On Day 3 of Cybersecurity awareness month, learn to protect your organization from password spray attacks today. Stay tuned for more blogs in the Office 365 Cybersecurity blog series
Microsoft reported that they see 12 million username/password pair attacks every day. The number is alarming, isn’t it? Even though multi-factor authentication is available, only 26.64% of Microsoft 365 accounts use MFA. If the attacker can guess the password, they can easily bypass MFA with a fatigue attack if push notification is used for authorization. Hence, password plays a vital role in account compromise. The stronger the users’ password, the more it protects them from hackers.
Importance of Custom Password Ban:
Often, we are instructed not to use weak or easily-hackable passwords such as Password@123 and qwerty123. But still, simple and insecure passwords are used. To avoid this situation, the Azure AD Identity Protection team analyses current password trends & breaches and forms a global banned password list. By default, this list automatically applies to all cloud-only Office 365 users. We can’t enable or disable it.
The global banned password list is subject to change without any prior info. What if your organization wants to permanently block specific passwords in your organization? Here comes Azure AD Password Protection. It helps you ban a list of custom passwords in your organization.
How Azure AD Password Protection Works?
Azure AD Password Protection helps to enable custom banned passwords and add entries to it. Thus, it prevents users from using weak and commonly used local passwords, such as
- Company name
- Trademark
- Product name
- Company-specific internal terms, etc.
Choosing a hard-to-guess, but easy-to-remember password is important!
–Kevin Mitnick
When a user or administrator changes their password, Azure AD validates the password strength with its banned password list. If the new password matches the banned password, it will show the below error “Unfortunately, you can’t use that password because it contains words or characters that have been blocked by your administrator. Please try again with a different password”.
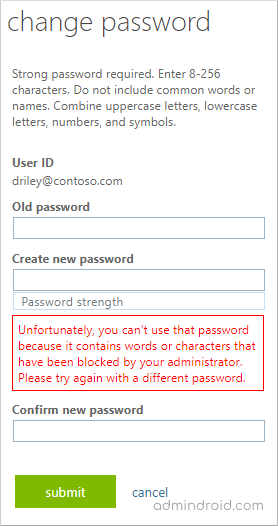
Note: Many organizations adopt hybrid models. If you are one of them, you can extend the Azure AD Password Protection to on-premise AD by installing required agents on your servers.
License Requirement:
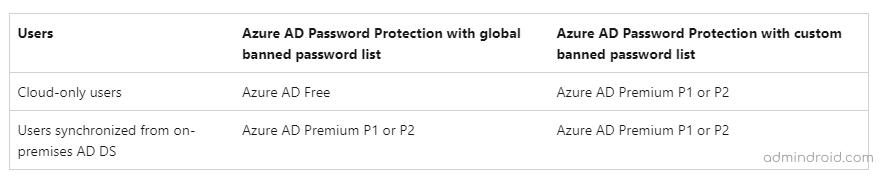
How to Enable Custom Banned Password in Microsoft 365?
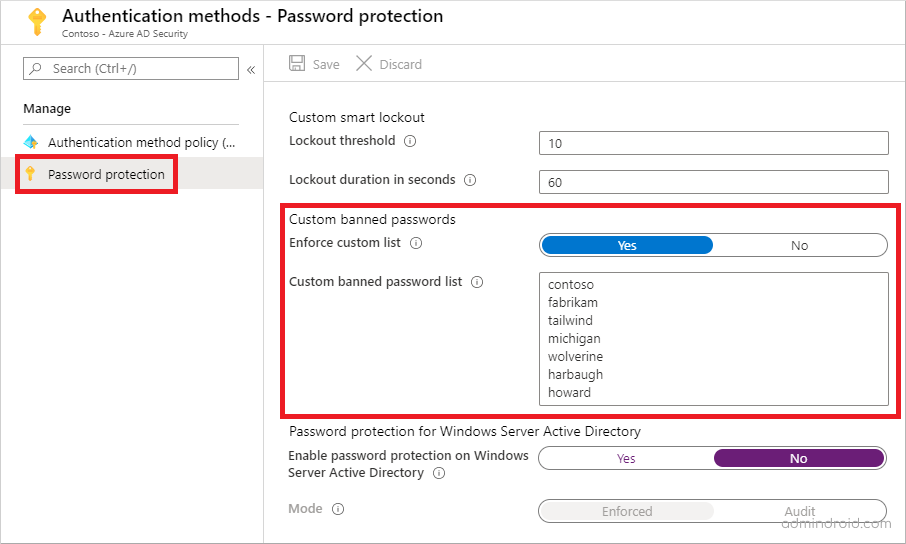
To block your own list of passwords, you need to ‘Enforce custom list’ to prevent using easy-to-guess passwords. You can follow the steps below to enable custom banned passwords.
- Login to the Azure Active Directory portal as a global administrator.
- Navigate to Azure Active Directory–> Security–> Authentication methods.
- Select ‘Password protection’.
- Toggle ‘Enforce custom list’ to Yes.
- Enter your own custom passwords in the ‘Custom banned password list’.
- If you don’t want to extend Azure AD Password Protection to on-premise AD, set ‘Enable password protection on Windows Server Active Directory’ to No.
- ‘Save’ the settings.
Note: You can add up to 1000 terms in the custom banned password list.
How Custom Banned Password Works in Real Time?
To test the custom banned password, I tried to change my account password to Contos0@2022 and got an error. When you check the custom banned password list, you can see ‘contoso’ as a banned password. Even though I didn’t use the exact word, I got the error.
How is it possible? Let me explain in detail.
The Azure AD Password algorithm applies a variety of methods to avoid the usage of a variant of banned passwords. Following are a few methods,
- Custom banned passwords are case-insensitive. i.e., When you change a new password, all the upper-case letters are converted to lower-case and evaluated.
- Common character substitutions are performed, such as a by @, o by 0, s by $, etc.
- Fuzzy matching: Validating the banned password within an edit distance of one comparison. For example, consider ‘abcdef’ as banned password. Then, the user can’t set its variants such as abcdeg, abcdefg, and abcde.
- Substring matching: This method is performed to eliminate users’ first names, last names, tenant name, etc.
- Score calculation: The password score is calculated after performing all the validations. If the score is less than 5, the password will be rejected.
Apart from enabling custom banned passwords in Entra, Microsoft recommends configuring 6 essential M365 password settings to improve security and safeguard sensitive data.
Enhance Password Security in Azure AD with AdminDroid:
AdminDroid provides Microsoft 365 users’ password reports to identify weak or expired passwords. By leveraging this valuable information, you can strengthen your password policies in Azure AD.
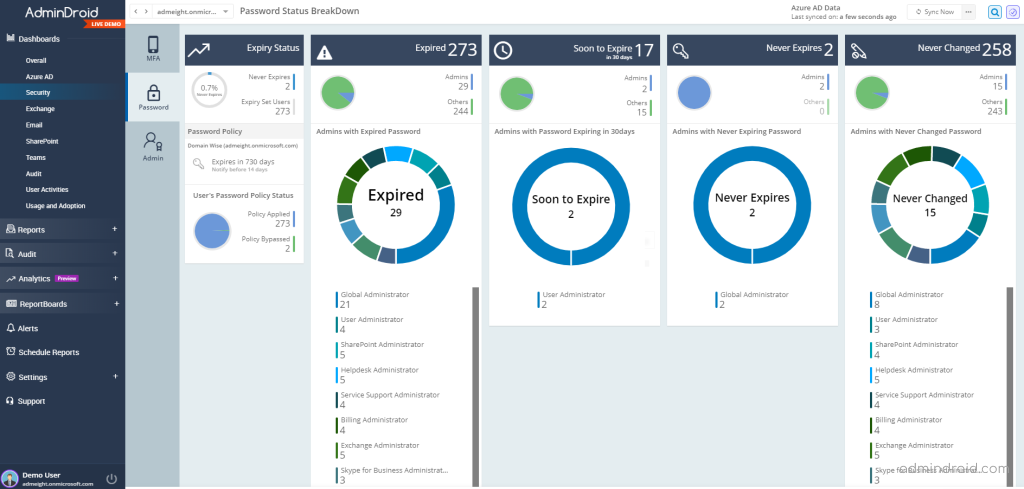
AdminDroid Azure AD management tool offers 120+ free reports on users, groups, group membership, user activities, login activities, password changes, admin role changes, etc. Also, AdminDroid’s free O365 reporter supports report customization, scheduling, send report to email, export, and many more.
Additionally, AdminDroid Microsoft 365 reporting software provides 1800+ pre-built reports and 30+ smart dashboards on various Microsoft 365 services. Download the best Office 365 reporting tool and take proactive steps to protect against potential security breaches.
Conclusion:
Azure AD Password Protection efficiently blocks all known weak passwords likely to be used in password spray attacks. Banning custom passwords is highly effective at removing weak passwords from your organization. While Azure AD Password Protection blocks weak passwords to combat password spray attacks, managing local admin passwords is equally important for securing your systems. With the cloud version of Windows LAPS (Local Administrator Password Solution), you can efficiently manage and protect local admin passwords for both Microsoft Entra and hybrid join devices. This ensures that sensitive credentials remain secure across your organization, helping you stay protected from unauthorized access at all levels.
Be smart and be safe from hackers!






