In today’s digital age, maintaining the security of an organization has become more crucial than ever before. With a significant increase in the number of cyber threats, it has become essential to monitor and analyze sign-in data to minimize the risk of security breaches. That’s where Azure Active Directory’s Usage & insights reports come in. These comprehensive reports offer an application-centric view of the organization’s sign-in data, enabling admins to take proactive measures to enhance application security.
Among those reports, one of the most significant reports is the Azure AD application activity – currently in preview. This report allows admins to generate sign-in activities for various applications in the organization. Now, let’s take a closer look at how this report can benefit organizations and help them enhance their overall security posture! 💻
Who Can Access ‘Usage & Insights’ Reports in Azure AD?
Find the license requirements to access the Azure Active Directory Usage and insights reports below.
- An Azure AD tenant
- An Azure AD premium (P1/P2) license
Next, make sure you have been assigned one of the following roles: Global Administrator, Security Administrator, Security Reader, or Reports Reader. Once you have these prerequisites in place, simply sign into the Azure portal and navigate to,
Azure Active Directory –> Usage & insights –> Azure AD Application Activity (Preview)
Usage and Insights of Azure AD Application Activity Report
Application activity report in Azure AD provides valuable insights into the sign-in attempts of services and applications in the organization. It allows admins to find answers to questions like,
- What are the top used applications in my organization?
- Which applications have the most successful sign-ins?
- What applications have the most failed sign-ins?
- What is the top sign-in error for an application?
It is also important to note that the sign-in activity of a deleted application may still appear if it occurred during the selected date range. Additionally, if a user attempts to sign into an application without a service principal, this activity may also appear in the report. In these cases, it is necessary to review the sign-in logs for further investigation.
What Details Can Be Obtained from an Application Activity Report in Azure AD?
Find the list of details that admins can obtain from an Azure AD application activity report below.
- Successful sign-ins count for each application.
- Failed sign-ins counts of each application.
- Success rate of each application.
- Sign-in activity graph for each application.
- Reports for the Application sign-in data for the last 7 days to 30 days.
Sort the columns in descending order to find which application has the most successful sign-ins, failed sign-ins, and success rates. If you specifically want to look over an application, you can utilize the ‘Search’ box.
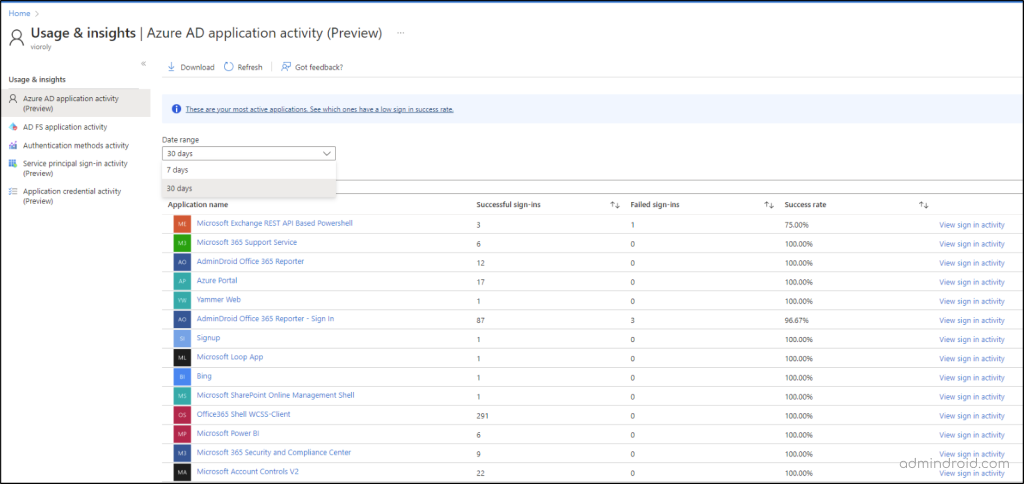
View Sign-in Activity in the Azure AD Application Activity Report
Sign-in activity graphs provide admins with a visual representation of the spike and fall in sign-in attempts over the last 30 days, 7 days, or 1 day. This information can be used to understand the usage patterns and trends of applications in the organization. 📈
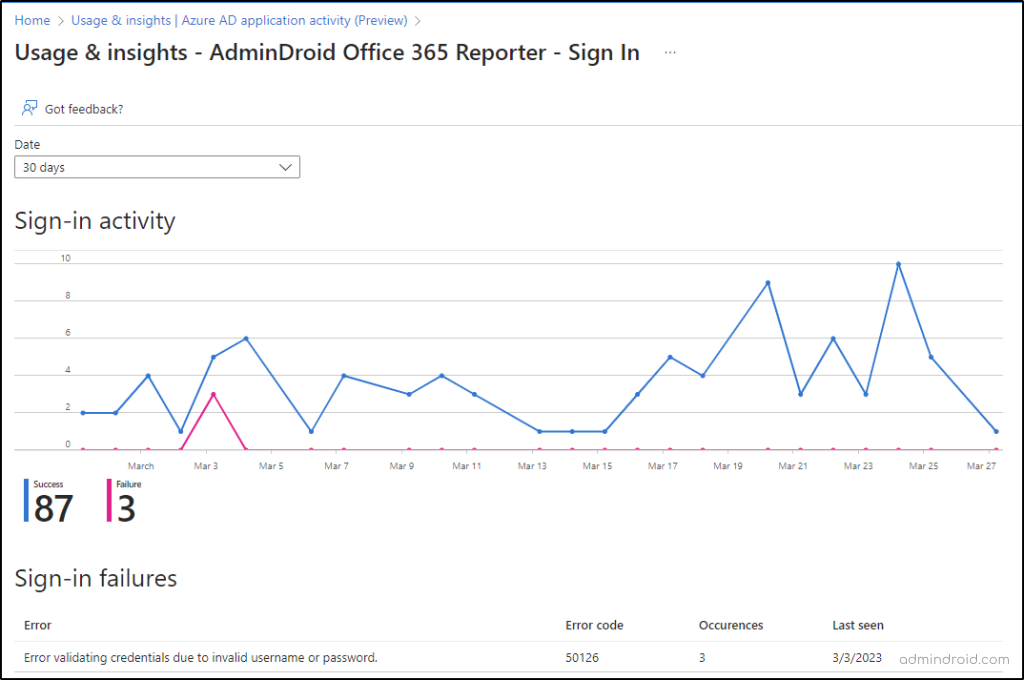
In the above graph, the blue and pink lines represent successful sign-ins and failed sign-ins, respectively. Further, admins can also find the reason for sign-in failure down to the sign-in activity graph that includes details such as error, error code, sign-in failure occurrence count, and last seen.
Remember when I mentioned that the sign-in attempts to an application could show up in the activity report even if there was no service principal involved? You may wonder what a service principal really means!
What is a Service Principal?
A service principal is a special type of account that represents an application or service rather than a user. When a service principal needs to access resources, it uses its own credential, such as a certificate or app secret, to authenticate and gain access. Think of it as a secret key that only the application knows and uses to unlock the resources it needs.
What is a Service Principal Sign-in?
Service principal sign-ins are unique in the way that they don’t involve a user at all. Instead, they’re sign-ins by non-user accounts like apps or service principals, which use their own credentials to authenticate and access resources.
To monitor service principal sign-ins, Microsoft introduced a new preview report under ‘Azure AD Usage & insights’ named Service principal sign-in activity to make admin’s work easier. In this report, you can find details of the application name, last sign-in date, application ID, and other details.
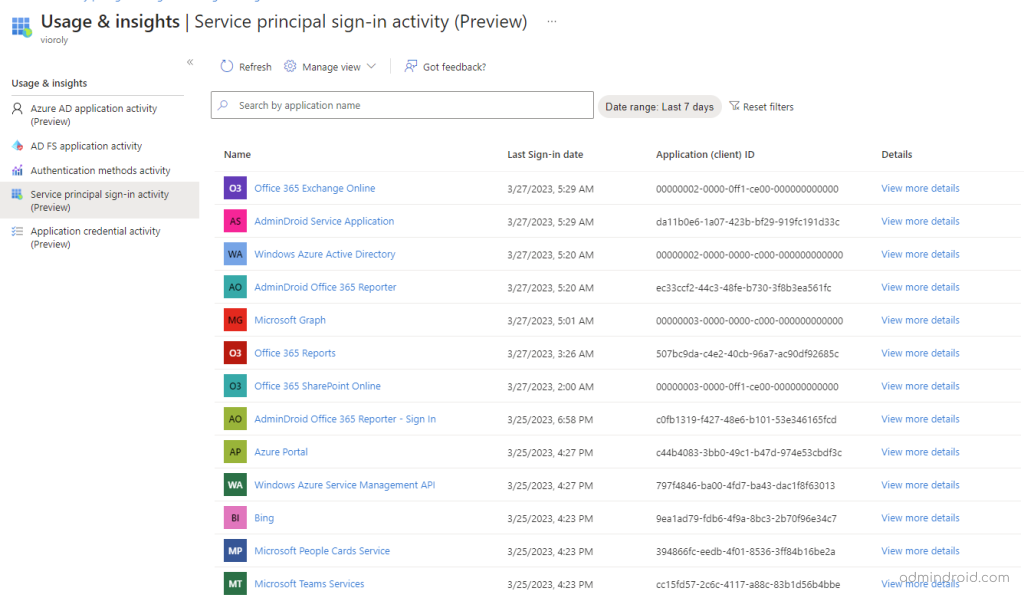
By clicking on ‘View more details’, admins can gain information on the application’s client ID and object ID.
In case of any issues with the application’s authentication, the client ID and object ID can be used to trace the issue by reviewing logs and audit trails in Azure AD. This information can help you identify the root cause of the issue and take corrective actions.
Elevate Your Azure AD Application Audit with AdminDroid
In today’s workplace, Microsoft 365 third-party applications have become essential tools for employees to perform their job responsibilities. Consequently, it has become crucial for administrators to keep track of application activity within their organization.
AdminDroid offers a solution by providing a comprehensive categorization of third-party and custom applications, going beyond mere sign-in audit logs. By providing unparalleled visibility, AdminDroid empowers administrators to stay informed about application activities, ensuring optimal management of your organization’s resources.
AdminDroid’s Application Audit Reports
Find the AdminDroid’s reports on application audit below.
- Added Applications – Verify the application objects created.
- Updated Applications – Review the updated application objects.
- Deleted Applications – Audit the deleted application objects.
- Consent to Applications – Examine the consents given to applications.
- OAuth2 Permission Grant – Check if the OAuth2 permission grants are given.
- App Role Assignments – Evaluate the app role assignments given to users or service principals.
- Service Principal Changes – Audit the service principal changes.
- Credential Changes – Track the credentials changes performed in service principals.
- Delegation Changes – Monitor authentication changes on the applications.
- All App Operations – Audit operations performed on application objects.
- Organization Sign-in Count based on Application – Gives a summary of the sign-in count for an application.
- User’s Sign-ins Summary by Application – Gives a summary of the user sign-ins count in an application.
- User’s Last Logon Summary by Application – Lists the recently signed-in users by an application.
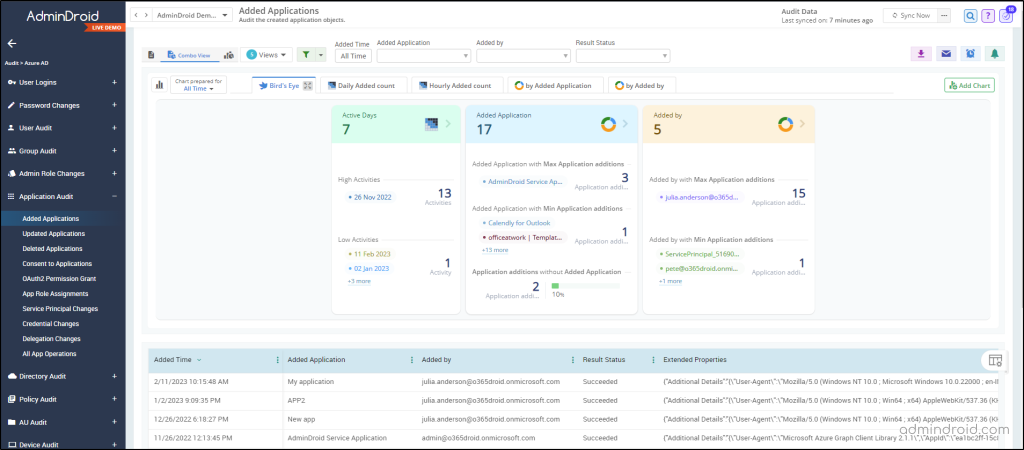
AdminDroid goes beyond Azure AD reporting & auditing! It also offers 1500 pre-built reports for various Office 365 services such as Azure AD, Security, Exchange Online, SharePoint Online, Microsoft Teams, and so on.
- These reports provide comprehensive insights and auditing information, allowing you to gain a deeper understanding of your organization’s performance.
- With AdminDroid’s AI-powered graphical analysis, you can easily visualize complex data and extract valuable insights in a visually appealing manner.
- Whether you’re looking to monitor user activity, track service usage, or ensure compliance with regulations, these reports offer the in-depth information you need to make informed decisions.
Download the Microsoft 365 Active Directory reporting tool today and unlock the full potential of your Microsoft 365 environment!
There you go, that’s all there is to know about Azure AD application activity report, which is now in public preview. The blog will be updated once the feature becomes generally available. We’ll keep you posted!
If you need any assistance, feel free to comment.






