Gear up for Day 6 of Cybersecurity Awareness Month series ! Today, we’ll explore how to strengthen your organization’s identity posture with the three Microsoft identity secure score recommendations. Stay tuned for insights on other vital aspects of Microsoft Secure Score each day.
“Your identity is your most valuable possession—protect it!” This powerful quote resonates not only with individual users but also with organizations. If you’ve implemented Microsoft 365 security settings to protect your organization’s identity, give yourself a well-deserved pat on the back!
But don’t stop there! We’re excited to share three essential identity secure score recommendations. Check your checklist—if you’ve already put them into action, kudos to you! If not, don’t worry; we’ll walk you through each recommendation in detail to help improve your identity secure score.
Before we dive in, let’s first discuss what Microsoft Secure Score means in relation to identity.
What is Microsoft Secure Score?
Let’s start from the basics! Microsoft Secure Score is a feature within Microsoft Defender that offers a numerical summary of your organization’s security status based on your configured settings. It provides a set of recommended actions by comparing your configurations against Microsoft’s security standards. As you implement these recommended security features, you earn secure points that contribute to your overall security score.
Essentially, the higher your score, the stronger your organization’s security posture, allowing you to reduce vulnerabilities in Microsoft 365.
What is Identity Secure Score and Where to Find It?
Microsoft secure score provides scores across various categories, such as apps, data, and devices. Among these, the secure score focuses specifically on recommendations related to an organization’s identity, which we call “Identity secure score recommendations”.
The Identity secure score is a percentage that measures how well an organization’s identity security aligns with Microsoft’s security recommendations. It serves as an analytical tool to help organizations:
- Measure their identity security level.
- Plan improvements to their identity security.
- Review the success of those improvements.
You can find Identity secure score in two areas.
A) View Identity Secure Score in Microsoft Entra Admin Center:
- Sign in to the Microsoft Entra admin center with required permissions.
- Go to the Identity > Overview > My feed > Secure Score for Identity > View secure score.
Here, you’ll be able to view:
- Identity Secure Score: This provides insights into your organization identity secure score percentage, helping you understand how well you’re protected.
- Comparison Dashboard: This feature benchmarks your security score against other organizations of a similar size, allowing you to see where you stand in the secured organization row.
- Score History: Track improvements or changes over time, making it easier to monitor your security progress and identify areas needing attention. You can review and analyze trends over the past 7, 30, 60, or 90 days.
- Improvement Actions: Contains Azure AD identity secure score recommendations along with the score impacts, status and other insights.
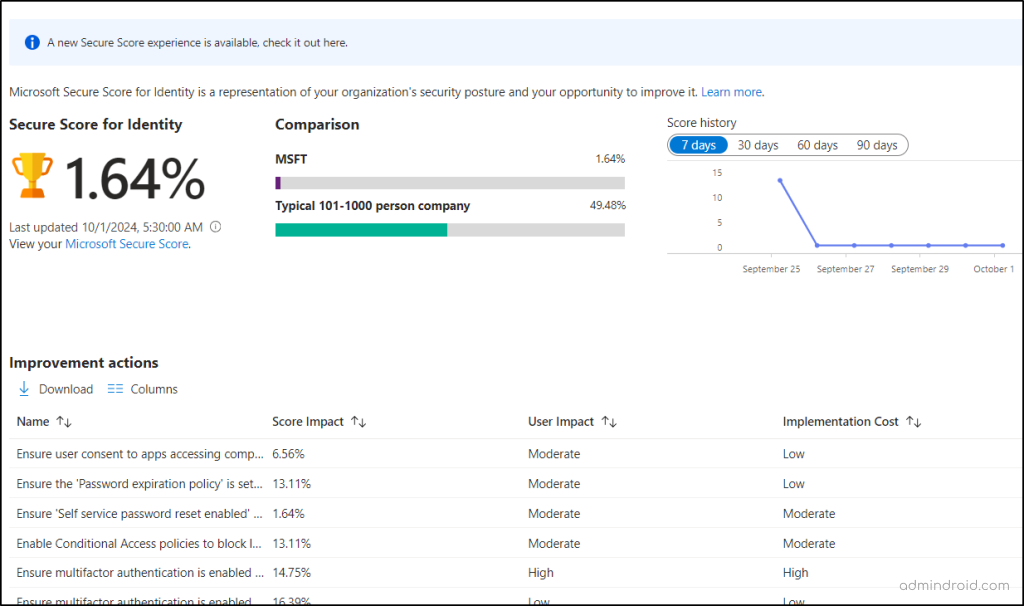
You can also be able to view the Identity secure score under Entra ID recommendations.
B) View Identity Secure Score Recommendations Via Microsoft Defender
- Sign in to the Microsoft Defender.
- Go to the Expose Mangement > Secure Score > Recommended Actions.
- Filter the results to show recommendations of “Identity” category.
Now, you can view all the identity recommendations specific to your tenant, along with valuable insights such as score, points, status, license requirement, etc.
Additionally, the score is also reflected in the Identity Threat Detection and Response dashboard, where it’s correlated with risky users, identity-related incidents, and other threat signals. This unified view supports proactive threat detection and informed action to strengthen your security posture.
Let’s dive into the crucial 3 recommendations that help you boost your identity secure score by 6 points.
3 Settings to Improve Microsoft Identity Secure Score
Here are the crucial 3 recommendations found under the identity category of Microsoft secure score.
- Designate more than one global admin.
- Use the least privileged administrative roles.
- Ensure user consent to apps accessing company data on their behalf is not allowed.
1. Designate More than One Global Admin in Microsoft 365
Why this recommendation? Consider a scenario where you are the sole global admin in your organization, and your account is compromised by attackers. If this happens, your ability to respond is severely limited because no one else has full access to the tenant. This situation highlights why cybersecurity frameworks like CISA, including Microsoft secure score, recommend having more than one global admin.
Having more than one super admin enables collective access to the Microsoft 365 environment for addressing potential breaches and implementing preventive measures. This setup creates checks and balances, allowing admins to monitor each other for unauthorized access or suspicious activity in M365.
Note: When you assign roles in Microsoft 365, ensure global admin roles are granted only to trusted users, such as co-admins or executives. Granting high-level privileged access to users who don’t need it can pose significant risks.
Benefits of assigning more than one global admin:
| Attacks Prevented | Account Breach, Elevation of Privilege. |
| Secure Score Points | 1 point |
How to Assign Global Admin Role in Office 365?
To assign a global admin role to a user in Microsoft 365, follow the steps below:
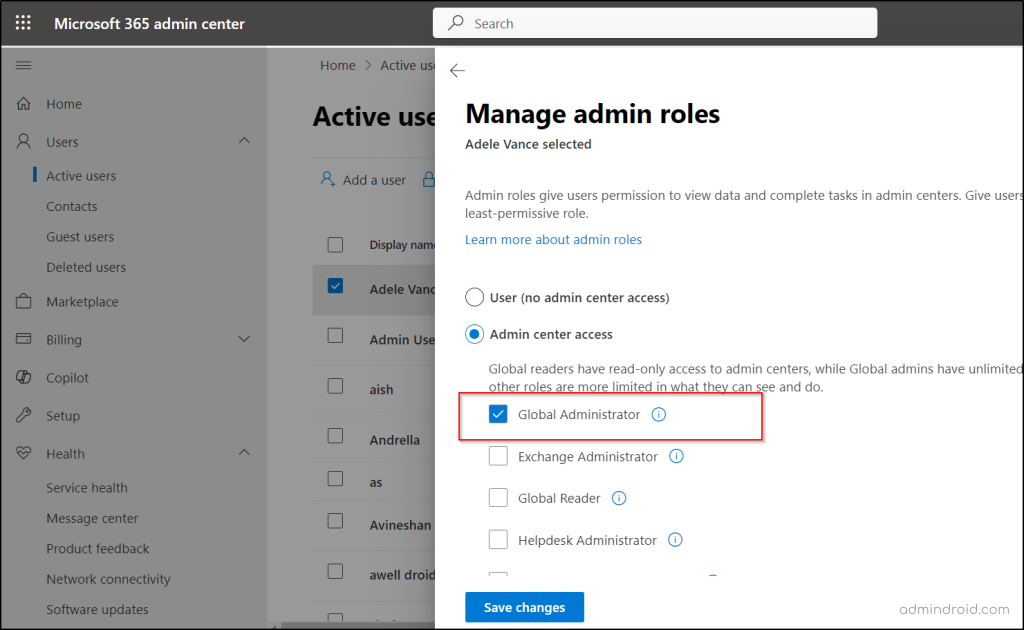
- Sign in to the Microsoft 365 admin center.
- Go to the Users > Active users.
- Select the user you want to assign to a global admin role.
- Click on the Manage roles link found under “Roles” option.
- Check the Admin center access radio button and choose the Global Administrator role for the user.
- Finally, proceed to save the changes.
2. Use the Least Privileged Admin Roles in Microsoft 365
Why this recommendation? “Too much of whatever is dangerous”, and the same applies to granting Microsoft 365 users’ permissions. Giving users more access than they need poses a security threat.
For instance, if you need a user to manage password processes, assigning them the global admin role—which grants excessive privileges—is not the best choice. Instead, Microsoft Secure Score recommends following the least privilege principle. In this case, you should assign the user the password administrator role, giving them just enough access to perform their tasks without unnecessary privileges. This minimizes potential security risks while ensuring the job gets done.
The upside of using least privileged access:
| Attacks Prevented | Account Breach, Elevation of Privilege, Malicious Insider. |
| Secure Score Points | 1 point |
View and Assign Least Privilege Administrator Roles in Entra ID
To implement Azure Role-based Access Control (RBAC), follow the steps below:
- Sign in to the Microsoft Entra admin center and navigate to Roles & Admins section > Roles & admins.
- Click on the Global Administrator role in the roles table to view the users assigned to this role.
- Review the tasks assigned to each user and determine which least privileged admin role is necessary for them to complete their responsibilities.
- Return to the Roles & admins page and assign each user to their respective least privileged role.
- After completing the assignments, go back to the Roles and administrators page and remove the users from the global admin role.
Note: Ensure that at least two Global Administrators are retained at all times to mitigate issues in case one account is locked out or compromised.
3. Do Not Allow Users to Grant Consent to Unreliable Applications
Why this recommendation? Microsoft allows both admins and users to grant consent to applications in Entra ID, but here’s where the risk comes in. By default, all users can approve apps to access your organization’s data, which opens the door to potential security threats. Malicious apps can exploit this by tricking users into granting access and looting organization’s data.
To safeguard against this, Microsoft Secure Score recommends limiting user consent to applications from verified publishers only. This simple step greatly reduces the chances of unauthorized apps gaining access to sensitive information.
Benefits of restricting user consents to apps:
| Attacks Prevented | Data exfiltration, Data spillage. |
| Secure Score Points | 4 points |
Manage User Consent to Applications within Microsoft 365
To restrict user consent to malicious apps, follow the steps below:
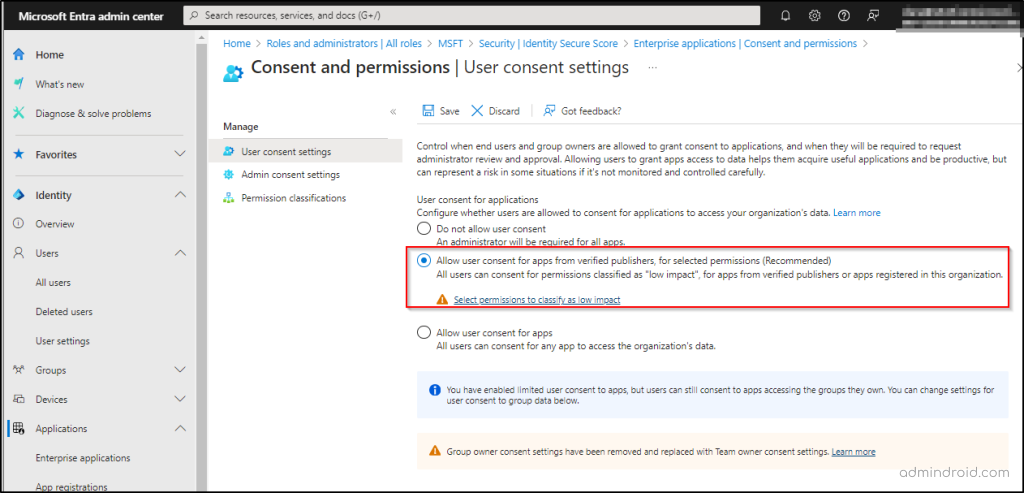
- Sign in to the Microsoft Entra admin center as a Privileged Role Administrator.
- Browse to Identity > Applications > Enterprise applications > Consent and permissions > User consent settings.
- Under User consent for applications, check the “Allow user consent for apps from verified publishers, for selected permissions (Recommended)” option.
- Click on the “Select permissions to classify as low impact” and add low impact permissions for the users. This will allow users to consent for permissions mentioned in low impact, for apps from verified publishers or apps registered in this organization. Optional: You can also enable the admin consent workflow to let users request approval for applications they can’t consent to.
- Select Save to save your settings.
I hope these three recommendations help improve Microsoft identity secure score Additionally, don’t forget to explore other identity-related security score suggestions, such as enabling MFA for all users, securing admin roles, removing unused apps, and implementing user risk policies and more, to reach a 100% identity secure score in Azure AD. Stay secure and happy reading!