On Day 5 of Cybersecurity awareness month, learn how to implement least privilege access using Entra ID administrative units and enhance security within Microsoft 365. Stay tuned for more blog posts in our M365 Cybersecurity blog series.
With the increasing complexity of cybersecurity challenges, protecting sensitive data and systems has become a top priority. One crucial aspect of this protection is the principle of least privilege (POLP). Microsoft 365 offers several tools and features to help organizations implement the least privilege access. Administrative units in Microsoft Entra ID (Azure AD) is a powerful feature that enables organizations to refine and manage access rights effectively, thereby strengthening security and reducing unnecessary permissions.
As the world is increasingly interconnected, everyone shares the responsibility of securing cyber space.
-Newton Lee
As the quote goes, everyone shares the responsibility of securing cyber space. By implementing the principle of least privilege access using Entra ID administrative units, organizations can help to protect their sensitive data. Let’s first dive into the principle of least privilege access in Entra ID (Azure AD).
What is “Principle of Least Privilege Access” and Why Do You Need It?
The principle of least privilege access states that “Users and applications should be granted access only to the data and operations they require to perform their jobs”. As stated, it restricts users’ access rights to the minimum levels required to complete their tasks. By adhering to this principle, organizations can significantly reduce the attack surface, mitigate the risk of unauthorized access, and limit the potential damage caused by security breaches. In a Microsoft 365 environment, ensuring the least privileged access is essential to maintain data confidentiality and system integrity, making it a critical component of any organization’s security strategy.
One of the best practices of leveraging least privilege access to users is by configuring Privileged Identity Management (PIM) in Microsoft Entra ID and granting Just-in-Time (JIT) access. With Privileged Identity Management, admins can manage Microsoft Entra roles, Azure resource roles, or PIM for Groups based on organizational needs. This approach provides users with time-limited permissions to carry out privileged actions, thereby ensuring that unauthorized or malicious users cannot gain access.
What are Entra ID Administrative Units?
Administrative units in Azure AD allow organizations to logically group and manage users & resources based on specific criteria. It’s like giving keys to different rooms in a big building – each group gets access only to their own rooms, not the whole building.
Difference Between Entra ID Groups and Administrative Units:
Unlike Entra ID groups, which are primarily used to manage access to resources like applications, files, or permissions, administrative units are designed for delegating administrative tasks. They scope administrative privileges to specific subsets of users, groups, or devices, offering more control over how tasks are assigned and managed.
By organizing users and resources into admin units, organizations can ensure that users have access only to the resources necessary for their roles, aligning with the principle of least privilege. To further shield important accounts in your organization, you can use the restricted management administrative units.
License Requirement for Entra ID Administrative Units:
- Global administrators and privileged role admins create admin units with a Microsoft Entra ID Free license.
- Every member of an administrative unit needs a Microsoft Entra ID Free license.
- Each administrator managing an administrative unit (like a team or department) needs a Microsoft Entra ID P1 license.
How to Create Administrative Units in Entra ID?
Creating admin units using the Microsoft Entra admin center involves the following steps:
Creating a New Administrative Unit using Microsoft Entra Admin Center:
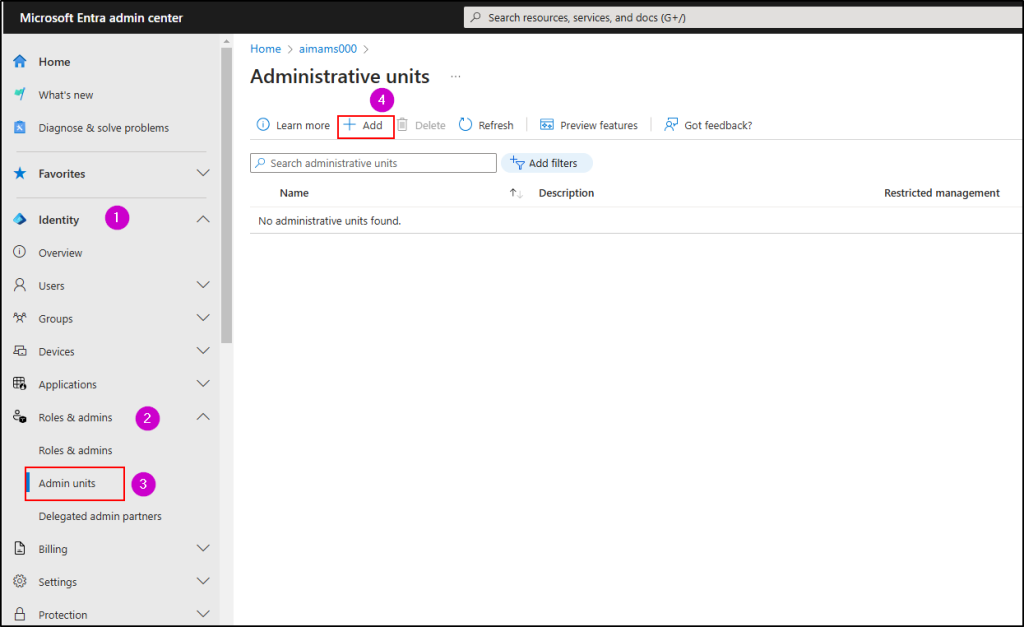
- Go to the Microsoft Entra admin center and navigate to Identity.
- Under Roles & admins, select Admin units -> Click Add.
- Enter a name for the administrative unit in the Name field and provide a description if required.
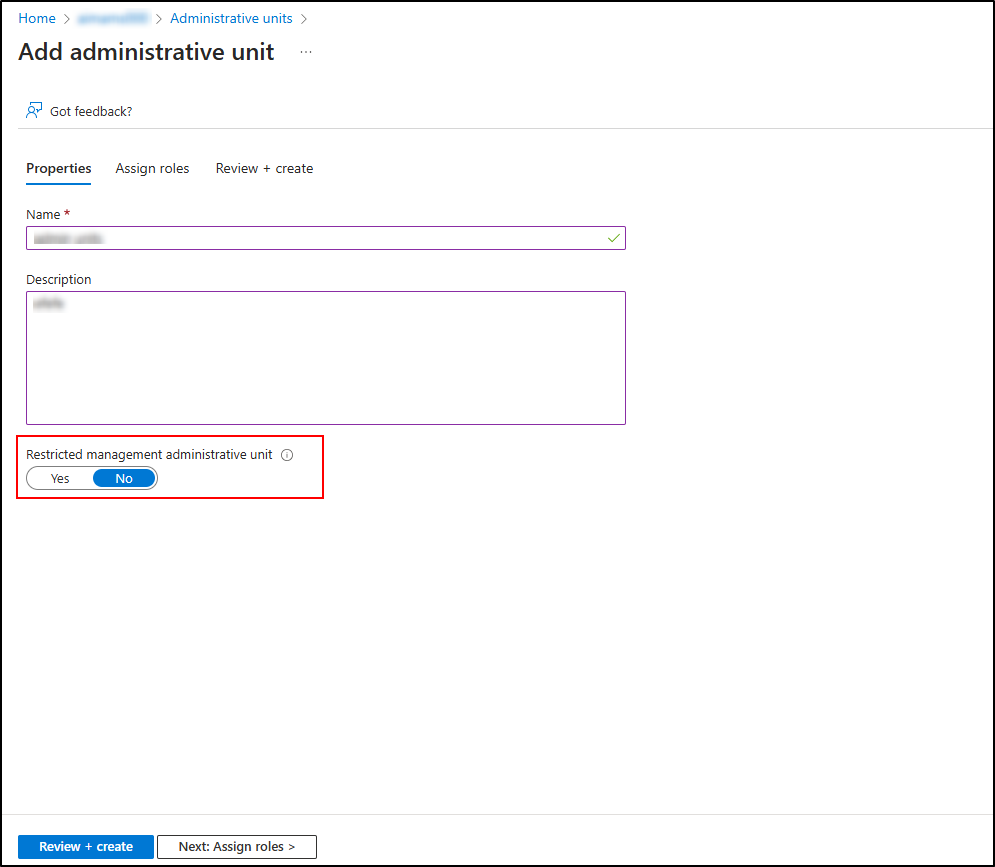
To protect specific users, security groups, or devices in your Microsoft Entra ID tenant from being modified by tenant-level administrators, you can enable restricted management administrative units on this page.
- On the Assign roles tab, assign roles to the administrative unit if required.
- Review your configuration on the Review + create tab.
- Click Create to finalize the administrative unit creation.
Adding Users to the Admin Units:
After creating the administrative unit,
- Navigate to the user, group, or device you want to assign.
- Under Manage, select Administrative units.
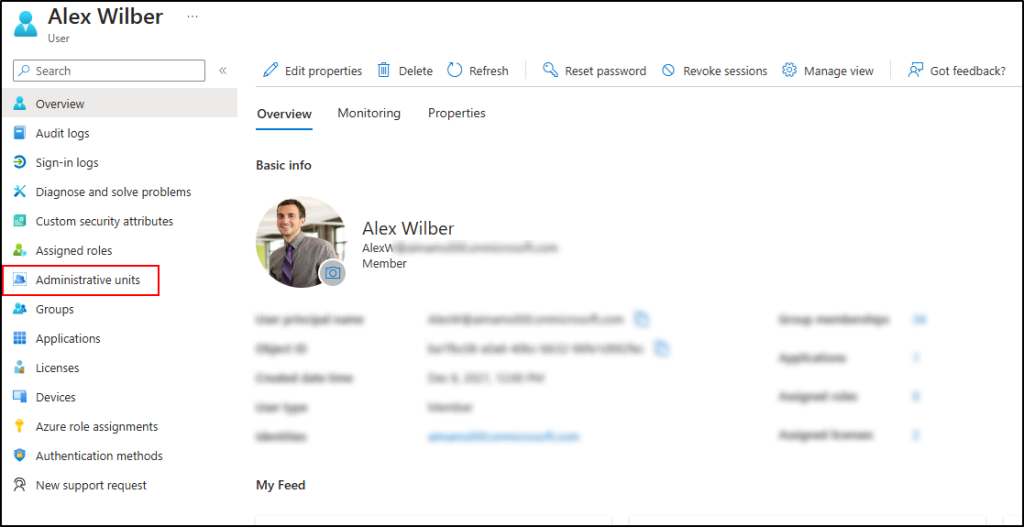
- Click Assign to administrative unit.
- In the selection pane, choose the newly created administrative unit and confirm by clicking Select.
How to Use Administrative Units in Entra ID?
We recommend using administrative units in Azure Active Directory (Entra ID) to improve security for the following reasons:
Granular Access Control: Administrative units enable organizations to define and enforce precise access policies for different groups of users and resources, reducing the risk of over-privileged accounts.
Delegation of Administrative Tasks: AUs facilitate the delegation of administrative tasks, allowing organizations to assign specific responsibilities to designated administrators while maintaining overall control.
Simplified Compliance: With AUs, organizations can easily meet compliance requirements by ensuring that users only have access to the data and applications they need to perform their job functions.
Points to Remember:
Here are some important points and limitations to note about administrative units in Entra ID.
- An administrative unit can contain only users, groups, or devices.
- When you add a group to an administrative unit, admins can manage the properties of the group alone, not the members of the group.
- Users can be members of multiple administrative units.
- Administrative units cannot be nested.
- Dynamic groups cannot be added to an administrative unit.
- To recover a deleted administrative unit, you must use Microsoft Graph.
- Administrative units require manual effort to add and maintain members. Switch to dynamic administrative units to automate membership management using rules.
How Administrative Units Help to Implement Least Privilege Access?
Entra ID administrative units help organizations implement least privilege access by allowing them to restrict the scope of role assignments to specific groups of users. Let’s see some of the use cases where we can use administrative units to implement the least privileged access in Entra ID for enhanced security.
Case 1: Departmental Access Control
An organization can create an administrative unit for its engineering team in Entra ID (Azure AD). By assigning the Group Administrator role to users within that unit, the engineers gain the ability to manage users and groups in Entra ID, specifically within their department, without having access to other departments’ users and groups.
Case 2: Just-in-time Admin Access
Entra ID administrative units can also be used to implement just-in-time administrative access. For example, an organization can grant Global Administrator role to users only when they need to perform a specific task, such as creating a new Azure AD tenant. Once the task is complete, the user’s elevated privilege roles get revoked.
Case 3: Project Management
When multiple projects are running concurrently, each project can have its own administrative unit with project-specific administrators. This approach provides isolation and control over user & group management within each project, improving security and project management.
Case 4: Geographic Segmentation
If your organization operates in multiple geographic regions, create administrative units for each region. Assign regional administrators to manage users and groups within their specific locations. This approach ensures that access to Azure AD resources is limited to the geographic area, reducing the risk of unauthorized access.
Case 5: Role-Based Privileges
Utilize Entra ID roles in combination with administrative units. Assign Microsoft 365 roles to users within their administrative units based on their job responsibilities. For example, give a Help Desk role to support staff within their department’s administrative unit, granting them enough access to perform user support tasks without broader privileges.
Case 6: Resource-Specific Access
Use administrative units to group resources (e.g., Azure resources, applications, or SharePoint sites) based on their function or project. Assign administrators with access only to the administrative units containing the specific resources they need to manage, thereby preventing unnecessary access to resources.
Conclusion
Therefore, Entra ID administrative units are valuable for organizations seeking to enhance security by implementing the principle of least privilege. By segmenting administrative access into different units, organizations can better manage and restrict user & group access within their Entra ID environment. Thanks for reading! Feel free to reach us in the comment section for any assistance.