On Day 21 of Cybersecurity Awareness Month, learn how to prevent users from adding computers to your domain using the Group Policy Object. Stay tuned for more security insights in our ongoing Cybersecurity blog series.
Did you know that, by default, any authenticated user in Active Directory can add computers to your domain—up to a total of 10? 😳 Yes, the default setting of the “Add Workstations to Domain” privilege and the ms-DS-MachineAccountQuota attribute behind the scenes allows this ability to any user.
This hidden configuration can turn into a serious vulnerability for your network. Every computer added without oversight is a potential gateway for attackers. Beyond compliance risks, accounts used to join computers have elevated permissions that attackers can exploit to escalate privileges, impersonate users, and move laterally across the network.
In short, leaving this default setting unchecked is like leaving your front door unlocked. It gives attackers an easy way to exploit generic access rights and compromise your Active Directory environment in multiple ways.
To secure your network, understand why restricting this privilege is important and learn how to limit domain-join permissions through proper user rights assignments.
Why You Should Restrict Who Can Join Computers to the Domain
Allowing all authenticated users (anyone with valid domain credentials) to join computers might seem harmless. However, it opens multiple attack paths that can be chained together to take over systems and escalate privileges.
Key risks include:
- Quota abuse
Default quotas let non‑privileged accounts create computer objects. Attackers can use those accounts and computer objects as footholds inside the Active Directory.
- Delegation abuse
If an attacker controls a computer object, they can exploit delegation mechanisms to impersonate other accounts. Resource-Based Constrained Delegation (RBCD)in particular allows attackers to move laterally and escalate privileges across the network.
- Relay and delegation chains
Attackers can combine domain-join gaps with common authentication attacks, like NTLM relays or Kerberos delegation, to gain higher privileges or execute remote code on other systems.
- Object ownership and Access Control List (ACL) abuse
How a computer account is created determines its owner and permissions. Uncontrolled ownership or loose ACLs can allow attackers to change rights or enable further abuse.
These vulnerabilities make it clear that allowing users to add computers to the domain creates multiple paths for attackers. This alone is reason enough to ensure that unauthorized workstations cannot be joined to your domain.
How to Prevent Users from Adding Computers to the Domain in Active Directory
To prevent users from adding computers to the domain, you can follow the steps below.
Step 1: Set “ms-DS-MachineAccountQuota” Attribute to 0
The ms-DS-MachineAccountQuota attribute in Active Directory defines how many computer accounts a user can create in the domain. By default, this quota is set to 10, which means any authenticated user can add up to 10 computers to the domain.
To restrict this, set the ms-DS-MachineAccountQuota attribute to 0 using ADUC.
- Open the Active Directory Users and Computers console.
- Right-click your domain (e.g., DC=contoso,DC=local) and select Properties.
- Go to the Attribute Editor tab. Scroll to ms-DS-MachineAccountQuota and click Edit.
- Change its value from 10 to 0, then click OK twice.
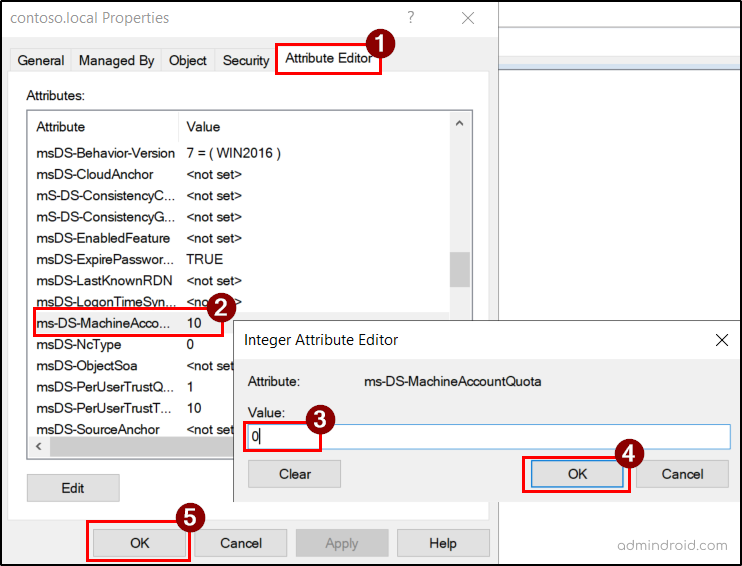
Setting the quota to 0 helps prevent users from adding computers to the domain unless explicitly delegated, significantly improving security and control. However, this setting does not affect users in the Administrators or Domain Admins groups, who can still create and delete computer accounts in Active Directory.
Step 2: Restrict ‘Add Workstation to Domain’ Privilege Using GPO
The Add Workstations to Domain privilege is a user right in Active Directory that controls which accounts can add computers to an Active Directory domain.
By default, this privilege is granted to Authenticated Users on domain controllers, allowing any domain account to add up to 10 computers (as governed by the ms-DS-MachineAccountQuota).
Even if you set the ms-DS-MachineAccountQuota to 0, this alone is not sufficient. If the quota is later changed or misconfigured, users could regain the ability to add computers because of the default Add Workstations to Domain privilege.
For this reason, it is critical to remove this privilege from Authenticated Users and assign it explicitly to a dedicated security group with delegated permissions using Group Policy Objects. This ensures the restriction remains effective even if the machine account quota is modified in the future.
Delegate a Security Group to the Computers Organizational Unit
- Open Active Directory Users and Computers console.
- In the left pane, locate and right-click the Computers OU (the default container where new computers are added).
- Select Delegate Control to launch the Delegation of Control Wizard.
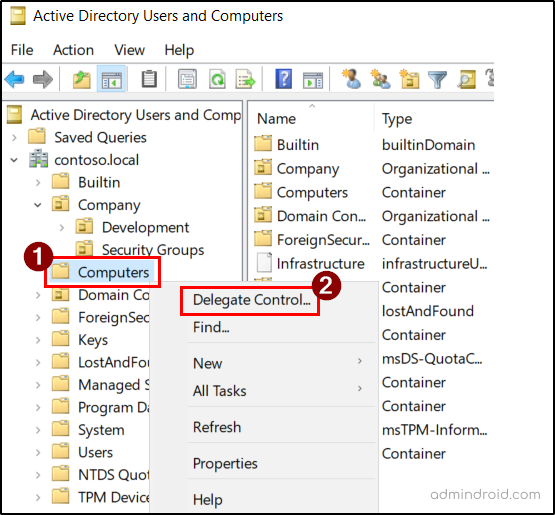
- Click Next, then Add, enter the security group (e.g., Join-Computers), click Check Names, then OK, and Next.
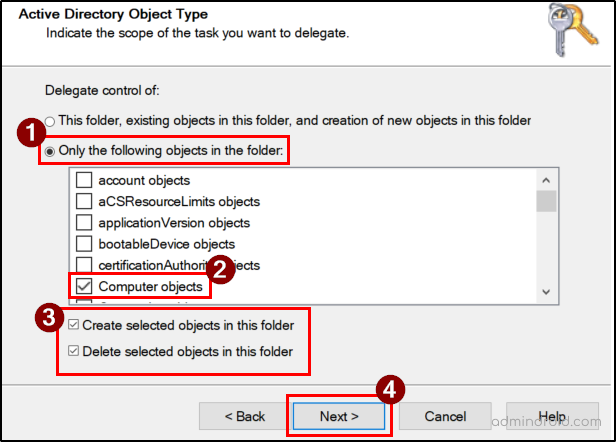
- Choose Create a custom task to delegate and click Next.
- Select Only the following objects in the folder under Delegate Control of, then check Computer objects.
Also, enable the permissions:
- Create selected objects in this folder
- Delete selected objects in this folder
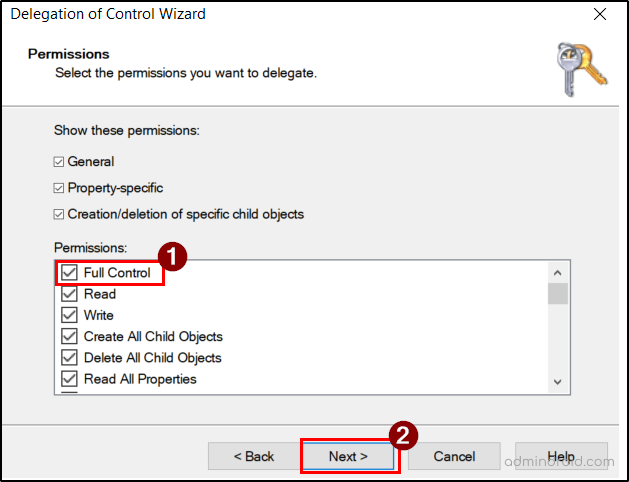
- Click Next and choose Full Control in the Permissions section. Then, select Next and click Finish to complete the delegation.
Note: To check the delegation permission, right-click the Computers OU and select Properties. Navigate to the Security tab and locate the added security group under the Group or user names section. Select the group to view its assigned permissions in the Permissions for section.
Prevent Users from Adding Computers to the Domain
- Open Group Policy Management Console (GPMC).
- Expand the domain name, select Domain Controllers container and locate Default Domain Controllers Policy GPO.
- Right-click the GPO and choose Edit. Navigate to:
Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → User Rights Assignment - Select Add workstations to domain policy and double-click to open it. Select Authenticated Users and click Remove. Then, click Apply.
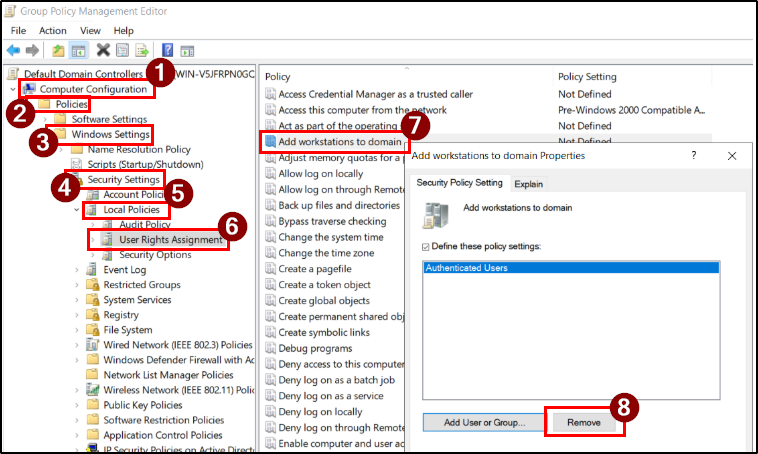
Assign the ‘Add Workstation to Domain’ Privilege to the Security Group
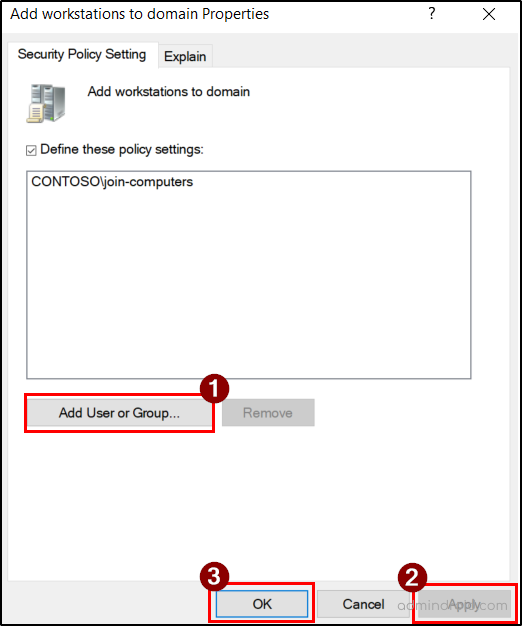
After removing users from the default policy, assign the privilege to the delegated security group so that only its members can add computers to the domain.
- Click Add User or Group, then click Browse.
- Enter the security group name(join-computers) and click Check Names. Then, select the group and click OK.
- Select OK again, to save your changes.
Right-click the Default Domain Controllers Policy on Group Policy Management Console and select Refresh. Then, under the Settings tab, expand Show All and scroll to Computer Configuration to verify the updated changes.
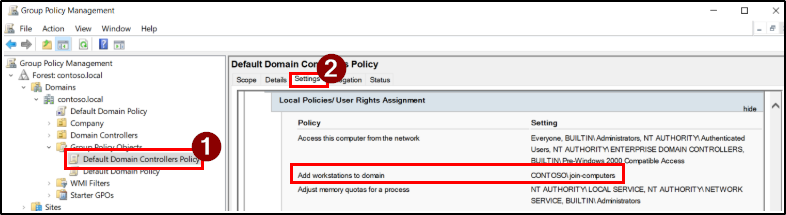
This ensures the selected group permission to add or delete computer objects within that OU, without needing domain-wide privileges. This approach provides finer control and reduces security risks.
Note: If you prefer to keep this restriction separate from the default policies, you can create a dedicated Group Policy Object (GPO) to manage who can add computers to the domain and add your security group to this GPO. This approach helps maintain cleaner policy control and easier troubleshooting.
However, before applying this new policy, ensure that the default configuration in the Default Domain Controllers Policy (which allows authenticated users to add computers to the domain) is restricted.
In conclusion, restricting who can join computers to the domain is a simple but powerful way to prevent unauthorized workstations from joining your network and maintain better visibility over domain-joined systems. Combine this with other Active Directory security best practices to strengthen your domain security.
A few minutes of configuration can make a big difference in your Active Directory security posture.






