On Day 31 of Cybersecurity Awareness Month, let’s wrap up our series with a super handy feature: creating an auto-labeling policy to apply sensitivity labels to your content automatically. For a recap on other significant settings to enhance security, check out our Microsoft 365 Cybersecurity blog series.
Throughout this month, we’ve shared some great tips to enhance your security, and now it’s time to spotlight a standout feature from Microsoft Purview Information Protection. Imagine your data—whether it’s in transit or at rest being automatically protected! How does this work? Microsoft Information Protection uses auto-labeling policies to monitor your content for the presence of sensitive information, like credit card numbers, Social Security Numbers (SSN), etc. When such sensitive info is detected, a sensitivity label is automatically applied to that content, restricting access to unauthorized users.
Now, let’s get into the steps to create an auto-labeling policy in Microsoft 365. But first, let’s take a quick look at how sensitivity labels work in Microsoft 365.
What are Sensitivity labels in Microsoft 365?
Sensitivity labels help protect sensitive content across Microsoft 365, including documents and emails across platforms like SharePoint, OneDrive, Teams, Exchange, Microsoft 365 Groups, and Microsoft purview data map. These labels classify documents and emails based on their sensitivity and apply security features like encryption and content markings. You can check out detailed licensing requirements for sensitivity labels here.
By default, only global administrators can create and manage sensitivity labels. However, compliance officers can also be granted access to manage these labels if they are added to specific role groups such as Information Protection, Information Protection Admins, Information Protection Analysts, Information Protection Investigators, and Information Protection Readers.
Applying Sensitivity Labels
Microsoft provides two ways to apply sensitivity labels:
- Manual Application: Users can select and apply labels by themselves.
- Automatic Application: Labels can be automatically applied based on predefined rules.
In this blog, we will explore how to create an auto-labeling policy to apply sensitivity labels automatically to the content in Microsoft 365.
How to Apply Sensitivity Labels to Content Automatically?
After creating a sensitivity label, you can automatically assign it to files and emails that meet specific conditions. Auto-labeling policies eliminate the need to train users on how to classify data accurately. This way, users can focus on their work while the system ensures compliance and data protection automatically. When defining these conditions, you can also create custom Sensitive Information Types (SITs) to detect organization-specific confidential data and ensure the correct label is applied automatically.
Note: Setting up auto-labeling policies is also part of the Microsoft Information Protection Secure Score recommendation.
There are two main methods for automatically applying sensitivity labels:
1. Auto-labeling for Files and Emails (Client-side Labeling)
Auto-labeling for Office apps applies labels during document editing or email composition. Users can accept or reject the labels suggested by the system. Labels can be applied directly to:
- Individual items (files, emails, meetings)
- Groups and sites (Teams, Microsoft 365 Groups, SharePoint sites)
- Schematized data assets in Microsoft Purview Data Map
When the information entered in a document or Outlook email matches your configured conditions, the system will automatically apply or recommend the sensitivity labels based on your auto-labeling settings.
License Requirement:
To use automatic client-side labeling, users need an Azure Information Protection P2 license, which comes with: Enterprise Mobility + Security E5/A5/G5, Microsoft 365 E5/A5/G5, Microsoft 365 E5/A5/G5/F5 Compliance, Microsoft 365 F5 Security & Compliance, and Microsoft 365 E5/F5/G5 Information Protection and Governance.
Client-Side Auto-labeling Behavior:
- If a file isn’t labeled yet, the highest priority sublabel will be applied.
- If a file already has a sub label from the same parent, no changes will be made.
2. Auto-labeling Policy (Service-side Labeling)
You must create an auto-labeling policy to automatically apply sensitivity labels to the content stored in SharePoint and OneDrive (at rest) and for emails sent through Exchange Online (in transit). It ensures that labels are applied immediately across the organization.
License requirement: Automatic service-side labeling requires Information Protection for Office 365 – Premium license.
Service-Side Auto-labeling Behavior:
For service-side auto-labeling, if multiple sub labels from the same parent meet the conditions, the sub label with the highest priority will be selected.
Difference Between Client-side and Server-side Sensitivity Auto-Labeling
Here’s a simplified table showing the major differences between both the auto-labeling methods.
| Feature | Auto-labeling for Files and Emails | Auto-labeling Policy |
| App Dependency | Yes (minimum versions) | No |
| Restrict by Location | No | Yes |
| Conditions: Sharing Options and Additional Options for Email | No | Yes |
| Conditions: Exceptions | No | Yes |
| Support for PDF Files | No | Yes |
| Support for Images | No | Yes |
| Recommendations, Policy Tooltip, and User Overrides | Yes | No |
| Simulation Mode | No | Yes |
| Apply Visual Markings | Yes | Yes (email only) |
| Exchange Attachments Checked for Conditions | No | Yes |
| Label Incoming Email | No | Yes |
| Assign a Rights Management Owner for Emails Sent from Another Organization | No | Yes |
| For Emails, Replace Existing Label That Has Same or Lower Priority | No | Yes |
| Override IRM Encryption Applied Without a Label | Yes (if user has minimum usage right of Export) | Yes (email only) |
How to Create an Auto-labeling Policy in Microsoft 365?
In this example, let’s check how to create an auto-labeling policy to detect sensitive information types, like an International Bank Account Number (IBAN), in documents at rest and emails in transit. First, ensure you have a document containing this sensitive information type (at rest) so you can observe the process in action.
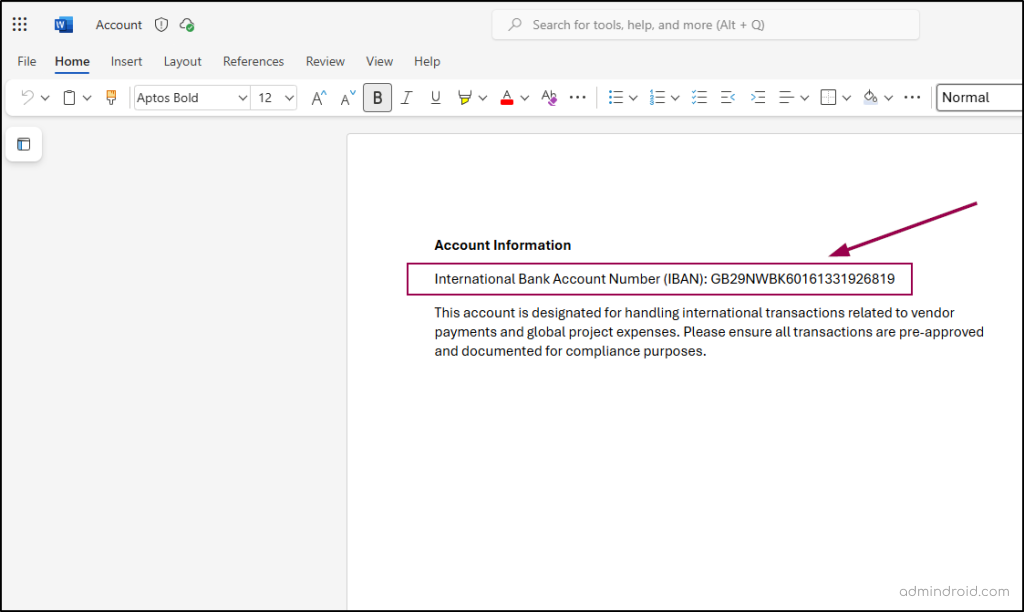
The first step in creating an auto-labeling policy is to create the sensitivity label itself.
Create Sensitivity labels
To create and publish sensitivity labels in Microsoft 365, follow the steps below.
- Sign in to the Microsoft Purview compliance portal.
- Navigate to the Information Protection option under Solutions.
- Select Sensitivity labels -> Create a label.
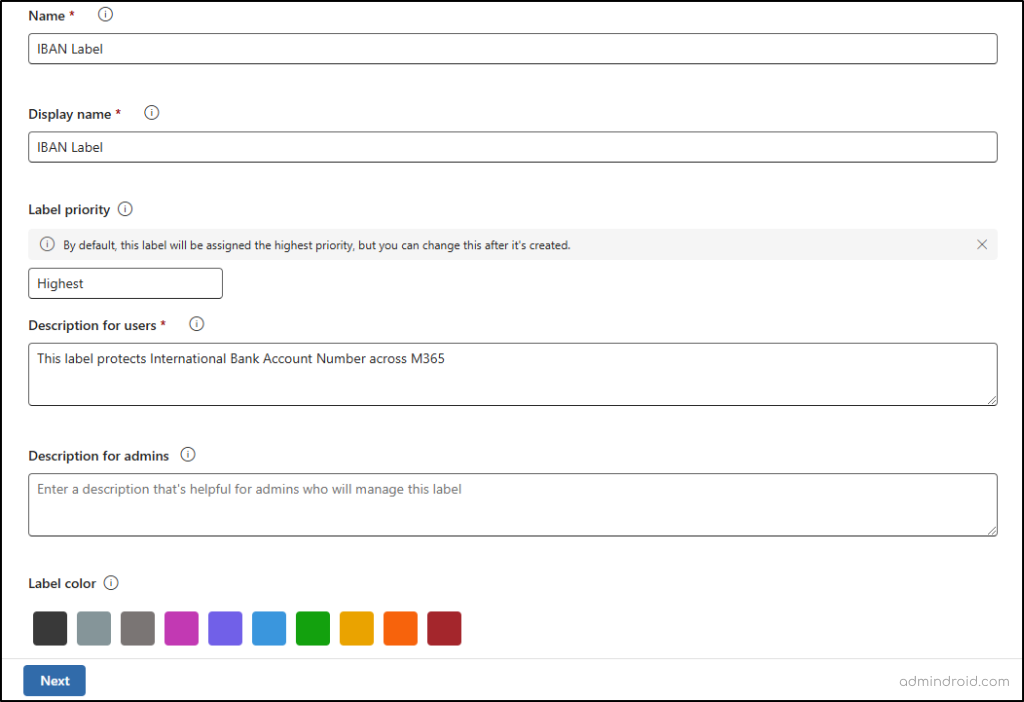
- Enter the name, display name, label priority, and description for your label, then click Next.
- On the “Define the Scope for This Label” page, specify where the label will apply (e.g., files, emails, Teams chats).
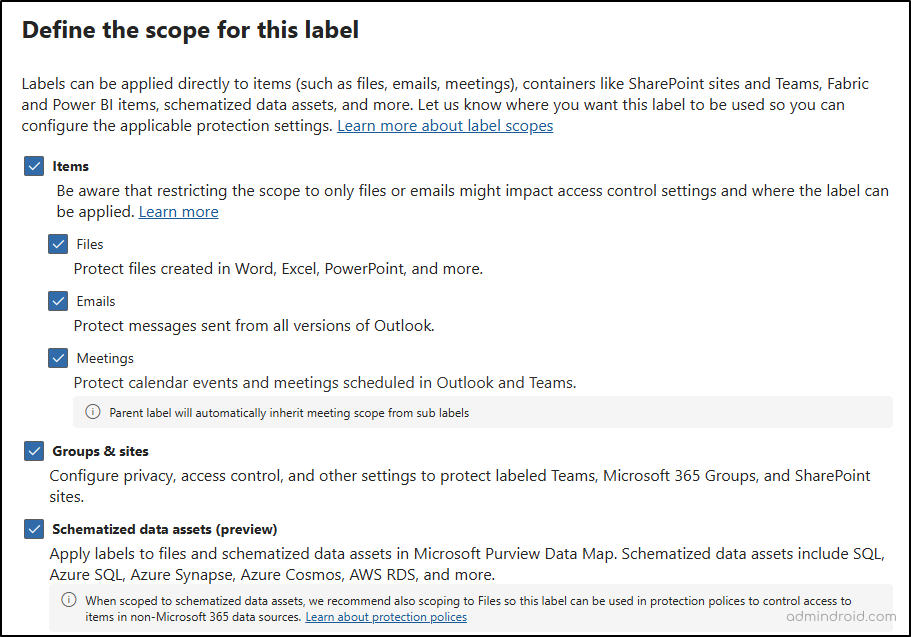
- Next, configure protection settings for labeled items, such as controlling access, applying content marking, and protecting Teams meetings and chats (note: Teams Premium license is required for this feature).
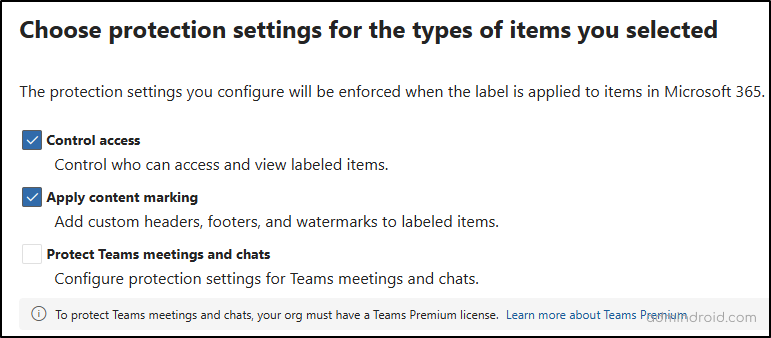
- If client-side auto-labeling is needed, you can enable the “Auto-labeling for files and emails” toggle in the next step, though you can skip this if setting up a policy instead.
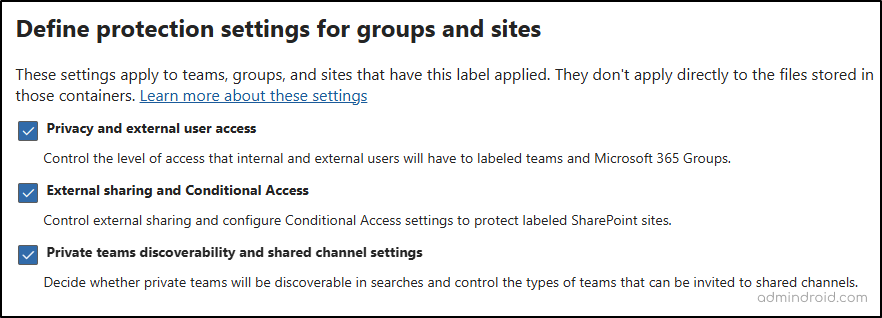
- Proceed to the next step to define protection settings for groups and sites, then save the label.
Publish Sensitivity Labels to Users and Groups:
Now that we have created the sensitivity label, the next step is to publish it to relevant users or groups so they can view and apply it as needed. Here’s how:
- Select the newly created sensitivity label from the list of labels and click “Publish labels.”
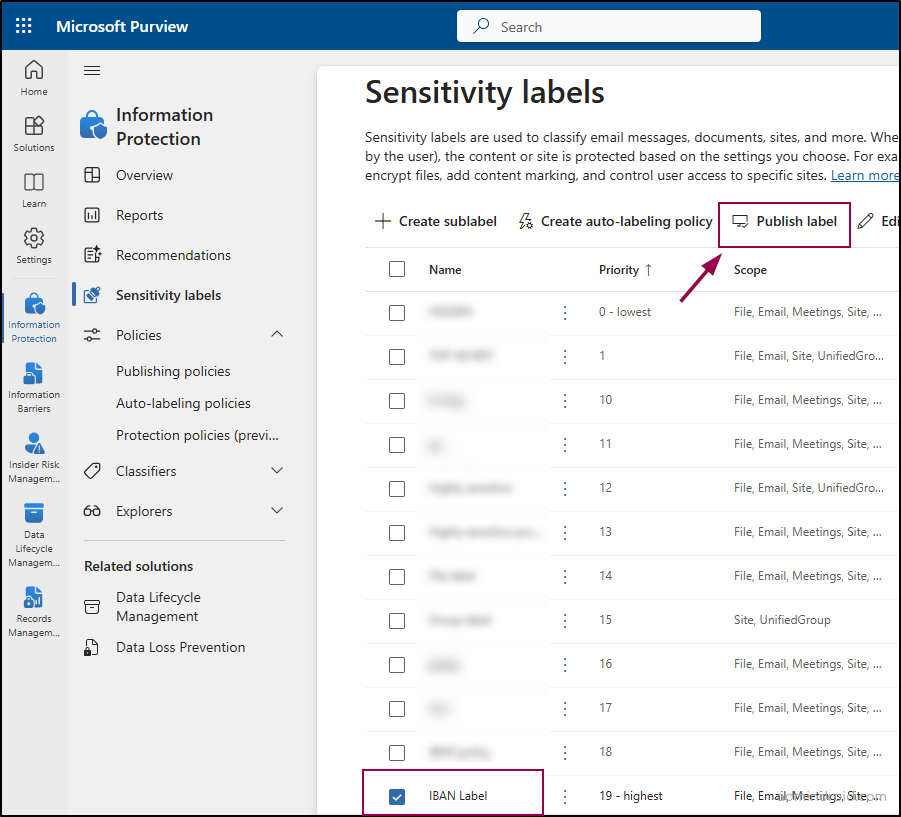
- In the “Publish to users and groups” section, choose the users or groups who can use the label.
- Under “Policy Settings,” specify whether users must justify removing or lowering the label classification.
- Name your policy and click “Submit” to complete the publishing process.
Once the label gets published successfully, the next step is to create an auto-labeling policy that automatically applies a sensitivity label to the content meeting specific conditions.
Creating an Auto-labeling Policy
- Go to Auto-labeling policies under Policies and click Create auto-labeling policy.
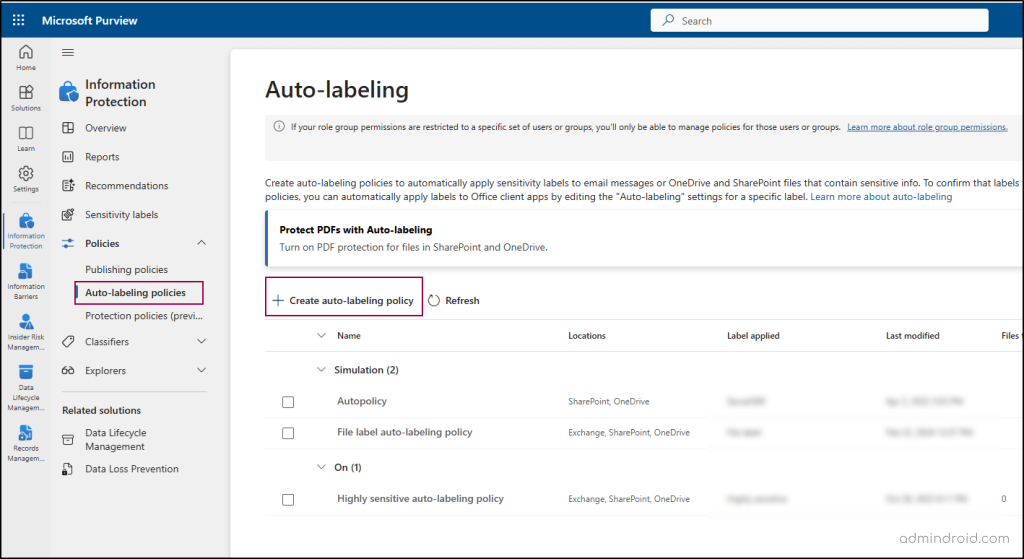
- Under Categories, select Custom -> Custom policy.
- Name your policy and assign administrative units, if necessary.
- Select the locations where the policy will apply, such as Exchange email, SharePoint sites, and OneDrive accounts.
- Choose between Common or Advanced rules, depending on the location; use Advanced to define specific rules for each location.
- Add a new rule and name it.
- In the Conditions tab, select Content contains -> Add -> Sensitive info types -> choose International Banking Account Number (IBAN) -> Add.
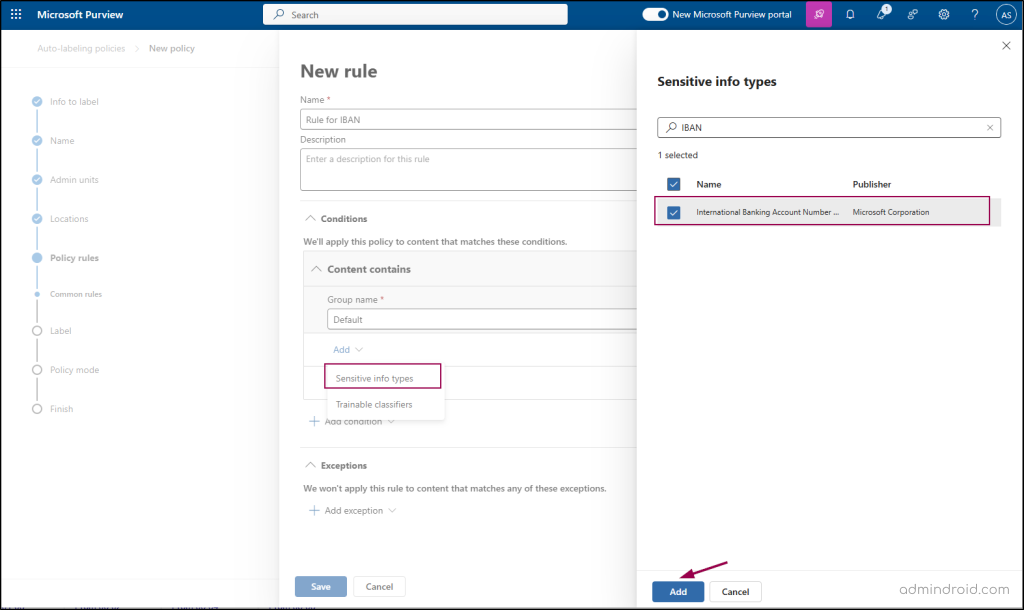
- Next, choose the label created earlier and add it.
- Configure any additional email settings if needed.
- On the ‘Decide if you want to test out the policy now or later’ page, choose the ‘Run policy in simulation mode’ -> Click create policy.
What You Need to Know About the Simulation Mode for Auto-labeling Policies:
- Simulation mode allows administrators to run the policies and ensure that the content is correctly labeled before the actual application of labels.
- Automatic labeling of documents and emails cannot occur until the policy has completed at least one simulation run.
- Ensure that Microsoft 365 auditing is turned on, as this is necessary for the simulation to function properly.
- Running the policy in simulation mode can take up to 12 hours to complete.
- After the simulation is complete and you’ve confirmed that the conditions are configured correctly, you can enable the server-side auto-labeling policy. This policy will automatically apply the sensitivity label to content that matches the specified conditions.
To check the configuration details and status (such as whether the policy simulation is still running), go to Policies -> Auto-labeling Policies and click on the policy under Simulation. Then, navigate to the Items to Review tab. Here, you can see which emails or documents matched the specified rules, confirming that the policy has been applied to the file containing the sensitive information we created earlier.
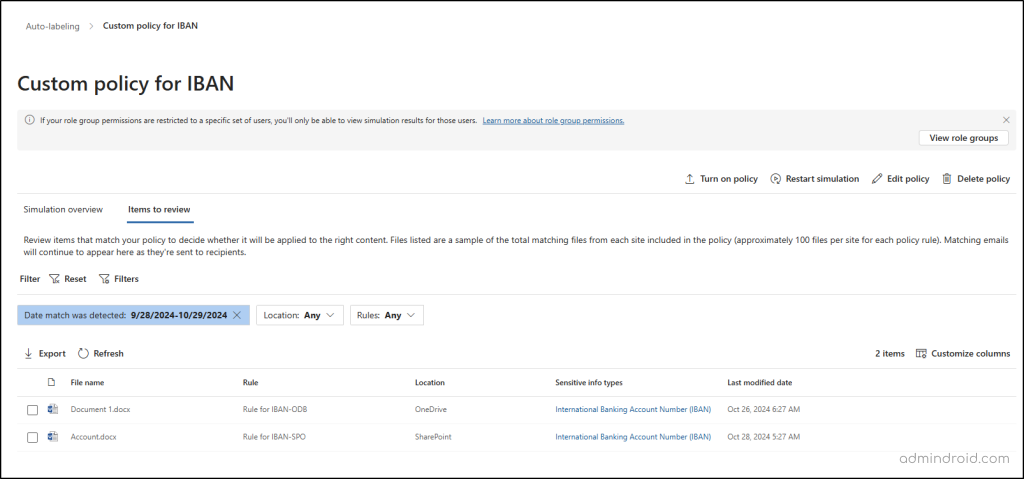
We can see that the file created with the sensitive information type (International Bank Account Number) is included in the reviewed items, confirming that the policy is functioning correctly.
When you’re ready to activate the policy without simulation, select the Turn on Policy option.
Please note that automatically applying labels to files and emails may still take some time to process.
Points to Remember
- When the content has been manually labeled, that label won’t be replaced by automatic labeling.
- Auto-labeling policies run continuously until they’re deleted.
- Automatic labeling will replace a lower priority sensitivity label that was automatically applied, but not a higher priority label.
- Supported file types for auto-labeling include PDF, Word (.docx), PowerPoint (.pptx), and Excel (.xlsx).
- Email attachments are not labeled.
- A maximum of 100,000 files can be labeled automatically per day, with up to 100 auto-labeling policies per tenant targeting various locations.
We hope this blog will help you with insights on how to automatically label content in Microsoft 365. Thank you for reading! If you have any further questions, feel free to reach out to us in the comments section.