Multi-factor authentication (MFA) plays a vital role in securing Microsoft 365 sign-ins, effectively helping organizations prevent brute-force attacks! 🔐 Additionally, adding Conditional Access policies to Microsoft 365 secures them even more, providing an extra layer of protection against a wide range of threats. To improve and oversee CA policies, Microsoft has recently announced the general availability of the Conditional Access overview dashboard and policy templates.
Both the Conditional Access overview dashboard and policy templates, previewed in November 2021, are officially ‘Generally Available’ following improvements and enhancements.
Let’s explore the features of the Conditional Access overview dashboard and see how CA policy templates simplify the process in this blog!
What is Conditional Access Overview?
Conditional Access policies in Microsoft 365 serve as a powerful tool for organizations to enforce strict security requirements and access controls based on specific conditions. In simple words, CA policies are like if-then statements, where users must meet specific conditions when accessing resources.
The Conditional Access overview serves as an integrated dashboard, providing an extensive perspective on your Conditional Access status. For administrators, it delivers a compact policy summary, detects policy coverage deficiencies, and offers valuable sign-in activity insights within your environment.
- This dashboard offers a holistic view of your Conditional Access policies🔎, helping you make informed decisions and strengthen your security strategy.
- With its monitoring capabilities, this functionality facilitates the implementation of new Conditional Access policies for specific users, granting them access to Microsoft 365 services.
Features of Conditional Access Overview Dashboard
Hereafter, the Conditional Access overview will act as the default landing page when you click on the “Conditional Access” in Microsoft Entra ID. Navigate to the page by following the below steps:
Microsoft Entra Admin Center → Protection → Conditional Access
Note: Only global Admin or users with the Conditional Access administrator role can access this page.
The Conditional Access policy overview dashboard consists of the following three categories with each having a different feature.
1. Conditional Access Policy Summary
Admins can have a bird’s eyesight on configured policies and how they are implemented with Microsoft 365 users, devices, and applications. The Policy Summary category consists of four tiles which have the following reports regarding the CA policies.
- Check the conditional access policy status in Microsoft Entra
- Azure AD users sign-in report
- Find unmanaged and non-compliant devices in Microsoft 365
- Find applications not protected by conditional access policies
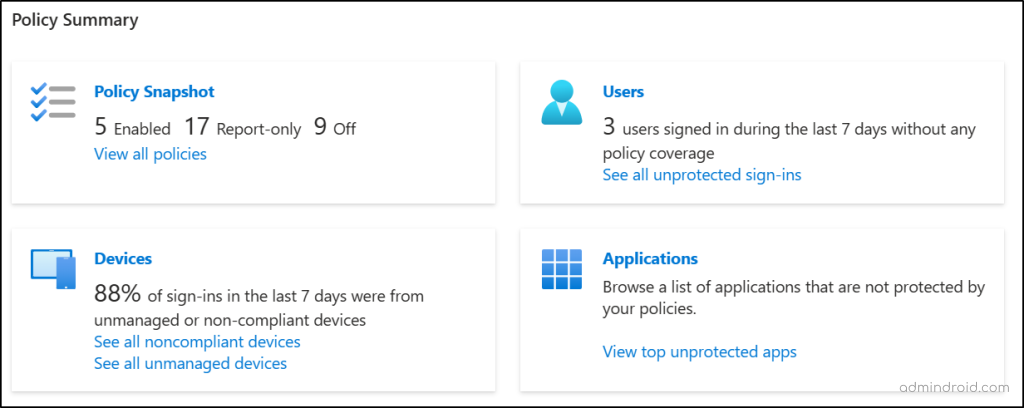
Check the Conditional Access Policy Status in Microsoft Entra
The ‘Policy Snapshot’ tile gives an overview of information about the Conditional Access policies configured in your organization. It lists the count on the total number of policies enabled, policies with the report only state, and policies with the state off.
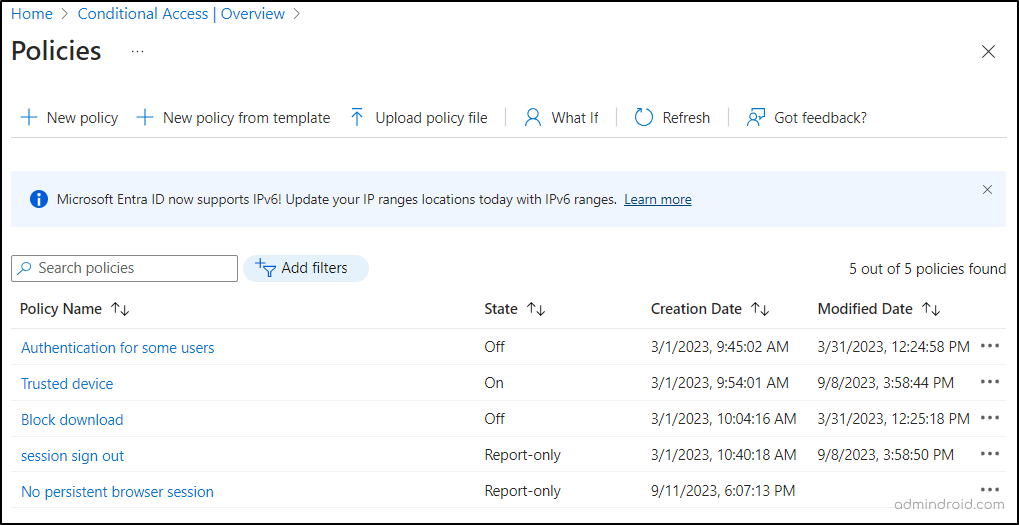
- When you click on the Policy Snapshot tile, it takes you to the “Policies” page. This page lists all the Conditional Access policies created, their status, created date, and last modified date all in one view. Admins can use this to make informed decisions regarding policy adjustments.
Azure AD Users Sign-in Report
The ‘users’ tile shows the number of users who signed in without any policy coverage in the last 7 days! Clicking on this tile takes you to a Monitoring (preview) chart with details on sign-ins, including the count granted or denied due to Conditional Access policies.
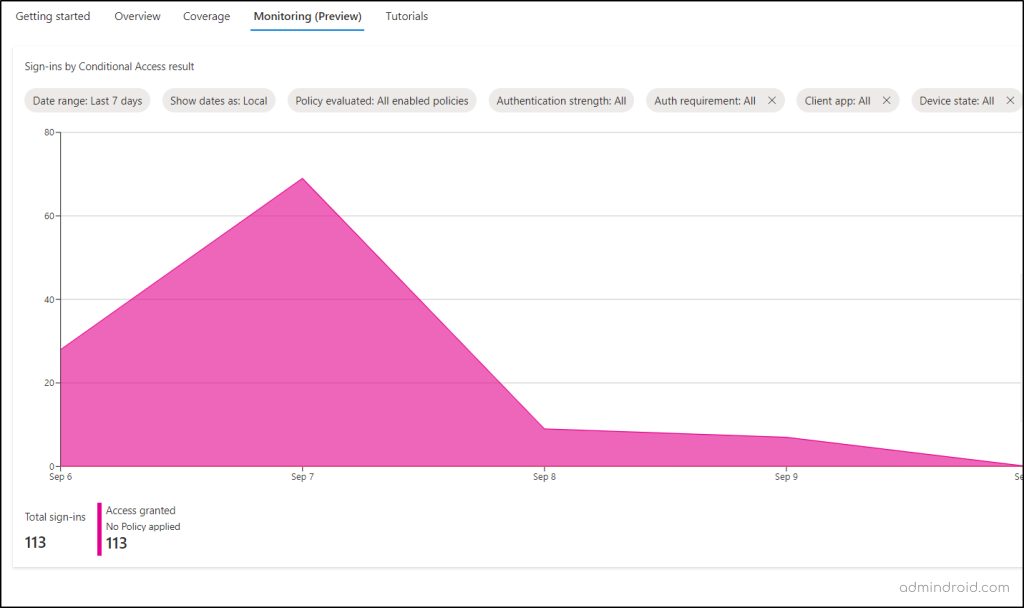
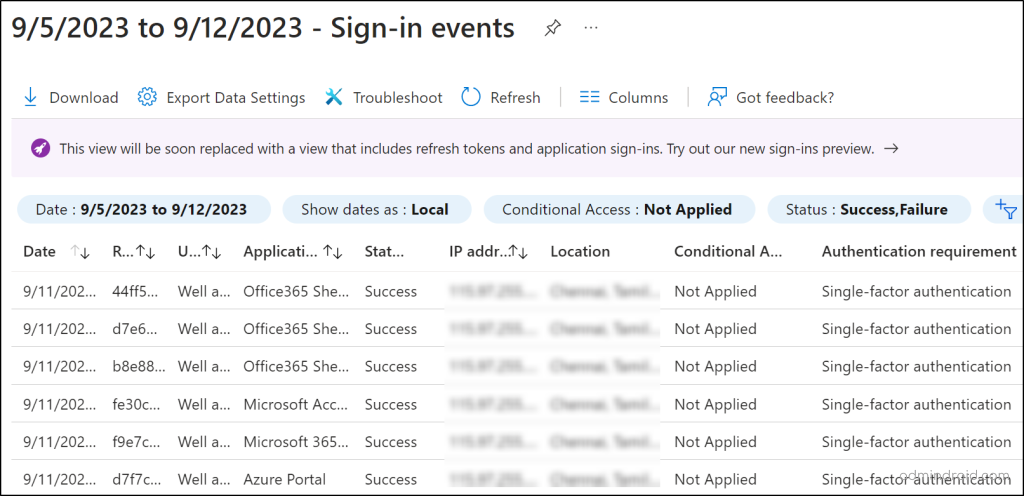
Using this tile, admins can also identify all the unprotected sign-ins happened within your Microsoft 365 organization.
Unprotected Sign-ins: User sign-ins that occurred without any coverage of Conditional Access policies. This helps admins pinpoint users who have logged in without any CA policies applied over the past week.
- With this report, admins can swiftly identify and enforce mandatory Conditional Access policies, ensuring all Microsoft accounts adhere to security standards proactively.
Find Unmanaged and Non-Compliant Devices in Microsoft 365
Here, admins can see the number of sign-ins that occurred from unmanaged or non-compliant devices within Microsoft 365. Plus, this title has two reports:
1. Non-compliant devices report
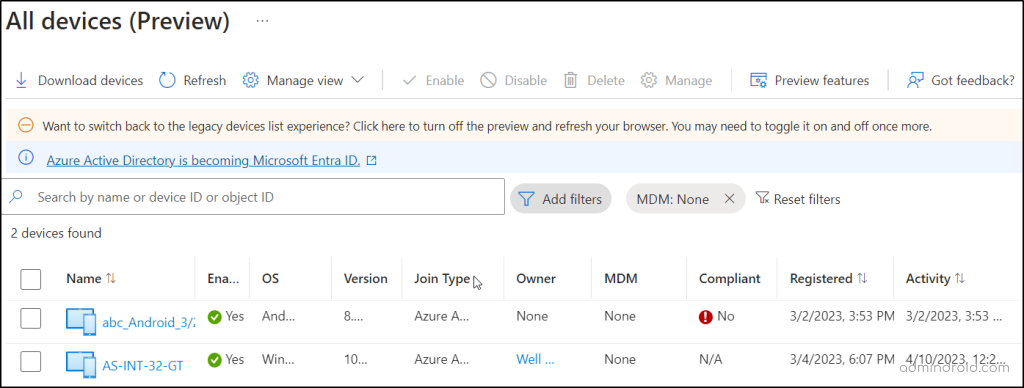
Navigating through the ‘See all non-compliant devices’ link helps to identify all the non-compliant devices in the report. This report consists of data about devices which include the device name, enabled status, OS, version, joint type, MDM, Compliant status, registered date, and last activity date. With this report, admins can plan to remove or disable the non-compliant devices from accessing your data.
2. Unmanaged devices report
On clicking the ‘See all unmanaged devices’ link, admins can see a list of all the unmanaged devices with the associated properties. This insight allows the admin to effectively manage all the unmanaged devices or remove unwanted devices as needed.
Find Applications Not Protected by Conditional Access Policies
The last tile named ‘Applications’ consists of two reports on top accessed apps concerning the coverage of CA policies.
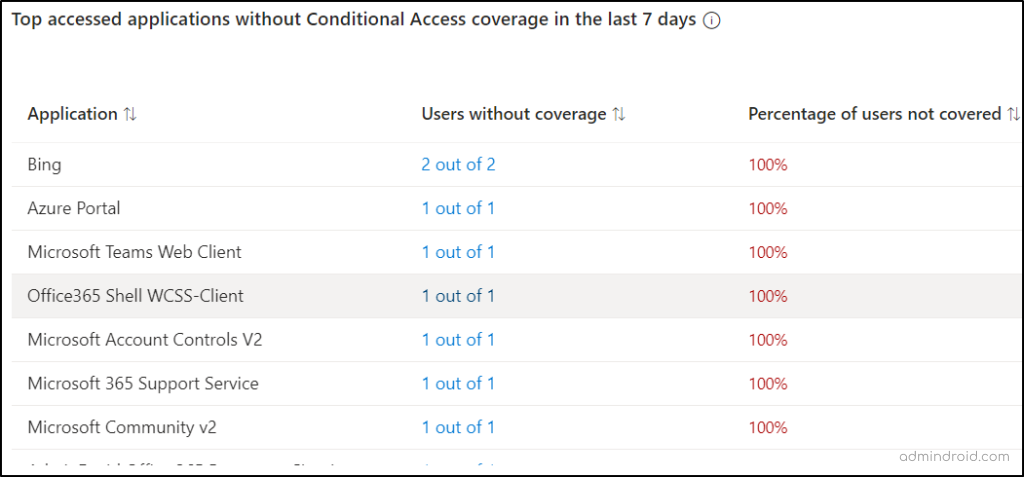
Top Accessed Applications without Conditional Access Coverage
The first report displays data on the top applications accessed without Conditional Access coverage in the last 7 days. Analyzing these reports helps in implementing new CA policies to enhance app access security.
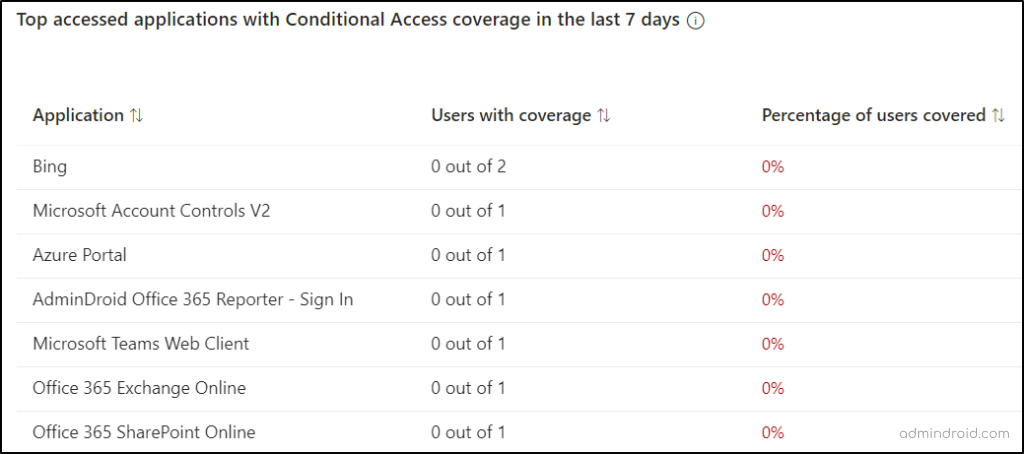
Top Accessed Applications with Conditional Access Coverage
The second report provides admins with a clear-cut view of the top accessed apps that have conditional access coverage. This report results in the removal of unwanted policies configured with the top-accessed apps.
2. Conditional Access Policy General Alerts
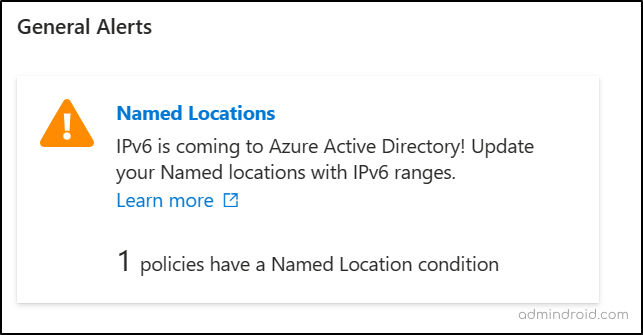
This category includes alerts related to Conditional Access policies, providing preparation for upcoming updates within Entra. These alerts also show the count of configured policies that require updating to align with Entra’s forthcoming changes.
For example, an alert notifying administrators to update their named locations to IPv6, as IPv6 is being introduced to Microsoft Entra ID.
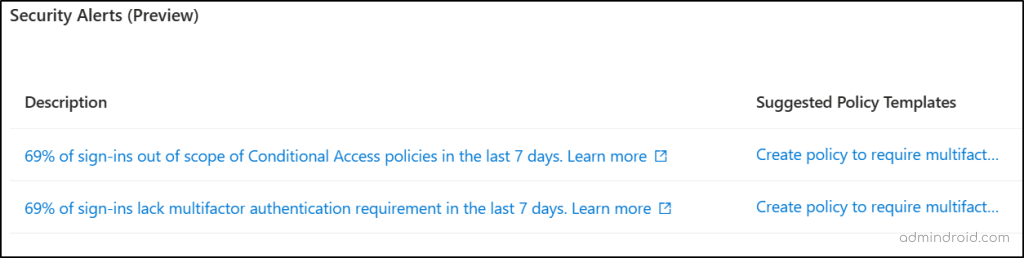
3. Conditional Access Policy Security Alerts
As of now, this alert is under the preview stage. This category provides a list of recommended security alerts that highlight potential vulnerabilities within your Microsoft 365 organization. It also suggests the policy templates to help you implement recommended security measures in response to these alerts.
Importance of Conditional Access Overview
Here are the key points highlighting the major importance of the Conditional Access overview dashboard.
Security Management: The comprehensive overview acts as the central hub, offering a spectating capability to evaluate the CA policies effectiveness.
Streamlined Policy Deployment: It helps to analyze and create new CA policies based on the alerts and provides an easy way to start monitoring the existing policies.
Ease of Monitoring: The overview dashboard also helps to maintain a user-friendly interface with the Conditional Access policy insights.
Conditional Access Policy Templates
And in the list, the second announced is the general availability of “Conditional Access policy templates”.
Microsoft 365 Conditional Access templates are a special feature designed to simplify the policy creation process. The templates are preconfigured with conditions and controls aligned with Microsoft security best practices, making policy setup easier!
As these templates have predefined conditions, they greatly simplify the policy configuration process and save the administrator’s time.
To explore more and to create a new Conditional Access policy from templates, you can refer the ‘Conditional Access policy templates’ blog.
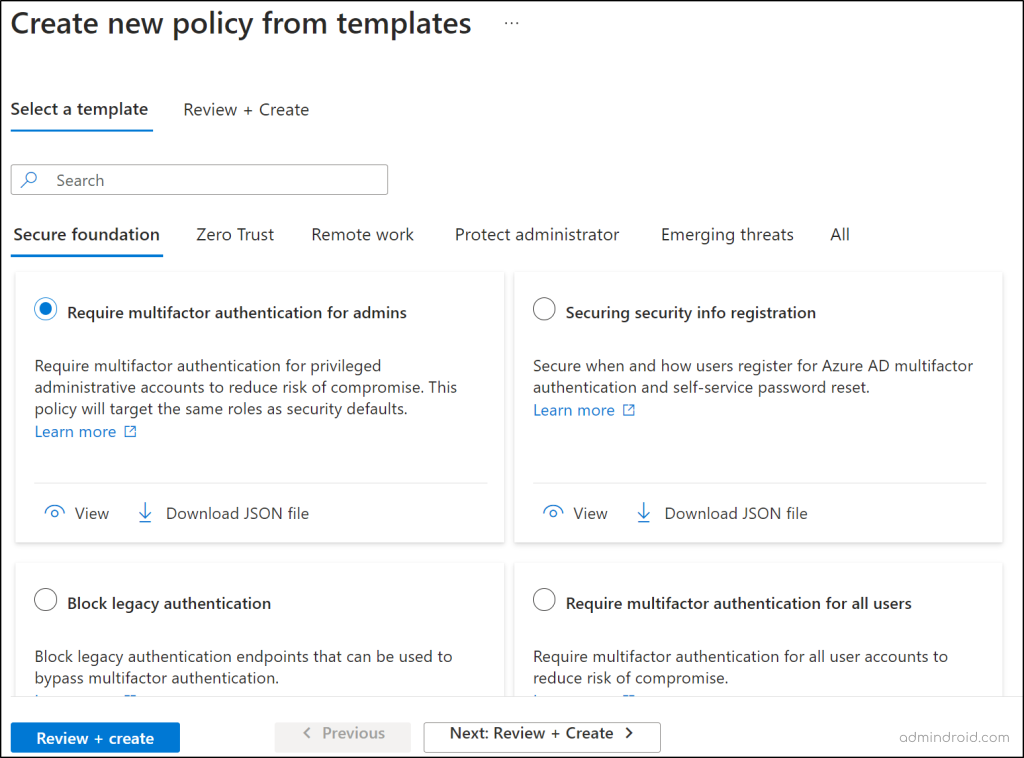
This consists of 16 predefined Conditional Access templates that are categorized into five scenarios, each addressing specific security needs:
- Secure Foundation
- Zero Trust
- Remote Work
- Protect Administrator
- Emerging Threats
Most of these 16 prebuild templates include the device-based Conditional Access policies and MFA configuration policies. They not only simplify the life of admins but also supercharge your security efforts with:
- Seamless Selection: Quickly select a template and apply it with ease.
- Streamlined Management: Effortlessly streamline the process of managing your security policies.
- Enhanced Monitoring: Spend more time monitoring your security environment.
- Up-to-date Best Practices: Stay at the forefront of security with up-to-date best practices.
- Fine-Grained Control: Enjoy advanced and finely granulated controls to meet your absolute compliance requirements.
Utilize AdminDroid for In-Depth Conditional Access Analytics
The Conditional Access Overview provides reporting capabilities but lacks crucial insights. It doesn’t detail which policies blocked specific user sign-ins or highlight sign-ins without CA. Additionally, it overlooks important aspects such as unauthorized access from unusual locations, visibility into suspicious login attempts, and more vital insights.
Therefore, to address this concern, we introduce AdminDroid, a powerful Microsoft 365 reporting tool that seamlessly bridges the information gap between Entra ID reports.
AdminDroid offers in-depth insights into your Conditional Access (CA) policies, giving you a detailed look at their effectiveness in safeguarding your organization’s data and resources. Their comprehensive reports go beyond basic reporting, helping you understand how CA policies impact user access, analyze sign-in patterns for anomalies, assess the efficacy of report-only policies, pinpoint potential conflicts or loopholes, and much more! AdminDroid M365 reporting tool elaborately categorizes the CA report collections into three sections:
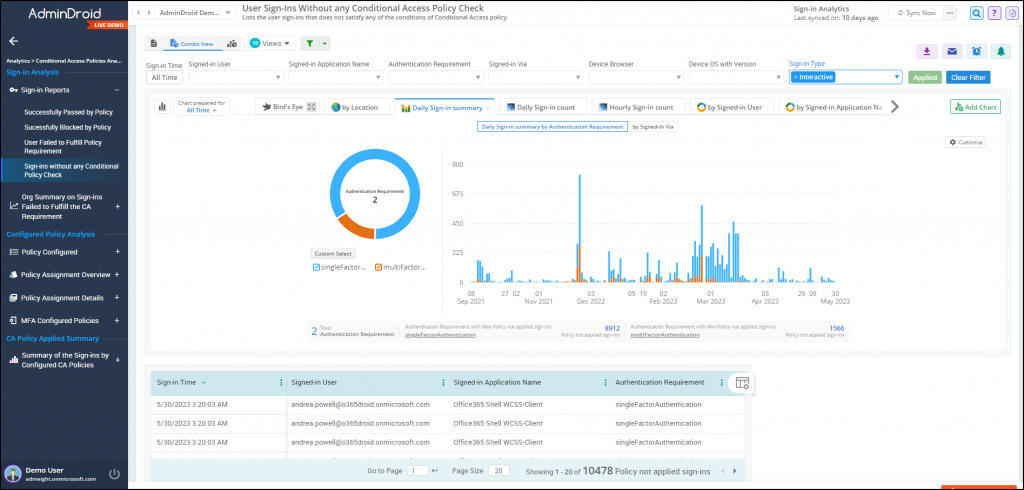
Sign-in Analysis
- Reports on sign-in passed/blocked by CA
- Conditional Access failure summary
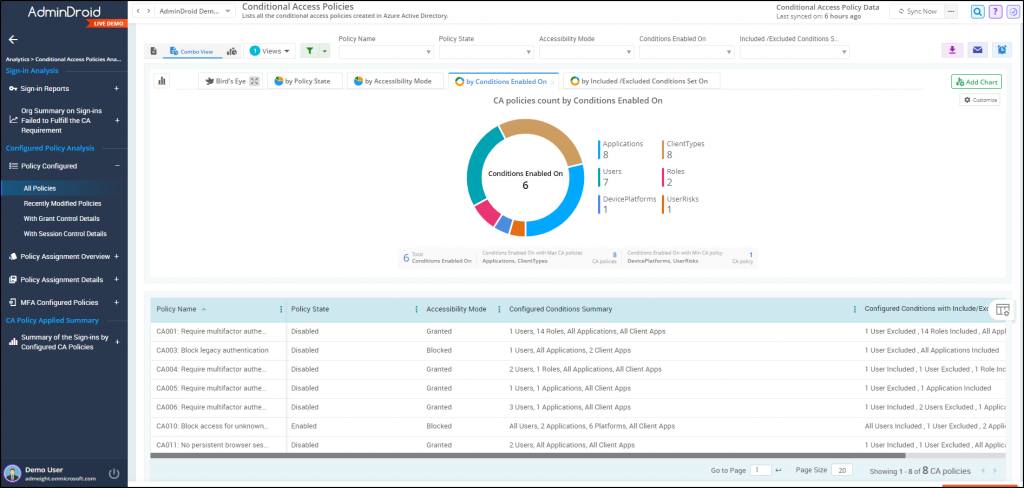
Configured Conditional Access Policy Analysis
- Configured policy reports
- CA policy assignment overview reports
- CA Policy assignment details reports
- MFA configured CA policies Report
CA Policy Applied Summary
- Sign-ins using CA policies summary
But AdminDroid doesn’t stop at Conditional Access analytics! It extends its capabilities across various Microsoft 365 services, offering comprehensive usage and audit reports.
Overall, the AdminDroid M365 reporting tool provides 1800+ reports and 30+ powerful dashboards to monitor your entire Microsoft 365 hassle-free. Plus, it offers a 15-day trial to experience its extensive reporting capabilities firsthand. AdminDroid also provides access to 120+ Azure AD reports, all for completely FREE.
Download AdminDroid today and see how it reduces your workload for Microsoft 365 management!
Closing Lines
Overall, the Conditional Access overview and templates in Microsoft 365 are a game-changer for organizations seeking to enhance their security. These functionalities not only offer a robust defence, it also help admins gain better insights into the CA policies and make the creation easy with the templates!
I hope you have obtained clear-cut knowledge about the CA overview and templates. If you have any questions or need assistance with this blog, please feel free to reach out.
Stay secure, stay vigilant!






