Testing Conditional Access policies is critical to ensure that the right people have access when they need it, without over-restricting or leaving resources unprotected. To evaluate how these policies work in uncommon scenarios, the What If tool in Microsoft Entra ID has long been a go-to solution. Now, Microsoft has taken this a step further by introducing a new Graph-based “What If” Conditional Access tool, powered by the What If evaluation API.
While the legacy version is still available in the Entra portal, the Graph-based What If tool adds enhanced condition evaluation and full API integration support. In this blog, we’ll break down how this new tool differs from the traditional one, and why it’s a game-changer for testing and fine-tuning Conditional Access policies.
A Closer Look at the Graph-Based ‘What If’ Tool for Conditional Access
The Graph-based What If tool is a new preview feature in Microsoft Entra that enables admins to test Conditional Access policy evaluations via Microsoft Graph API. This allows faster automation, deeper integration into custom workflows, and a future-proof way to test access scenarios using real policy logic.
Key Features:
- Migration to Graph API Endpoint: Switched from the legacy ‘main.iam.ad.ext.azure.com’ endpoint to the officially supported Microsoft Graph ‘conditionalAccess/evaluate’ endpoint, which is documented and publicly accessible.
- Unified Experience via Entra and Graph API: The new Graph-based “What If” experience can be used through the Conditional Access UX in Entra portal and the Microsoft Graph API.
- Accurate Policy Evaluation Logic: The What If evaluation API uses the same authentication logic as actual sign-ins, providing a more accurate assessment of Conditional Access policy conditions.
- Input-Dependent Accuracy: The What If API needs all relevant sign-in details to give accurate results. If your Conditional Access policies include specific conditions, and those conditions aren’t provided, the API won’t be able to evaluate them.
For example, let’s say there’s a Conditional Access policy that targets: ‘Users: All users’, ‘Resource: Office 365’, ‘Location: United States’, and ‘Sign-in risk: High’. The results of the legacy tool and the new Graph-based What If tool behave as follows:
| Parameters Provided During Evaluation | Legacy Tool Result | Graph-Based API Result |
| Only UserId | ✅ Applies | ❌ Does not apply (missing app, location, risk) |
| UserId, ApplicationId | ✅ Applies | ❌ Does not apply (still missing location, risk) |
| UserId, ApplicationId, Location | ✅ Applies | ✅ Applies (meets user, app, location condition) |
| UserId, ApplicationId, Location, Sign-in Risk | ✅ Applies | ✅ Applies (all conditions matched) |
User Interface Comparison: Legacy vs. New Graph-Based ‘What If’ Tool
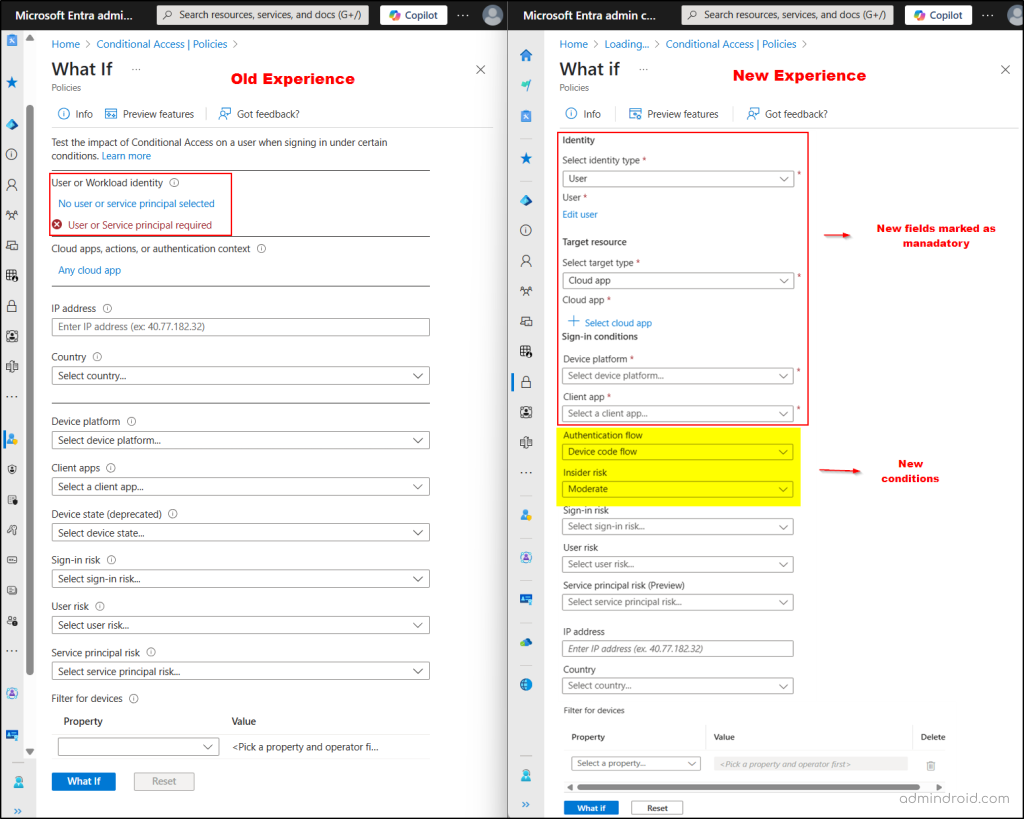
While both the legacy and new tool serve the same purpose, their user interface and interaction model differ significantly. To use the Conditional Access policies What If feature, go to the Microsoft Entra admin center → Protection → Conditional Access → Policies → What If (in the top bar).
If the enhanced What If evaluation is enabled in your Microsoft Entra ID, you’ll be presented with the new Graph-based What If tool. Otherwise, you’ll be redirected to the legacy What If tool.
Difference Between Legacy vs. New Graph-Based ‘What If’ Tool UI Experience
The following outlines the key differences between the legacy and the new Graph-based What If tools in the Entra admin center:
- The key difference is that the new experience requires you to provide more details such as the target resource, device platform, and client app. In the old version, you could simply select a user or workload identity and get results.
- The new experience supports the Insider risk and Authentication flow conditions, which weren’t available in the legacy tool.
- The deprecated ‘Device State’ condition has been removed in the new UI experience.
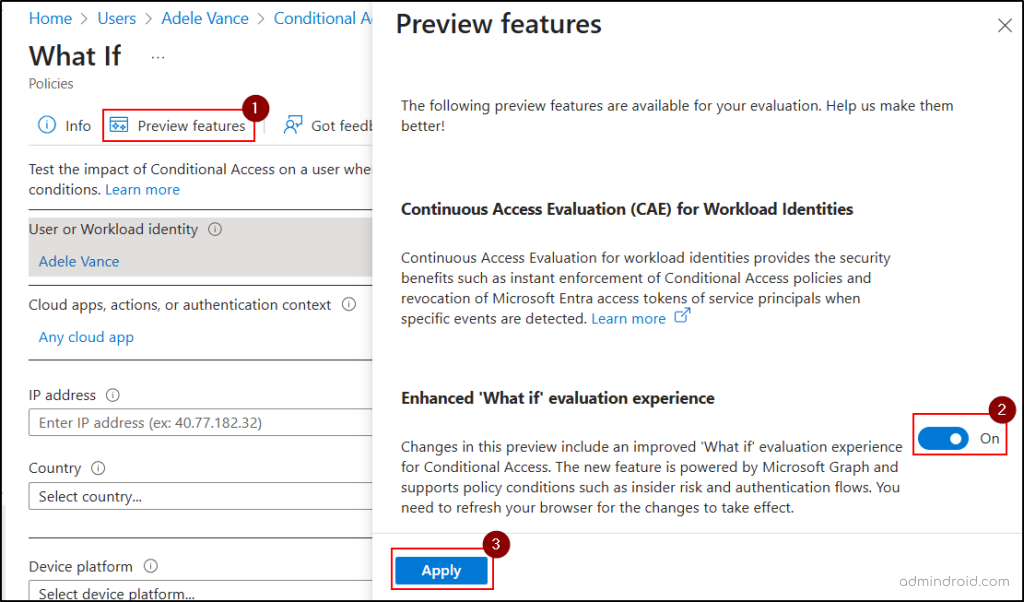
How to Enable New Graph-Based ‘What If’ Evaluation Experience in Entra Portal?
By default, the preview experience is enabled, but if you have disabled it, you can re-enable it easily:
- Go to the What If page in the Microsoft Entra admin center by navigating to Protection → Conditional Access → Policies → What If.
- Click the Preview features button at the top of the page.
- In the flyout pane, toggle the Enhanced ‘What If’ evaluation experience option to On and click Apply.
- Then, refresh the What If page to make the changes take effect.
Evaluate Conditional Access Policies with ‘What If’ Tool Using Graph API
One of the most exciting updates is the launch of the Microsoft Graph API for the What If tool. Because this API is part of Microsoft Graph, it comes with all the usual benefits like the ability to authenticate once and use that token across multiple Microsoft services seamlessly.
Here we’ll see how to test Conditional Access policies with What If Evaluation API tool using Microsoft Graph Explorer and PowerShell.
Test Conditional Access Using the ‘What If’ Evaluation API in Graph Explorer
To simulate a Conditional Access evaluation using Microsoft Graph Explorer, you need to use a valid JSON request body with the right HTTP POST endpoint.
The JSON payload must include the following resource types. Adhere to the official Microsoft Graph documentation linked with each resource type to build the correct structure.
- signInIdentity – Identifies the user or entity attempting the sign-in.
- signInContext – Specifies the sign-in scenario, like accessing an app or performing an action.
- signInConditions – Defines the conditions that apply during the sign-in attempt.
For example, to evaluate sign-ins for a user, refer to the userSignIn documentation linked within the signInIdentity documentation.
In addition to the required resources, you may optionally include the following (based on your evaluation needs): deviceInfo, authenticationStrength, appliedPoliciesOnly, and more.
Here’s a sample JSON payload used in a POST request to evaluate a Conditional Access policy:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
{ "signInIdentity": { "@odata.type": "#microsoft.graph.userSignIn", "userId": "15dc174b-f34c-4588-ac45-61d6e05dce93" }, "signInContext": { "@odata.type": "#microsoft.graph.applicationContext", "includeApplications": [ "00000003-0000-0ff1-ce00-000000000000" ] }, "signInConditions": { "clientAppType": "browser", "signInRiskLevel": "high", "userRiskLevel": "high", "insiderRiskLevel": "elevated", }, "appliedPoliciesOnly": true } |
📌 Optional: You can use the optional appliedPoliciesOnly flag in your request payload to return only the policies that match the evaluation, reducing noise in your response.
After drafting the JSON payload, complete the following steps to evaluate Conditional Access policies using Graph Explorer.
1. Sign in to Microsoft Graph Explorer using your Microsoft 365 account.
2. Set the HTTP request method to POST.
3. Choose beta as the Microsoft Graph API Version.
4. Enter the following API in the HTTP request URL:
|
1 |
https://graph.microsoft.com/beta/identity/conditionalAccess/evaluate |
5. Paste the drafted JSON payload you’ve created to evaluate the Conditional Access policies in the Request Body tab.
6. On the Modify Permissions tab, click Consent on the Policy.Read.All and Policy.Read.ConditionalAccess permissions.
7. Click Run Query to execute the request.
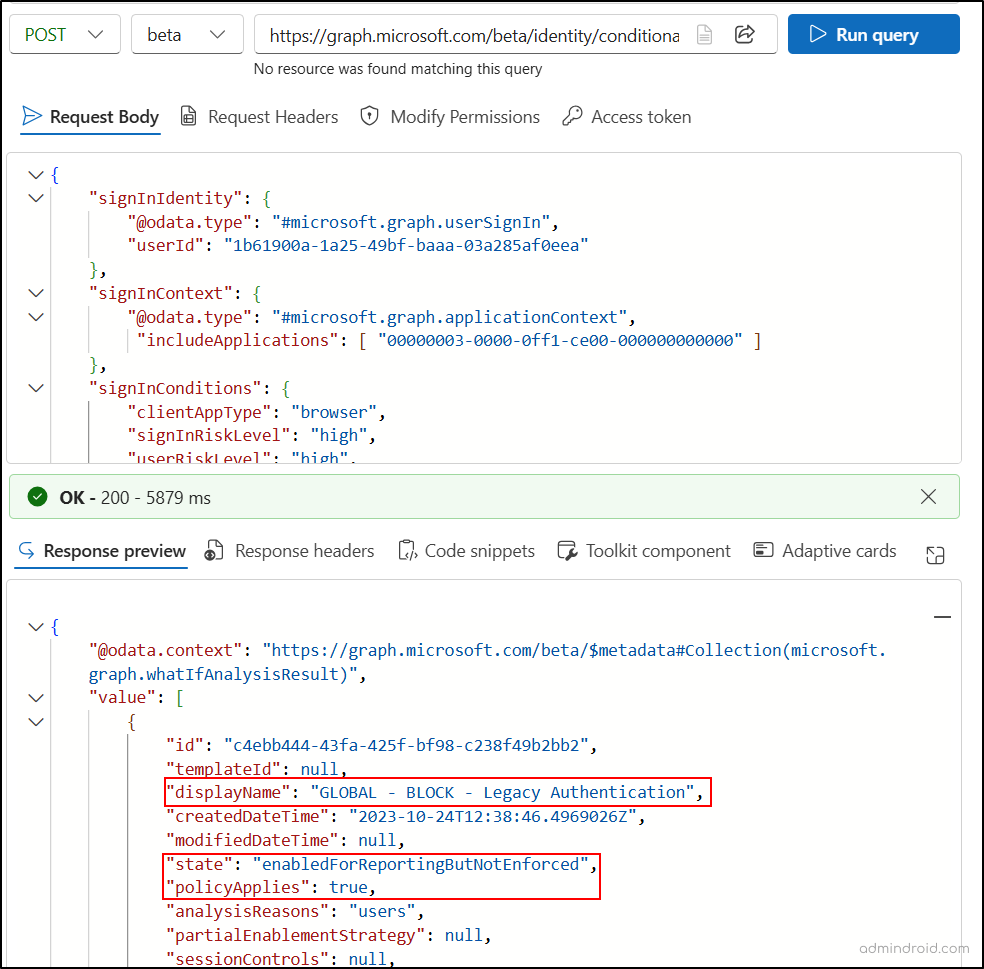
📝Note: Refer to the Conditional Access root evaluate examples presented in the Microsoft documentation for a clear approach to preparing the JSON request body.
Troubleshoot Conditional Access Using ‘What If’ Evaluation with Microsoft Graph PowerShell
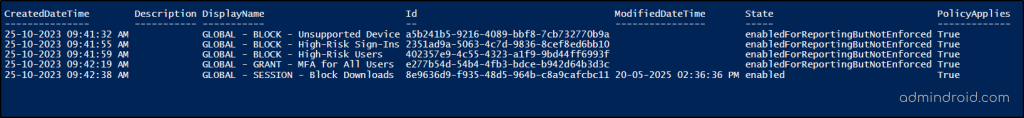
Similarly, you can use Microsoft Graph PowerShell to evaluate and troubleshoot Conditional Access policies with the What If evaluation. This allows you to format the output data neatly for better visibility. While the Graph API lets you filter and display data, PowerShell lets you present it in a clear table format.
To evaluate Conditional Access with What If evaluation using PowerShell, follow these steps:
1. Ensure the Microsoft Graph PowerShell module is installed on your machine.
2. Connect to Microsoft Graph PowerShell with the required permissions by running the cmdlet below. Alternatively, you can also connect to Microsoft Graph PowerShell using certificate.
|
1 |
Connect-MgGraph -Scopes "Policy.Read.All","User.Read.All" |
3. Then, run the ‘Test-MgBetaIdentityConditionalAccess’ cmdlet, to simulate Conditional Access What If evaluation. Make sure to replace the payload as needed.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
$payload = @{ signInIdentity = @{ "@odata.type" = "#microsoft.graph.userSignIn" userId = "15dc174b-f34c-4588-ac45-61d6e05dce93" } signInContext = @{ "@odata.type" = "#microsoft.graph.applicationContext" includeApplications = @("00000003-0000-0ff1-ce00-000000000000") } signInConditions = @{ clientAppType = "browser" signInRiskLevel = "high" userRiskLevel = "high" insiderRiskLevel = "elevated" } appliedPoliciesOnly = $true } | ConvertTo-Json -Depth 4 Test-MgBetaIdentityConditionalAccess -BodyParameter $payload |
Limitations of the ‘What If’ Evaluation API for Testing Conditional Access Policies
Below are some known limitations of the What-If API that you should be aware of when performing conditional access evaluations:
- The What-If API requires all sign-in parameters to be defined for accurate evaluation. Missing sign-in details related to specific policy conditions mean those conditions won’t be evaluated.
- It does not evaluate classic Conditional Access policies, so legacy policies won’t appear in the results.
- The API does not support “bundle” client app values, like Office 365 or Microsoft Admin Portals, limiting the scope of app-based conditions it can simulate.
📝Note: Since this API is currently in preview/beta, some features and behaviors might change.
Final Thoughts
The Microsoft Graph-based Conditional Access What If tool is a game-changer for Entra ID admins. It goes beyond manual testing by enabling scriptable, scalable, and accurate simulations of access behavior. Whether you’re onboarding new users or refining zero-trust policies, this tool ensures you’re always a step ahead of potential issues. To complement these evaluations, the Conditional Access Optimization agent helps identify redundant or rarely triggered policies, ensuring your CA configurations stay clean and efficient over time.
If you have any questions about Conditional Access policy evaluation with the new Graph-based What If tool, feel free to reach out through the comments section.