In a world where digital threats loom large; Microsoft security measures stand as a vigilant guardian for its users. Microsoft’s security pros are so keen, checking out 65 million threats every day to keep us safe from any attackers’ game.
Stepping up their security game, Microsoft is now initiating an automatic rollout of basic Conditional Access policies in Microsoft Entra ID. These policies place multi-factor Authentication (MFA) at the forefront, serving as the primary defense against malicious attacks.
Curious to know what those Microsoft Entra’s Conditional Access policies are? Dive into the blog to find out!
What Are Conditional Access Policies in Microsoft 365?
Conditional Access policies are indeed a powerful feature in Microsoft 365 that allows organizations to enforce strict security requirements and access control on specific conditions.
These policies function as conditional “if-then” statements, allowing you to set specific access controls based on a variety of conditions. They are often used to add extra layers of security, such as enforcing multi-factor authentication, specifying device requirements, and more.
You might be wondering why Microsoft is rolling out MFA-based Conditional Access policies when we have the flexibility to configure various conditions. Well, MFA serves as a crucial defense against password spray, phishing, and replay attacks. So, Microsoft decided to use it along with CA policies to achieve 100% MFA for all users.
Got it? Without any further delay, let’s see the Microsoft-managed Conditional Access policies now!
5 Automatic Conditional Access Policies in MS Entra ID
As per the recent roadmap update 183905, Microsoft is rolling out five MFA-based Conditional Access policies to its customers, aimed at enhancing security. The five policies are:
- Multifactor authentication for admins accessing Microsoft Admin Portals
- Multifactor authentication for per-user multifactor authentication users
- Multifactor authentication and reauthentication for risky sign-ins
- Block device code flow for Microsoft 365 users
- Block legacy authentication in Microsoft 365
These 5 CA policies are designed to provide a baseline level of security for all tenants. They are based on Microsoft’s deep understanding of cybersecurity best practices and are designed to protect against common attacks.
Admins with at least the Conditional Access administrator role can be able to see these Conditional Access policies by following the navigation below.
- Sign in to the Microsoft Entra admin center.
- Scroll down to “Protection” and select “Conditional Access”.
- Click the “Policies” in the navigation pane, you can be able to view the newly rolled out Microsoft-managed policies there.
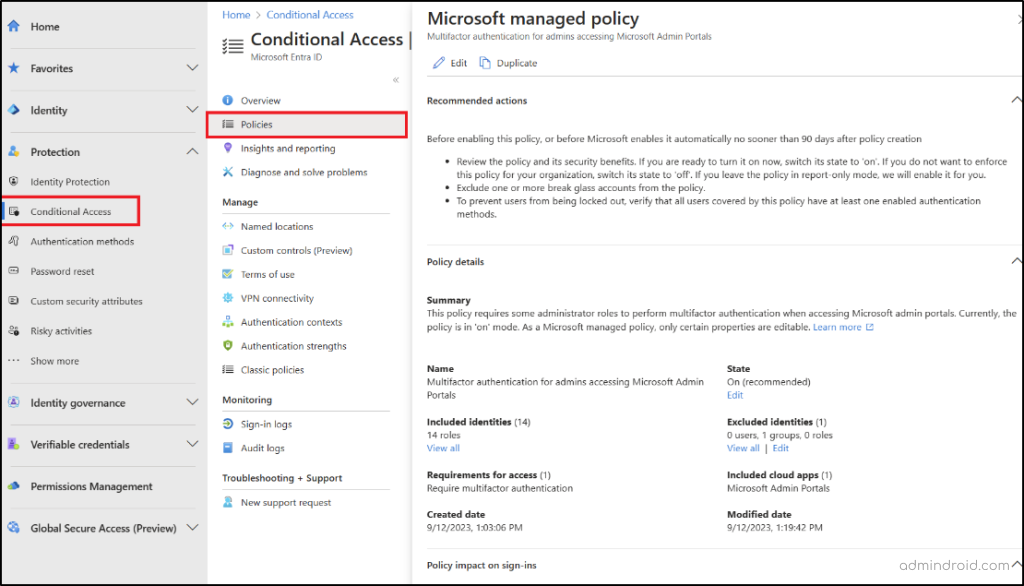
Let’s see the auto rolled out Conditional Access policies one by one in detail.
| Require MFA for admin portals | Applies to admins when accessing admin portals. |
| Require MFA for per-user MFA users | Applies on existing per-user MFA customers. |
| Require MFA for high-risk users | Applies to users with high-risk detection. |
| Block Device Code Flow | Applies to users who haven’t used device code flows in the past 25 days |
| Block Legacy Authentication in M365 | Applies to sign-ins using legacy protocols |
1. MFA Enforcing CA Policy for Admins Accessing Microsoft Admin Portals
Admins play a pivotal role in managing and safeguarding sensitive information across various admin portals like Entra, Exchange Online admin center, and some more. And if they were targeted by brute force or password attacks, it could lead to a catastrophic breach where sensitive data is at risk.
To prevent such things from happening, Microsoft is rolling out the “Require MFA for admins accessing Microsoft admin portals” policy for 14 admin roles.
Even if attackers manage to obtain an admin’s password through various means, they will still face a formidable obstacle: Multi-factor authentication! This added layer of security requires a second form of verification beyond just a password, making it harder for attackers to access the admin’s accounts.
Target: This policy is for tenants with Microsoft Entra P1 and P2 licenses with disabled security defaults.
2. Multifactor Authentication for Per-User Multifactor Authentication Users
Many organizations continue to rely on per-user MFA, even though Microsoft recommends admins to convert from per-user to Conditional Access MFA. This recommendation is made to enable more fine-tuned MFA requirements for all cloud apps. Because per-user MFA allows you to skip MFA only for specific IP addresses, and it doesn’t offer much flexibility for other security conditions.
Microsoft, on the other hand, emphasizes the importance of various security conditions such as named locations and device-based conditions in CA policy.
So, to discontinue support for per-user MFA and bolster security measures, Microsoft has introduced the Conditional Access MFA policy. This policy covers all the existing per-user MFA users and requires MFA which signing into the cloud apps.
Target: This policy is for Microsoft Entra ID P1 and P2 tenants with the security defaults feature turned off and with fewer than 500 users using per-user MFA.
3. Multifactor Authentication and Reauthentication for Risky Sign-Ins
In the latest defense report, Microsoft highlighted that they have successfully blocked nearly 4,000 attacks per second this year. This revelation is indeed eye-opening, showing how quickly cyberattacks target organizations without stopping. In response to this ever-present threat, Microsoft has auto rolled out a policy “Risk-based Conditional Access”.
Under this policy, when a user account is flagged for high-risk behavior, including signs of anonymous sign-ins or compromised credentials, they will be prompted for MFA.
Target: This policy is for Microsoft Entra ID P2 tenants with sufficient licenses for each user.
That’s it! Microsoft starts auto deploying these CA policies in early November itself. You can check it in Microsoft Entra ID. If it’s not showing up in your Microsoft Entra ID yet, the rollout for your organization should be on its way soon.
4. Blocking Device Code Flow with Conditional Access
Device code flow is an authentication method used by input-constrained devices like smart TVs. However, attackers can exploit this flow in phishing and brute-force attacks by tricking users into approving fraudulent authentication requests.
To mitigate this risk, Microsoft has introduced a Conditional Access policy to block device code flow by default for organizations that haven’t used it in the past 25 days. This ensures a more secure authentication process and reduces the chances of unauthorized access.
5. Block Legacy Authentication in Microsoft 365
Legacy authentication protocols like POP, SMTP, IMAP, and MAPI lack support for modern security measures such as multifactor authentication (MFA), making them a common attack vector.
A recent Microsoft analysis revealed that 99% of password spray attacks target legacy authentication protocols. To prevent such attacks, Microsoft has taken action by disabling or blocking these outdated authentication methods.
Yes. Microsoft now enforces a Conditional Access (CA) policy to block legacy authentication by default. This policy prevents sign-ins from older clients and applications using these insecure protocols, reducing the risk of unauthorized access.
Is It Possible to Customize the Microsoft-Managed Conditional Access Policies?
You have the flexibility to customize these automatic CA policies in Azure AD to suit your organization’s needs. For example, you can exclude specific groups or users as per necessity. But make sure you have excluded the break glass account or emergency access accounts from these CA policies.
Suppose you want to make more changes to these policies; you can use the Duplicate option. This allows you to create a new policy with extra conditions that better align with your organization’s security needs.
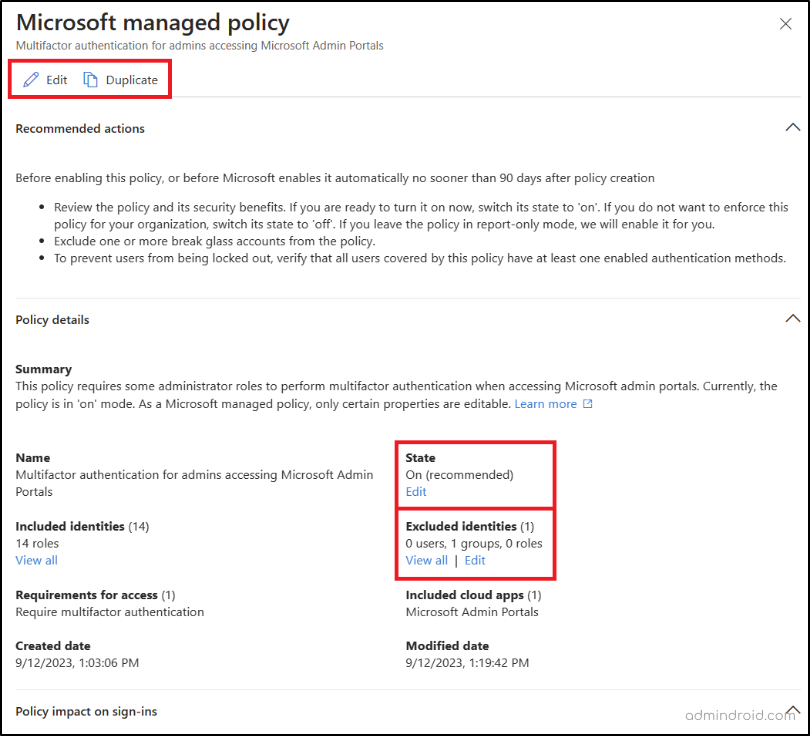
Also, initially, Microsoft is rolling out these policies in report-only mode. If you want to enforce the policy sooner; you can enable it.
Important:
- Microsoft-managed policies are not counted toward the Conditional Access policy creation limit. So, it will not impact the Conditional Access policy creation limit.
- If you already have a policy in the “on” state with the same conditions as the Microsoft-managed policies, these policies will not automatically get enforced in your tenant.
- You can have over 90 days to review and customize the Microsoft-managed Conditional Access policies. Additionally, you’ll receive an email and a notification 28 days before Microsoft enforces them on your tenant.
Monitor Automated Conditional Access Policy in Microsoft Entra ID
Admins can keep a close eye on policy enforcement through the “Policy impact on sign-ins” section within the respective Conditional Access policy. This section provides a convenient summary of the policy’s effects within their organization.
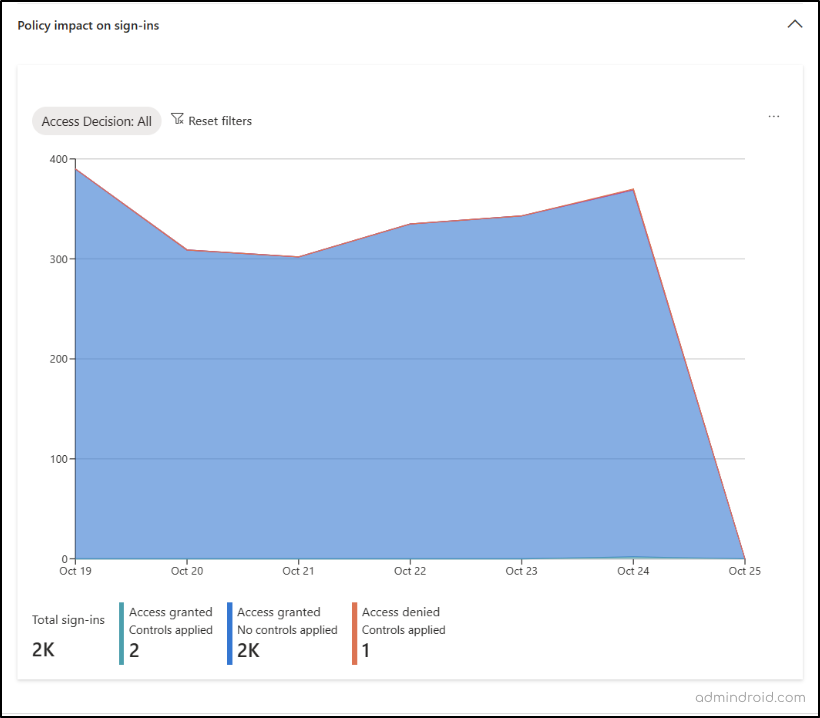
For a more comprehensive breakdown of policy enforcement, you can explore the “Sign-in logs” and “Audit logs” options on the Azure AD Conditional Access Page. There, you can gain in-depth insights into whether these policies have been successfully applied, track users who were allowed or blocked due to the policy, and more. This detailed view ensures you thoroughly monitor Conditional Access policies in Microsoft 365. Not only the policy enforcement, but you also need to keep on Conditional Access settings changes by comparing tenant configuration with M365DSC.
Effortlessly Monitor Conditional Access Policies with AdminDroid
Navigating the audit logs and sign-in logs provides a broad view of policy enforcement in your tenant. However, for an intricate breakdown of Conditional Access policies, these logs fall short. Additionally, there are times when you lose sight and wonder if certain users are added or excluded from the policies. In such instances, you might decide to scroll through policies and review users – a process that consumes time.
But no more such things! Achieve an easy and drilled-down monitoring of your CA policies with AdminDroid!
AdminDroid Azure AD reporter, acts as your magnifying glass for CA policy monitoring, providing inch-by-inch details. With AdminDroid, you can zoom in on drilled details of CA policies, such as the exact count of successful sign-ins, failed sign-ins for each user, and others.
To ensure that the policy is configured for the right users, there’s a separate report available: “MFA Policy Assignments”
Here are some of the deep-analyzed AdminDroid’s Conditional Access reports benefits for the admins:
CA Policies with MFA Requirement
- MFA-configured CA policies
- Assignment conditions of MFA-enabled policies
Sign-in Audit Reports
- Sign-ins blocked by CA policy
- Sign-ins successfully passed the CA policy
- Sign-ins failed to bypass the CA policy
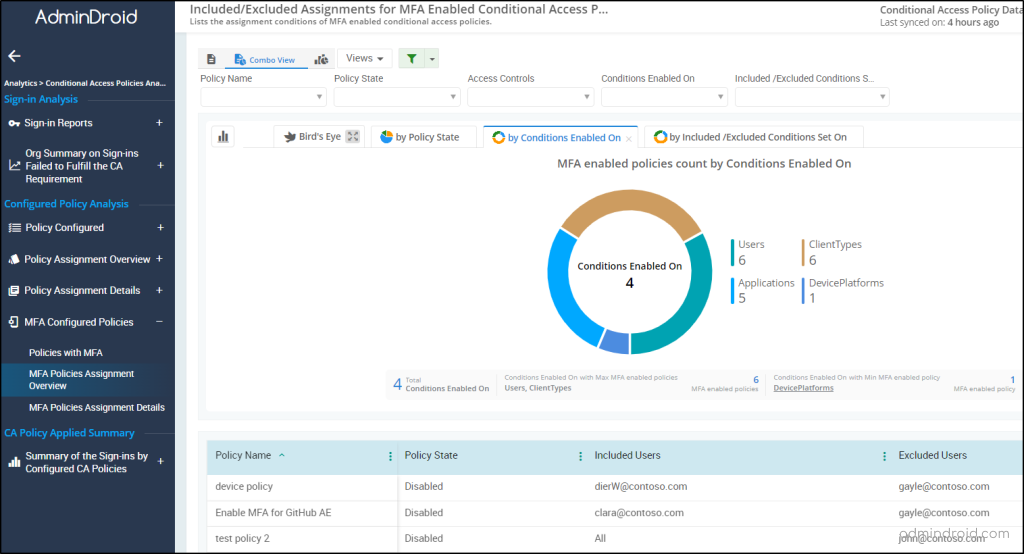
AdminDroid doesn’t just stop at providing insightful CA policy reports; it goes above and beyond, allowing you to monitor successful user logins to risky sign-ins entirely from your seat! Yes, AdminDroid offers 120+ auditing and statistical reports, and 10+ insightful dashboards, all completely free of cost for effective Azure AD management.
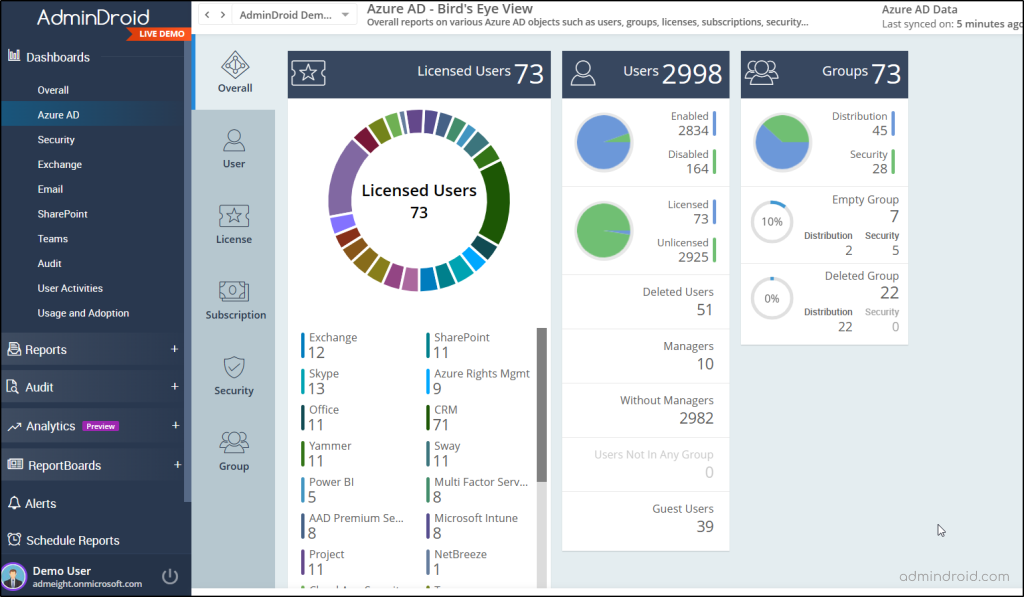
Besides the above, AdminDroid offers 1800+ reports to give full control of M365 resources such as Exchange Online, SharePoint Online, One Drive, and more.
So, give a 15-day free trial to AdminDroid, and we are confident you will realize its capabilities and continue to use it.
Furthermore, if you have any queries, feel free to reach out to us in the comment section. Thanks for reading!