On Day 15 of Cybersecurity Awareness Month, learn how to secure your Active Directory environment with best practices. Stay tuned for upcoming blogs in our Cybersecurity Awareness Series.
Active Directory sits at the core of enterprise identity and access management, controlling user permissions and access to critical resources. Even a minor vulnerability, like over-permissioned accounts or weak credentials, can give attackers an entry point.
Real-world breaches like SolarWinds and other ransomware attacks have shown how compromised AD user accounts can disrupt entire organizations. These incidents highlight the importance of securing Active Directory against lateral movement and privilege escalation.
“Securing Active Directory isn’t just a precaution; it’s a necessity.”
So, without further delay, let’s dive into the key Active Directory security best practices to reduce vulnerabilities and keep your organization resilient against evolving threats.
Top 22 Best Practices for Active Directory Security
Strengthen Active Directory and block attackers by implementing these 22 key security best practices:
Password & Authentication Security
- Enforce strong password policies
- Apply fine-grained password policies
- Configure account lockout settings
Identity Hygiene & Account Cleanup
- Clean up inactive user accounts
- Remove stale computer accounts
- Secure service accounts with managed identities
User Access Control
- Disable guest access
- Restrict anonymous access
- Configure user rights assignments
- Disable Remote PowerShell access
Privileged Account Management
- Protect built-in administrator accounts
- Disable local administrator accounts
- Use separate admin and regular user accounts
- Limit privileged group usage
- Implement tiered administration model
- Follow least privilege using RBAC
Auditing & Monitoring
Maintenance, Patch, & Recovery
- Patch domain controllers regularly
- Reset the Krbtgt account password
- Use secure admin workstations (SAW)
- Perform and test Active Directory backups
Password & Authentication Security
1. Enforce Strong Password Policies in Active Directory
Regular password changes are intended to improve security or meet compliance, but it can backfire if users pick weak or repetitive passwords. Simple or reused passwords make it easy for attackers to gain access through brute-force or credential-stuffing attacks, making account compromise a top risk in Active Directory.
To strengthen protection, configure strong password policies through Group Policy. Set a minimum password length of at least 14 characters, enforce complexity requirements (mix of uppercase, lowercase, numbers, and symbols), and maintain a password history of 24 previous passwords to prevent reuse. Also, disable reversible encryption to ensure credentials are securely stored.
Enforcing strong password policies makes it harder for attackers to crack passwords and enhances your AD ransomware defense.
2. Configure Fine-Grained Password Policies for Active Directory Users
Weak or uniform password policies across all users can leave privileged accounts exposed to credential-based attacks. When administrators and regular users share the same password complexity and expiration settings, sensitive accounts remain vulnerable for longer periods.
To address this, you can configure Fine-Grained Password Policies (FGPP) in Active Directory. FGPP lets you apply different password requirements to specific users or groups within the same domain—enforcing stricter rules for privileged accounts while keeping password management simpler for standard users. This targeted approach enhances identity protection and strengthens overall security.
3. Configure AD Account Lockout Settings
If a user falls for a phishing attack and reveals their organization’s email or UPN, attackers often attempt to guess passwords to gain unauthorized access to your Active Directory. That’s where account lockout policies become a vital line of defense.
By configuring account lockout settings through Group Policy, you can define how many failed sign-in attempts trigger a temporary lock and how long it lasts. This helps prevent brute-force and password-spraying attacks while keeping access smooth for legitimate users.
Identity Hygiene & Account Cleanup
4. Remove Inactive Active Directory User Accounts
Inactive accounts in Active Directory are a major security risk because attackers often exploit them to gain unauthorized access. Real-world incidents, such as breaches in U.S. state agencies, show how dormant accounts were leveraged for privilege escalation and lateral movement.
Regularly reviewing and cleaning up inactive accounts helps keep your Active Directory environment safe and organized. It also prevents misuse of old credentials and supports compliance efforts.
5. Delete Stale Computer Accounts in Active Directory Domain Services
Stale computer accounts in Active Directory are machines that haven’t connected to the network for a long time. Leaving them active gives threat attackers an easy way in and can also disrupt reports, patching, and even slow down Group Policy processing.
Identify and remove inactive computer accounts to reduce security risks, clean up your Active Directory structure, and improve overall network hygiene.
6. Secure Service Accounts with Managed Identities
Service accounts represent non-human entities such as applications, APIs, or background services. Because they often have elevated privileges, compromising one account can give attackers broad access. Using shared or static passwords for these service accounts increases the risk of widespread security breaches.
To reduce this risk, use Managed Service Accounts (MSAs) instead of traditional service accounts. MSAs automatically manage and rotate passwords, enforce strong policies, and remove the need for manual updates. Assign only the permissions necessary for the service to function and monitor account activity for unusual behavior.
Securing service accounts with managed identities simplifies administration, strengthens security, and prevents attackers from exploiting high-privilege accounts in your Active Directory environment.
User Access Control
7. Disable Active Directory Guest Access
The built-in guest account in Active Directory is disabled by default. If enabled for business need, it should be managed carefully with guest account security considerations in place.
Guest accounts have minimal restrictions, and if misused, users can access shared resources or gather information about your network. Limiting their use reduces unnecessary exposure and helps prevent unauthorized activity.
For temporary access, create dedicated accounts with expiration dates and review them regularly. This simple step strengthens your domain security and ensures only authorized users have access.
8. Disable Anonymous Access in Active Directory
Anonymous access allows users to view resources or gain the same access as the everyone’s group in Active Directory without signing in. While this might have been useful for older systems, it’s rarely needed today and can create security gaps if left enabled.
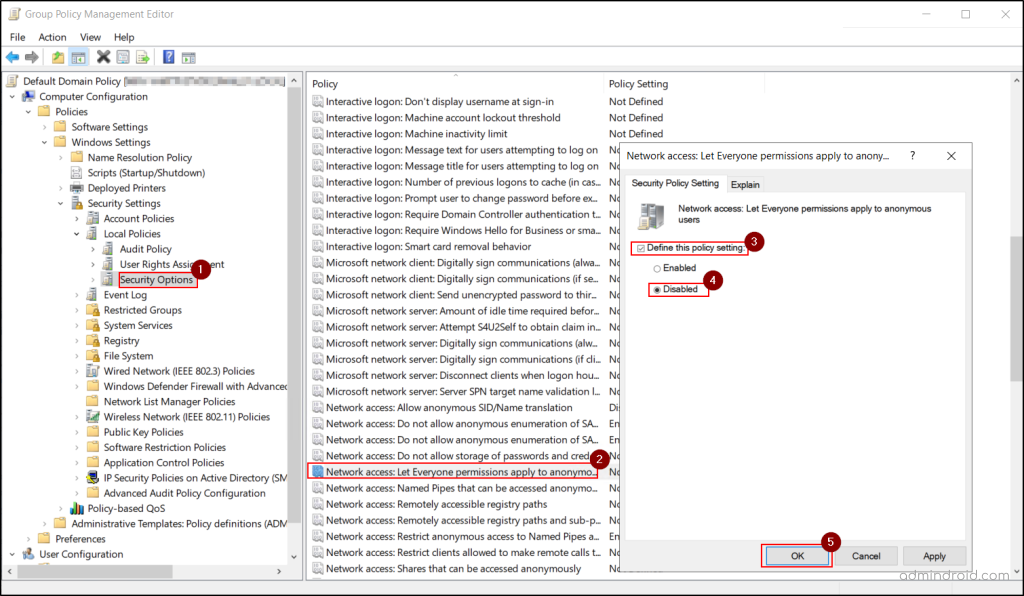
Disabling it ensures that only authenticated users can access Active Directory data and shared resources, reducing potential security risks. To disable anonymous access, open the Group Policy Management Console (GPMC), select your domain GPO, and click Edit. Navigate to:
Group Policy Management Editor ➝ Computer Configuration➝ Policies➝ Windows Settings ➝ Security Settings ➝ Local Policies ➝ Security Options.
Then set, ‘Network access: Let Everyone permissions apply to anonymous users’ to Disabled and click OK.
9. Configure User Rights Assignments in Active Directory
Excessive or unnecessary user rights in Active Directory pose significant security risks, as accounts with more permissions than required can be exploited to make unauthorized changes or disrupt operations.
Configure user rights assignments carefully using Group Policy, as they determine what actions users and groups can perform. These include logging on, accessing files, shutting down servers, or adding workstations to the domain. Regularly review and remove unnecessary rights, document changes, and keep user rights up to date to protect Active Directory from misuse.
10. Disable Remote PowerShell Access
By default, members of the Administrators and Remote Management groups can use PowerShell Remoting to connect to remote computers. In some cases, standard users are also granted this access for specific tasks.
However, this opens the door to serious security risks, as attackers with compromised accounts that have Remote PowerShell access can run malicious scripts, modify permissions, or take control of systems. Such actions can disrupt your Active Directory security and system integrity.
To minimize these risks, the best practice is to restrict Remote PowerShell access for non-admins so that only trusted administrators can use it, and unnecessary users are blocked.
Privileged Account Management
11. Protect the Built-in Active Directory Administrator Account
The built-in administrator account in Active Directory has high-level privileges and is often targeted by attackers. Without strong protection, a compromised account can be leveraged to take over the entire domain, making it a double-edged sword.
That’s why securing the built-in administrator account is essential. It includes enabling Account is sensitive and cannot be delegated, requiring a smart card for interactive logon, denying access from the network, and blocking logon as a batch job, as a service, and through RDP. These measures reduce the attack surface and strengthen Active Directory security.
12. Disable Local Administrator Accounts on All Computers
Local administrator accounts exist on every domain-joined computer and pose a security risk because they are well-known accounts (the SID remains the same even if renamed) and often share the same password across multiple systems. This makes it easier for attackers to pivot from one compromised computer to others in the domain.
To secure local administrator accounts, rename them to something less predictable and disable them if not needed, ensuring alternate admin accounts are properly configured. Apply strong password policies, monitor account activity, and use Microsoft LAPS to manage and rotate passwords, preventing attackers from exploiting default or unmanaged credentials.
13. Use Dedicated Accounts for Admin and Daily Tasks
Administrators should avoid using high-privilege accounts for everyday tasks like checking email or browsing the web. Doing so increases the risk of credential theft—especially if the device gets compromised.
Separating admin accounts enhances their protection, providing a simple and effective way to secure privileged access in Active Directory.
14. Limit Built-in Privileged Groups Usage
High-privilege groups like Domain Admins, Enterprise Admins, and Schema Admins have full control over your Active Directory. Excessive membership increases the risk of unauthorized access and misuse, so restrict membership to only those who genuinely need it.
Regularly review and monitor privileged built-in groups to remove unused memberships. Keeping access tight minimizes the attack surface and protects critical Active Directory resources.
15. Implement Tiered Administration Model
A tiered administration model allows admins to organize privileges into layers based on sensitivity, which limits how far cybersecurity attackers can escalate if one account is compromised. By using OUs to isolate access levels and delegating permissions, you prevent attackers from moving laterally across tiers in Active Directory.
- Tier 0: Domain controllers and highly sensitive assets
- Tier 1: Servers and infrastructure services
- Tier 2: Workstations and user devices
Regularly review and validate tier assignments to keep them accurate and up to date. Implementing this model strengthens security, enforces least privilege, and maintains a well-structured Active Directory environment.
16. Implement Least Privilege Using Role Based Access Control in Active Directory
Role-Based Access Control (RBAC) in Active Directory assigns permissions based on job roles, ensuring users and service accounts have only the access they need. This prevents unnecessary privileges that can lead to unauthorized changes or data exposure.
The principle of least privilege complements RBAC by ensuring accounts have only the permissions required for their tasks. Implement RBAC effectively by creating security groups for roles (e.g., Helpdesk Technicians or Server Administrators) instead of assigning permissions to individual users.
You can implement least privilege using the Delegation of Control Wizard to grant specific administrative rights without providing full domain access.
Auditing & Monitoring
17. Enable Advanced Audit Policies
Advanced audit policy configurations help you track important actions in Active Directory, such as logons, file access, and user account changes. The recorded audit data also enables admins to identify logon types, authentication protocol usage, GPO changes, account lockout sources, and other investigation details. Without proper auditing, suspicious activity can go unnoticed, making it harder to detect threats early.
To enable advanced audit policies, open the Group Policy Management Console (GPMC), select your domain GPO, and click Edit. Navigate to:
Group Policy Management Editor ➝ Computer Configuration ➝ Policies ➝ Windows Settings ➝ Security Settings ➝ Advanced Audit Policy Configuration.
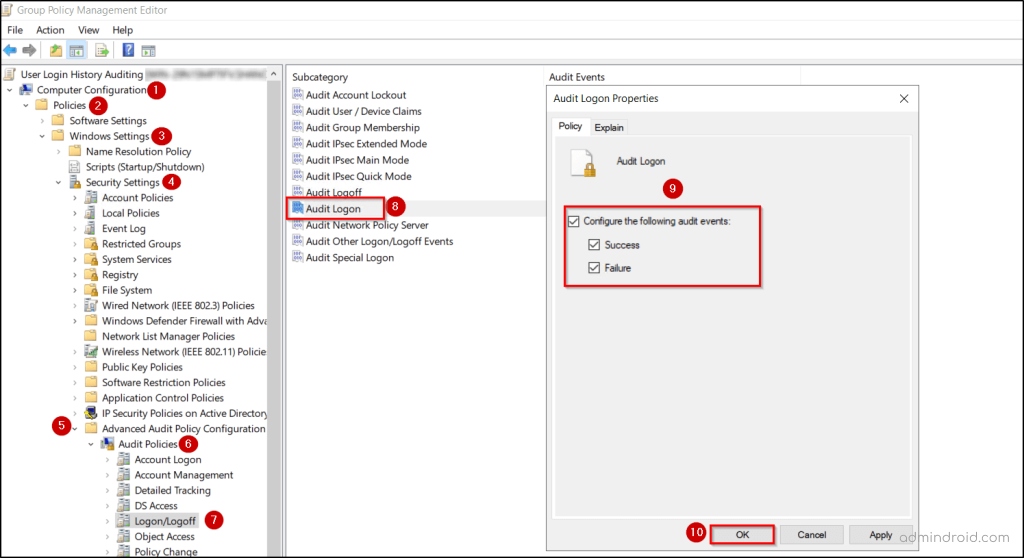
Configure key audit categories such as logon events, account management, and directory service access to improve visibility, support compliance, and detect potential cybersecurity risks before they escalate.
Once enabled, make it a routine to analyze and monitor audit logs regularly to identify anomalies and respond to threats proactively.
18.Deploy Honeypot Accounts to Detect Malicious Activity
Honeypot accounts are fake user accounts that look real but are never used for normal work. They act as traps to detect anyone trying to access sensitive parts of your Active Directory.
Place these accounts in sensitive groups or give them tempting permissions. Any login attempts or changes to these accounts can show someone is trying to attack.
Keep an eye on these accounts using audit logs or security tools. They add an extra layer of protection and help keep your Active Directory safe from unauthorized access.
Maintenance, Patch & Recovery
19. Patch Active Directory Domain Controllers Regularly
Domain controllers are the backbone of Active Directory. If they are not updated regularly, they can become vulnerable to exploits such as privilege escalation, remote code execution, or denial-of-service attacks. Attackers often target unpatched systems because they provide an easy entry point into the network.
Therefore, apply operating system and security updates as soon as they are available. Always test patches in a staging environment before deploying them to production. Additionally, avoid installing additional software or server roles on DC’s, as this increases the attack surface and adds unnecessary risks. Keep domain controllers dedicated to their core function—identity and authentication services.
By documenting patching steps to meet compliance, you create a clear audit trail. Regular updates and minimizing unnecessary components help keep Active Directory secure.
20. Reset the Krbtgt Account Password to Prevent Golden Ticket Attacks
The Krbtgt account plays a vital role in Kerberos authentication by issuing Ticket Granting Tickets (TGTs). If compromised, attackers can forge Golden Tickets—allow unrestricted access across the domain without detection. This makes Krbtgt one of the most sensitive accounts in Active Directory.
To defend against this, reset the Krbtgt password twice in succession using PowerShell or Active Directory Users and Computers (ADUC) console. This invalidates existing TGTs and ensures new tickets are based on updated credentials. Always perform this reset during a maintenance window and monitor authentication logs for anomalies post-reset. Regular Krbtgt password resets is a proactive defense against advanced threats. Pair this with strong domain controller security and Kerberos auditing to prevent stealthy lateral movement and privilege abuse.
Even after resetting the Krbtgt account, legacy encryption like RC4 can still put Kerberos at risk. Make sure to detect RC4 usage in your Active Directory and safely migrate to stronger ciphers to prevent authentication failures and protect accounts from Kerberoasting attacks.
21. Use Secure Admin Workstations (SAW) in Active Directory
Administrative credentials are a prime target for attackers, and using regular workstations for admin tasks exposes them to phishing, malware, and keyloggers. This increases the risk of credential theft and compromise of your Active Directory environment.
To mitigate these risks, use Secure Admin Workstations (SAWs)—dedicated, isolated devices for administrative tasks. By restricting software installation, disabling internet access, and monitoring activity through audit logs, SAWs protect privileged credentials and reduce the attack surface.
22. Perform and Test Active Directory Backups
Backups are essential for business continuity and quick recovery from security incidents, system failures, or accidental changes. Without reliable backups, organizations risk losing critical identity data and facing prolonged downtime.
To stay prepared, schedule regular Active Directory backups and store them securely. It’s equally important to test restoration procedures to ensure backups work when needed. Document recovery steps and periodically verify backup integrity to meet compliance requirements.
In addition to maintaining regular backups, it’s important to add additional domain controllers for your domain to avoid a single point of failure.
Final Thoughts
Securing Active Directory is a continuous effort, not a one-time setup. Regularly reviewing configurations, applying updates, and monitoring for suspicious activity are key to maintaining a strong security posture. Stay tuned for more blogs in our Cybersecurity Awareness Series!