Securing your Microsoft 365 environment is essential, but manually reviewing all the settings & resources is a daunting and time-consuming task😣! It would be great if we have a virtual assistant to help keep track of all the tenant’s settings & resources, right? Fortunately, Azure AD recommendations are here to make the process effortless.
The MS Entra ID (Azure AD) recommendations are designed to monitor the status of your Microsoft 365 environment and provide security best practices to guarantee a remarkably secure and robust tenant 💯. These MS Entra recommendations feature is globally available now.
How Does Azure AD Recommendations Works?
Before delving into its functionality, let’s locate this feature:
Microsoft Entra admin center → Overview → Recommendations.
Basically, the MS Entra ID (Azure AD recommendations) feature automatically evaluates your tenant’s configuration against a predefined set of best practices and suggests security configurations your tenant should follow to keep the security score high and stay secure.
As of now, there are a total of nine Azure AD recommendations in place.
- Convert per-user MFA to Conditional Access MFA
- Migrate applications from AD FA to Azure AD
- Migrate from ADAL to MSAL
- Migrate to Microsoft Authenticator
- Minimize MFA prompts from known devices
- Remove unused application
- Remove unused credentials from applications
- Renew expiring application credentials
- Renew expiring service principal credentials
Points to Remember:
- Among those 9 recommendations, few are out in general availability, and few are in public preview.
- These recommendations come up with a priority level that indicates their level of importance and urgency for implementation within your tenant.
- You can also see the recommendation status, last updated time, what resources are impacted, and other information related to the recommendations.
Let’s learn about “Convert per-user MFA to Conditional Access MFA” now.
Switch Per-user MFA to Conditional Access Policies MFA
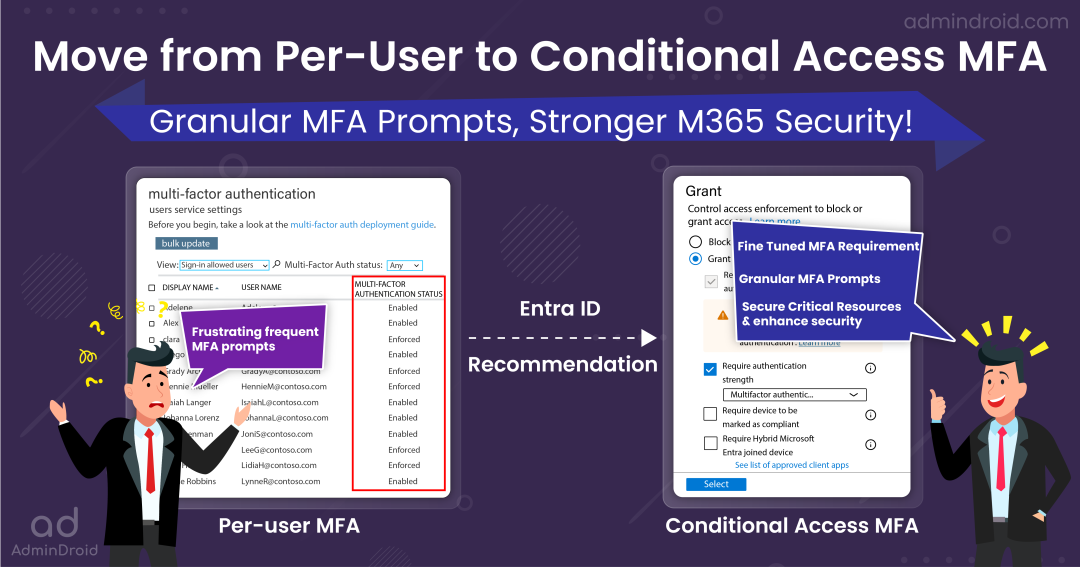
Configuring and managing MFA is a crucial thing, as it is a digital shield against security vulnerabilities in your M365 environment. However, enabling per-user MFA will prompt users for MFA during each sign-in.
- This can be frustrating for legitimate users disturbing their workflow by giving frequent MFA prompts, especially during critical tasks!
To strike a balance between security and user convenience, Microsoft recommends transitioning from per-user Multi-Factor Authentication (MFA) to Conditional Access (CA) policy-based MFA. This recommendation typically applies to organizations currently using per-user MFA. Let’s explore the advantages of making this switch.
- You can provide a fine-tuned MFA requirement to your users by configuring named locations, device-based conditions in CA policies, etc.
- You can enhance user convenience by providing granular MFA prompts with CA policy. For instance, you can enable users to bypass MFA when they attempt sign-ins from within the organization’s network or on compliant devices. This streamlines their login experience without compromising security, where it truly matters!
- Instead of requiring basic multi-factor authentication for all app access controls, you can adopt a more granular approach by specifying different types of MFA for different apps. This can be done using authentication strength within Conditional Access policies.
For example, you can require robust MFA methods like Microsoft Authenticator and FIDO2 keys for critical resources while applying less secure MFA methods like SMS and voice call MFA for less sensitive resources. Additionally, you can now use Microsoft Entra external authentication methods to meet the MFA requirements for Conditional Access MFA.
When Azure AD Requires Admins to Switch from Per-user MFA to Conditional Access MFA?
The “switch per-user MFA to CA policy MFA” recommendation in your tenant is tied to specific MFA configurations within your environment. Here are the conditions that trigger this recommendation.
- At least 5% of your tenant users are configured with per-user MFA.
- Only more than 1% of the users are configured for MFA in CA policies.
On clicking the recommendation in Entra ID, it’ll display a detailed insight about why the recommendation has been raised and what’s the status of the recommendation. And, with this information, admins can plan to take wise decisions towards safeguarding your Microsoft 365 environment.
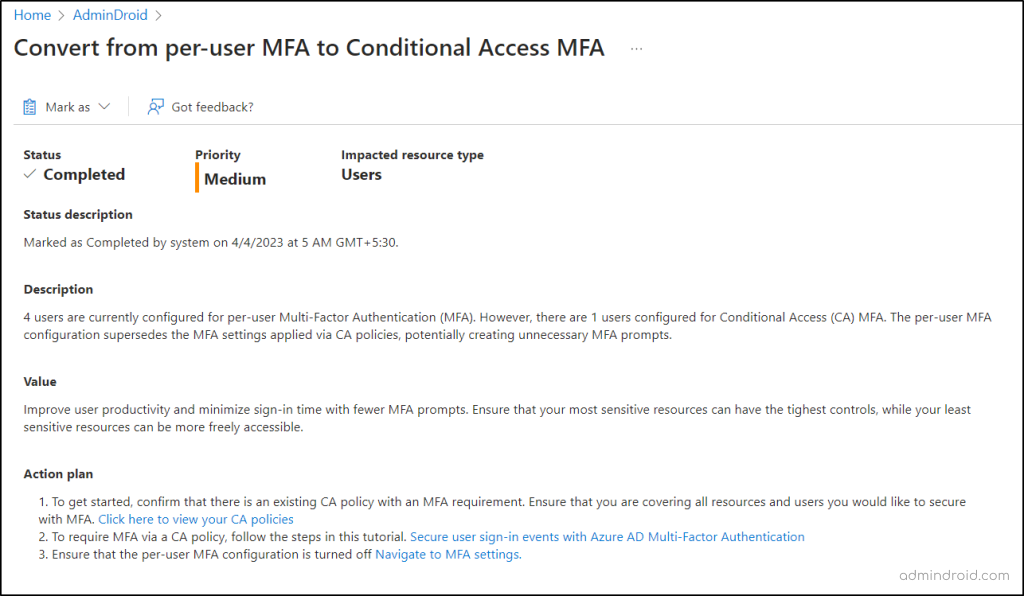
Fix the Recommendation: Move from Per-user MFA to Conditional Access MFA
Once this recommendation flag appears in your tenant, the next crucial step is to act and resolve the suggestion!
To do so, Microsoft simplifies this for you by providing proactive steps and offers you the relevant documentation & direct links to help you enable multi-factor authentication using Conditional Access. Let’s explore the action plans provided by the ‘switch per-user MFA to CA policy MFA’ recommendation.”
- Review existing Conditional Access policy with MFA requirement
- Create a Conditional Access policy to require MFA for users
- Check the per-user MFA status in Microsoft 365
1. Review Existing Conditional Access Policy with MFA Requirement
First and foremost, it’s essential to verify if there is any existing Conditional Access policy that requires MFA. If such policies exist, double-check that the specified users and resources are correctly configured for multi-factor authentication. If there is any misconfiguration, you can review and reconfigure them to work as you expected!
Overall, the purpose of this step is to review the Conditional Access policies and update rightly. So, make sure to start with this step instead of directly creating a Conditional Access policy!
2. Create an MFA Conditional Access Policy in Microsoft Entra ID
Tip: You can also make use of the predefined Conditional Access policy templates to quickly create a policy.
While reviewing the policies using the overview dashboard, if you don’t find any existing policy that requires MFA for all users, it’s time to take the next step: creating a new MFA Conditional Access policy.
Note: Admins need to disable security defaults in the Microsoft Entra admin center before configuring the Conditional Access policy. Make sure to have an MS Entra ID P1 or P2 license to create an Conditional Access policy.
- Navigate to Microsoft Entra admin center → Protection → Conditional Access.
- + Create new policy → Name → Give a suitable name.
- Assignments → Users → All users.
- Target Resources → Select All cloud apps or select specific apps that you want to require MFA.
- Conditions → Configure the location, device, client apps conditions based on your requirement.
- Access controls →Grant → Grant access → select Require authentication strength option→ Select.
- Finally enable the policy to ‘On’ mode and continue to save the policy.
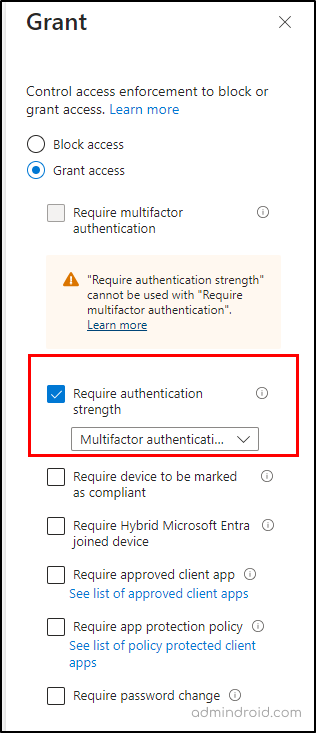
3. Turn Off the Per-user MFA in Microsoft 365
To effectively enforce MFA on Microsoft 365 using Conditional Access, it’s essential to make sure that per-user MFA configuration is turned off for users. You can check per-user MFA status using PowerShell or Azure portal.
To check whether the per-user MFA in Azure portal is turned off, follow these navigation steps:
Microsoft Entra admin Center → Identity→ Users → All Users → Per-user MFA
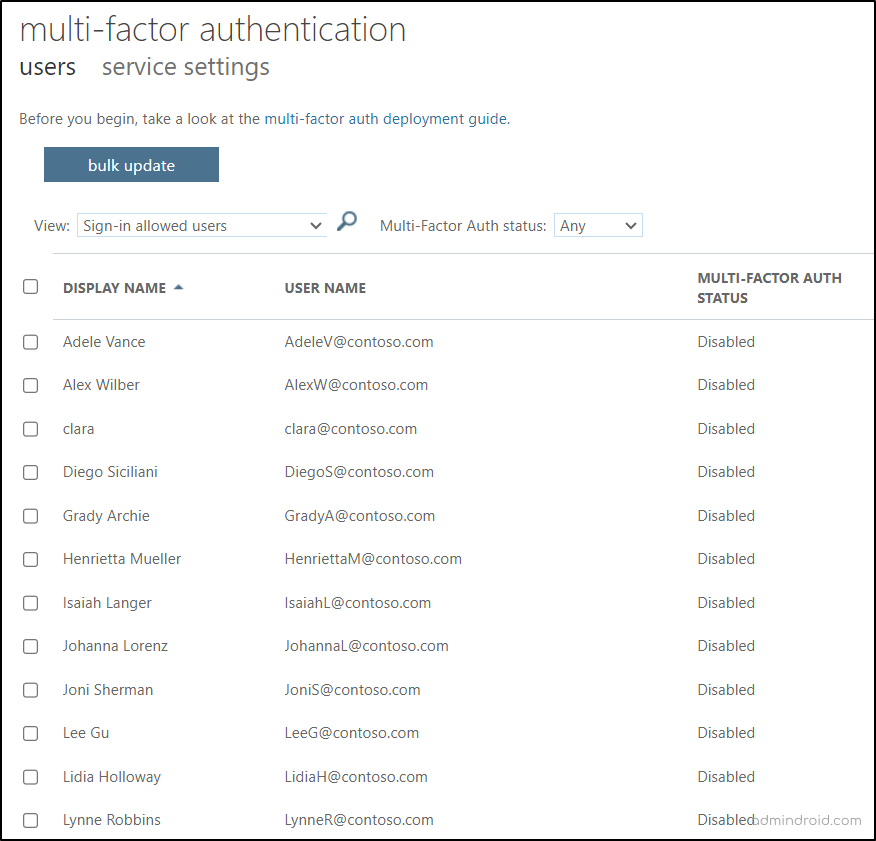
- By checking this section, you can review the legacy per-user MFA status for all users and confirm that it is set to “Disabled” for users. If it is found enabled, turn it off for all the users.
Once done with migrating all users from per-user MFA to Conditional Access MFA, the recommendation status will automatically update during the next service run. Remember to periodically monitor Conditional Access policies changes as unauthorized or unintended changes may open security vulnerabilities that malicious attackers can take advantage of. Additionally, explore how external authentication methods in Microsoft Entra ID can be used to satisfy MFA requirement for Conditional Access MFA.
Effectively Monitor MFA Status with AdminDroid
When transitioning from per-user MFA to Conditional Access MFA, it’s crucial to stay vigilant about its enforcement. However, it can be a bit of a juggling act as you need to know about the CA and per-user MFA statuses. But fear not! AdminDroid has come to the rescue to make this process smoother and save you from the tab-switching hassle!
AdminDroid provides you with a seamless way to get a clear picture of per-user MFA status through the convenient “User’s MFA Details” report. With just a few clicks, you can effortlessly access this information, saving you the hassle of navigating through the user interface! 😌
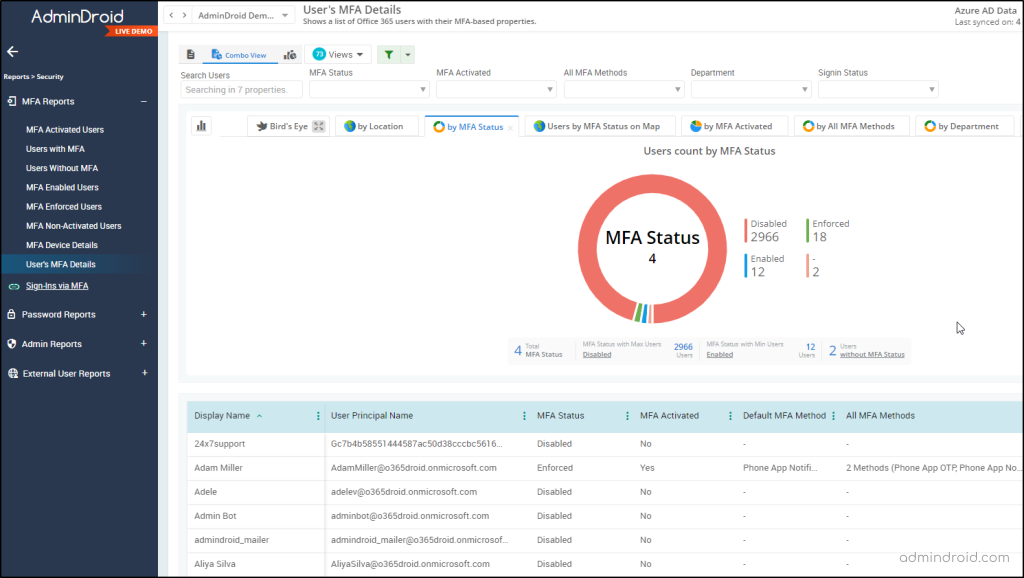
Plus, AdminDroid goes the extra mile in delivering a holistic MFA (Multi-Factor Authentication) analysis for you! Admins can track the MFA adoption rate, ensure all users are using MFA, identify users who need MFA enabled, troubleshoot MFA issues, and resolve more problems with the comprehensive suite of MFA reports below.
- MFA activated users
- Users with MFA
- Users without MFA
- MFA enabled users
- MFA enforced users
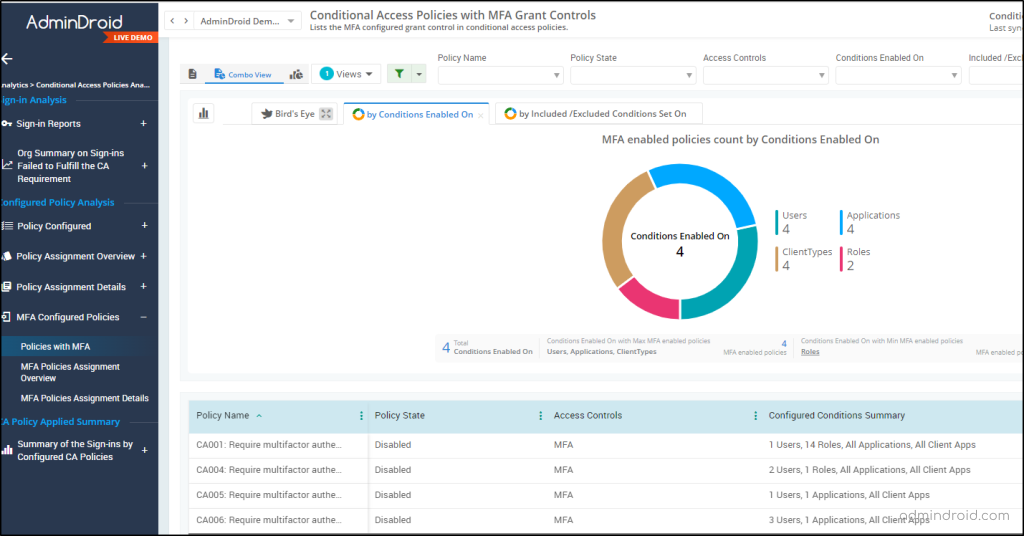
AdminDroid sets a new standard in Conditional Access policy analytics, going beyond the basics! It doesn’t just point out CA policies with MFA configurations; it helps you to dig deeper, and you can closely monitor successful sign-ins that passed or bypass the configured MFA policies.
Conditional Access Policies with MFA Requirement
- MFA configured CA policies
- Conditions configured of MFA policies
Conditions Configured in Conditional Access Policies
- Role-based CA policies
- Platform/location specified policies
- Location/device-based policies
AdminDroid goes beyond just delivering insightful reports; it offers a user-friendly MFA dashboard for a quick and comprehensive view of your organization’s MFA status. With just a glance, you can access crucial information about your configured MFA methods, default MFA methods, disabled MFA users, and more.
AdminDroid takes your Microsoft 365 monitoring to the next level. It doesn’t just stop at the basics; it lets you effortlessly oversee all your M365 resources. Whether it’s Exchange Online, OneDrive, SharePoint Online, Teams, or any other service, we’ve got you covered! 😌
So, download AdminDroid for seamless Microsoft 365 management.
Closing Lines
So, make the best choice for your M365 security! I hope this blog brings you more information about the “switch per-user MFA to CA policy MFA” recommendation. Furthermore, if you have doubts, feel free to reach out to us. We are here to resolve them!