On Day 31 of Cybersecurity awareness month, learn how Microsoft helps in forensic investigation and where to find the forensic artifacts today. Stay tuned for more blogs in the Cybersecurity blog series.
As Cyberattacks are arising day-by-day, every organization needs to be secure enough to fight against them. Besides all the security measures, attackers can still enter an organization through any loopholes or the weakest link in the security chain. Before we realize that the attacks have happened, the attacker may access all the sensitive information, change security configurations, and can do whatever they need to do in our Office 365 environment. Here is where forensic investigation comes in.
It’s the not knowing that’s the worst… After a breach, there are more questions than answers.
– Dwayne Melancon
Indeed, investigators have more questions and want more details to move further. To that end, forensic investigators analyze the attack to identify details like how the attacker entered the organization, what data they stole, compromised Office 365 accounts, and much more. Subsequently, they help the organization get back to normal and recommend Office 365 security best practices for staying secure. Let’s dive deep into what details they look for when investigating the breach and where they could find the required data in Office 365.
How Microsoft helps in Forensic Investigation?
Microsoft provides a wealth of information about each activity that occur within an organization. Admins monitor these details to find out unusual user activities, sensitive info accesses, unwanted changes in configurations, privileged access assignments, etc. Furthermore, admins can use the alerting feature to stay updated about risky happenings. Similarly, forensic investigators surf various Microsoft portals and collect the appropriate details to identify the start of the attack, the affected areas, and more. Here are some of the Microsoft 365 features that lend a hand to forensic investigations.
- Office 365 Audit Log
- Microsoft Azure Active Directory Logs
- Microsoft Purview eDiscovery Tools
- Microsoft 365 Defender
Office 365 Audit Log
Office 365 audit log provides all the activities done by users, admins, etc., in the organization. As such, forensic investigators often use this audit trail in ordeer to pinpoint any suspicious activities that occur during the attack period. The attackers will primarily focus on gaining access to a privileged account like global admin. So, besides all the audit activities, investigators will focus on some of the admin activities to identify the attacker’s move.
Some of the activities verified by the investigators are,
- New admin role assignments – To verify any new highly privileged admin roles are assigned to users, applications, service principals, etc.
- Accessed mailbox items (MailItemsAccessed) – To find out if any sensitive emails have been accessed by the attackers.
- Purging messages from mailboxes (HardDelete) – To verify that any confidential messages were deleted permanently from the mailbox.
- Inbox rule creation (New-InboxRule) – To check if any forwarding or redirecting rules created for the admin mailboxes.
- SharePoint and OneDrive File Activities – Activities like file accesses, file delete, file move, file sync, file downloads, etc., will be monitored to identify if any sensitive files have been accessed and used by the attackers.
- Role group member changes (Update-RoleGroupMember) – To check if any new members were added to highly privileged role groups like Organization Management.
- eDiscovery role additions – To identify if any user has been newly assigned or removed from an eDiscovery role like ‘eDiscovery Manager’ or ‘eDiscovery Administrator’.
- eDiscovery compliance search or Content search creation – As eDiscovery search or content search helps to search for instant messages, emails, and documents, attackers may use these searches. So, investigators can find any of these searches were started by the attackers.
- eDiscovery compliance search or Content search exports – To verify any eDiscovery searches or content search results have been exported by the attackers.
- Consent to application – To check whether any sensitive permissions have been newly granted to an application to access the resources on behalf of a user.
- Application modification – To identify whether any new credentials have been added to an existing application or a service principal.
- Directory role changes – To verify the recent changes made in the directory role and role group memberships.
The above-mentioned activities are a few important activities that the investigators monitor in your organization post-breach. The list includes many activities that investigators use to deeply investigate and identify the attacker’s activities. Furthermore, the list helps to uncover the full extent of the breach.
Microsoft Azure Active Directory Logs
Azure Active Directory is one of the trump cards for forensic investigators to identify activities with more details in the organization. It provides details on directory activities, sign-in logs, domain changes, application changes, etc. Additionally, you can integrate Azure AD audit data into the log analytics workspace to query the details precisely and examine the data. Let’s see them in detail.
Azure AD Sign-ins Log
This sign-ins log helps to identify the interactive user sign-ins, non-interactive user sign-ins, service principal sign-ins, and managed identity sign-ins in the organization. So, investigators use the sign-in log to identify all the Azure AD sign-ins and risky user sign-ins with more details and find the compromised account’s sign-ins, etc. The following are a few examples of sign-in details which are particularly beneficial for the investigators.
- Sign-in Location & IP – User’s sign-in location details like country, state, etc., and IP addresses of the device used to sign in.
- Failed Sign-ins – The user’s failed sign-ins help to identify the reason for the sign-in failure.
- Conditional Access Status – It gives the status of the conditional access of the users’ sign-in. It aids to identify whether the CA check is not applied, successful, or failed.
- Authentication Details – It provides the authentication method used to sign in and the policies applied while signing in to the tenant. So, it helps to identify whether any stronger authentication policy is applied or not.
Risky Users & Risk Detections Logs
Risky users log provides the details of the risky users and their risk status. Risk detection shows all the risks detected in the organization and their risk status.
Microsoft Purview eDiscovery Tools
eDiscovery solutions in Microsoft Purview include content search and eDiscovery case investigation. Both eDiscovery solutions help investigators identify data instantly by searching content from various resource locations. Let’s take a closer look at how both work and examine the difference between them.
Microsoft 365 Content Search
Using the content search in Microsoft Purview, investigators can view instant messages, email attachments, documents, etc. Investigators can search for content in the following locations.
- Exchange mailboxes
- SharePoint sites
- OneDrive for Business
- Microsoft Teams
- Microsoft 365 Groups
- Yammer Teams
Investigators can view statistics of search results and export them if required.
Microsoft Compliance eDiscovery
Forensic investigators often rely on eDiscovery for case investigations to place hold on the data and can do compliance searches for various resource locations. Similarly, forensic investigators can use eDiscovery to properly handle a case in the organization.
- You can create a case investigation and properly handle them using the RBAC approach. Thus, only authorized users can access the case and perform the necessary actions.
- Moreover, placing the data on hold helps to identify the attackers’ further activities like message modification. You can retrieve the original content as well as the modified version.
- In addition, compliance search (User data search) helps to search content in various resource locations based on specific keywords, specific users’ content, or all locations in the organization.
- You can manage the custodians involved in the case. Custodians are the users who are suspected to be added to the case to monitor their further activities until the case is closed.
- You can communicate with custodians using legal hold notification to instruct them to preserve their content for the case investigation.
- You can collect reports, remediate processing errors, use the OCR feature, conversation threading, and more to investigate the case in detail.
What is the difference between content search and eDiscovery?
Content search and compliance search in eDiscovery share the same workflow but the only difference is that eDiscovery requires you to create a case and you can place the content on hold.
Microsoft 365 Defender
Microsoft 365 Defender portal provides various features to identify threats and secure your organization. Among them, Advanced Hunting and Activity Log under Cloud Apps will be useful for a forensic audit. Let’s see how it helps forensic investigators.
Advanced Hunting
Advanced Hunting helps to hunt threat incidents with more details in the organization. It reviews data sets from Microsoft Defender for Endpoint, Defender for cloud apps, Defender for Office 365, and Defender for Identity. Advanced hunting lets you to
- Query the database using Kusto Query Language (KQL).
- Hunt using guided mode or advanced mode based on your KQL query knowledge.
- Create custom detection rules that help you to query the activities using the MITRE technique.
- Save your queries for further usage in the investigation.
- Load sample queries and apply filters to ease your threat-hunting job
The above-mentioned points are a few of the hunting features. Investigators can utilize the portal completely to hunt threats effectively.
Activity Log
Activity log in Microsoft 365 Defender is used to store Office 365 audit log when configured explicitly. Also, the multiple alert templates help to detect and respond to various security activities in the tenant.
Note: Microsoft Defender for Cloud Apps has been moved to Microsoft 365 Defender portal. If it is not available in your tenant, you can access the activity log in the Microsoft Defender for cloud Apps portal.
Difficulties in Microsoft 365 Environment
- By default, the audit log will not be turned on in the organization and won’t retain data beyond 90 days.
- Few auditable actions in mailboxes are not enabled by default. We need to manually enable it for every user.
- You can preview only 1000 mailbox items on the preview page while searching content using content search and eDiscovery.
- You can export only 2TB of data from a single search and for a single day. The maximum size of PST file allowed is 10GB.
- You can retain only 30 days of data in Azure AD logs. With a free license, you can retain only up to 7 days. For retaining data beyond that you should go for Azure storage or Log analytics workspace.
- Using Activity log in Defender for Cloud Apps, you can retain data up to 180 days. But, when investigating data older than 30 days, some advanced filters are not available due to Microsoft’s data retention policy.
- The Advanced Hunting will query the data only for the last 30 days. Also, it requires KQL language to query the database.
Are you ready to boost up your budget?
- Though you can extend the audit log retention period with premium licensing, you can preserve only 365 days of data. For more extensions, you should go for E5 licensing. Else, you should look for third-party tools.
- For retaining Azure AD logs beyond the retention period, you should go for an Azure storage account, Log analytics workspace which requires Azure Subscription.
- For advanced features in eDiscovery like custodian management, OCR, conversation threading, and more, you should go for eDiscovery Premium licensing.
- Also, the audit log results in GUI and PowerShell are not appealing and you wouldn’t get well-structured audit data. So, most admins always rely on third-party tools to audit their data efficiently.
Aside from budget upswing, there are many difficulties if you rely on Microsoft 365 for forensic investigation. Restrictions on audit log retention and navigating multiple portals to find the right reports are real trouble. What if you had a solution that provides all the forensic reports at your fingertips? Yes, you heard it right! It’s none other than AdminDroid Microsoft 365 reporter.
How AdminDroid Helps You to Overcome Forensic Investigation Challenges?
- Infinite Audit Retention – Using AdminDroid, you can retain both audit log and Azure sign-in log as long as your organization requires them to.
- Reports in a single pane of glass – No more navigation! With AdminDroid, you can view all the forensic reports with detailed insights all to your hands.
- Best in class insights – Visualize every nook and corner of your organization’s activities with AdminDroid’s dashboards, a treat to the eyes.
- Advanced Alerting Capability – AdminDroid Microsoft 365 alerting tool provides an advanced alerting feature that notifies you of suspicious events to make your organization’s security stronger than ever.
- Reporting without PowerShell – With AdminDroid Microsoft 365 reporting tool, you can get in-depth details and insights about the organization, such as users, license usage, app usage, device details, etc., without relying on PowerShell.
AdminDroid Forensic Reporting – Intuitive yet Feature rich!
AdminDroid Microsoft 365 auditing tool covers most of the activities required by forensic reporting in Microsoft 365. It provides in-depth report details on the criteria below.
- Admin privilege assignments & changes
- Application consents
- Mailbox access rights
- Mailbox message purge
- SharePoint file activities
- OneDrive file activities
- eDiscovery case details
- Directory role group changes
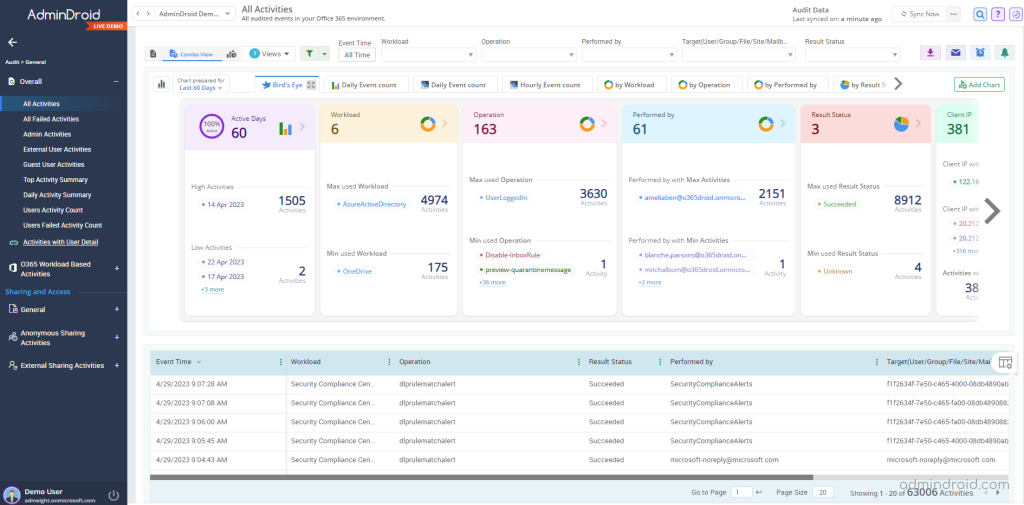
These are some of the key Office 365 audit log activities provided by AdminDroid. Apart from these, it provides more than 1800 activities across all Microsoft 365 services which solves all requirements of a forensic investigator.
AdminDroid free Azure AD auditing tool provides 115+ reports to monitor all Azure AD activities right from sign-ins, MFA, CA policies, etc., happening in your organization. Considering Azure Sign-in logs, it provides the following reports.
- User’s sign-ins with location & IP
- High risky sign-ins
- Medium risky sign-ins
- Low risky sign-ins
- Confirmed risky sign-ins
- Open risky sign-ins
- Failed sign-ins
- Conditional access policy sign-ins
- Sign-ins with MFA details
- Sign-ins with basic authentication
- Risky sign-in events
- Risk resolved methods
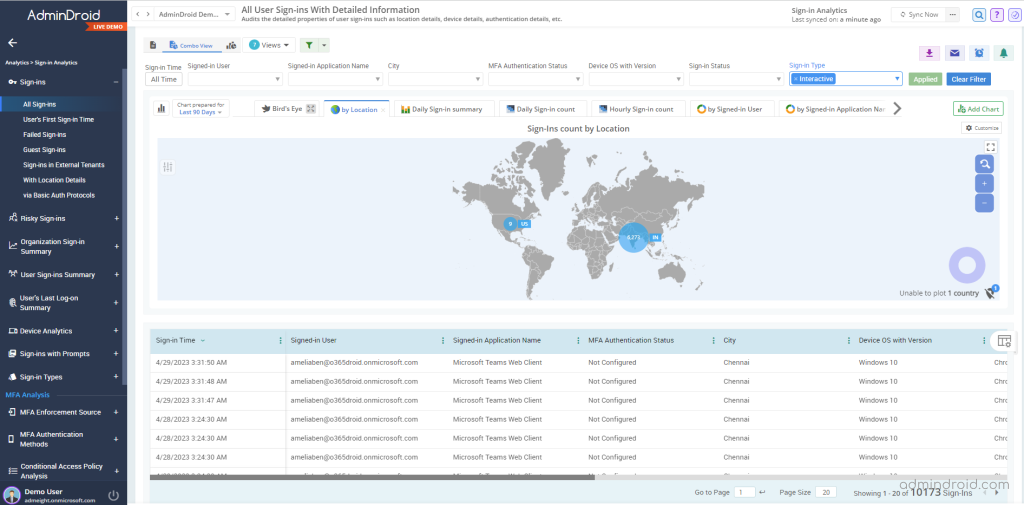
In addition, it provides details like the last logon time, first sign-in time, crucial sign-in attempts, and more to help you efficiently monitor Office 365 sign-in logs as never before.
By all odds, AdminDroid is truly a whip hand for forensic investigators to overcome all challenges and save time. Moreover, AdminDroid provides 1800+ reports to solve almost all your Microsoft 365 reporting and auditing requirements. AdminDroid’s assorted features, like alerting, delegation, scheduling, etc., are an absolute treat to admins. Start exploring AdminDroid Microsoft 365 reporter today and enhance your reporting experience!
I hope this blog helps you to understand the requirements when doing forensic investigations and how to overcome the challenges. Feel free to drop your thoughts in the comment section.






