. It provides you a guided experience to migrate ADFS relying party applications from ADFS to Microsoft Entra ID. You can easily identify which applications are capable of migration and it even suggests how to resolve issues. With less manual intervention and minimized downtime, you can migrate apps to Entra ID with this tool.
I hope this blog brings you the importance of migrating apps from AD FS to AAD. Furthermore, feel free to reach us in the comment section for any assistance needed. By the way, wait for the next Azure AD recommendations soon!