Microsoft Entra ID is the core of identity and access management in Microsoft 365, providing secure access for users and applications. However, admins often encounter sign-in issues that can disrupt authentication, security, and compliance. From login failures to conditional access blocks, these problems can impact productivity and security if not addressed quickly.
To tackle these challenges, Microsoft’s built-in tools, like the Entra ID sign-in diagnostic tool, provide a great first step in troubleshooting. They help identify and fix common sign-in errors before manual Entra ID troubleshooting is needed.
Microsoft Entra Sign-in Diagnostic Tool: Your First Step for Troubleshooting
Microsoft Entra sign-in diagnostic tool is a built-in resource that helps identify and resolve common issues related to sign-ins. This tool provides insights into authentication failures, conditional access misconfigurations, and sync errors, allowing admins to diagnose issues quickly.
🔍 Where to Find the Entra ID diagnostic tool?
Go to Microsoft Entra admin center → Diagnose and solve problems
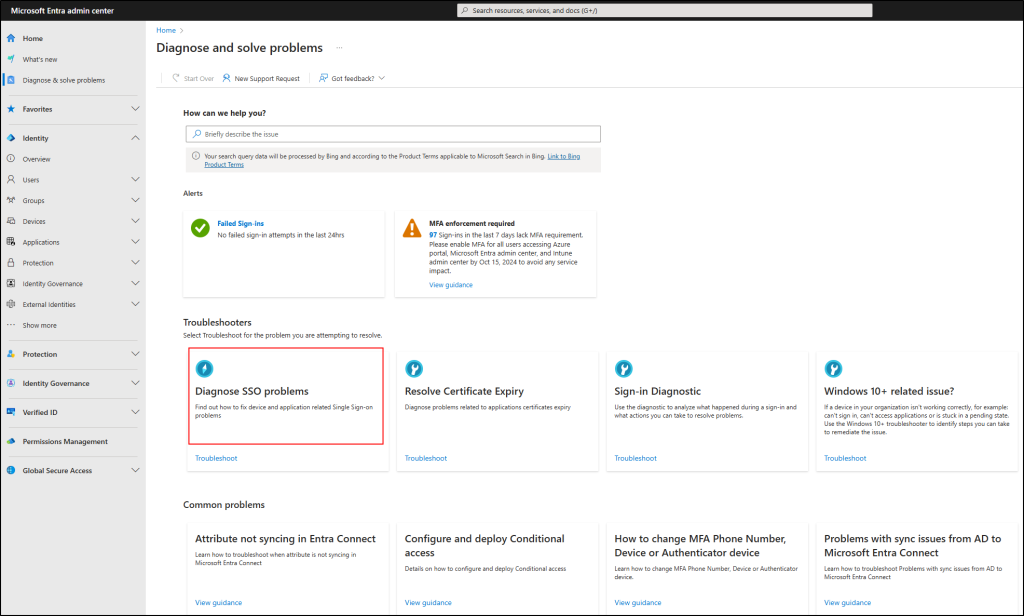
With detailed logs, admins can better understand authentication failures and sync errors. Plus, guided troubleshooting offers step-by-step fixes for Microsoft Entra authentication and authorization errors, ensuring smooth and secure authentication.
Common Microsoft Entra ID Issues
Most Microsoft Entra ID sign-in issues can be resolved directly from this tool. However, some issues require deeper troubleshooting. Below, we’ve covered specific Microsoft Entra ID issues, their causes, and solutions to help admins resolve them efficiently and keep their environment running smoothly.
- Microsoft Entra ID Sign-in Errors
- Password-Related Issues
- Entra ID Multifactor Authentication Issues
- Conditional Access Blocking Users
- Brute Force Attacks
- User Lockouts in Microsoft Entra ID
- Unable to Join Devices to Microsoft Entra ID
- Entra ID Sync Issues
- Service Principal Authentication Issues
- Consent Issues in Microsoft Entra ID
- Microsoft Entra Connect Connectivity Issues
- Licensing Errors in Entra ID
1. Microsoft Entra ID Sign-in Errors
One of the most common issues users face when signing into Entra ID is receiving error messages like “We couldn’t sign you in. Please try again.” These errors can occur due to various reasons, including expired sessions, MFA failures, or internal service issues.
✅ Troubleshoot and Solution: Microsoft Entra sign-in logs
Microsoft Entra sign-in logs provide valuable insights into authentication patterns and help diagnose access issues. You can use these logs to answer key questions like:
- What is the user’s sign-in pattern?
- How many users have signed in over a specific period?
- What is the status of recent sign-ins?
To access Microsoft Entra sign-in logs, go to:
Microsoft Entra admin center → Identity → Monitoring & Health → Sign-in Logs
Start by gathering sign-in details from Azure AD sign-in logs, reviewing error codes, and identifying the root cause to resolve authentication issues efficiently. Some key sign-in error codes to look for include:
- 50058 – User is authenticated but not signed in.
- 90025 – Microsoft Entra service reached its retry limit for signing in the user.
- 500121 – User didn’t complete the MFA prompt.
- 70046 – Session expired or reauthentication check failed.
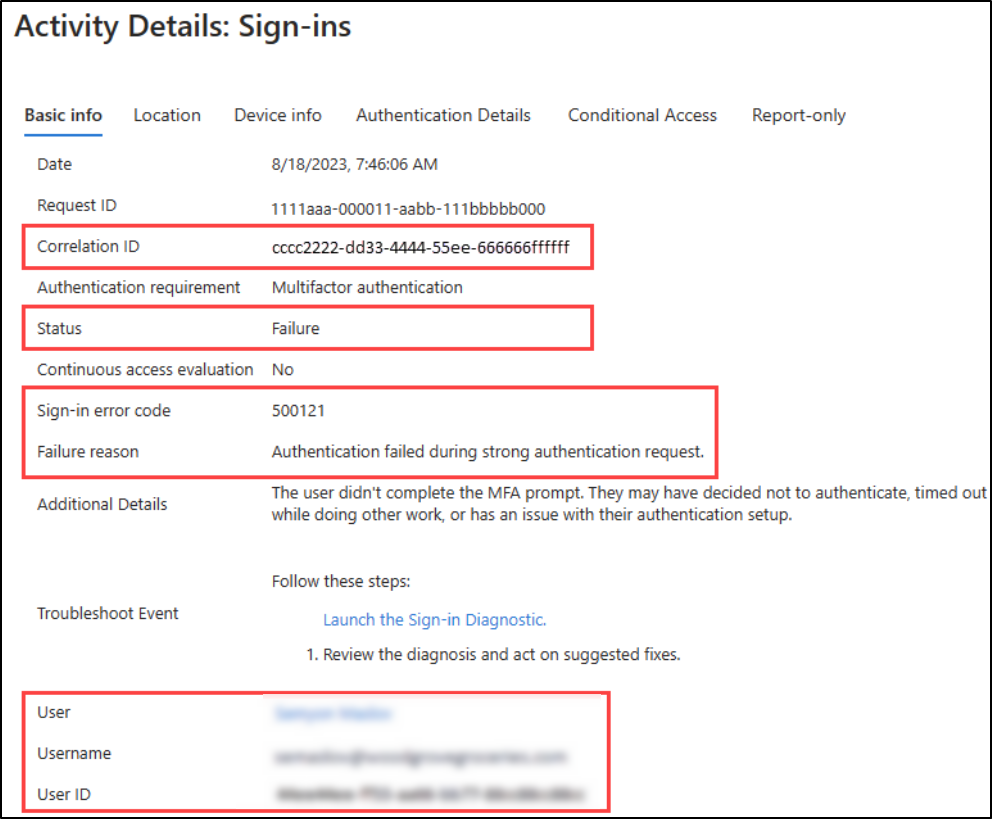
In addition, you can also use Microsoft Entra Workbooks to visualize sign-in trends, monitor authentication failures, and gain deeper insights into user access patterns.
Therefore, to resolve Microsoft Entra ID sign-in errors, analyze sign-in logs, review error codes, and use Workbooks to monitor trends, ensuring a seamless authentication experience.
2. Password-Related Issues in Entra ID
Password-related issues can disrupt Microsoft 365 sign-ins, often due to expired passwords or forgotten credentials. Addressing these proactively ensures seamless authentication while maintaining security.
Expired Passwords
Passwords expire based on the organization’s password policy, leading to login failures. Users may see errors like “Your password has expired” when attempting to sign in.
✅ Troubleshoot and Solution: Enable password expiration notifications using Power Automate
Setting up password expiry reminders can help users reset their passwords before expiration, preventing access issues.
This ensures users receive timely reminders to update their passwords, reducing login issues and support requests.
Forgotten Passwords
Forgetting passwords is a common issue in any organization, often leading to frustration and unnecessary IT support tickets. Without a self-service recovery option, users must rely on IT admins for password resets, consuming valuable time and resources.
✅ Troubleshoot and Solution: Encourage users to register for SSPR
Enable Self-Service Password Reset (SSPR) in Microsoft Entra to allow users to reset passwords independently.
However, traditional passwords are vulnerable to phishing and brute-force attacks.
✅ Passwordless Authentication – Moving to passwordless authentication enhances security and streamline logins by eliminating passwords.
Both passwordless authentication and Self-Service Password Reset (SSPR) serve different purposes and complement each other in securing user access. The best approach depends on your organization’s security goals and user needs.
- Go passwordless whenever possible – This is the most secure and user-friendly option.
- Keep SSPR as a backup – If passwordless isn’t fully adopted, SSPR ensures users can still recover access when needed.
Therefore, enable password expiration reminders, SSPR, and passwordless authentication to reduce login issues and minimize IT support dependency.
3. Entra ID Multifactor Authentication Issues
Multifactor authentication (MFA) issues can also prevent users from signing in to Microsoft Entra ID, often due to misconfigured policies, unregistered authentication methods, or problems with the authentication app.
✅ Common Issues and Fixes
- MFA Not Configured: Ensure the user has registered their phone number or email for MFA verification.
- No Verification Code Received: Check if the number/email is correct and ensure no spam filters or carrier issues are blocking the message.
- Authenticator App Issues: If the Microsoft Authenticator app isn’t working, try resetting MFA for the user and re-registering the app.
- Blocked by Security Settings: Review security defaults and Conditional Access policies to ensure they aren’t restricting MFA prompts.
Therefore, verify MFA settings, re-register authentication methods if needed, and review security policies to resolve sign-in issues without compromising security.
4. Conditional Access Blocking Users
If you see the error “Access has been blocked by Conditional Access policies,” it means a Conditional Access policy is preventing the user from signing in based on conditions like device type, location, or risk level.
✅ Troubleshoot and Solution: Prevent Issues by Testing with the Conditional Access “What If” Tool
Before applying Conditional Access policies, use the “What If” tool in Microsoft Entra ID to test sign-in scenarios and ensure users aren’t unintentionally blocked. This helps identify potential access issues before enforcement. To use this tool,
- Open Microsoft Entra admin center.
- Go to Protection → Conditional Access -> Policies.
- Click What If.
- Simulate the user’s sign-in attempt by entering their details (such as username, device, and location) to see which Conditional Access policies would be enforced.
- Adjust policies if needed to allow access.
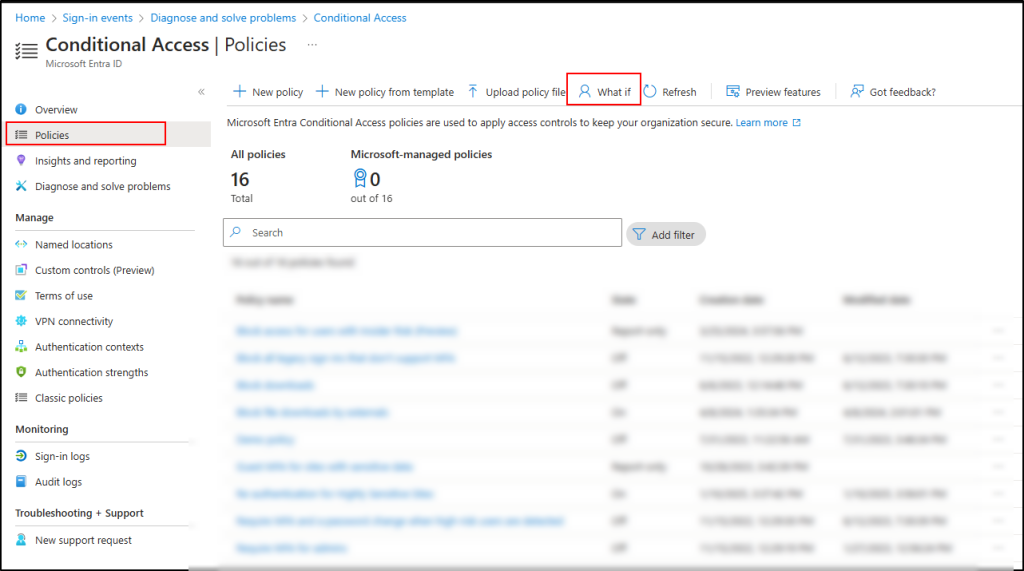
By identifying and modifying the blocking CA policy, users can regain access without compromising security. Additionally, monitoring Conditional Access policy changes and ensuring modern authentication is enabled helps to maintain secure access and prevent future sign-in issues.
Therefore, use the Conditional Access “What If” tool to test policies before enforcement, adjust settings as needed, and monitor changes to prevent unintended sign-in blocks.
5. Brute Force Attacks
Brute force attacks occur when attackers repeatedly try different password combinations to gain unauthorized access to Microsoft Entra accounts. These attempts often come from unknown locations, unfamiliar devices, or automated scripts trying to exploit weak credentials. To prevent brute force attacks, a common solution is Smart Lockout in Microsoft 365. However, attackers can still attempt large-scale credential stuffing or use rotating IPs to bypass basic protections.
✅ Troubleshoot and Solution: Enable Microsoft Entra Identity Protection
To effectively detect and mitigate brute force attacks, enable Microsoft Entra Identity Protection by following these steps:
- Go to the Microsoft Entra admin center.
- Navigate to Identity Protection under “Protection”.
- Configure “Sign-in risk” policy and “User risk” policy.
- Enable the policies to enforce security measures.
With Microsoft Entra Identity Protection, admins can proactively monitor and respond to suspicious sign-ins, reducing the risk of brute force attacks and unauthorized access. Visit the Identity Protection dashboard in the Microsoft Entra admin center for insights into your organization’s risk posture.
6. User Lockouts in Microsoft Entra ID
Frequent account lockouts can result from brute force attacks or excessive failed sign-ins in Entra ID.
Troubleshoot and Solution:
✅ Check Smart Lockout Settings – Smart lockout helps prevent brute-force attacks by automatically locking out accounts after multiple failed login attempts. In Microsoft Entra, admins can review and adjust lockout thresholds to balance security and usability.
✅ Use Conditional Access with Risk-Based Policies – Conditional Access policies analyze sign-in behavior to detect risky login attempts. With Risk-Based Conditional Access, organizations can enforce MFA for suspicious sign-ins.
✅ Remove Old Passwords from Devices – Stored passwords on devices can cause repeated authentication failures after a password change. Ensure users update or remove old saved passwords from browsers, email clients, and mobile devices to prevent account lockouts and authentication issues.
Therefore, to prevent frequent account lockouts, review and adjust Smart Lockout settings, enforce Risk-Based Conditional Access for suspicious sign-ins, and ensure users update or remove outdated saved passwords from their devices.
7. Unable to Join Devices to Microsoft Entra ID
When trying to join a device to Microsoft Entra ID, a “Something went wrong” error may appear. This issue often occurs due to misconfigured Mobile Device Management (MDM) settings. It is more common in organizations that previously had Intune licensing but later switched to a Business Standard plan. In such cases, you may also encounter errors like:
- “Something went wrong” during Entra (Azure) domain join
- Unable to access Workplace or School domain
- Device join to Microsoft Entra ID failed
✅ Troubleshoot and Solution: Disable Intune MDM Enrollment
If Intune was previously enabled but is no longer in use, it may still be blocking device enrollment. To disable Intune MDM enrollment, go to the MDM Configuration page.
Note: Before resetting MDM scopes, users should verify if any policies are still being applied via Intune that might impact device enrollment.
Reset MDM and WIP Scopes
- If you see the message:
“The Intune app is enabled. Click here to reset the MDM and WIP scopes for Intune to None.” - Click the link to disable it.
- This action does not delete the Intune app but resets MDM settings.
- After resetting MDM scopes, attempt to join the Windows device to Entra ID.
- The issue should now be resolved.
By ensuring Intune is properly disabled when not in use, you can prevent unnecessary blocks and successfully enroll devices into Microsoft Entra ID. If enrollment issues persist, advise users to check the device’s current management state via Settings > Accounts > Access work or school in Windows.
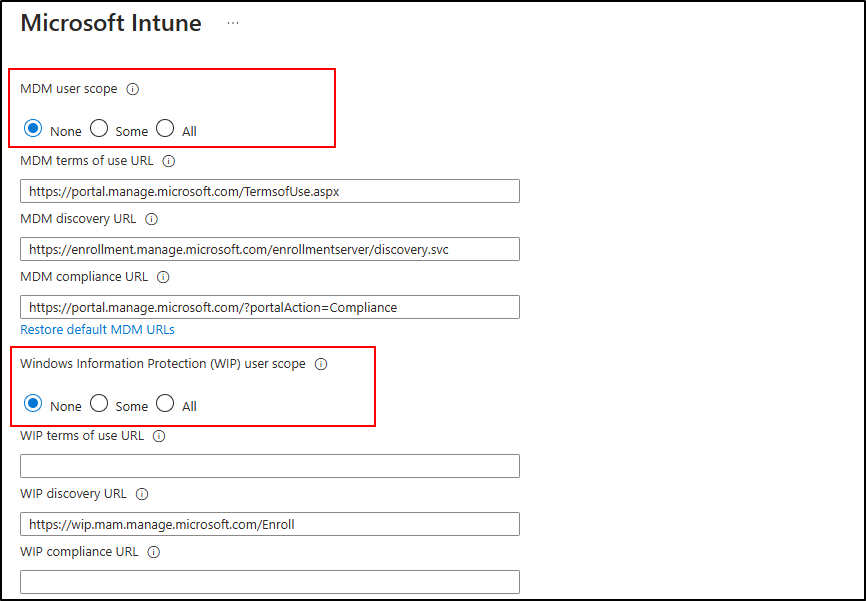
Therefore, to fix Microsoft Entra ID device join failures, disable unused Intune MDM settings and reset MDM scopes if needed.
8. Entra ID Sync Issues
Entra ID sync issues can disrupt user management and authentication, causing delays and login problems. If your directory isn’t syncing properly, the issue might be due to various reasons. Here’s how to troubleshoot and fix these common problems.
- Problem: The Azure AD Connect sync service has stopped, preventing directory synchronization.
Troubleshoot & Solution: Restart the Azure AD Connect service to restore sync functionality.
- Problem: Users have duplicate User Principal Names (UPNs), leading to sync conflicts.
Troubleshoot & Solution: Check the AAD Connect Health logs to detect and resolve duplicate UPNs.
- Problem: Misconfigured Organizational Unit (OU) filtering is blocking certain users from syncing.
Troubleshoot & Solution: Verify the OU filtering settings in AAD Connect to ensure the correct users and groups sync properly.
Therefore, to resolve Entra ID sync issues, restart the Azure AD Connect service, check AAD Connect Health logs for duplicate UPNs, and verify OU filtering settings to ensure proper directory synchronization.
9. Service Principal Authentication Issues
Service principals authenticate using client secrets or certificates. When these expire, applications fail to authenticate, disrupting automated tasks and integrations. When a client secret or certificate expires, the service principal loses access, causing authentication failures. Without proactive management, apps may stop functioning unexpectedly.
✅ Troubleshoot and Solution: Retrieve expiring client secrets and certificates in Entra ID using PowerShell
Regularly checking for expiring secrets and certificates using PowerShell helps prevent authentication failures and ensures continuous access for applications. Proactively identifying and updating these credentials minimizes outages to automated workflows and integrations, keeping critical services running smoothly.
It’s also essential to verify API permissions and exclude service principals when necessary to ensure seamless authentication.
Handy Tip: Client secrets are easy to create but just as easy to forget. To reduce risk, consider blocking the creation of client secrets for apps that don’t require them, particularly for high-privilege or unattended applications.
10. Consent Issues in Microsoft Entra ID
Application consent issues in Microsoft Entra ID can prevent users from accessing third-party or custom apps, leading to workflow disruptions. This often happens when an app requires user consent before signing-in.
Common causes include:
- Missing User.Read permission preventing basic profile access.
- User consent disabled at the tenant level, restricting users from granting app permissions.
- User assignment enabled for the application, requiring explicit user assignment before access.
- Scopes or permissions requiring admin consent, blocking access until an admin approves them.
✅ Troubleshoot and Solution: Manage user consent to applications in Microsoft 365.
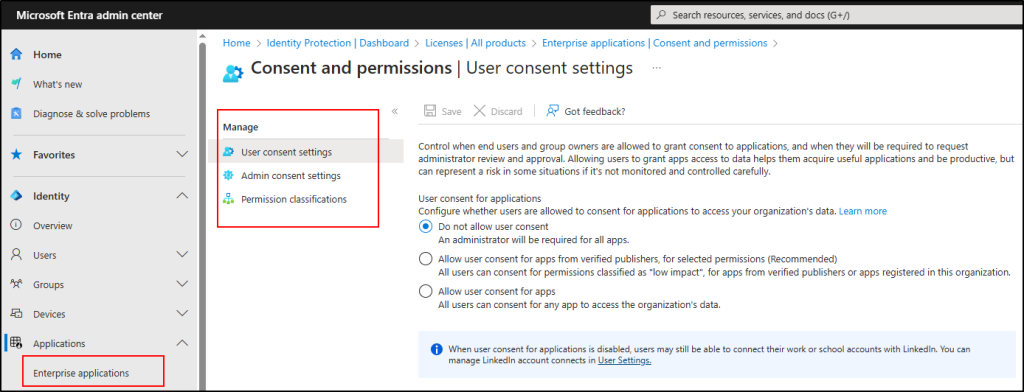
Review and manage user consent settings to ensure users have appropriate access to third party or custom apps.
To maintain control over application access and ensure compliance, it’s crucial to regularly review app permission consents in Microsoft 365. Regularly auditing app permissions ensures only necessary access is granted, reducing security risks and enforcing compliance.
11. Microsoft Entra Connect Connectivity Issues
Network issues can disrupt authentication and synchronization between Microsoft Entra Connect and Entra ID. To resolve connectivity problems:
✅ Test Connectivity with PowerShell – Run:
Invoke-WebRequest –Uri https://adminwebservice.microsoftonline.com/ProvisioningService.svc
A failed response may indicate proxy or DNS issues.
✅ Review Network Logs – Analyze Entra Connect Health logs for unexpected failures in Entra Connect communication.
For more details about the troubleshooting of Microsoft Entra Connect connectivity issues, refer to this documentation.
12. Licensing Errors in Entra ID
Licensing issues in Microsoft Entra ID can prevent users from accessing essential Microsoft 365 services. Understanding license availability and dependencies is key to avoiding assignment failures.
✅ Troubleshoot and Solution: Check whether Microsoft Entra ID P1/P2 is available
- Navigate to the Microsoft Entra admin center → Identity -> Billing -> Licenses → All Products
- Ensure users have the necessary Microsoft Entra ID P1 or P2 license, as basic Entra ID features are included in Microsoft 365 E3, E5, and other enterprise plans.
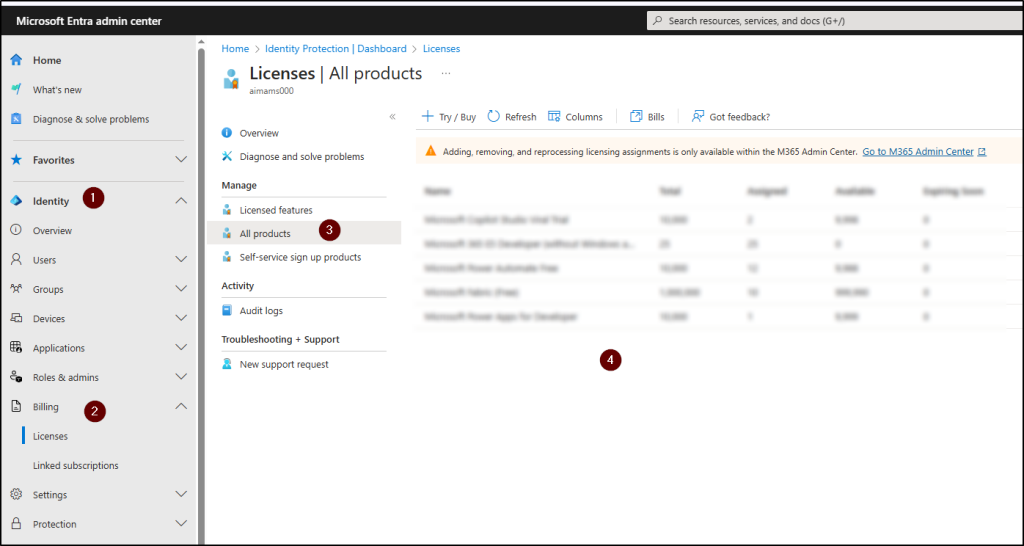
Checking license availability ensures that admins can proactively manage allocations, prevent assignment failures, and avoid service delays. If licenses are insufficient, they can either free up unused ones or purchase additional licenses before issues arise.
Wrap-Up
These common Entra ID issues can impact user access and security. By reviewing sign-in logs in the right places, admins can quickly diagnose and resolve authentication problems. Implementing Entra ID security best practices further helps strengthen access controls and protection. Thanks for reading! Feel free to leave a comment below for any queries.






