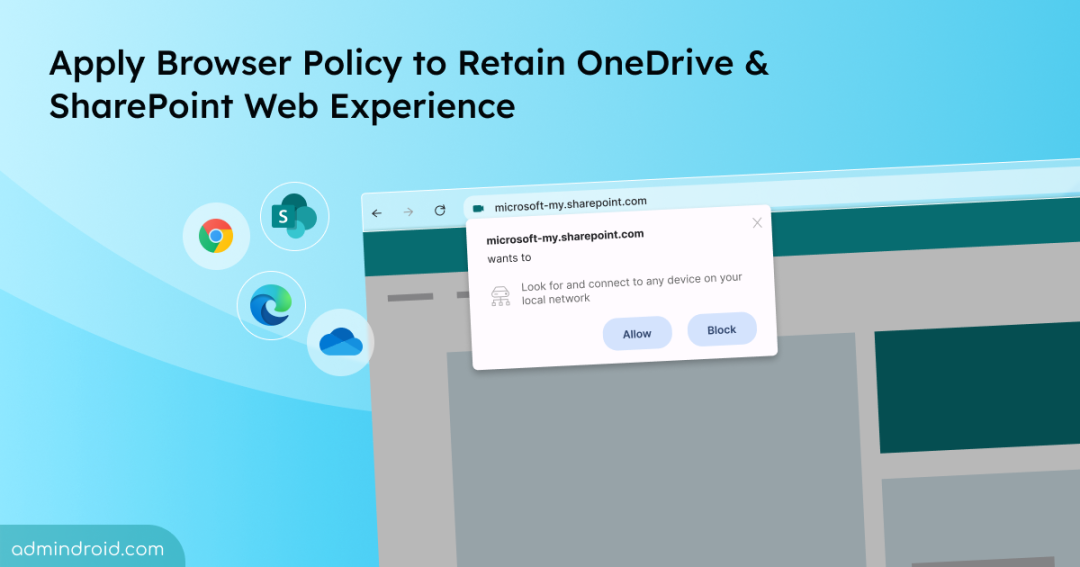
A browser privacy change in Chromium 141 introduces a new permission prompt that appears when public websites try to access a user’s local network. Chrome and Edge browsers will adopt this change by the end of September to protect users from malicious sites silently scanning or attacking devices on private networks.
Once enforced, users accessing OneDrive for web, SharePoint Document Libraries, and Microsoft Lists will encounter unexpected permission prompts for local network access. If the necessary browser policies to allow trusted Microsoft 365 domains for local network access aren’t in place, users will face degraded performance and lose offline functionality.
In this blog, we’ll break down how this change will impact your Microsoft 365, highlight the key browser policies to configure, and provide guidance on the necessary steps to stay prepared.
How Local Network Access Changes Will Impact OneDrive & SharePoint
This upcoming privacy enhancement will change the way users interact with OneDrive for Web, SharePoint Document Libraries, and Lists if no action is taken. When opening these sites, users will encounter a new browser prompt requesting permission for local network access.
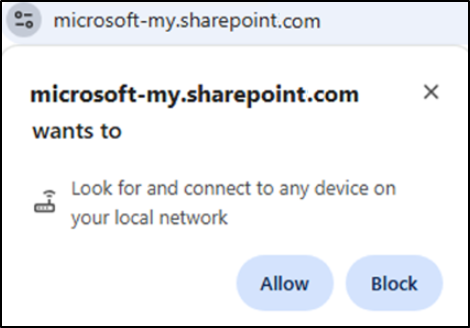
If users don’t click “Allow,” they’ll lose performance acceleration, leading to slower data access and the loss of offline functionality in OneDrive for Web. This could lead to a rise in help desk contacts from frustrated users facing unexpected prompts and missing features.
In addition to users, admins managing browser policies across Windows, macOS, and VDI environments will also be affected by this update.
Configure Browser Policies to Preserve OneDrive & SharePoint Web Performance
Instead of letting end users choose to allow or block access, which can restrict functionality, admins can configure the LocalNetworkAccessAllowedForUrls browser policy. Deploying this policy in advance suppresses the prompt for trusted Microsoft 365 endpoints while preserving performance and offline behavior for accessing OneDrive files.
Additionally, it helps reduce user confusion and minimize help desk requests. Here’s how to configure the Local Network Access browser policy.
1. List Trusted Domains
- Add your tenant’s SharePoint Online and OneDrive endpoints (https://<YourTenant>-my.sharepoint.com, https://<YourTenant>.sharepoint.com).
- Include any additional approved host variations, such as specialized cloud environments, but avoid using overly broad wildcards.
2. Configure Local Access Network Browser Policy
- Set the LocalNetworkAccessAllowedForUrls browser policy in Chrome and Edge to pre-authorize the listed domains.
- Deploy this policy to all your managed devices using ADMX/JSON for Windows and plist/configuration profile for macOS.
- Also, it is essential to deploy the allow-list even if policies like DisableNucleusSync or DisableOfflineMode already exist. This helps prevent future prompts and ensures a seamless user experience.
What to Do After Deploying the Browser Policy
Once the policy is deployed, any user who previously clicked “Block” will automatically have their settings overridden, restoring access to the trusted Microsoft 365 endpoints.
Next, ensure your OneDrive Sync Client is updated to v.25.164. For per-machine installs, the required permissions are applied automatically. Per-user installs will prompt users via a Windows Toast notification to enable the permissions, guiding them to complete setup quickly.
If immediate remediation is needed before the policy propagates, users can manually reset permissions using the following steps.
- Click the site lock icon in the browser’s address bar.
- Select ‘Allow’ from the Local Network Access permission dropdown.
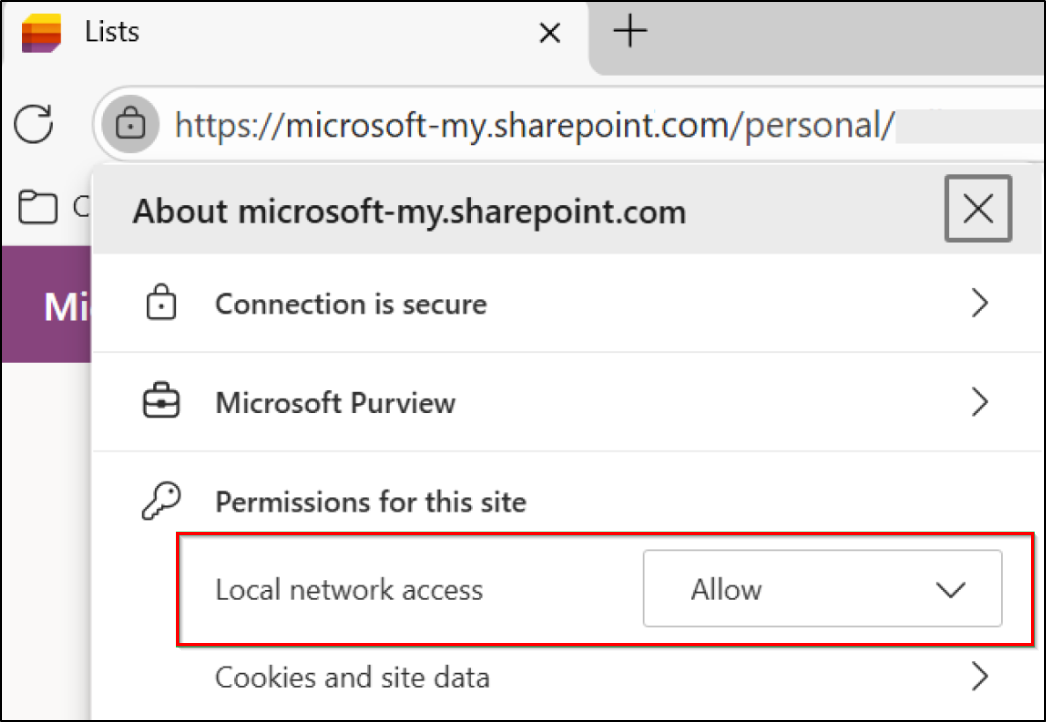
This permission will allow OneDrive to store file metadata locally and operate a local web server, which is essential for offline functionality. Without them, offline mode will not work correctly.
Points to Remember
Even though all information was conveyed in a detailed manner, here are the key points extracted for quick reference and special attention.
- Configure the local network policy before the Chromium 141 rollout in late September.
- You can deploy the LocalNetworkAccessAllowedForUrls browser policy using Group Policy or configuration profiles. Deployment can be scoped to device groups managed via Entra ID.
- Local network access affects how OneDrive and SharePoint optimize performance and offline access to cached data.
- If the policy is not enforced, users can manually allow or block local network access through browser prompts.
- If your organization primarily uses non-Chromium browsers such as Mozilla Firefox, this update will not impact your users.
In a nutshell, proactively configuring the LocalNetworkAccessAllowedForUrls browser policy preserves OneDrive & SharePoint offline access, maintains performance, and prevents unexpected prompts. Deploy it early to ensure seamless access, reduce help desk requests, and keep your organization running smoothly.