After more than two years from the announcement of deprecation, the complete retirement of the AzureAD and MSOnline PowerShell modules is now approaching 🚨. For many organizations, these modules have been a key tool for managing Microsoft Azure AD through PowerShell. However, with the advent of the modern Microsoft Graph module, you can access the same functionalities along with enhanced security 🔒. As a result, the transition is not only inevitable but also beneficial.
Alongside this shift, you may experience temporary outages ⚠️ as services adjust during the changeover. Therefore, this blog dives deep into the implications of the MSOnline and AzureAD module retirement. It explains what these changes mean and helps you navigate temporary disruptions during the transition.
Why Microsoft Retiring MSOnline & AzureAD PowerShell Modules?
The legacy MSOnline and AzureAD PowerShell modules rely on the older Azure AD Graph API. This API is a collection of fragmented interfaces that do not meet modern demands for security, advanced functionality, and cross-platform compatibility.
To address these shortcomings, Microsoft is transitioning to the MS Graph PowerShell SDK. This modern, unified module leverages the Microsoft Graph API to simplify the management of Microsoft Entra ID resources. They also offer improved security and support a wider range of platforms.
Key Dates for MSOnline & AzureAD Modules Retirement & Downtime
Temporary Outages:
- February 3 – February 11, 2025: As per MC993972, MSOnline module will undergo one or two outages of 3-5 hours long.
- February 17 – February 28, 2025: As per MC1002396, MSOnline PowerShell will experience at least one temporary outage lasting approximately 8 hours.
- March 1, 2025 – March 30, 2025: A final and longer outage test will be conducted for the MSOnline module as final preparation for retirement.
End of Support and Retirement:
- March 30, 2025: End of support for the AzureAD & MSOnline PowerShell module, i.e., Microsoft will no longer provide updates or technical support for these modules.
- Early April – Late May 2025: MSOnline PowerShell module will retire and stop working.
- July 1, 2025: Retirement will start for AzureAD PowerShell module.
Moreover, as the Azure AD Graph API is phased out, every application that currently depends on it must migrate to the Microsoft Graph API.
How to Identify if MSOnline & AzureAD Modules are Still in Use in Your Microsoft 365 Tenant?
To spare us from playing detective like Sherlock Holmes , Microsoft offers the following methods. This helps to find out whether the MSOnline and AzureAD modules are still being used by our tenants.
Analyze Microsoft Entra Sign-in Logs to Detect MSOnline & AzureAD PowerShell Activity
To verify whether your tenant is actively using the AzureAD and MSOnline modules, simply follow the steps below to inspect the sign-in logs.
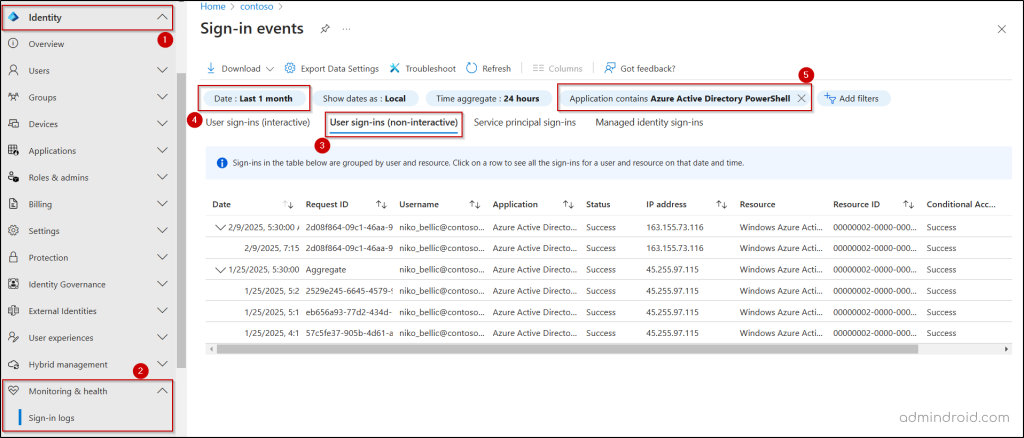
- Log in to the Microsoft Entra admin center and navigate to the Identity → Monitoring & health → Sign-in logs.
- Switch to the User sign-ins (non-interactive) tab and set the Date filter to Last 1 month to capture all recent login activities.
- Then, click Add filters, select Application, and click Apply.
- In the Application text box, enter Azure Active Directory PowerShell and hit Apply.
Now, you can see all the sign-in activities of scripts, apps, or workflows still using MSOnline or AzureAD PowerShell modules. Follow the same procedure in the User sign-ins (interactive) tab to view users actively using these modules in your tenant.
Review Microsoft Entra Recommendations to Identify MSOnline & AzureAD Usage
Microsoft Entra recommendation provides additional information about the usage of MSOnline & AzureAD PowerShell modules. Follow these steps to identify their usage through these recommendations.
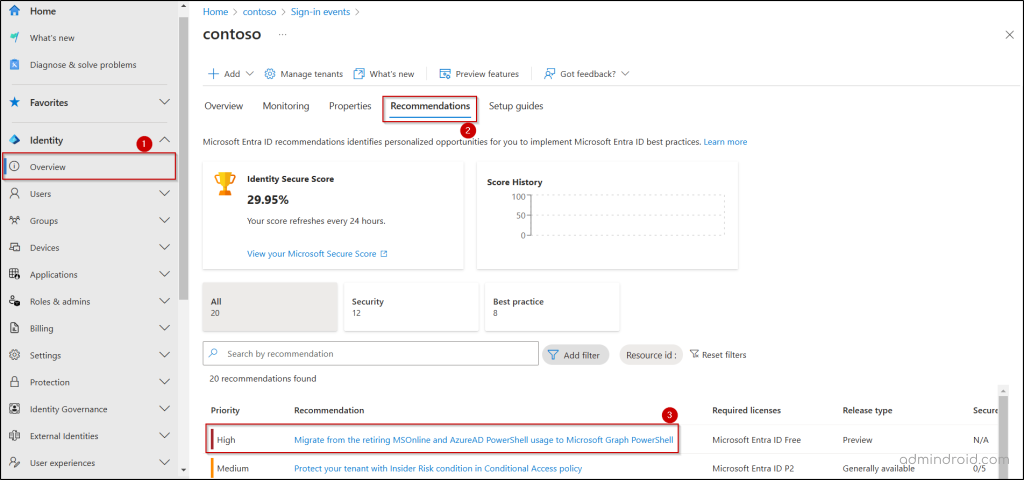
- In the Microsoft Entra admin center, navigate to the Recommendations tab under Identity → Overview.
- If your tenant is still using AzureAD or MSOnline PowerShell modules, you’ll see the following recommendation with high priority: Migrate from the retiring MSOnline and AzureAD PowerShell usage to Microsoft Graph PowerShell.
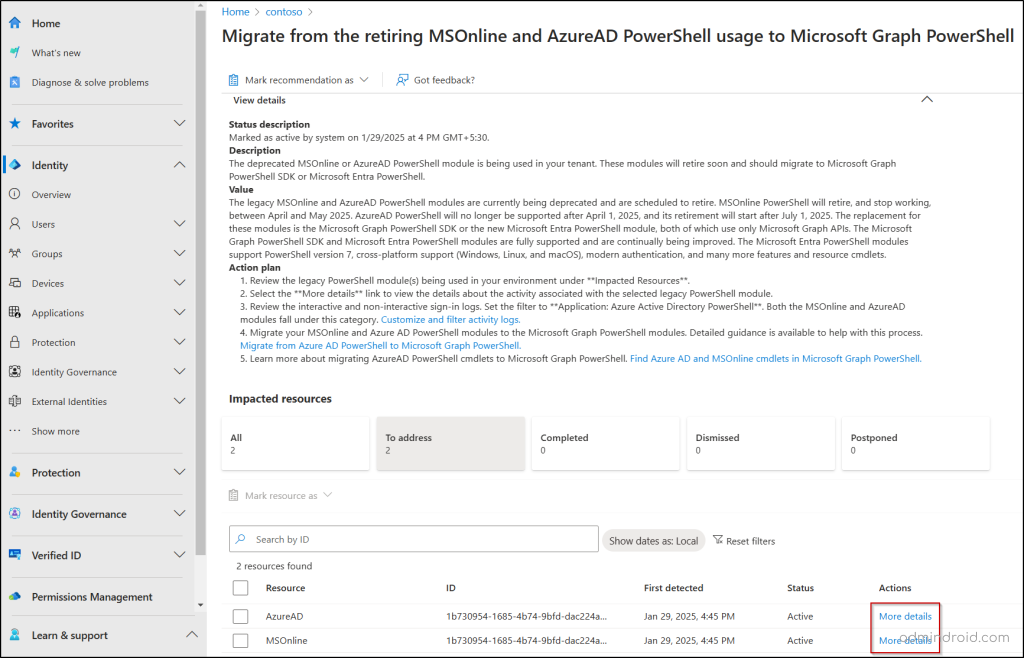
- Click the recommendation and select More Details appear next to one of the listed PowerShell modules.
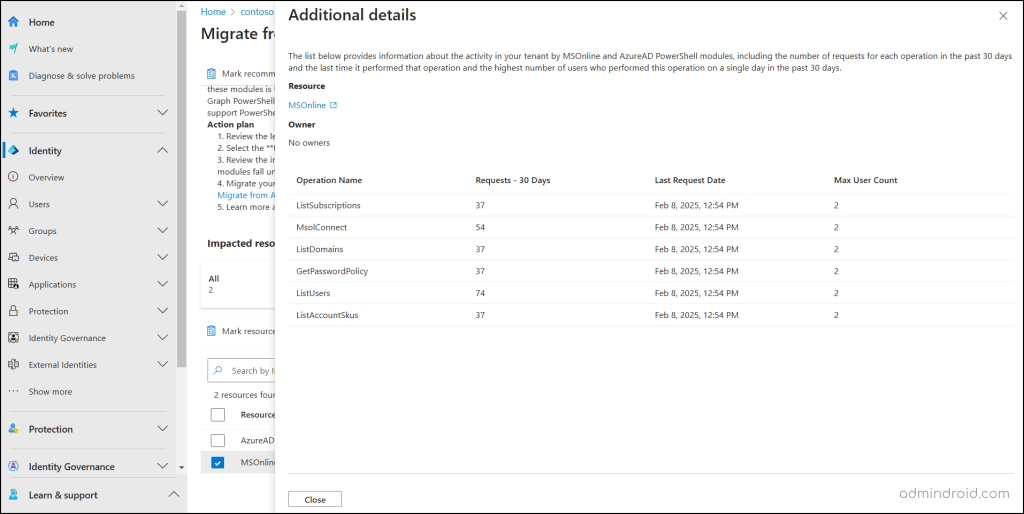
- This will display the operations performed using the module (e.g., MsolConnect, ListUsers, GetPasswordPolicy), the total number of requests made in the last 30 days, the date of the most recent request, and more.
Where to Migrate? – Microsoft Graph PowerShell SDK
If you still rely on the MSOnline or AzureAD PowerShell modules for administration, you must migrate to the official replacement: Microsoft Graph PowerShell SDK. Migrating immediately helps you avoid upcoming outages and prepares you for the retirement of these older modules.
Getting Started with Microsoft Graph PowerShell Module
The commands used in AzureAD and MSOnline modules won’t directly work with Microsoft Graph PowerShell because the modules differ in structure and functionality. You first need to install and connect to the Microsoft Graph module to start, using the following cmdlets.
|
1 2 3 4 5 |
#To install the module Install-Module Microsoft.Graph -Scope CurrentUser #To connect to the module interactively (Replacing "<Scopes>" with "User.Read.All", "Group.ReadWrite.All" enables the user to manage all groups and users) Connect-MgGraph -Scopes "<Scopes>" |
Microsoft Graph PowerShell adopts a streamlined naming convention by replacing the ‘AzureAD’ or ‘Msol’ prefixes with ‘Mg’. For commonly used cmdlets, refer to the table below.
| MSOnline | AzureAD | Microsoft Graph |
| New-MsolUser | New-AzureADUser | New-MgUser |
| Get-MsolUser | Get-AzureADUser | Get-MgUser |
| Set-MsolUser | Set-AzureADUser | Update-MgUser |
| Get-MsolGroup | Get-AzureADGroup | Get-MgGroup |
| Set-MsolUserPassword | Set-AzureADUserPassword | Update-MgUserPassword |
To find all Azure AD PowerShell and MSOnline cmdlets in Microsoft Graph PowerShell, refer here.
Migrate Azure AD Scripts Easily with Entra PowerShell Module
Recently, Microsoft introduced the Entra PowerShell module to streamline administration and ease migration from the retiring modules. This module works directly with the Graph API and supports over 98% of the cmdlets used in Azure AD PowerShell and MSOnline. By replacing the connection cmdlet with ‘Enable-EntraAzureADAlias’ in existing scripts, you can keep most Azure AD PowerShell cmdlets unchanged.
📝 Note: If you’ve already migrated to Microsoft Graph PowerShell, there’s no need to switch to the Entra PowerShell module.
Benefits of Microsoft Graph PowerShell Module
- Unified Management: Offers a single endpoint to manage Microsoft Entra ID and services such as SharePoint, Exchange, Outlook, etc., using one access token.
- Modern Authentication: Leverages the Microsoft Authentication Library (MSAL) to enable secure features like Passwordless sign-in and supports external identities from other Microsoft Entra tenants.
- Streamlined Access: Provides easy and secure access to resources using Certificate-Based Authentication (CBA), simplifying the authentication process. This helps run Microsoft Graph scripts unattended using tools like Azure Automation or Task Scheduler.
- Cross-Platform Compatibility: Works across Windows, macOS, and Linux, fully supporting PowerShell 7 and later versions while maintaining backward compatibility with Windows PowerShell 5.1.
- Enhanced Security: Enforces the principle of least privilege by requiring users to explicitly request permissions, ensuring granular access control.
- High Performance & Open Source: This solution offers powerful query capabilities for managing large-scale environments without performance bottlenecks. It is an open-source platform that encourages community contributions and is frequently updated to support the latest Graph API features.
Most Useful Microsoft Graph PowerShell Scripts
To ease your transition to Microsoft Graph PowerShell, we’ve gathered key MS Graph-powered PowerShell scripts for managing your essential M365 tasks. This will help you avoid disruptions in your day-to-day operations due to MSOnline & AzureAD retirement.
- Microsoft 365 Licenses Management: This PowerShell script offers over 10 license management functions, including assigning and removing licenses for individual and bulk users, as well as generating license reports.
- Microsoft 365 Inactive User Report: This script identifies users who haven’t logged in within a specified timeframe, aiding you to efficiently manage inactive user accounts.
- Microsoft 365 Groups Report: This PowerShell script creates over 12 group membership reports by categorizing groups based on type (e.g., distribution, security, etc.) and size (e.g., empty groups, groups with a specific no.of members).
- Microsoft 365 Guest User Report: This script helps you find all external users in your Microsoft 365 tenant and shows their group membership information. By leveraging its advanced filters, you can effortlessly identify both stale and recently added guest accounts.
- Microsoft 365 MFA Status Report: This PowerShell script generates 7 MFA status reports using user authentication data. It covers users with MFA enabled, disabled, and those allowed for sign-in.
- Conditional Access Policy Report: This MS Graph PowerShell script produces 6 key Conditional Access policy reports, featuring 33 essential attributes. It helps you track CA policies based on their status, creation, and last updated dates.
- M365 Users Last Successful Sign-in Report: This report allows you to track inactive users by identifying their last successful sign-in, in addition to viewing the overall last login time, which includes failed attempts.
Don’t Wait Until It’s Too Late – Start Your Migration Today and Keep Your Workflows Uninterrupted.
This transition offers more than just updated cmdlets—it provides enhanced security, better performance, and access to modern Microsoft 365 management capabilities. We hope this blog serves as a helpful reminder to take precautionary steps in tackling MSOnline and AzureAD module retirements. If you have any questions regarding the blog, feel free to leave a comment below.






