On Day 30 of Cybersecurity awareness month, learn how to implement a passwordless Office 365 environment with a Temporary Access Pass in Azure AD on the first go. Stay tuned for more blogs in the Cybersecurity blog series.
IBM reports that one in five malicious attacks resulted from stolen or compromised credentials. Consequently, passwords are the prime target for cyber-attacks and phishing scams. So, for a more seamless experience with Office 365, Microsoft recommended passwordless authentication.
Passwordless authentication streamlines user interactions while enhancing security posture. Though passwordless authentication has been available for a year, some companies haven’t yet welcomed it. Well, now the time has arrived! With the start of passwordless authentication, Temporary Access Pass (TAP) has also rapidly come into existence.
True cybersecurity is preparing for what’s next, not what was last!
-Nell Rerup
These Temporary Access Passes are the next, and that helps to create a world without passwords!
A temporary access pass (TAP) helps onboard passwordless authentication methods and recover access to accounts when a device is lost or stolen without requiring the authentic password login method.
Now, further on this blog, let’s dive into what a temporary access pass is and how you can implement it in your organization.
What is a Temporary Access Pass in Microsoft Entra?
A temporary Access Pass is a multi-factor authentication mechanism. It is a time-limited passcode issued by an administrator to meet strong authentication requirements.
A Temporary Access Pass can be used in two different scenarios:
- TAP can be used to onboard other authentication methods like passwordless methods, FIDO2, or Windows Hello for Business.
- Additionally, TAP can be useful to users/admins who have lost their FIDO2 security key or their second-factor authentication app.
Now let’s look at how to enable temporary access passes and onboard passwordless authentication and other authentication methods.
Primary Usage of Temporary Access Pass:
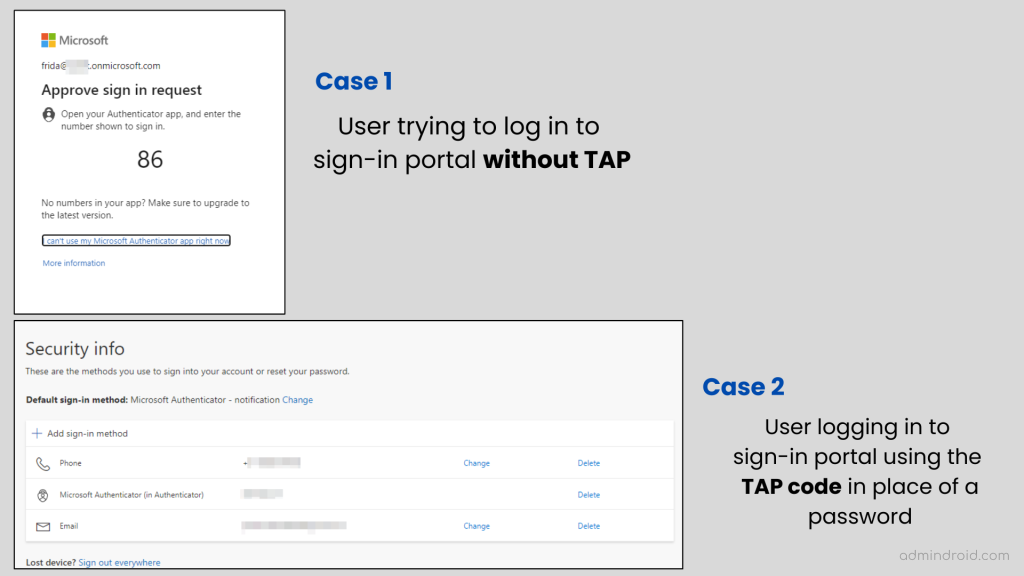
With Temporary Access Passes, you can skip the additional security requirements (second-factor authentication).
Case 1: Normally, a user must satisfy their second-factor authentication requirement when they update their authentication method in My Sign-ins.
However, sometimes you may need to avoid 2FA, or what happens if your 2FA device is lost? When a device is lost, it is no longer possible to provide multi-factor authentication. 😕
Therefore, here comes the Temporary Access Passes to rescue! 🛡️
Case 2: This case is an example of logging in using Temporary Access Passes.
With the TAP, users will no longer need to enter their password or perform other second-factor authentication steps. Users are directly permitted to log in and onboard other authentication methods like passwordless authentication, FIDO2 security key, etc.
Users who update their authentication method using a temporary passcode are automatically redirected to the “Sign-ins page” without having to perform second-factor authentication.
Configure Temporary Access Pass in Microsoft Entra:
You should enable the temporary access pass policy before creating a temporary access pass for the users in your tenant. So, to enable TAP for your users in your organization, follow the steps below.
- Open the Microsoft Entra admin center.
- Then, navigate to the following path to enable a temporary access pass for Entra users.
Microsoft Entra admin center → Protection → Authentication methods → Policies.
- Next, click on the Temporary Access Pass.
- In the beginning, it won’t be enabled by default. So, now toggle the Enable bar to Yes.
- After that, you can choose between All users and Select users based on your requirements.
- Default TAP settings are applied when the TAP policy is enabled. Hence, if you wish to update or modify the default Temporary Access Pass settings, click the Configure tab.
→ Here, it is possible to modify the Minimum lifetime, Maximum lifetime, Default lifetime, and Passcode length. Furthermore, you can specify whether the issued passcode is for one-time or recurring use.
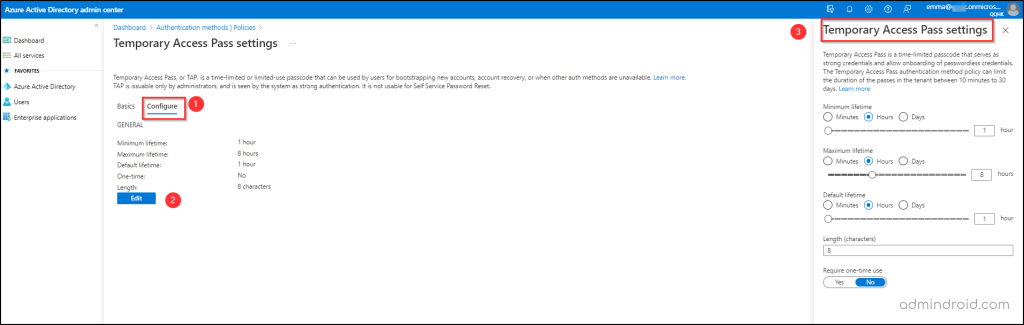
That’s it! Now, the Temporary Access Pass for your organization is enabled. Next, it’s time to issue the Temporary Access Pass to those who need it!
Create a Temporary Access Pass in Entra ID
Once you’ve configured the TAP settings, you can create TAP codes for the required users to perform the chores. Before creating a passcode, it is important to know who has access to create and manage Temporary Access Passes in Azure AD. There are several roles that can perform TAP-related actions.
| Global Admins | Create, delete, and view a Temporary Access Pass on any user (except themselves) |
| Privileged Authentication Admins | Create, delete and view a Temporary Access Pass on admins and members (except themselves) |
| Authentication Admins | Create, delete, and view a Temporary Access Pass on any user (except themselves) |
| Global Reader | View the Temporary Access Pass information on the user (without reading the code itself) |
Steps to Create a Passcode for Entra User:
As I mentioned earlier, the Temporary Access Pass helps you create a Microsoft 365 environment without passwords. For that reason, admins must allow users to register without passwords. However, normally, we don’t have anything like this before!
Here, the Temporary Access Pass saved the day for admins! By using TAP, users can register their second-factor authentication method without registering their passwords.
Note: Generally, when you create a new user, they must set a password and two-factor authentication. However, it is best to go passwordless at the start due to the emergence of MFA attacks. In this section, we’ll see how to onboard passwordless authentication for both existing and new users without requiring a password.
(Ensure to enable passwordless authentication for the required user before creating a passcode. If the user is not enabled, they cannot set a passwordless authentication method.)
- Sign in to the Microsoft Entra admin center as a global administrator, privileged authentication administrator, or authentication administrator.
- Next, click Users → All Users on the left pane.
- Then, choose the user to whom you want to generate the passcode (Here I’m using ‘emde‘).
- Under the manage section in the left pane, select Authentication Methods.
- Following this, add the authentication method (Temporary Access Pass) and toggle the One-time use bar if required.
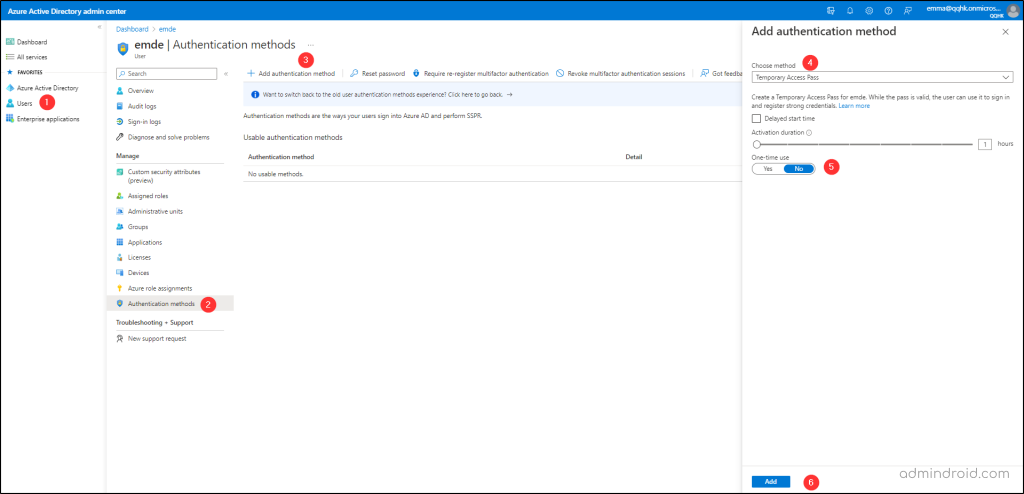
- Finally, when you click Add, it creates a Temporary Access Passcode. It is recommended to share the code with users as soon as it has been generated.
❗Once you select OK, this passcode value cannot be viewed again.
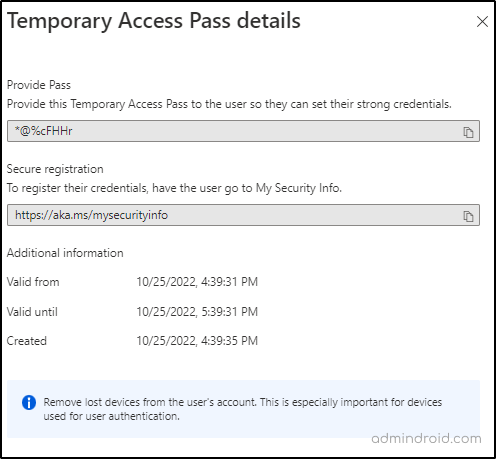
There you go! Now, the rest of the magic is up to the end user! With the temporary access pass, he can set up other authentication methods or delete the lost device authentication method and quickly add new devices.
How a New User Can Go Passwordless From First Sign-in?
Step 1: Now, after getting the TAP from an admin, the newly created Office 365 user (emde) can visit this URL ( https://aka.ms/mysecurityinfo) using the passcode in place of the password.
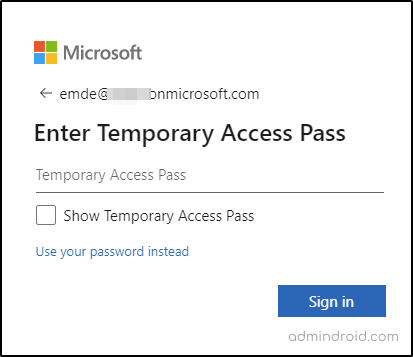
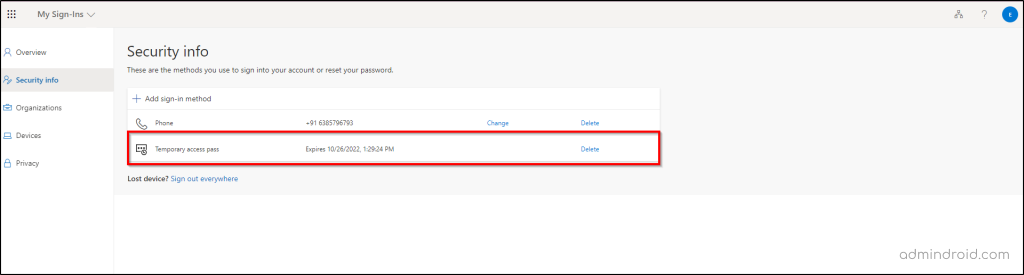
Step 2: On the Security info page, you will see the Temporary Access Pass sign-in information. Now, proceed to add the additional sign-in method (Microsoft authenticator).
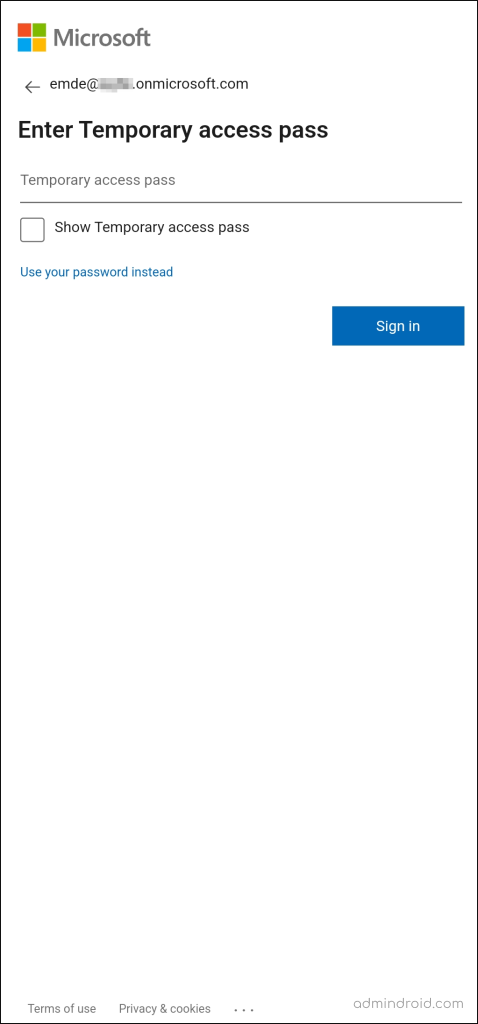
Step 3: Now that you’ve added the Microsoft authenticator device to your account. Use the TAP code issued by the administrator to enable passwordless authentication on mobile.
Step 4: There you have it! Now the newly created account is ready for the passwordless authentication method. If you haven’t implemented this method yet, now is a perfect time!
Troubleshoot Time:
Sometimes, users might notice the following error message, when they’re trying to sign in using TAP.
Temporary Access Pass sign-in was blocked due to User Credential Policy
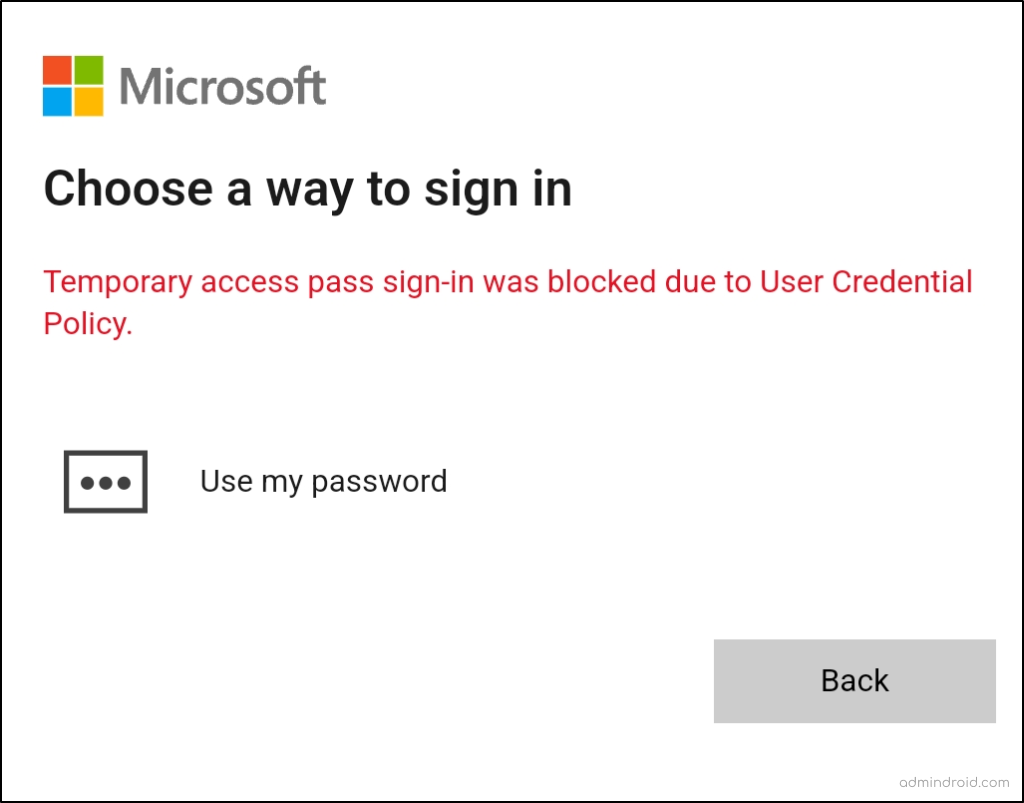
The above error will be popped up if any of the below cases happen.
- Temporary Access Passes have already been used one time.
- The user has a multi-use Temporary Access Pass, whereas the authentication method policy requires a one-time Temporary Access Pass.
- Be sure that the user falls within the scope of the TAP policy.
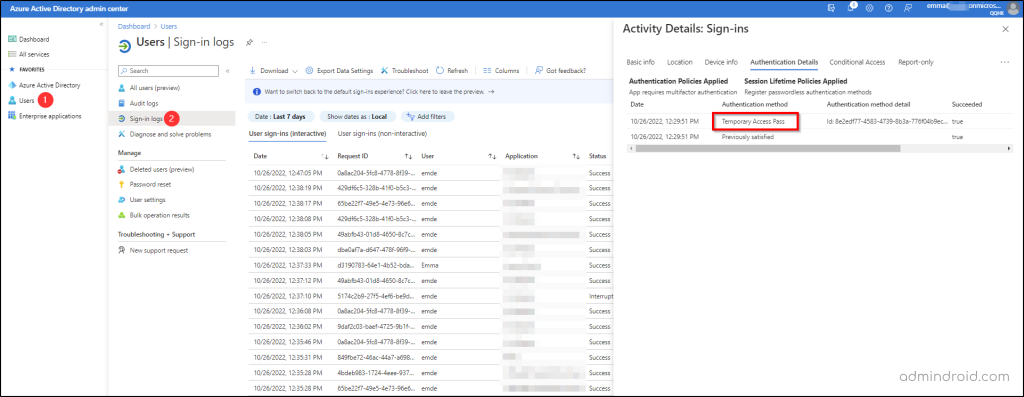
Get Reports of Temporary Access Pass Sign-ins:
While enabling, creating, and providing Temporary Access Passes is beneficial, it is also critical to constantly keep track of the passcode logins that occur within the organization. Navigate to the path below to gain insights on TAP sign-ins that occurred across your organization.
Microsoft Entra admin center → Users → Sign-in logs → Select a sign-in entry → Authentication Details
You can view the details of temporary access passes in the Authentication Details tab.
How Does Temporary Access Pass Work for Guest Users?
It is possible for guest users to access their respective resource tenants using a temporary passcode provided by their home tenants. However, if the resource tenant requires MFA, the guest user will be required to perform multi-factor authentication.
Concluding…
However, temporary access passes come with certain limitations. But, the pros of deploying the TAP in the organization outweigh the cons. Overall, TAP is considered the gateway path that leads us to a passwordless universe! Implement the one-time passcode now and create a robust, user-friendly environment that doesn’t compromise security.
Finally, now it’s time to wrap things up! Hopefully, we’ve provided you enough ideas on temporary access pass in Entra ID and ways to implement them in great detail.






