On Day 1 of Cybersecurity awareness month, learn to safeguard your organization from MFA attacks today. Keep an eye out for the upcoming blogs in our Cybersecurity blog series.
One single vulnerability is all the attacker needs
-Window Snyder
Why are we bringing this quote to your attention today? Well, because there are organizations out there still utilizing less secure MFA methods like SMS and voice calls. Are you one of them? If so, it’s like you’re leaving the door wide open for MFA attacks to stroll right in. 🚪💥”
But don’t fret! You can provide a airtight security strategy by steering your users towards a robust MFA approach. To help you with this, Microsoft gave the perfect answer via Entra ID recommendation: Migrate to Microsoft Authenticator. From the title alone, you might already have a hunch that this recommendation is all about transitioning your users to authenticate via Microsoft Authenticator💯.
But what lies beneath this Entra ID recommendation? Why has Microsoft been showing up this recommendation to your tenant? If these questions have been popping up in your mind, then don’t delay!
Explore this blog to uncover the compelling reasons behind Microsoft’s recommendation and swiftly transition your users to MS Authenticator!
Microsoft Entra ID Recommendation: Move Users to Microsoft Authenticator App
Microsoft 365 multi-factor authentication acts as a vital safety net, eliminating phishing, spoofing, and other malicious account compromise attempts. And if we dug deep into any account compromise attacks happening in your organization, the first reason would be the use of “less secure multi-factor authentication methods like SMS or voice calls!”
- SIM swapping attacks, MitM attacks, and other attacks are quite common with the above-mentioned MFA methods.
So, to stay one step ahead of these threats, it’s the admin’s responsibility to delete phone-based MFA and direct users toward the robust Microsoft Authenticator. Here, Microsoft gives a helping hand by bringing attention to this suggestion in the Entra admin center.
Microsoft shows up the “Migrate eligible users from SMS and Voice calls to Microsoft Authenticator app for better user experience” in Azure AD if it detects any users are authenticated continuously via SMS and voice calls for the past week. Also, this recommendation is currently in preview.
You might be curious why Microsoft suggests a shift to MFA push notifications and verification codes over other authentication methods. Let’s explore the reasons behind it in the following topic.
Why Microsoft Authenticator is the Best Choice for MFA?
A single crack in MFA can let your entire organization go under the attacker’s control! But a strong MFA method can filter out attackers’ malicious attempts in your tenant. And this is why Microsoft suggests a shift to MS Authenticator for authentication.
But what makes ‘Microsoft Authenticator’ robust and the best choice for MFA? It’s because it has a powerful lineup of security features like:
1. Azure MFA Number Matching:
Microsoft enforces MFA number matching in MS Authenticator, enabling users to input the two-digit number displayed on the Authenticator app’s homepage. This feature enhances security by mitigating MFA fatigue attacks. Match the numbers and access the rest!
When system-preferred MFA is enabled, users may see other sign-in methods first, like external authentication methods (EAM). For instance, if Authenticator is enabled, users are prompted for number matching but can choose another method before selecting EAM.
2. MFA Additional Context for Push Notification:
Admins can enable “Show location and application name for MFA request” features in Entra ID. This will show the location from where the MFA request has been initiated and the application name. Overall, this MFA location display will help detect and address anonymous MFA requests leading to MFA push notification attacks. Pinpoint the location and knockout cybercrimes!
3. Temporary One-Time Verification Codes in Microsoft Authenticator:
Each login attempt generates a unique, time-based one-time Passwords (TOTP). This means any captured old codes are worthless to the attackers, keeping your account safe. No more reusing OTPs!
4. No Internet Connectivity Needed for MFA:
Microsoft Authenticator allows users to utilize temporary one-time verification codes even in locations lacking mobile data or cellular signals, surpassing the limitations of SMS and voice calls. No connection is needed, just do a code verification!
5. Suppressing Authenticator Notifications from Risky Sources:
Now, Microsoft itself has started to suppress risky notifications in the MS Authenticator, eliminating MFA requests from unknown IP addresses and locations. Wipe out risky sign-in requests in the MS Authenticator app!
As we are done with the benefits, the next step we have to concentrate on is to know the steps to be taken when you receive the “Migrate to Microsoft Authenticator” recommendation. Let’s see that in detail.
Action Plan to Migrate Users to Microsoft Authenticator App
Once you see the “Migrate to Microsoft Authenticator” recommendation, your next step is to resolve it. But how will you do that? The Entra ID recommendation comes along with the action plan to help you fulfill it. Further, let’s see how to resolve the suggestion and shift to stronger MFA authentication effectively!
- Review multifactor authentication settings in Microsoft Entra ID
- Educate users to setup Microsoft Authenticator for MFA
Check the Multifactor Authentication Settings in Microsoft Entra ID
As an administrator, your first task is to review whether you have enabled users for the Authenticator app. By the way, you might have done this configuration via any of the two methods: Legacy MFA registration policy or authentication methods policy. So, we’ve provided steps to check whether it is enabled under each method for your convenience.
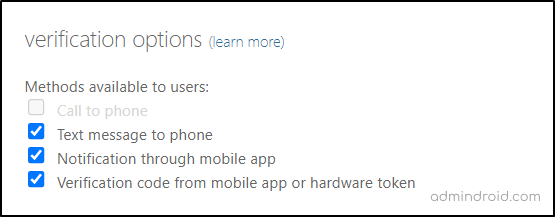
Way 1: Check the MFA settings in legacy MFA registration policy.
Microsoft Entra admin center → Protection → Multifactor authentication → Configure → Additional cloud-based multifactor authentication settings.
Ensure that the ‘Notification through mobile app‘ and ‘Verification code from mobile app‘ authentication methods are enabled for users. And if not, click the respective checkboxes to enable them.
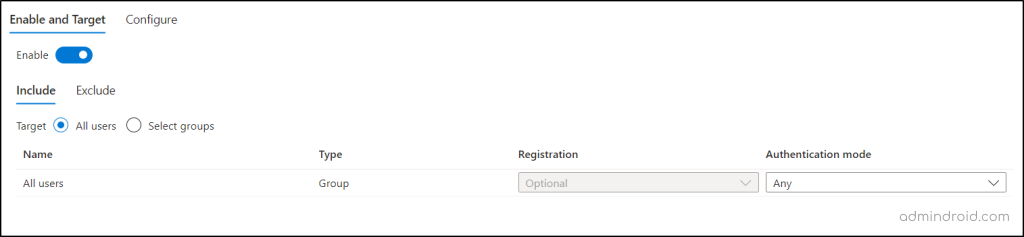
Way 2: Check the MFA settings in authentication methods policy.
Microsoft Entra admin center → Protection → Authentication methods → Policies → Microsoft Authenticator
Here, you need to check whether it is enabled for all the users in Microsoft 365. If not, include all the users in the policy.
Educate Users to Setup Microsoft Authenticator for MFA
Even after being given the option to use Microsoft Authenticator, users may hesitate to set it up, as they lie on the convenience of using less secure methods! So, it’s the admins’ responsibility to educate them about the significance of MS Authenticator app for MFA. Once they grasp its importance, the decision to transition to the Authenticator app becomes a natural choice.
Ensure that your Microsoft 365 users download the Microsoft Authenticator app before proceeding. Then, you can guide them with the steps below to add their M365 account to Authenticator.
Microsoft Authenticator → ‘+’ icon → work or school account → Sign in → Enter account credentials
Here, users need to complete their standard sign-ins (SMS, voice calls) and then click the ‘Finish’ button within the app. Once done, their account has been successfully added to the Microsoft Authenticator app.
If users continue to resist registering for the Authenticator app, then the only solution is to force users to register with Microsoft Authenticator for multi-factor authentication.
Suppose if you decide to nudge your users to use MS authenticator app for MFA, you can do that via two distinct methods given below.
- Push Users to Set Up Microsoft Authenticator App via Registration Campaign
- Set the Default MFA Method as Microsoft Authenticator for Microsoft 365 Users
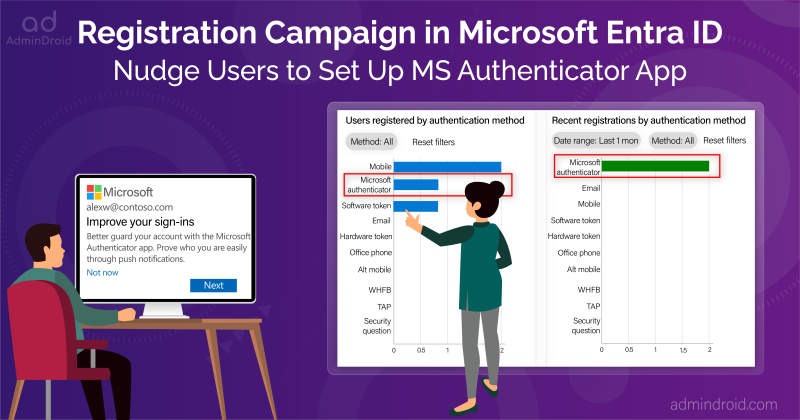
Push Users to Set Up Microsoft Authenticator App via Registration Campaign
Admins can enable registration campaign in Microsoft Entra ID to nudge MS Authenticator usage among users. This is a ‘Nudge’ feature that consistently prompts users to set up the MS Authenticator app for multi-factor authentication (MFA).
When an admin starts to run a registration campaign, it will trigger users to configure the Authenticator app after their typical sign-ins. While admins can permit a 14-day nudge skip, it’s unadvisable to allow snoozing, as it may pose security risks. Therefore, setting the snooze date to ‘0’ is appreciable to enhance security.
Once this is done, the recommendation will automatically be resolved in Microsoft Entra ID! ✅
Set the Default MFA Method as Microsoft Authenticator for Microsoft 365 Users
By the way, simply setting up the Authenticator app for MFA isn’t the endgame! 😯 Users might still have the ability to use less secure MFA methods, opening the door for attackers to make malicious sign-in attempts. Therefore, it’s advisable to set Microsoft Authenticator as the default MFA method for users.
Admins can change the default MFA method in Microsoft Entra ID, thereby making them authenticate via the secure MFA method only of their choice!
Final Takeaway
So, the decision to shift users from weaker to strong MFA methods is not just a choice; it’s a game-changer. When done right, there’s no room for attackers, no compromises, and absolutely no room for fear!”
I hope there will be no MFA attacks in your organizations as you are taking the decision to move your users to MS authenticator after the blog😉. Furthermore, if you require any assistance, please feel free to reach out to us in the comment section.