On Day 16 of Cybersecurity Awareness Month, learn how to set up fine-grained password policy for users and groups in your Active Directory environment to strengthen security and protect critical accounts. Stay tuned for more blogs in the Cybersecurity blog series.
Managing passwords is not just about enforcing complexity—it’s about precision and control. Traditional policies treat all users the same and put high-privileged accounts at risk. ⚠️ For example, an admin using a short or reused password under the same rules as regular users, becomes an easy target and threatens critical systems and sensitive data.
“A strong password is the first line of defense in a digital world.”
That is why organizations need targeted, role-specific password complexity rules to ensure users create strong and secure passwords. Administrators can enforce these by configuring Fine-Grained Password Policies (FGPP) for specific users and groups. Before diving into how FGPP works, it’s important to understand why such granular control is critical in Active Directory environments.
Impact of Weak Password in Active Directory
Weak passwords can be easily guessed or cracked using brute-force or dictionary attacks, which gives attackers unauthorized access to user accounts and sensitive data. If this happens, attackers can escalate privileges, move laterally across the network, and potentially take control of critical systems.
To mitigate these risks, administrators need more granular control over password policies, which is exactly what FGPP provides. Fine-Grained Password Policies help enforce strong, complex passwords and apply appropriate password policies.
Why Organization Rely on Fine-Grained Password Policies?
Default domain password policies enforce the same complexity rules for every user. However, not all accounts carry the same level of risk. For instance, a domain administrator account requires stronger protection than a standard user account.
Fine-Grained password policies solves this problem by letting administrators set different password rules. Stronger policies can be applied to protect high-privileged accounts, while simpler rules can be used for regular users to keep password management easy.
Understanding how FGPPs differ from default domain policies helps highlight their advantages and shows why they are necessary.
Fine-Grained Password Policy Vs Default Password Policies
Default domain password policies are configured through Group Policy Objects (GPOs) in the Default Domain Policy. These apply broadly across the domain and indirectly affect users via the computers they log in to locally.
Here are the key differences between fine-grained password policies and default domain password policies:
- Scope- GPO applies to users indirectly through computers, whereas FGPPs apply directly to specific users and groups.
- Precedence- FGPPs can override default domain password policies, which allows stricter enforcement for targeted accounts.
- Flexibility– FGPPs enable different password policies for different roles, offering a more tailored approach.
How to Configure Fine-Grained Password Policies in Active Directory
Now that the importance and benefits of fine-grained password policies are clear, let’s go ahead and set them up in your environment. There are two ways to configure them.
- Create fine-grained password policies in ADAC
- How to create fine-grained password policy using PowerShell
1. Create Fine-Grained Password Policies Using ADAC
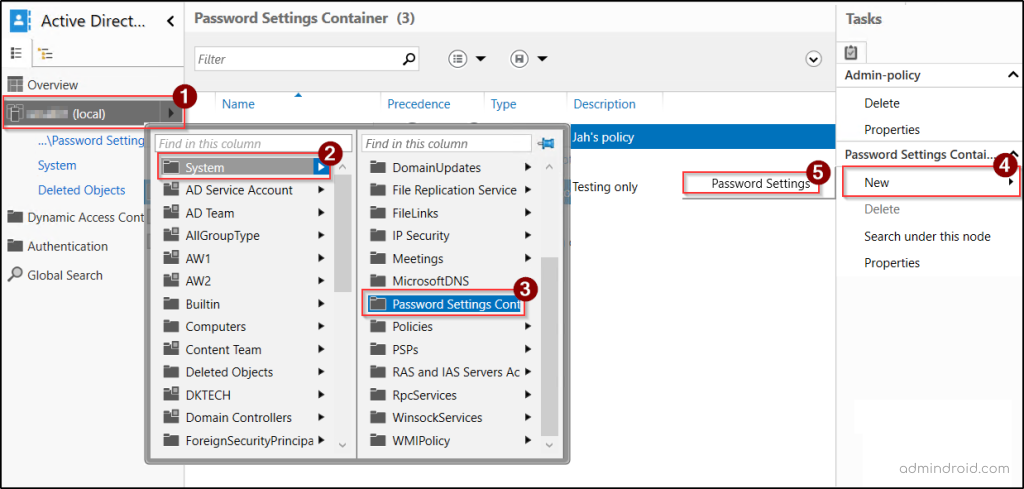
You can configure FGPPs in the Active Directory Administrative Center (ADAC) by creating ‘Password Settings’ within the Password Settings Container to define targeted password rules for specific users and groups.
Use the following steps to create stronger and role-specific password rules for users in Active Directory.
- Open the Active Directory Administrative Center (ADAC). Click on your domain and navigate to System → Password Settings Container.
- In the upper right corner, choose New → Password Settings.
- Configure the password parameters such as complexity, lockout threshold, password length, and history count.
- Assign the policy to specific users or groups from ‘Directly Applies To‘ section.
- Finally, click Ok to create the policy.
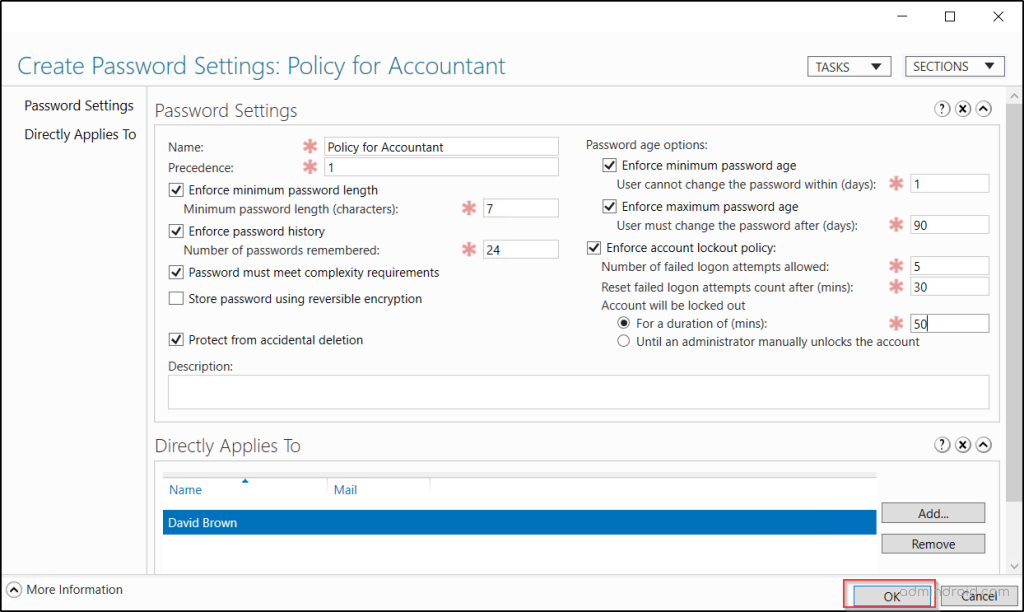
Once the password policy is created, administrators can easily modify or remove existing fine-grained password policies as organizational needs.
2. How To Create Fine-Grained Password Policy Using PowerShell
PowerShell offers a fast and efficient way to create a fine-grained password policy. This approach lets you complete the task easily without navigating through multiple menus and clicks.
You can use cmdlets like New-ADFineGrainedPasswordPolicy, Add-ADFineGrainedPasswordPolicySubject, and Get-ADUserResultantPasswordPolicy to create, assign, and verify password policies.
Open PowerShell as administrator and run the cmdlet below to create a fine-grained password policy.
|
1 |
New-ADFineGrainedPasswordPolicy -Name "Policy for Trainee" -Precedence "1" -ComplexityEnabled $true -LockoutDuration "00:20:00" -LockoutThreshold "4" -LockoutObservationWindow "00:20:00" -MaxPasswordAge "50.00:00:00" -MinPasswordAge "1.00:00:00" -MinPasswordLength "5" -PasswordHistoryCount "20" -ReversibleEncryptionEnabled $false -ProtectedFromAccidentalDeletion $true |
Here, a password policy name “Policy for Trainee” is created with specific rules for password length, complexity, and account lockout settings.
After creating a policy, assign the policy to groups or users by using the following cmdlet.
|
1 |
Add-ADFineGrainedPasswordPolicySubject -Identity "Policy for Trainee" -Subjects "Billa", "Trainee25" |
Here the user with logon name “Billa” and the security group “Trainee25” is assigned to the policy named “Policy for Trainee”
When a user falls under more than one policy, the one with the lowest precedence number takes effect. If two policies share the same precedence, the policy with the lower GUID is applied.
Check Which Fine-Grained Password Policies Applied to a User
A user might be affected by multiple fine-grained password policies (FGPPs) through different group memberships. To find out which policies are applied to the user, use the following PowerShell cmdlet.
|
1 |
Get-ADUserResultantPasswordPolicy -Identity "<User>" |
Replace the <User> with respective username of the user in the cmdlet.
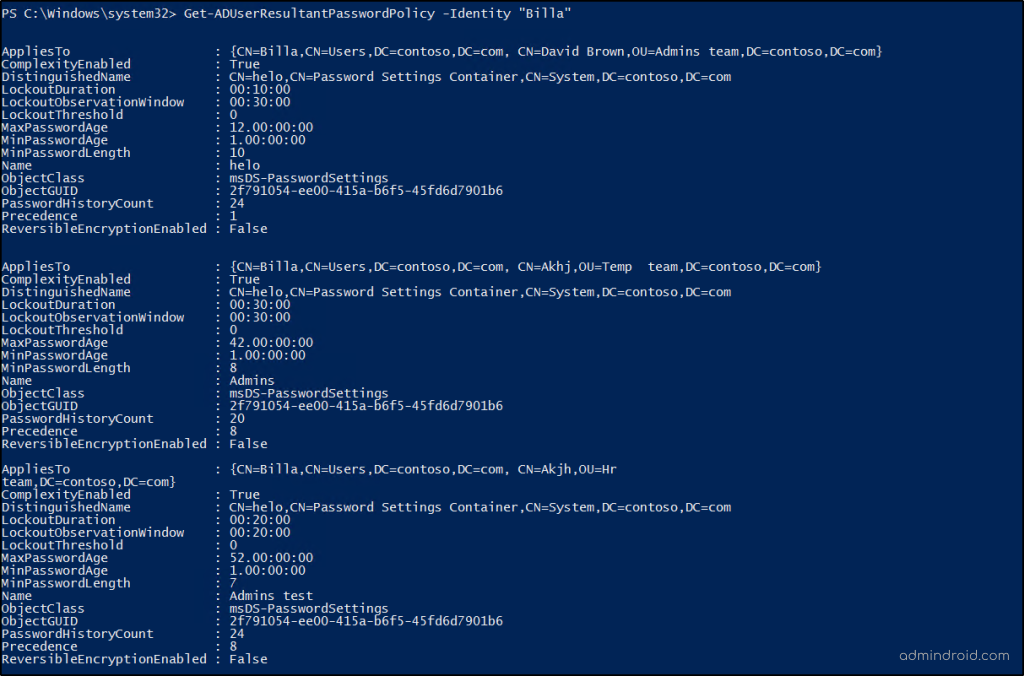
Before applying or modifying fine-grained password policies in your production environment, it’s best practice to test and review them in an Active Directory test lab. This allows you to verify inheritance and detect policy conflicts without risking unintended password restrictions or account lockouts in your live domain.
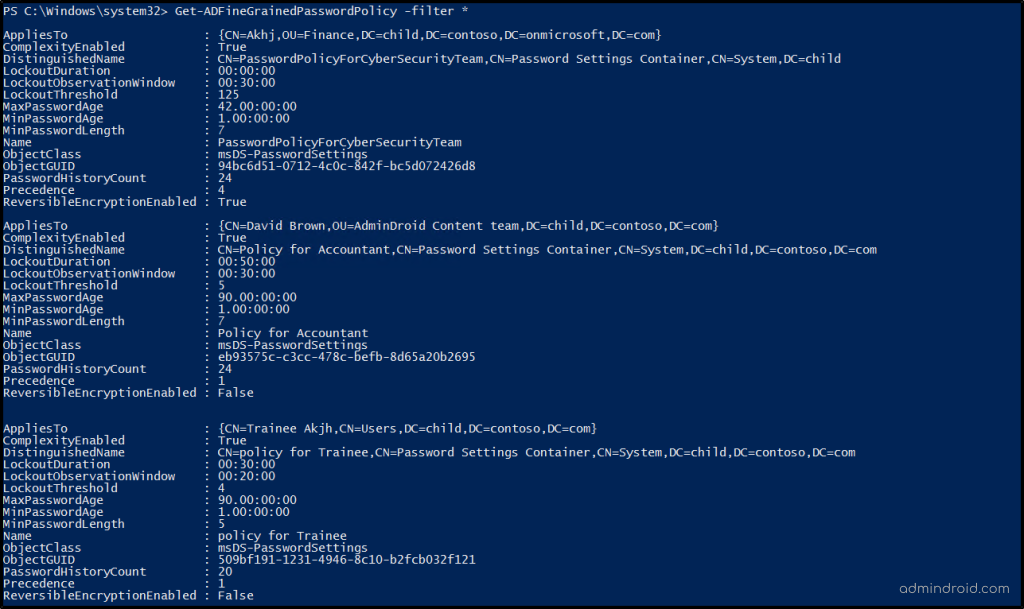
Additionally, regularly reviewing your FGPPs ensures they’re correctly configured and remain aligned with your organization’s security standards. Use the following cmdlet to list all password policies in your environment:
|
1 |
Get-ADFineGrainedPasswordPolicy -filter * |
We hope this blog helps you understand how to configure and manage fine-grained password policies in Active Directory. Configuring these policies serves as one of the most essential Active Directory security best practices to strengthen passwords, improve compliance, and enhance overall account protection. Stay tuned for more practical tips to keep your organization safe from evolving threats.