When securing user sign-ins across Microsoft 365, admins are often presented with two similar-sounding options: SMS sign-in and SMS-based multifactor authentication (MFA). At first glance, both SMS sign-in and SMS-based MFA appear similar — they use text messages to authenticate users. But in reality, they serve entirely different purposes, and choosing the wrong one could weaken your organization’s security.
In this blog, we’ll break down the difference between SMS sign-in and SMS MFA, discuss their pros and cons, and guide you through identifying users relying on SMS authentication.
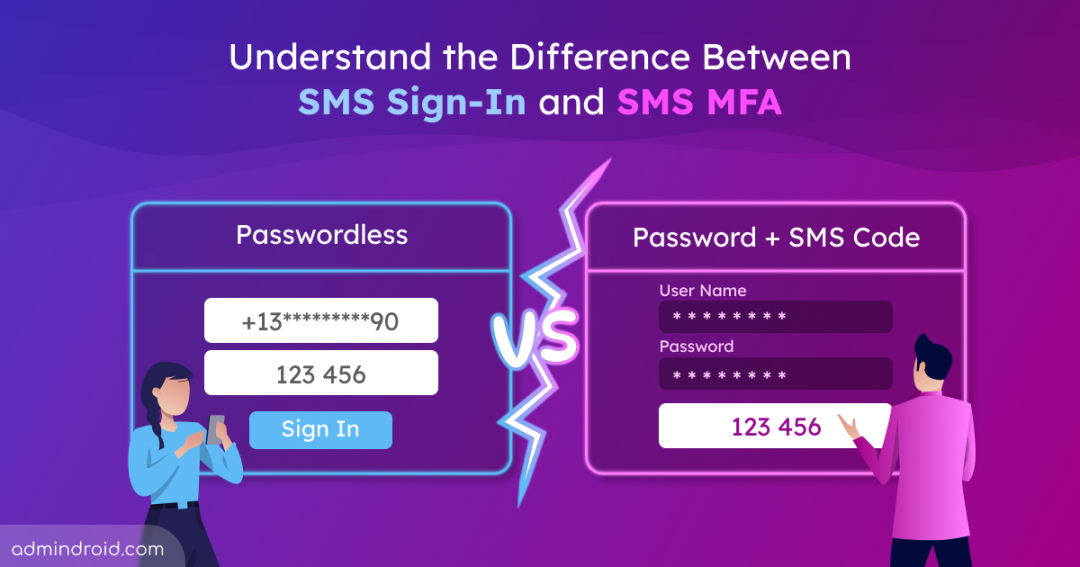
What Is SMS Sign-In?
SMS sign-in is a passwordless authentication method where users can log in using just a one-time code sent to their mobile number — no password required. This method is especially useful in frontline scenarios where users don’t typically remember or manage passwords, such as retail or field staff logging in from shared devices.
What Is SMS MFA?
SMS-based MFA, on the other hand, requires a password. It only works after the user enters their password. As a second factor, a code is sent to their phone to confirm their identity.
To help you clearly see how SMS sign-in and SMS-based MFA differ, here’s a quick side-by-side comparison:
| Aspect | SMS Sign-In | SMS-based MFA |
| Password required? | No | Yes |
| Authentication type | Passwordless – uses only a one-time SMS code. | Requires password + one-time SMS code. |
| When it’s used | During sign-in as the only authentication factor. | Used after entering a password as the second factor. |
| Primary use case | Frontline workers, shared devices, users who struggle with passwords. | General users who need an extra layer of security after a password. |
| Pros | 1. Reduces helpdesk load by eliminating password resets. 2. Simple onboarding for users with limited tech access. 3. Quick access experience, especially useful in low-security environments. | 1. Provides a second layer of protection, reducing the risk of compromised or reused passwords. 2. Helps block unauthorized access attempts even if credentials are leaked. 3. Widely supported across platforms, making it easy to implement minimum security standards at scale. |
| Cons | 1. Single-factor authentication is less secure than MFA. 2. Vulnerable to SIM swap attacks, SMS interception, and phishing. 3. Not supported in multi-tenant organizations (MTOs). | 1. Vulnerable to phishing and SIM swap attacks. 2. Can be exploited in social engineering/MFA fatigue attacks. 3. Lacks phishing resistance compared to app or hardware-based methods. |
While both methods have their place, it’s crucial to understand the security trade-offs—especially with SMS-based MFA, which remains widely used but vulnerable.
Let’s take a closer look at the real-world risks that come with using SMS-based MFA.
Real-World Risks with SMS MFA
Even though SMS-based MFA is simple to set up and familiar to users, it comes with significant vulnerabilities that attackers actively exploit. Since it still depends on one-time codes sent over text, it is especially prone to identity-based attacks and message interception.
One of the most common issues is users receiving unexpected MFA codes. This confusion opens the door to phishing or impersonation attacks. Similar to MFA fatigue attacks using app push notifications, attackers often try to trick users into sharing these codes by posing as IT support.
Why Do Users Receive Unexpected MFA Codes?
Unexpected MFA codes are one-time passcodes (OTPs) sent to users’ phones even though they didn’t attempt to sign in. These codes arrive without any user action and are usually a sign of suspicious or unauthorized activity. They may be caused by the following factors.
- Accidental Triggers: Sometimes, users may forget they tried to log in or accidentally trigger an MFA prompt on another device.
- Malicious Attempts: Most often, unexpected MFA codes are a result of attackers trying to access user accounts. Attackers may:
- Try to log in with a guessed or leaked username.
- Attempt a password reset using the user’s email or username.
- Use automated tools to trigger MFA prompts for multiple accounts.
- Try to register their own MFA methods to hijack the account.
Why Are Unexpected MFA Codes a Concern?
Let’s say a user gets a sudden MFA code on their phone. Moments later, someone calls pretending to be from IT, saying, “We need that code to fix your account.” The user, thinking it’s a legitimate request, shares it.
That’s exactly how attackers bypass MFA. They trigger a code, pose as support, and trick users into giving it up. Some even send multiple codes to confuse or pressure the user into responding.
Once they have the code, they’re in. They can access data, send emails, or move deeper into the system. All of this starts with a single code.
What should the admins do?
- Educate users: Make it clear that MFA codes should never be shared with anyone, including IT staff.
- Monitor for repeated or failed MFA attempts: This can indicate ongoing attacks.
- Encourage stronger MFA methods: App-based or hardware-based MFA are less vulnerable to these attacks, and Microsoft Entra lets you change default MFA method based on user roles and risk levels.
Whether you’re using SMS-based MFA or SMS sign-in, visibility is key. While MFA adds a second layer of defense, SMS sign-in replaces passwords entirely, which makes it even more critical to know who has access.
Here’s how you can identify users with SMS sign-in enabled in Microsoft Entra.
How to Find Users Using SMS Sign-In in Microsoft Entra
Knowing which users have SMS sign-in enabled is essential for maintaining your organization’s security posture. To identify users with SMS sign-in enabled in Microsoft Entra, follow any of the below methods.
- Find SMS Sign-In Users in the Microsoft Entra Admin Center
- Export SMS Sign-In Users from Microsoft Entra Using PowerShell
Find SMS Sign-In Users in the Microsoft Entra Admin Center
To find users enabled for SMS sign-in in the Microsoft Entra admin center, follow the steps below.
- Sign in to the Microsoft Entra admin center
- Navigate to Users > All Users. Select a user from the list you want to review.
- In the left menu of the user profile, click on Authentication methods and check for Phone number.
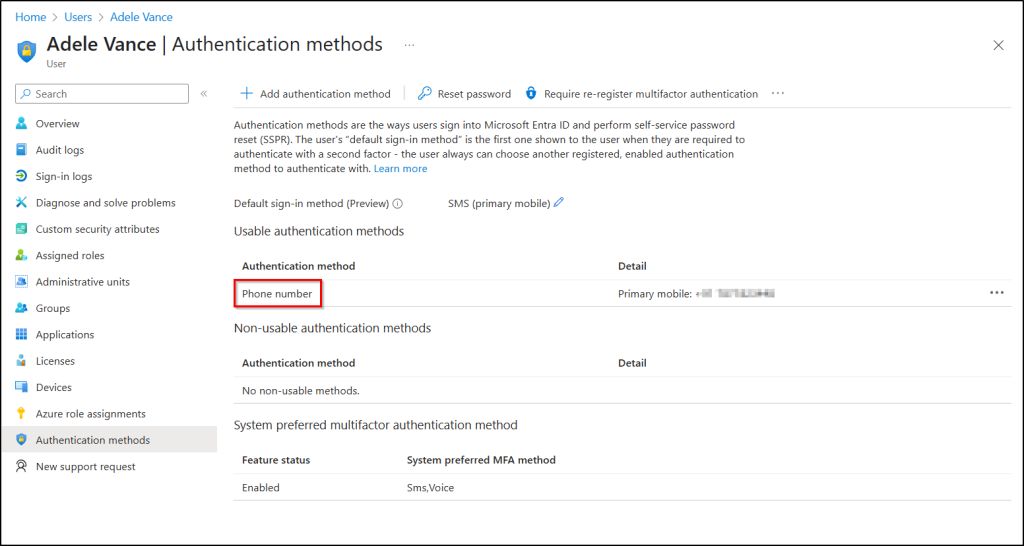
This means that SMS sign-in is enabled for that user. If there is no such entry, the user does not have SMS sign-in configured.
Export SMS Sign-In Users in Microsoft Entra Using PowerShell
For larger environments, you can use PowerShell to automate the process of identifying SMS sign-in users in Microsoft Entra. This method allows you to efficiently export a complete list without manually checking each user in the admin center.
Run the below snippet in PowerShell as Administrator.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
$Users = Get-MgUser -All $SmsUsers = @() foreach ($User in $Users) { $PhoneMethods = Get-MgUserAuthenticationPhoneMethod -UserId $User.Id -ErrorAction SilentlyContinue foreach ($Method in $PhoneMethods) { if ($Method.PhoneType -eq "mobile" -and $Method.SmsSignInState -in @("ready", "enabled")) { $SmsUsers += [PSCustomObject]@{ DisplayName = $User.DisplayName UserPrincipalName = $User.UserPrincipalName PhoneNumber = $Method.PhoneNumber SmsSignInState = $Method.SmsSignInState } } } } $SmsUsers | Export-Csv -Path ".\SmsSignInReadyOrEnabledUsers.csv" -NoTypeInformation |
Sample Output
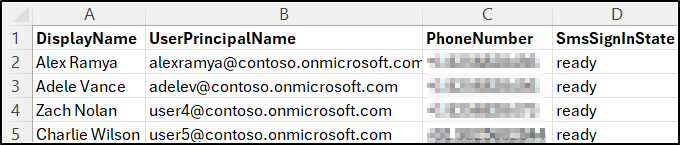
This script will list users who have SMS sign-in registered for authentication.
To find only those users with SMS sign-in currently enabled (and not just configured or pending), update the script to check for SmsSignInState -eq “enabled”
|
1 |
if ($Method.PhoneType -eq "mobile" -and $Method.SmsSignInState -eq "enabled") |
Therefore, understanding the difference between SMS sign-in and SMS MFA in Microsoft 365 helps you make informed decisions about your organization’s security, especially with the rise of phishing, SIM swap attacks, and MFA fatigue.
Identifying users with SMS sign-in is just the first step. To strengthen your authentication setup, focus on enforcing MFA for all users and adopting phishing-resistant methods.
Modern authentication method policies in Microsoft Entra help you control which sign-in options are allowed and guide users toward secure alternatives like Microsoft Authenticator or QR code-based sign-ins.
We hope this blog helped you understand the differences between SMS sign-in and SMS MFA and how to manage them effectively. Feel free to share your thoughts or questions in the comments below!