On Day 19 of Cybersecurity awareness month, learn to integrate SharePoint and OneDrive with Azure AD B2B today. Stay tuned for more blogs in the Cybersecurity blog series.
Sharing in Microsoft 365 is governed by Azure Active Directory. Azure AD B2B collaboration is a feature within External Identities management that lets you invite guest users to collaborate with your organization. On the other hand, Ad-hoc sharing via One Time Passcode is the traditional way of sharing content with external users in SharePoint online. But if a setting can do more than the existing one, it is better to give it a try. Integrating SharePoint and OneDrive with Azure B2B Invitation Manager extends your secured external collaboration. It provides an extra layer of security for externally shared content.
“Data is the pollution problem of the information age, and protecting privacy is the environmental challenge“
– Bruce Schneier
Have you enabled the Azure AD B2B Integration for your organization to protect your data?
If not, turn it on right away! The benefits are compelling. Let’s check them in detail.
UPDATE: Azure B2B Integration with SharePoint & OneDrive will be turned on by default for new tenants as of March 31, 2023.
What is Azure AD B2B Collaboration?
Azure B2B Collaboration is a feature that lets users securely collaborate with externals such as business partners even if they don’t have Azure AD or an IT department. With Azure AD B2B, the partners can use their own identities to access resources. The Azure AD B2B setting for external collaboration is available in the External Identities section of the Azure AD Admin Center.
How to Integrate Azure AD B2B with SharePoint and OneDrive?
By integrating SharePoint and OneDrive with Azure AD B2B, users can share files, folders, lists, libraries, and even sites with people outside their organization. After integrating with Azure AD B2B, the sharing invitation is sent via the Azure B2B platform instead of SharePoint B2B which automatically adds the guest users to the Azure AD directory. Once the integration is enabled you and your users don’t have to reshare or do any manual migration for guests previously shared.
Note: There is no specific license required for enabling this integration.
The Azure AD B2B Integration can be enabled by using the SharePoint Online Management Shell.
- Make sure you have downloaded the latest SharePoint Online Management Shell.
- Run the below cmdlet in the SharePoint Online Management Shell command prompt to connect to the SPO module.
|
1 |
Connect-SPOService -Url https://<yourdomain>-admin.sharepoint.com |
- To enable Azure AD B2B for your organization, run the following cmdlet.
|
1 |
Set-SPOTenant -EnableAzureADB2BIntegration $true |
- To ensure you have integrated successfully, run the following cmdlet.
|
1 |
Get-SPOTenant | Select *B2B* |
However, there might be specific scenarios where you want to disable this integration, such as for security or compliance reasons. Here’s the PowerShell cmdlet to disable SharePoint and OneDrive integration with Azure AD B2B.
|
1 |
Set-SPOTenant -EnableAzureADB2BIntegration $false |
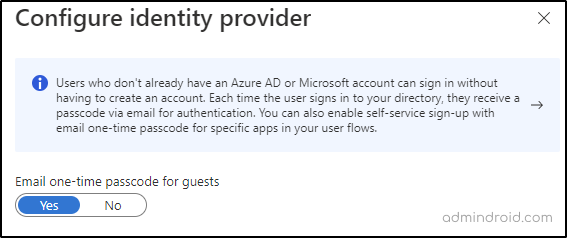
Azure AD B2B Integration together with the Azure AD one-time passcode functionality will increase security for external sharing. Using OTP functionality, users can sign in even if they don’t have an Azure AD or Microsoft account. It is turned on by default. Make sure that the one-time passcode switch is toggled to ‘yes’ from the All Identity Providers section of the Azure AD Admin Center.
Difference Between SharePoint External Sharing and Azure B2B Collaboration
As we all know, SharePoint external sharing is confusing and includes complex steps to set up, the following table depicts the major difference between guest access provided through Secure external sharing recipient experience and Azure AD B2B.
| Current SharePoint External Sharing | AAD B2B Integration with SharePoint and OneDrive |
| When sharing a site, the Ad hoc external recipient is prompted to create an MS account to authenticate. Ad hoc external recipients are not subjected to conditional access policies. | After accepting the consent from the recipient, a guest account is created in Azure AD for authentication. Guest accounts can be subjected to conditional access policies. |
How Azure AD would Improve External User Experience?
Before Enabling Azure AD B2B Collaboration
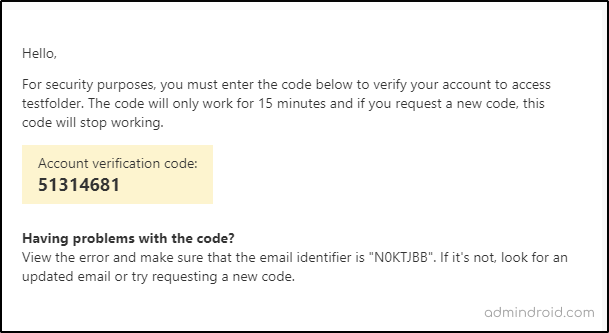
When you use the existing SharePoint Guest B2B for collaborating with users who are not in your directory, they are prompted to enter the verification code that is sent to their email, and once they enter the code, they can access the resource. That is only one step authentication via email is applied here.
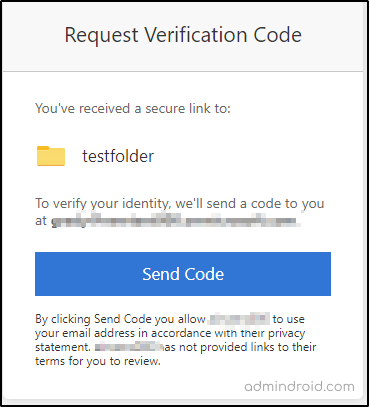
After Enabling Azure AD B2B Collaboration
When a guest signs in for the first time, the following consent page is displayed for them which includes Review permissions. The user can continue only if he accepts the permission request.
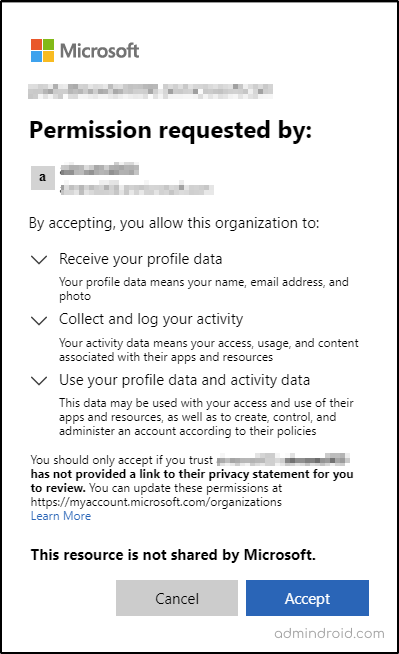
Additionally, if your organization has configured any conditional access policies such as MFA, the guest users are required to prove their identity before accessing the resource.

As we can now apply conditional access policy to Ad-hoc users as well, a preview feature introduced in Conditional access policy settings adds more benefits to this integration. Let’s explore them in detail.
When you create a new conditional access policy, the ‘Select users and groups’ section allows you to select users or groups you want to apply the policy to.
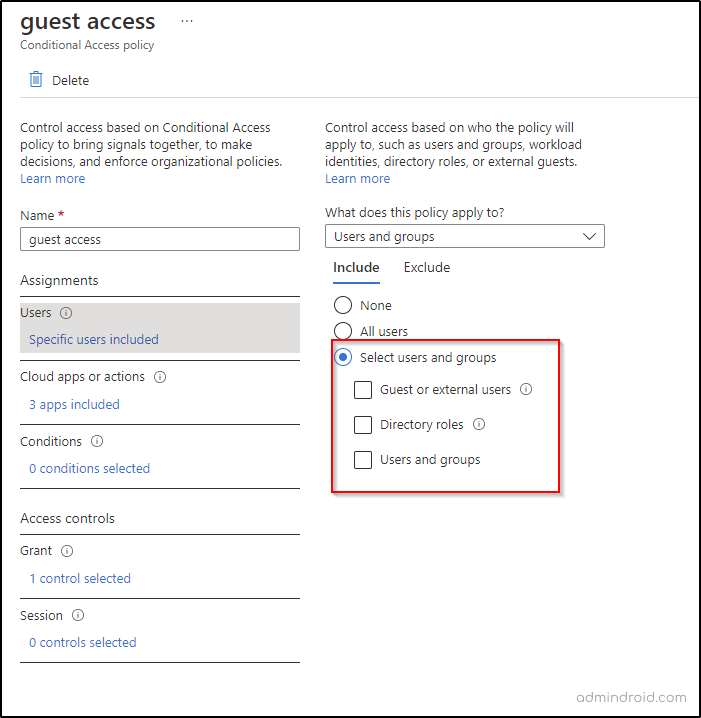
Earlier, the ‘All Guest and external users’ option when selected enforces conditional access policies to all users who fall under the attribute type ‘Guests’ in the directory. But now, Microsoft has enhanced this capability by including various types of external users and it is available for public preview.
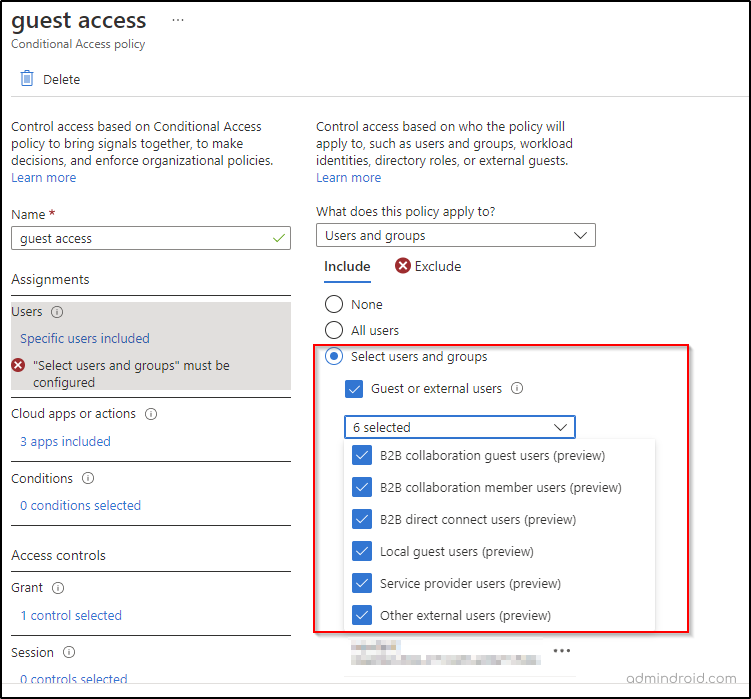
Admins can now choose to include or exclude any kind of external users among the following.
B2B collaboration guest users: These are users who are invited as guests and used self-service sign-up. They are given guest-level permissions in your organization. The Azure directory user type is ‘Guest’ for these users.
B2B collaboration member users: These users have an account in External Azure AD or other external identity providers with member-level access to resources in your organization. The Azure directory user type is ‘Member’ for these users.
B2B direct connect users: These users are mutually connected with another Azure AD organizations. They are not found in the directory list but are instead managed from within the application (for example, by the Teams shared channel owner).
Local guest users: Your organization manages the credentials of these users internally, and you have access to them at all times. They are designated as guests by setting the user object UserType to ‘Guest’.
Service provider users: Organizations that serve as cloud service providers for your organization.
Other external users: These are any users who don’t fall into the above-mentioned categories. They are not included as internal members as well and they don’t authenticate via Azure AD.
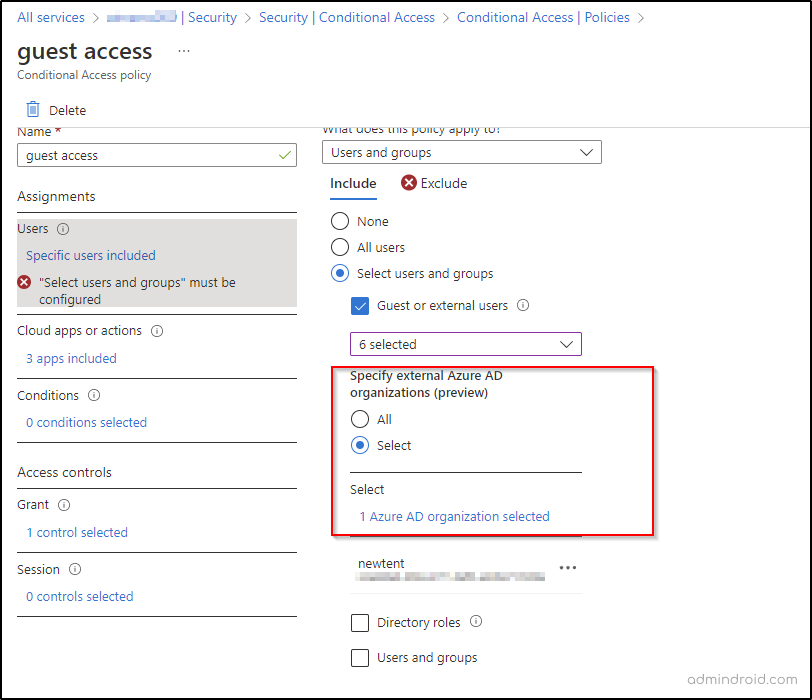
Apply CA Policy to Specific External Azure AD Organizations
This new preview feature allows you to apply CA policies to external Azure AD organizations. You can either select all or add specific organizations by entering their domain names.
What are the Other Customizations Available in External Identities?
Settings that give complete control on managing External Identities within the Azure AD Admin Center in a nutshell!
Cross-Tenant Access Settings for Collaboration
The Cross-tenant access setting allows collaboration only between Azure AD organizations. There are two types – B2B Collaboration and B2B Direct Connect.
B2B Collaboration – Used to invite users from Microsoft services by adding them as guests to your tenant.
B2B Direct Connect – Used to allow users from external Azure AD organizations to access resources directly without being added as guests through a mutual way of connection, configured by admins.
Identity Provider for External Identities
An Identity provider manages the identity information for authentication. Azure Active Directory and Microsoft Account are already added as configured identity providers for External identities. Therefore, external users who already have an Azure AD or Microsoft Account can sign in automatically using one-time passcode when the integration is enabled. You can also add other identity providers like Google federation, Facebook, and SAML/WS-Fed identity provider federation so that external users you invite can redeem invitations using their own social accounts.
External Collaboration Settings
In the external collaboration settings section, you can
- Manage the level of access for a guest user and also specify who can invite guests.
- Manage external users leaving themselves from your organization using external user leave settings.
- Use domain settings to allow/block external sharing to specific domains in your organization.
Create User Flows Using Self-Service Sign Up
This feature is used to create user flows that allow a user to sign up and create a new guest account by following the rules created with the flow such as identity providers that the user must use to sign in and user attributes that must be provided during sign-in.
Lifecycle Management
Terms of Use – In this section, admins can create Terms of Use policies that will be presented to the users at the sign-in and thereby requiring them to accept the policies before accessing the shared content.
Access reviews – Azure AD access reviews are used to efficiently manage roles and group memberships and can be reviewed to make sure only the right people have access.
Important Points to Remember
- When this integration is enabled, any external sharing setting for site collection remain unchanged. That is, if external sharing is turned off for a site collection, it will remain off.
- If the Azure AD organizational setting for external sharing is more restrictive than SharePoint or OneDrive external setting, only the Azure AD setting will override.
- The existing SharePoint B2B users are converted into Azure AD B2B guest users on signing in after integration.
- If you disable integration, the users who were shared to while the integration was enabled will still be Azure AD guests. To convert them back into SharePoint B2B guests, you need to delete the user from the Azure AD.
I hope this blog will guide you through the concepts of Integrating SharePoint and OneDrive with Azure AD B2B. Feel free to reach us in the comments for any assistance!
AdminDroid Reporting Suite for Managing External Sharing in SharePoint Online
Monitoring external users in SharePoint and OneDrive is an essential aspect of Office 365 management. While audit logs provide some level of monitoring, administrators should not solely rely on them. To prevent potential resource exploitation, it is crucial to gather accurate information. Worry no more! AdminDroid Microsoft 365 reporting tool has got you covered with its steadfast reports on site-sharing settings such as external sharing configurations, link-enabled sharing, etc. Additionally, AdminDroid offers a dedicated report board on external users that covers the following.
External User Info
- External/guest users
- Recently created external users
- SharePoint Guest users
- Groups by external users count
External User Audit
- External members added/removed from groups
- Guest/external user sign-ins
File/Folder/Page activities
- Files shared by/to external users
- File accessed by external users
- Page activities by external uses
External User Memberships
- External user memberships
- External members added/removed to SharePoint groups
Along with these reports, AdminDroid also offers reports on various policy audit reports that help admins to keenly observe any policy configured for external sharing in SharePoint Online and OneDrive. With these reports, admins can gain valuable insights into the policies implemented and ensure efficient management of their environment. Whether your business is large or small, leveraging AdminDroid SharePoint auditing tool can significantly enhance the efficiency and effectiveness of your management practices.
SharePoint Online management is made easy with AdminDroid which has comprehensive dashboards for widespread visibility! Moreover, the tool offers advanced features such as delegation, advanced scheduling, and advanced filtering that can help you manage your SharePoint Online environment with ease. Download AdminDroid and enjoy hassle-free Office 365 management today!






