Admins always have their hands full handling a variety of complex tasks, from onboarding to offboarding users in Microsoft 365. Amid these demands, managing groups and access rights can be an additional workload for them😑.
Fortunately, Microsoft understands this and provides admins with a solution through the “Self-service group management” setting in Microsoft Entra ID. This feature empowers users to create and manage their own security groups or Microsoft 365 groups, reducing the burden on admins💯.
Ready to implement self-service group management in your organization? Let’s get started!
Overview of Self-Service Group Management Setting
Self-service group management is a feature within Microsoft Entra ID that enables admins to grant users the ability to control various aspects of group management in Microsoft 365.
By default, the self-service group management feature allows users to create security and Microsoft 365 groups. It also provides group owners with the ability to delegate control of group memberships and approve or deny membership requests.
Note: Self-service group management feature is not applicable for mail-enabled security groups or distribution lists.
Default Group Policy Setting for Security and Microsoft 365 Groups
Here’s a breakdown of the default group behavior when a user attempts to create security and Microsoft 365 groups using Azure portals, API, and PowerShell:
For Security Groups:
- Azure AD PowerShell, Azure portal – The default group policy allows only owners to add members to the groups created.
- MyApps Groups Access panel – The default group policy sets other users to join directly to the created group.
For Microsoft 365 Groups:
- The default group policy allows other users to join the group directly when created through Azure, using APIs, or PowerShell.
Is Self-Service Group Management Setting Beneficial?
The default configuration of self-service group management setting can be quite beneficial for several scenarios.
- For example, imagine you’re an admin responsible for managing access rights to a SaaS application in your organization. However, you’re juggling numerous other critical tasks, so you are seeking an alternative approach. In such cases, the self-service group management setting can be a lifesaver. It enables you to delegate access management to the application owner. The business owner can create a new group, and add members to the group, all without the need for administrator approval. This delegation of responsibilities saves valuable time for admins and streamlines access management.
- In a different scenario, let’s say a user needs to collaborate with owners from various teams for a project discussion. In this case, the self-service group management setting enables the user to create a new group and add the relevant team owners to that group. This reduces the reliance on admins to create new groups, saving time for both the user and the admins. This not only streamlines collaboration but also enhances overall efficiency.
- Another example would be, if two users have independently set up SharePoint Online sites and wish to grant each other’s teams access to their respective sites, they can create a single group in Microsoft 365. Subsequently, they can choose this group in SharePoint Online to provide access to their sites. When someone requests access, they can do so via the MyApps Groups Access Panel. After approval, individuals gain access to SharePoint Online sites automatically.
Now, you might wonder if giving users such high privileges could compromise organizational security. That’s a valid concern! Also, enabling this feature for all users could result in the creation of unnecessary groups in Microsoft 365. So, it’s crucial to assess whether your organization has specific needs like the ones described above. If so, you can leave the default setting as it is.
Otherwise, you should wisely fine-tune the self-service group management setting to align with your organizational requirements. Let’s explore the process of controlling self-service group management in Microsoft 365.
Manage Self-Service Group Creation in Microsoft Entra ID
Here are the steps to make a group available for self-service in Microsoft Entra ID.
Note: This setting only restricts access to group information in the MyApps Groups Access Panel. It does not restrict access to group information via other methods like Microsoft Graph API calls or the Microsoft Entra admin center.
1. Navigate to the Microsoft Entra admin center.
2. Scroll down to “Identity” in the navigation pane.
3. Expand Groups and click “Group settings”.
4. Manage Group Membership and Group Information Access
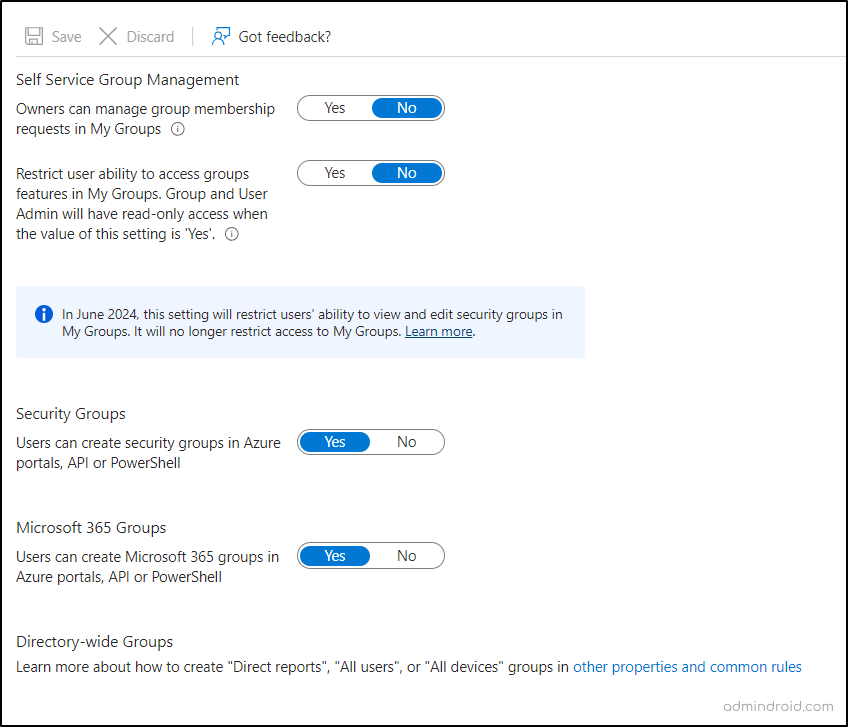
a) Set ‘Owners can manage group membership requests in the Access Panel’ to Yes or No.
- When this setting is enabled, users can identify and request access to groups through the MyApps Groups Access portal. And group owners possess the authority to either approve or reject these access requests.
b) Set ‘Restrict user ability to access groups features in My Groups’ to No.
- When enabled, this setting will limit users (excluding global admins and owners) from accessing group information within the MyApps Groups Access panel.
Note: By June 2024, the setting “Restrict user access to My Groups” will be modified to “Restrict users ability to see and edit security groups in My Groups”. If the current setting is “Yes,” end users will retain access to My Groups in June 2024, but won’t have visibility into security groups.
5. Control Who Can Manage Security Groups and Microsoft 365 Groups
a) Set ‘Users can create security groups in Azure portals, API or PowerShell’ to Yes or No.
| If the ‘users can create security groups in Azure portals, API or PowerShell’ is set to “Yes” | All Microsoft 365 users will be given the ability to create security groups via Azure portals, APIs, PowerShell, or the MyApps Group Access panel. |
| If the ‘users can create security groups in Azure portals, API’ is set to “NO” | If set to “No,” users are entirely restricted from creating or making changes to existing security groups. They can only manage the group memberships of the group they are owner of. |
b) Set ‘Users can create Microsoft 365 groups in Azure portals, API or PowerShell’ to Yes or No.
| If the ‘users can create Microsoft 365 groups in Azure portals, API’ is set to “Yes” | All Microsoft 365 users are granted the privilege to create Microsoft 365 groups using Azure portals, APIs, PowerShell, or the MyApps Group Access panel. |
| If the ‘users can create Microsoft 365 groups in Azure portals, API’ is set to “NO” | Users are completely prohibited from creating or editing existing security groups. They retain permission to manage the group memberships only if they are the group owners. |
After configuring the above group settings in Entra ID based on your requirement, proceed to save the setting.
Important: If you want to restrict Office 365 group creation only to admins, just set all the self-service group management settings to “No”.
You can also manage user permissions for creating security groups by utilizing the “allowedToCreateSecurityGroups” property in the authorizationPolicy object. Additionally, you can control the creation of Microsoft 365 groups by users through the configuration of the “EnableGroupCreation” object in the groupSettings object.
Key Points to Note About Self-Service Group Management
- The setting may take up to 15 minutes to take effect in your organization.
- The settings do not apply to service principals; even if the permission to create groups is set to “No,” service principals can still create groups.
- To enable certain users to create security and M365 groups while restricting others, assign the users with group creation rights, such as the group administrator role.
- For users to request to join and for owners to approve/deny membership requests for security or Microsoft 365 groups, they need a Microsoft Entra ID P1 or P2 license. Without it, users can still manage groups in the MyApps Groups Access panel, but they can’t create groups that need owner approval or request to join groups.
Now, everything is in your hands! We have demonstrated the effect of each and every configuration in the self-service group management setting. So, configure it properly without compromising the Microsoft 365 security.
I hope this blog brings you more information about the implementation of self-service group management settings in Microsoft Entra ID. Furthermore, if you have any queries, you can reach out to us through the comments section.