On Day 7 of Cybersecurity Awareness Month, learn how to get enterprise apps and assigned API permissions in Microsoft 365. Stay tuned for more blogs in our ongoing Cybersecurity blog series.
Modern cyberattacks in Microsoft 365 no longer rely on guessing privileged account credentials. Instead, attackers trick you into granting access to privileged enterprise applications (also called service principals). A carefully crafted OAuth consent phishing attack can persuade you to grant permissions to a malicious app. Once approved, that app gains persistent access to your organization’s data, often bypassing traditional security controls.
Many organizations unknowingly have apps with unnecessary API permissions that are consented to tenant wide. This opens the door to abuse or even full-scale tenant compromise.
In this blog, we’ll explore the methods available to retrieve enterprise apps with assigned permissions in Microsoft 365. By doing so, you can ensure that only trusted apps retain access and that permissions remain aligned with the principle of least privilege.
Retrieve Entra ID Enterprise Applications with Their Permissions
To check assigned permissions for a service principal, you can use either the Microsoft Entra admin center or Microsoft Graph PowerShell.
- View enterprise app permissions in Entra admin center
- Export enterprise app permissions via PowerShell
1. View Permissions Granted to Enterprise Apps Using Entra Admin Center
You can view all the enterprise applications and their assigned permissions in Microsoft Entra admin center by following the steps below.
- Navigate to the Entra ID → Enterprise apps in the Microsoft Entra admin center.
- Select the app for which you want to check granted API permissions.
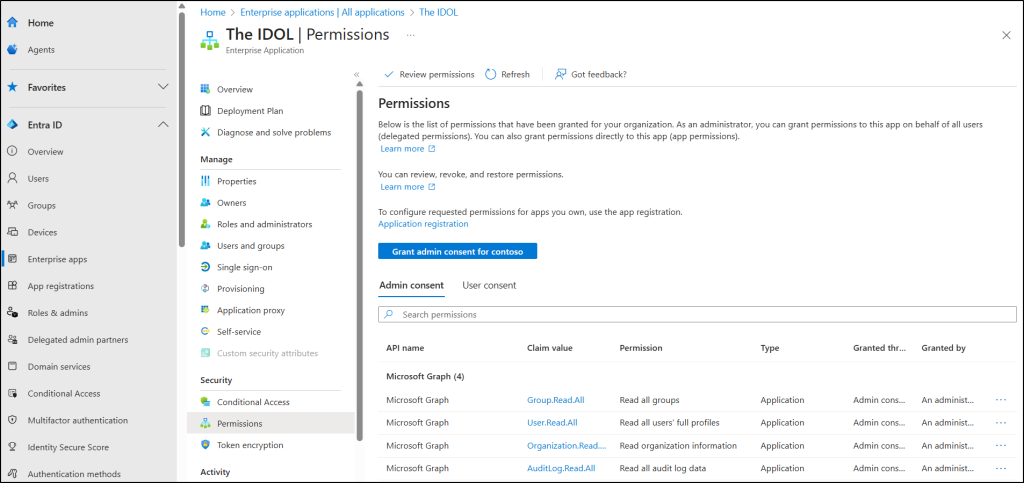
- Then, under the Security section on the left, click Permissions to view the assigned permissions in the Admin consent and User consent tabs.
- Here, you can explore all API permissions granted to the selected app, including the permission name, claim value, description, permission type such as delegated or application, consent type, and who granted them.
2. Export Enterprise Apps with Assigned Permissions Using PowerShell
While manually checking every enterprise app in the Entra admin center for assigned permissions can be time-consuming. An alternative is to use the Get-MgServicePrincipal cmdlet from Microsoft Graph PowerShell, which retrieves details for all Entra ID enterprise applications.
However, checking OAuth2 permission grants and app role assignments often require separate cmdlets for each permission type. To simplify this, we developed a PowerShell script that quickly exports all enterprise applications along with their user-consented, admin-consented delegated, and application permissions, including all key details.
Download Script: GetEnterpriseAppPermissions.ps1
Script Highlights
- The script installs MS Graph PowerShell SDK (if not installed already) upon your confirmation.
- Allows to filter applications with specific permissions (eg.,”User.Read.All”) assigned.
- Admin consented app permissions
- Admin consented delegated permissions
- User consented permissions
- Fetches the list of ownerless applications in Microsoft Entra.
- Find Entra app permissions granted thorough user consent and admin consent.
- Generates report for sign-in enabled and disabled applications.
- Assists in filtering based on following properties:
- Application Name
- Application Id
- Object Id
- API Name
- Filters apps that are restricted to specific users and accessible to all users.
- Lists applications that are hidden and visible to all users in the organization.
- Assists in filtering home tenant and external tenant applications.
- Exports the result to CSV.
- The script can be executed with an MFA enabled account too.
- It can be executed with certificate-based authentication (CBA) too.
- The script is schedular-friendly.
Enterprise Application Permissions Report – Sample Output
The exported ‘enterprise applications and their permissions’ report look like the screenshot below.
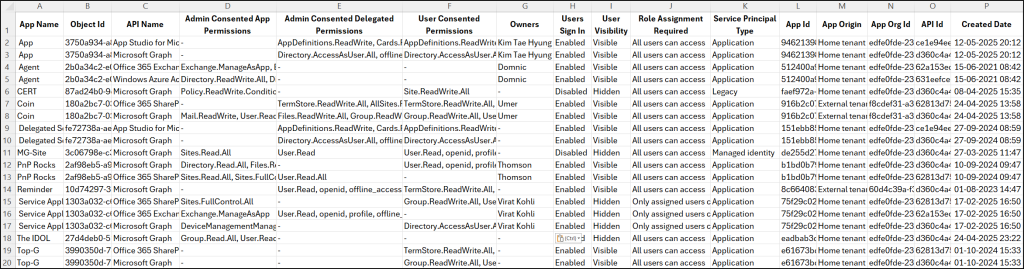
The script exports enterprise apps and permissions granted for them along with the following attributes: App Name, API Name, API Id, Admin Consented App Permissions, Admin Consented Delegated Permissions, User Consented Permissions, App Id, Owners, Users Sign-in Capability, App Origin, App Org Id, User Visibility, Role Assignment Required, Service Principal Type, Object Id, Created Date.
Export Enterprise Apps and Their Permissions Report Using PowerShell Script
To get started, download the script and launch Windows PowerShell. You can run this script two different ways.
Using interactive authentication
The method allows you to run the script directly with either an MFA or non-MFA Microsoft 365 account.
|
1 |
./GetEnterpriseAppPermissions.ps1 |
This generates a comprehensive report of all enterprise applications and their permissions in your tenant.
Using non-interactive authentication
You can also run the script using certificate-based authentication. For this approach, you’ll first need to register an app in Entra ID with Application.Read.All in app permission type. Then, obtain a certificate, either from a certificate authority or by creating a self-signed certificate.
|
1 |
./GetEnterpriseAppPermissions.ps1 -TenantId <TenantId> -ClientId <ClientId> -CertificateThumbprint <CertificateThumbprint> |
Get Enterprise Applications with Their Permissions – More Use Cases
The script provides granular enterprise app permissions report with flexible filtering options, allowing you to analyze various scenarios effectively, such as:
- Filter enterprise applications by consent type
- Find enterprise apps with specific permissions
- Discover enterprise applications with no owners
- Include enterprise apps with no permissions
- Get assigned permissions for a specific app
- Identify enterprise apps using specific API
- Export enterprise apps that are visible and hidden to all users
- Track down enterprise apps limited to specific users
- View enterprise applications accessible to all users
- Retrieve all home and external tenant enterprise app permission details
- Detect enterprise apps with high-privileged permissions
- Generate more granular enterprise app permissions reports
1. Track Enterprise Applications by Consent Type
The consent type filter helps you quickly distinguish between app permissions approved by admins and those approved by users. This allows you to focus on apps with potentially broader impact and understand how permissions are being distributed across your organization.
To filter apps with user consented permissions, use the –ConsentType with UserConsent option.
|
1 |
./GetEnterpriseAppPermissions.ps1 -ConsentType UserConsent |
To get apps with admin consented permissions, use the AdminConsent option.
|
1 |
./GetEnterpriseAppPermissions.ps1 -ConsentType AdminConsent |
The above format exports a report listing all service principals that hold admin-consented delegated or application permissions.
2. Review Enterprise Applications with Specific Consented Permissions
If you want to check for the applications that hold specific permissions, you can use the following filters to extract them quickly for review.
a. Admin-Consented Application Permissions
When enterprise applications are granted application permissions via admin consent, they often gain high-privilege, non-interactive access to resources. The -AdminConsentApplicationPermissions parameter helps you spotlight apps holding such permissions, so you can verify whether they truly require them.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AdminConsentApplicationPermissions "Directory.Read.All", "Sites.FullControl.All" |
Running this action helps to find the service principals’ admin consented with Directory.Read.All, Sites.FullControl.All application permissions.
b. Admin-Consented Delegated Permissions
To narrow down enterprise applications that have been assigned and admin consented with specific delegated permissions, you can use the -AdminConsentDelegatedPermissions parameter.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AdminConsentDelegatedPermissions "AppDefinitions.ReadWrite", "Cards.ReadWrite" |
c. User-Consented Permissions
Similarly, you can use the -UserConsents parameter to identify apps where end users have approved permissions such as Mail.Read or Contacts.Read.
|
1 |
./GetEnterpriseAppPermissions.ps1 -UserConsents "Mail.Read", "Contacts.Read" |
By tracking these apps, you gain visibility into unnecessary consents and plan user consent management effectively to avoid misuse.
3. Discover Ownerless Enterprise Applications in Microsoft 365
Ownership of enterprise applications is defined depending on how the application is registered in Entra. When a non-admin user registers an application, ownership is automatically assigned. However, apps created through other registrations often lack an owner, leaving governance gaps and increasing the risk of unmanaged permission assignments.
To detect such applications, run the script with the -OwnerlessApps parameter.
|
1 |
./GetEnterpriseAppPermissions.ps1 -OwnerlessApps |
This format helps you quickly identify enterprise apps without owners. By delegating ownership, organizations can strengthen accountability and improve the security of applications.
4. View Enterprise Applications with No API Permissions
Some enterprise applications may exist in your tenant without any assigned API permissions. While these apps don’t pose an immediate security risk, they can clutter your environment and make it harder to manage active, permissioned applications.
To identify and review such apps, you can use the -IncludeAppsWithNoPermissions param like below.
|
1 |
./GetEnterpriseAppPermissions.ps1 -IncludeAppsWithNoPermissions |
This helps you streamline application management and reduces noise, making it easier to focus on apps that have permissions and require oversight.
5. Generate Report of Specific Enterprise Application’s Permissions
By default, the script scans all enterprise apps and generates a comprehensive report of permissions. However, if you’re looking to narrow down your analysis to a specific app, you can use any one of the following identity parameters to filter.
- ApplicationId
- ApplicationName
- ObjectId
For example, if you know the ID of your enterprise application, you can use the format below to get permission details about that application.
|
1 |
./GetEnterpriseAppPermissions.ps1 -ApplicationId <AppId> |
6. Identify Enterprise Apps Using Specific API Name
You can also filter enterprise applications based on the specific API using -APIName param. This is especially useful when you need to identify apps that rely on APIs scheduled for deprecation or already deprecated.
|
1 |
./GetEnterpriseAppPermissions.ps1 -APIName "Windows Azure Active Directory" |
For instance, the above format will help you retrieve apps that use deprecated Azure AD Graph API. By listing those apps, you can take steps to migrate to Microsoft Graph API and avoid security gaps or service disruptions.
7. Export Visible and Hidden Enterprise Applications and Their Permissions
By using the -AppVisibility parameter like below, you can identify enterprise applications that are displayed to everyone in the My Apps portal and Microsoft 365 launcher.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AppVisibility VisibleApps |
Similarly, to trace hidden enterprise applications, you can adjust this app visibility filter like below.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AppVisibility HiddenApps |
This format will generate a report with a detailed list of service principals that are hidden from all users.
8. Track Enterprise Applications Restricted to Specific Users
When user assignments are enforced, enterprise applications are limited only to the specified users. To list applications restricted in this way, use the -RoleAssignmentRequiredApps parameter.
|
1 |
./GetEnterpriseAppPermissions.ps1 -RoleAssignmentRequiredApps |
With this report, you can review apps with permissions and consents assigned to specific users, verify whether the assignments are necessary.
9. Detect Overexposed Enterprise Applications in Microsoft Entra
Enterprise applications are automatically accessible to all users by default in a Microsoft 365 tenant. In addition, other services may retrieve access tokens for these apps. While this configuration simplifies access, it also increases the risk of misuse and data exposure.
To detect applications that are visible to all users, run the script with the -AccessScopeToAllUsers parameter.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AccessScopeToAllUsers |
This format helps you uncover privileged apps that may be unintentionally available to everyone, enabling better control over app permission management.
10. List Enterprise Applications by Origin in Microsoft Entra
Enterprise applications can either originate from your home tenant or be registered and managed by external tenants. Monitoring both types is essential for maintaining control over access.
You can use the -AppOrigin parameter to filter applications based on their source.
To list permissions of enterprise applications that are configured and managed by your own Microsoft 365 tenant use the format below.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AppOrigin HomeTenant |
To identify enterprise applications owned by external tenants execute the given below format.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AppOrigin ExternalTenant |
This report provides detailed insights into third-party apps and their permissions, helping you regularly monitor external integrations and revoke access to unnecessary or outdated apps.
11. Find Enterprise Apps with High-Privileged Permissions
To find apps that contain high privilege permissions, you can use the -AdminConsentApplicationPermissions, -AdminConsentDelegatedPermissions, and -UserConsents filters in combined manner.
This helps you find malicious applications that escalate to highly privileged roles in your tenant, or misconfigurations on any publicly accessible application.
|
1 |
./GetEnterpriseAppPermissions.ps1 -AdminConsentApplicationPermissions "Directory.ReadWrite.All" -AdminConsentDelegatedPermissions "Directory.ReadWrite.All" -UserConsents "Directory.ReadWrite.All" |
Here, this format will list all applications that have ‘Directory.ReadWrite.All’ with any consent types.
12. Generate More Granular Enterprise App Permissions Reports
Apart from the above-mentioned use cases, you can combine filter parameters to curate reports to your exact needs. Here’s a few more precise reports on your enterprise app permissions.
- To generate a report of ownerless applications that have admin-consented application permissions like Directory.Read.All.
1./GetEnterpriseAppPermissions.ps1 -OwnerlessApps -AdminConsentApplicationPermissions "Directory.Read.All" - To view apps that are external and admin consented, use the -AppOrigin and -ConsentType parameters together.
1./GetEnterpriseAppPermissions.ps1 -AppOrigin ExternalTenant -ConsentType AdminConsent - To ensure sensitive data isn’t exposed, audit sign-in enabled apps that are accessible to all users and have high-privileged delegated permissions with tenant-wide access using the following format.
1./GetEnterpriseAppPermissions.ps1 -UsersSignIn Enabled -AccessScopeToAllUsers –AdminConsentDelegatedPermissions "Directory.Read.All", "Files.Read.All"
We hope this blog helps you gain full visibility into your enterprise applications and their assigned permissions. We’re only on Day 7 of our Cybersecurity Awareness Month series, with many more tips to come. Stay tuned for practical guidance, actionable strategies, and insights to help you strengthen security against evolving threats, every single day. Feel free to share your questions or experiences in the comments.






