On Day 24 of Cybersecurity awareness month, learn to configure settings to improve the efficiency of mailbox auditing to detect unauthorized accesses and security breaches. Stay tuned for more blogs in the Cybersecurity blog series.
Exchange mailboxes contain important data and sensitive information. So, it’s necessary to monitor unauthorized access and malicious activities. Mailbox auditing must be enabled in your Office 365 organization to record those activities.
Things to Know about Mailbox Auditing:
- From Jan 2019, mailbox auditing was enabled by default for all organizations. So, you can monitor specific actions (Microsoft call them ‘default actions’) that are performed by all the logon types are automatically recorded. All the actions are not audited by default. Activities like mailbox logins, folder bind are not audited by default.
- If you have enabled auditing manually for any logon type before 2019, ‘default auditing’ won’t affect your existing customized settings. Newly added auditing activities will not be captured unless you manually enable them.
- Default mailbox auditing supports only user, shared, and group mailboxes. Suppose you want to track activities performed by other mailbox types, such as resource mailbox or public folder mailbox. In that case, you need to enable auditing manually.
- As per Microsoft doc: Although mailbox auditing is enabled by default, only users with premium audit licenses (e.g., E5, A5, G5) can return audit events through Audit log search and Office 365 Management Activity API. So, for users without E5/A5/G5 licenses, mailbox auditing needs to be enabled manually to view their activities in the audit log search in the admin center.
- Mailbox auditing can be bypassed. If a mailbox auditing bypass is enabled, actions performed by that specific user will not be tracked. An attacker can use this setting to conduct illicit activities through the compromised account. So, admins must identify audit-bypassed mailboxes and their purpose.
If you are unsure whether mailbox auditing on by default is turned on for your organization, run the following cmdlet.
|
1 |
Get-OrganizationConfig | Format-List AuditDisabled |
If the returned value is ‘False’, then mailbox auditing is turned on by default for your organization.
Checklist for Effective Mailbox Auditing:
In short, to make mailbox auditing effective, follow the below checklist.
|
1 2 3 4 5 |
✓ Identify audit-bypassed mailboxes to make sure nothing goes unnoticed ✓ Check whether all the mailbox activities are recorded ✓ If you have enabled auditing manually, check whether the newly added mailbox activities are audited. ✓ To audit the resource mailbox and public folder mailbox, you need to enable auditing manually. ✓ Enable auditing manually for users without E5/A5/G5 licenses to search audit logs in the admin portal. |
How will you check these points? No worries. We are here to help you. This blog will guide you to take the necessary action and configure the required settings.
Note: All the mailbox auditing configurations can be set through PowerShell. So, you must connect to Exchange Online PowerShell using the Connect-ExchangeOnline cmdlet before running the below cmdlets.
1.Identify Audit Bypassed Mailboxes:
Even though mailbox audit logging bypass is helpful to exclude authorized accounts, service accounts (which perform genuine operations) perform the tasks without logging. But attackers can abuse its purpose and use it for their illicit activities. So, the list of audit bypassed mailboxes must be monitored regularly.
To view the list of audit bypass enabled mailboxes, run the following cmdlet.
|
1 2 |
Get-Mailbox -ResultSize Unlimited | foreach { Get-MailboxAuditBypassAssociation -Identity $_.UserPrincipalName | where {$_.AuditBypassEnabled -eq $true} | select Name,AuditByPassEnabled } |
If you find any suspicious account with auditing bypassed, you can disable audit bypass using the Set-MailboxByPassAssociation cmdlet.
|
1 |
Set-MailboxAuditBypassAssociation -Identity <UPN> -AuditBypassEnabled $false |
2.Check Whether All the Mailbox Activities are Recorded:
Run the below cmdlet to view whether the default actions are tracked for a specific mailbox,
|
1 |
Get-mailbox -Identity <UPN> | Select DefaultAuditSet |
If the DefaultAuditSet returns any logon type, then only default actions are tracked for those logon types.
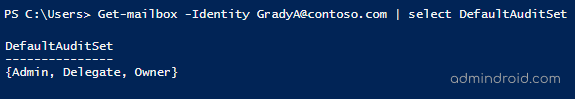
In the above screenshot, default auditing actions alone are audited for all the logon types.
You can download the enable mailbox auditing PowerShell script from GitHub to enable auditing for all the mailboxes with all/specific actions.
3.Check Whether the Newly Added Mailbox Activities are Tracked:
As said earlier, if you have enabled auditing manually before 2019, new default mailbox actions released by Microsoft will not be automatically audited.
It is easy to retrieve mailbox activities configured to be audited. But it’s challenging to get non-audited mailbox activities for all the mailboxes. To get the required data effortlessly, you can download a pre-built script to export non-audited mailbox activities from GitHub.
4.Enable auditing for Resource and Public Folder Mailbox:
Default mailbox auditing does not turn on auditing for resource and public folder mailboxes. If you want to track activities performed by those mailboxes, you need to enable auditing manually for them.
To enable auditing for all the equipment mailboxes, run the below cmdlet.
|
1 2 |
Get-Mailbox -ResultSize Unlimited -RecipientTypeDetails EquipmentMailbox | foreach { Set-Mailbox -Identity $_.UserPrincipalName -AuditEnabled $true } |
To enable auditing for all the room mailboxes, run the below cmdlet.
|
1 |
Get-Mailbox -ResultSize Unlimited -RecipientTypeDetails RoomMailbox | foreach { Set-Mailbox -Identity $_.UserPrincipalName -AuditEnabled $true } |
You can replace the “RecipientTypeDetails” according to the mailbox type.
5.Ensure Ingesting Mailbox Audit Log to Unified Audit Log.
To view audit log details of users without E5/A5/G5 licenses in the admin portal, you need to enable it manually. To turn on ingestion, run the below code snippet.
|
1 |
Get-Mailbox -ResultSize Unlimited | foreach { Set-Mailbox -Identity $_.UserPrincipalName -AuditEnabled $true } |
Note: Unlike mentioned in Microsoft doc, Microsoft allows ingestion for all the license types by default. But it may stop working without any prior announcement. So, it is better do the necessary configuration changes to avoid interruption.
Generate Exchange Mailbox Audit Reports in a Jiffy:
While PowerShell offers customization, it can be time-consuming and less user-friendly. AdminDroid Exchange reporting tool, on the other hand, provides a user-friendly interface and pre-built reports, making it effortless to access mailbox audit configurations and effectively track mailbox activities.
AdminDroid Exchange Online reporting tool provides 450+ Exchange Online statistics & auditing reports along with visually appealing smart dashboards.
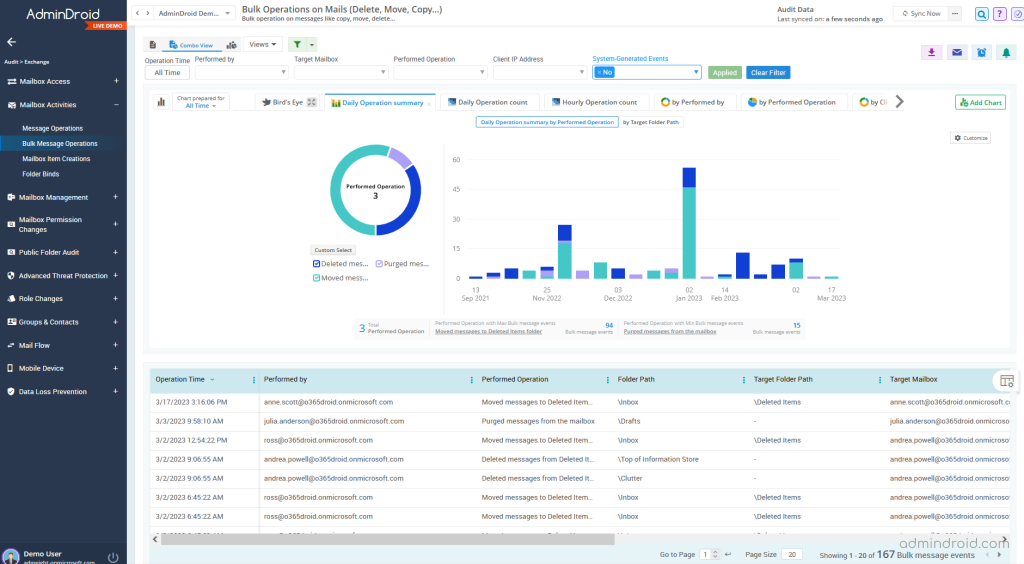
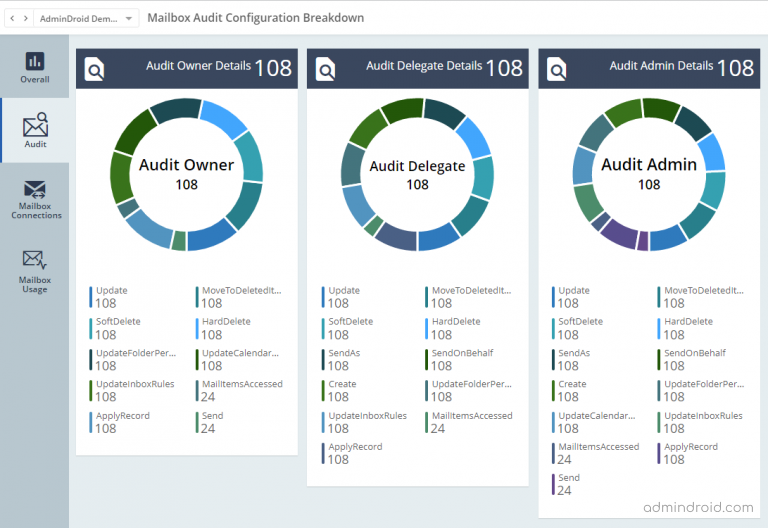
In addition, AdminDroid Microsoft 365 Manager offers a wide range of benefits. With over 1800 pre-built reports and 30+ dashboards, it allows you to effectively manage and monitor various Microsoft 365 services, including Azure AD, Teams, SharePoint Online, OneDrive, OneNote, Stream, and more.
Download the best Office 365 reporting tool and manage your M365 environment effortlessly.
I hope this blog helps you take steps to lessen or eliminate threats and identify security breach. In addition, monitor and audit unauthorized access and suspicious activities through the Audit log search.






