Confident your Microsoft 365 environment is secure? You might be overlooking some risks! 🚩Even the most sophisticated security systems can have their blind spots. While Microsoft 365 offers powerful tools for productivity, vulnerabilities often arise from misconfigurations, human error, or inadequate security practices rather than flaws within the platform itself. From clever phishing attacks to compromised credentials, hackers have many tools at their disposal. As admins, we go the extra mile to protect our data, but sometimes threats can exploit weaknesses before we even realize they’re there.
To ensure your organization remains secure, it’s crucial to understand and address some potential M365 vulnerabilities. We’ve compiled a list of the top vulnerabilities in Microsoft 365 and their corresponding solutions. By staying informed and proactive, you can safeguard your organization from potential threats in M365 security and prevent data loss before it becomes a significant issue.
Here are some common security issues related to using Microsoft 365:
- Office 365 Credential Phishing
- Over-provisioned Admin Access
- Bypassing Multi-Factor Authentication (MFA)
- Weak Conditional Access Policies
- Misconfigured Permissions in SharePoint Online
- Weak Password Policies
- Data Loss Prevention (DLP) Mismanagement
- Not Monitoring Suspicious Sign-In Activity
- Unregulated Registered Applications
- Anonymous Links Creation for SharePoint Sites
- Guest User Invitation Risks
- Not Restricting Access to Shared Mailboxes
- Unrestricted Access to MS Graph, Remote PowerShell, Azure AD
- Non-Admin Access to Entra Portal
- User-Caused Errors
1. Office 365 Credential Phishing
❌ Risk: Phishing attacks are a significant vulnerability because they trick users into revealing their Microsoft 365 login credentials. Attackers can craft convincing emails or messages that appear legitimate, often bypassing basic security filters. Once credentials are compromised, attackers can gain unauthorized access to sensitive data and systems, potentially leading to data breaches or account takeovers. This vulnerability is exacerbated when advanced threat protection and user training are not adequately implemented.
✅ Solution: Use Advanced Threat Protection (ATP) – Safe Links Protection for Email Messages. ATP scans and blocks malicious emails before they reach users’ inboxes.
How to Set Up Office 365 Advanced Threat Protection?
To set up safe links policies in Microsoft Defender, navigate to,
Microsoft Defender -> Policies & rules -> Threat policies -> Safe links
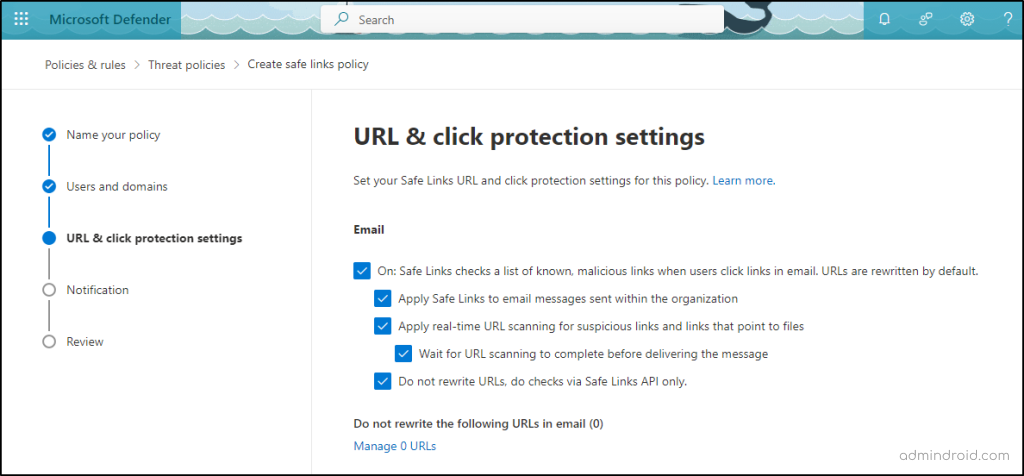
On the page, ensure that all options under ‘URL & click protection settings’ are selected.
Note: The Built-in ‘Protection preset security policy’ provides Safe Links protection to all recipients by default.
Additional measures to consider:
- Safe Attachments: Enable Safe Attachments to protect your environment from malicious files in emails.
- External Email Tagging: Utilize External Email Tagging to identify and flag emails from outside your organization for enhanced security.
2. Over-provisioned Admin Access
❌ Risk: Assigning too many users to global admin roles represents a major vulnerability. Global admins have full control over all aspects of Microsoft 365, including sensitive data and configurations. If a global admin account is compromised, it can lead to severe security breaches, allowing attackers to manipulate or exfiltrate critical information.
✅ Solution: Implement principle of least privilege. This limits users’ access to only what is necessary for their roles, helping to protect Microsoft 365 admin accounts.
How to Implement Principal of Least Privilege in Office 365?
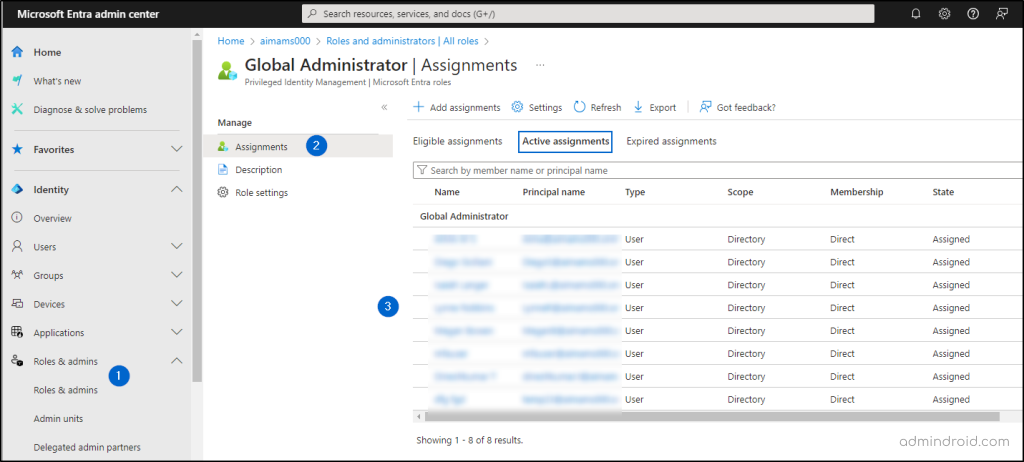
To apply the principle of least privilege in Microsoft 365, follow these steps to ensure users have the minimal access required to perform their tasks securely.
Microsoft Entra admin center > Roles & admins -> All roles -> Global administrator -> Active assignments.
To apply the principle of least privilege in Microsoft 365, follow these steps to ensure users have the minimal access required to perform their tasks
- Identify and review all accounts with global admin roles.
- Validate and check if current admin access is necessary.
- Limit the number of global admins to less than 5 users.
- Reassign users to lower-privilege roles based on their needs.
- Continuously monitor admin accounts for suspicious activities.
- Use just-in-time access to limit admin rights when necessary.
Additional measures to consider:
- Enforce Role-Based Access Control (RBAC): Limit permissions to the minimum required for each user’s role.
- Privileged Identity Management (PIM): Privileged Identity Management ensures that users only have privileged access when needed and monitors their activities. MFA adds an additional layer of protection to global admin accounts.
A layered approach provides the strongest defense!
3. Bypassing Multi-Factor Authentication (MFA)
❌ Risk: MFA is a critical security measure that requires users to provide multiple forms of verification. When MFA is not enforced strictly, users may bypass this step, significantly increasing the risk of unauthorized access. This O365 security issue can lead to account takeovers, as attackers who have acquired login credentials can gain access without the additional layer of protection MFA provides.
✅ Solution: Enforce MFA for All Users: Use Conditional Access policies to mandate MFA for accessing Microsoft 365 resources.
Require MFA for All Users with Conditional Access
To require MFA for all users with Conditional Access, navigate to,
Microsoft Entra admin center -> Protection -> Conditional Access.
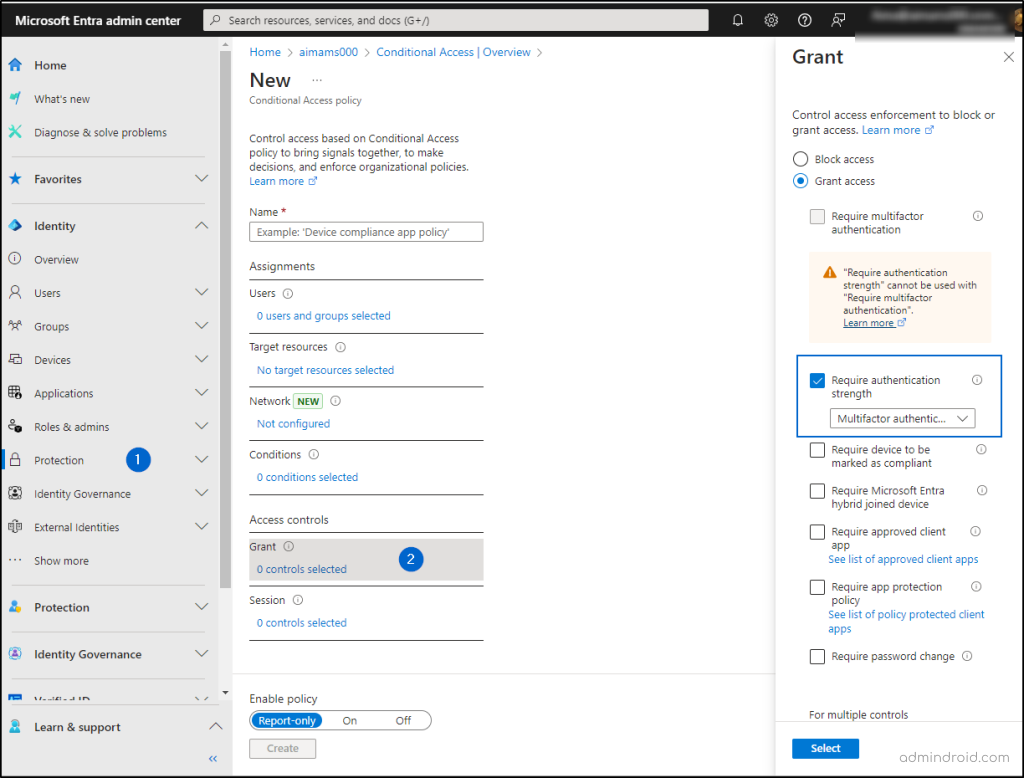
As Microsoft mandates MFA for accessing admin portals like Entra, Intune, and Azure, it’s important to get ahead of these changes by setting up strong authentication methods, including phishing-resistant MFA, for all users.
4. Weak Conditional Access Policies
❌ Risk: Conditional access policies are designed to control access based on factors like device, location, and user risk. Even after configuring strong authentication methods, weak or poorly configured conditional access policies can still allow unauthorized access from unmanaged devices, leaving the organization vulnerable. This happens when the policies are not restrictive enough to account for all potential risks.
✅ Solution: Set Up Risk-Based Conditional Access Policies: Strengthen your security by adjusting access controls based on the assessed risk of users or sign-in, providing an extra layer of protection beyond MFA.
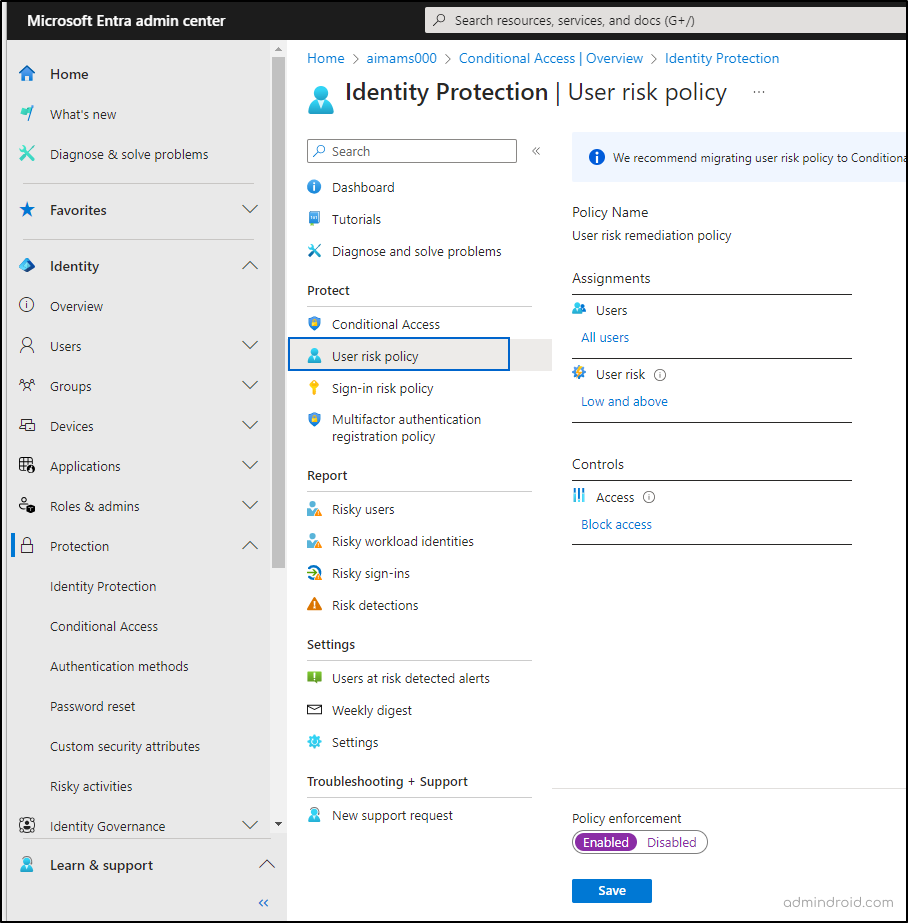
How To Deploy Risk-Based Conditional Access Policies with Microsoft Entra ID?
To implement risk-based Conditional Access policies in Microsoft 365, navigate to,
Microsoft Entra admin center 🡢 Identity 🡢 Protection 🡢 Conditional Access 🡢 Create new policy -> Conditions.
Additional measures to consider:
- Conditional Access What If tool: You can also use the Conditional Access “What If” tool to simulate how your policies will apply to different scenarios. This allows you to test and refine your Conditional Access configurations, ensuring that they provide the right level of security without unintended gaps.
5. Misconfigured Permissions in SharePoint Online
❌ Risk: SharePoint Online permissions are extensive and can be complex to manage. Default or misconfigured permissions can grant excessive access to users, leading to the accidental exposure of sensitive information. This vulnerability arises when administrators assign overly broad permissions generously.
✅ Solution: Understand SharePoint Permission Levels & Best practices.
How to Manage SharePoint Permissions in Microsoft 365?
To effectively manage SharePoint permissions, ensure you are well-versed in the following key areas.
- Full control: Complete authority over a site.
- Edit: Ability to add, modify, and delete lists and documents.
- Read: View content without modification rights.
- Contribute: Add and edit content but not site pages.
- Design: Customize sites and manage other predefined permissions.
Best Practices:
- Follow least privilege: Assign only the necessary permissions.
- Centralize sensitive data: Use specific permissions for sensitive documents.
- Limit item-level permissions: Apply them sparingly to simplify management.
- Optimize access control: Use groups for permission management instead of assigning them directly to users.
- Secure subsites: Align subsite permissions with the parent site’s settings.
Adhering to these SharePoint Online security best practices ensures your environment remains secure and manageable.
6. Weak Password Policies
❌ Risk: When users are asked to create a strong password, what do they often come up with? Their pet’s name or something like @123. While those may be easy for them to remember, they’re also a breeze for attackers to crack. Default password policies that allow weak or reused passwords can make accounts highly susceptible to brute-force attacks and unauthorized access.
Remember, a password like Fluffy123 or P@ssw0rd is not just a cute choice—it’s a vulnerability waiting to be exploited. So, encourage your users to step up their password game with something stronger and more complex. After all, your accounts deserve better protection than a password inspired by your dog’s favorite toy or your first car’s year!
✅ Solution: Ban custom passwords in Office 365
How to Enable Custom Banned Passwords in Microsoft 365?
To ban custom passwords in Microsoft 365, navigate to,
Microsoft Entra admin center -> Protection -> Authentication methods -> Password protection -> Enforce custom list.
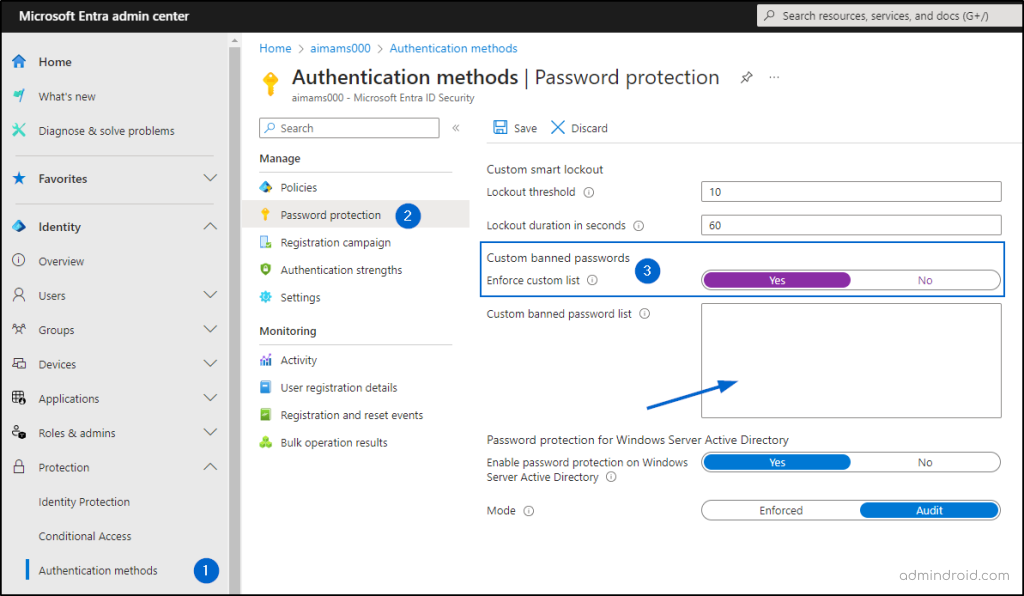
After enabling the Custom banned passwords, make sure to list your banned password in the given box -> Then Save.
Additional measures to consider:
- Use Password Expiry Notification Tool: Require users to regularly update their Office 365 passwords and implement a solution to send password change reminders.
7. Data Loss Prevention (DLP) Mismanagement
❌ Risk: Default DLP settings may not effectively prevent the accidental leakage of sensitive data. Without proper DLP configurations, sensitive information can be exposed or shared unintentionally, leading to data breaches and compliance issues.
✅ Solution: Configure DLP Policies: Set up customized DLP policies to protect sensitive data across Microsoft 365.
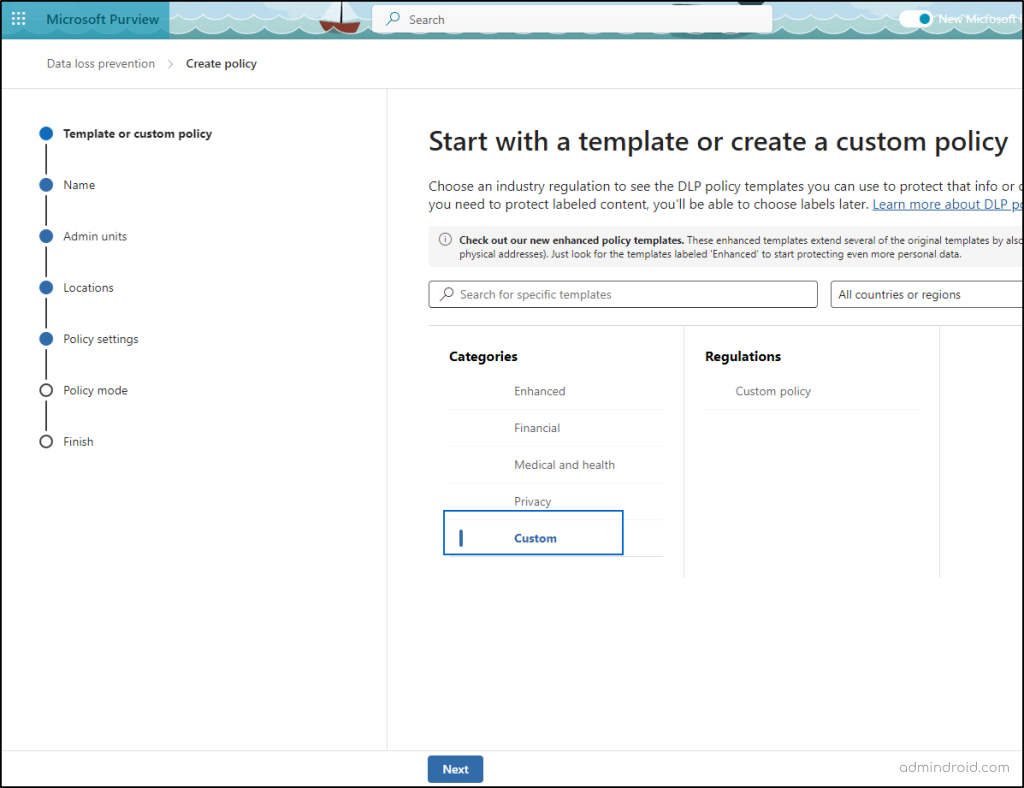
How to Create a Custom DLP Policy?
To create a custom DLP policy,
Microsoft Purview -> Data loss prevention -> Policies -> Create policy -> Categories -> Custom.
If you want to safeguard sensitive files specifically in SharePoint, ensure to configure SharePoint Online DLP. This helps to monitor and prevent unauthorized sharing of sensitive content, enhancing your organization’s data protection measures.
8. Not Monitoring Suspicious Sign-In Activity
❌Risk: Failing to monitor sign-in activities can lead to undetected security breaches. Suspicious sign-ins may indicate compromised accounts or unauthorized access attempts, and without monitoring, these activities can go unnoticed, increasing the risk of a security incident.
✅ Solution: Enable report suspicious activity & check reports for unusual or unauthorized suspicious activities.
How to Enable Report Suspicious Activity in Microsoft Entra Admin Center?
To enable ‘Report Suspicious Activity’ in Microsoft Entra Admin Center, navigate to,
Microsoft Entra admin center → Protection→ Authentication methods → Settings → Report suspicious activity .
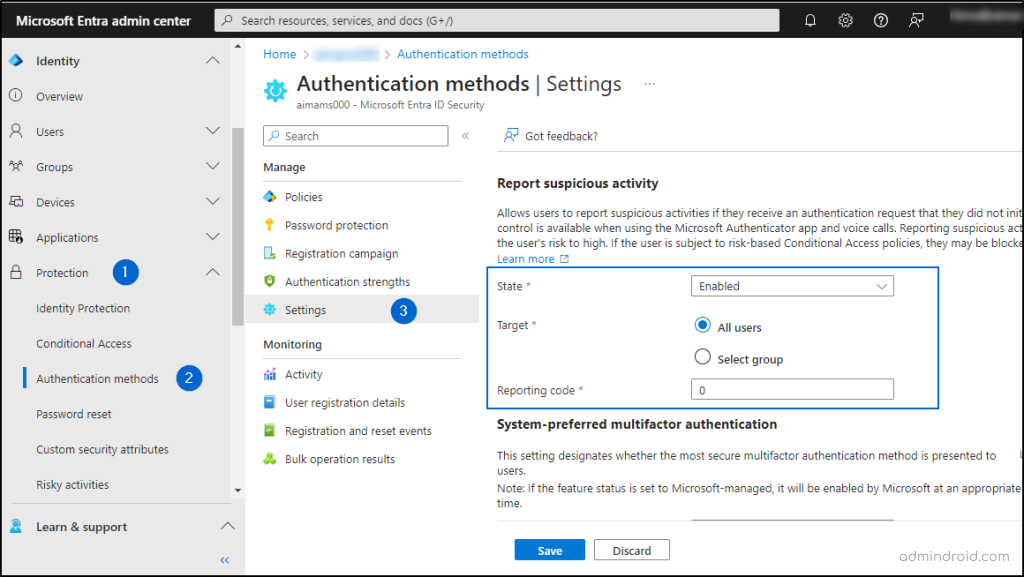
Here, make sure that the state is enabled. Now, to view the risk detection reports, navigate to,
Microsoft Entra admin center → Protection → Identity protection → Risk detections (under the ‘report’ section).
9. Unregulated Registered Applications
❌ Risk: Allowing unmanaged or outdated applications to access Microsoft 365 can expose your organization to security risks. Applications with unnecessary or excessive permissions can be a vector for data breaches or unauthorized access. Additionally, unused applications can accumulate over time, potentially becoming a security vulnerability if their permissions are not reviewed and managed.
✅ Solution: Use App Consent Policies: Manage user consent to applications and require admin approval for new app registrations.
Microsoft Entra admin center -> Applications -> Enterprise Applications > Consent and Permissions > User Consent Settings.
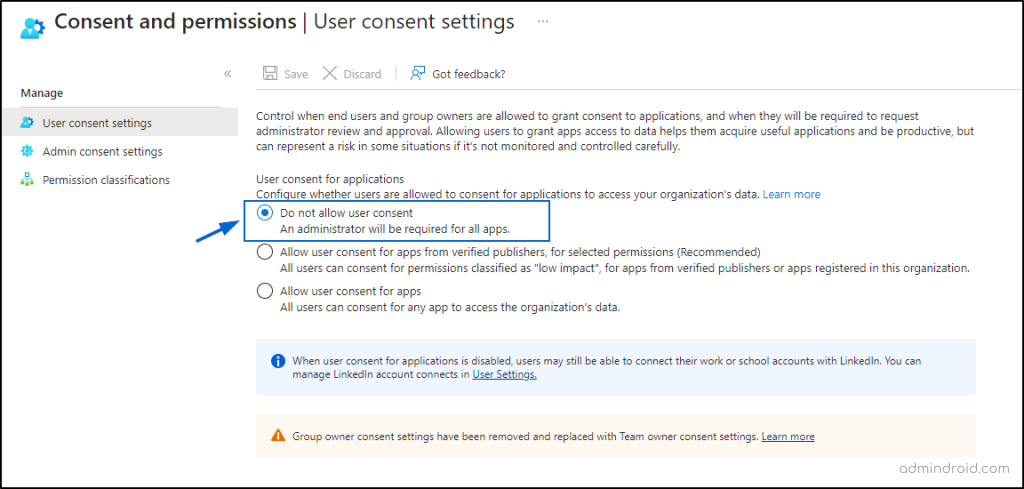
- Remove unused applications in Entra ID:
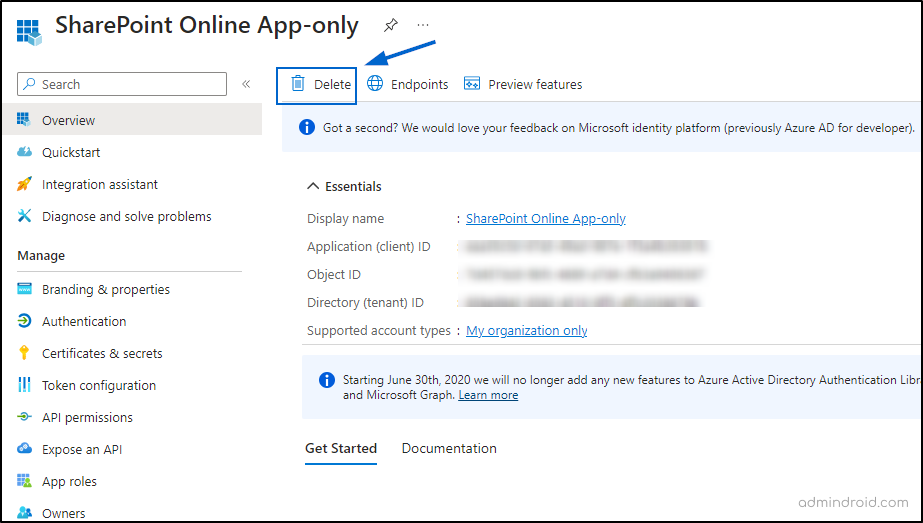
To remove unused applications in Entra ID, navigate to,
Microsoft Entra admin Center→ Applications → App registrations → Select the respective unused app → Delete.
In addition, regularly review the Azure AD application activity report to track the usage of applications and identify any that might pose security risks.
10. Anonymous Links Creation for SharePoint Sites
❌ Risk: Allowing anonymous links to be created can lead to unauthorized access to sensitive documents. Users may inadvertently share these links, making it easy for unauthorized individuals to access confidential information.
✅ Solution: Disable Anonymous Links: Configure settings to prevent the creation of anonymous links for document sharing.
How to Turn off Anyone Links in SharePoint?
To turn off anyone links in SharePoint, navigate to,
SharePoint admin center -> Policies -> Sharing -> Move the indicator and change the permission based on your requirements.
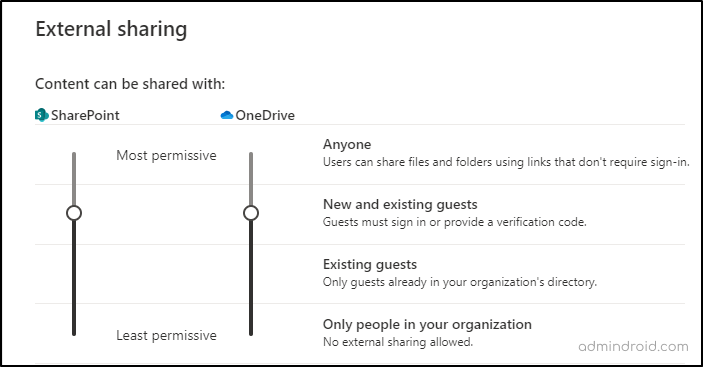
In addition to disabling anonymous links, it is essential to manage external sharing carefully to prevent security breaches by understanding and implementing possible ways to limit external sharing in SharePoint.
11. Guest User Invitation Risks
❌ Risk: Are you aware that guest users in your organization can invite other guest users? This ability can expand access beyond the intended boundaries, potentially allowing unauthorized or untrusted individuals to gain access to sensitive information and increasing the risk of data exposure or security breaches.
✅ Solution: Restrict Guest Invitations: Control guest user invitations through Microsoft Entra ID settings, allowing only trusted individuals to invite new guests. To do this, navigate to,
Microsoft Entra admin center 🡢 Identity 🡢 External Identities 🡢 External collaboration settings
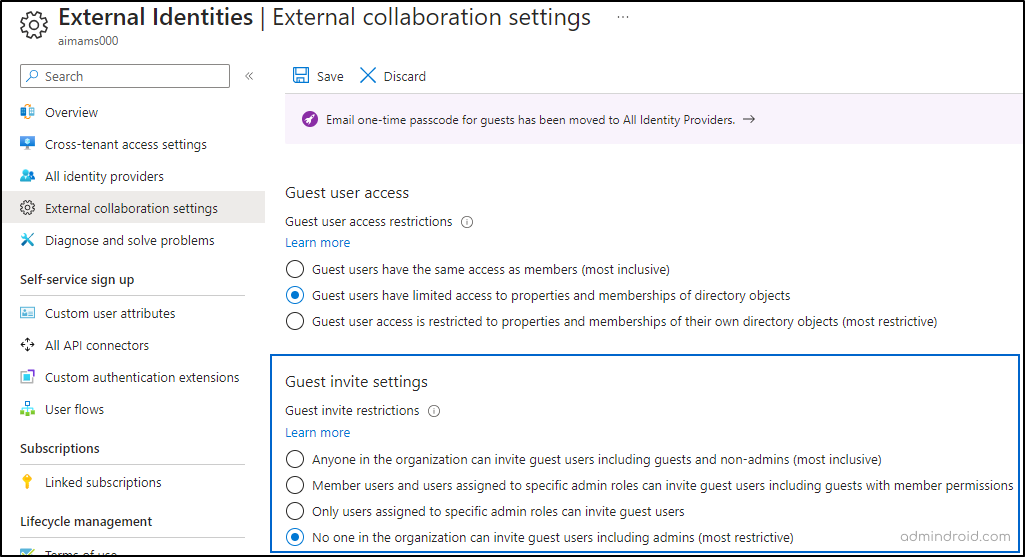
Under ’Guest invite settings‘, choose your desired option and save.
12. Not Restricting Access to Shared Mailboxes
❌ Risk: Shared mailboxes can be vulnerable if not properly managed. Default configurations may allow sign-in capabilities, which could potentially be exploited if access credentials are compromised or if users with legitimate access inadvertently share mailbox details. This exposure increases the risk of viewing sensitive communications.
✅ Solution: Block shared mailbox sign-in using M365 admin center.
How to Block Access to Shared Mailboxes in Microsoft 365?
To block shared mailbox sign-ins in M365, navigate to,
Microsoft 365 Admin Center. -> Users -> Active Users-> Select the user -> Block sign-in -> Block this user from signing in -> Save changes.
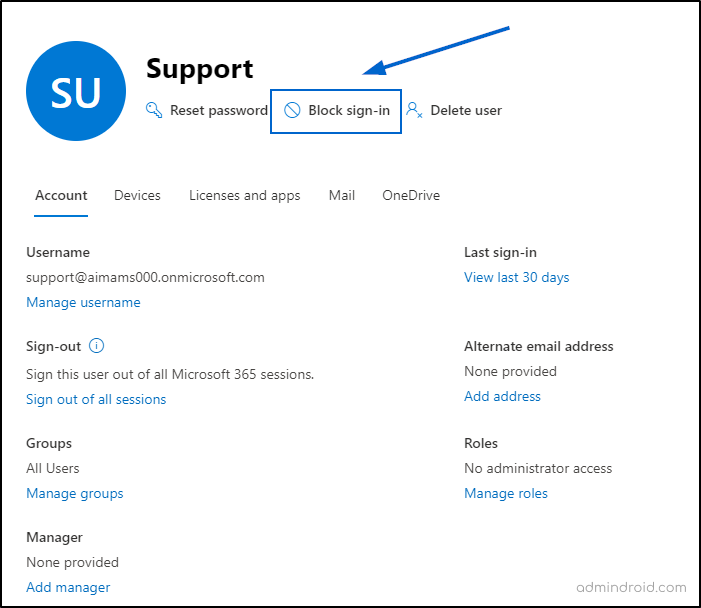
13. Unrestricted Access to MS Graph, Remote PowerShell, Azure AD
❌ Risk: Allowing broad access to management tools like MS Graph and Remote PowerShell can expose your environment to risks. These tools, if accessed by unauthorized individuals, can lead to unauthorized changes or data exposure.
✅ Solution: Implement Access Controls: Restrict access to MS Graph, Remote PowerShell, and Azure AD to authorized users only.
To do this, first, connect to Microsoft Graph PowerShell, then run the following cmdlet to restrict access to Azure AD PowerShell.
|
1 |
Update-MgPolicyAuthorizationPolicy -AuthorizationPolicyId <AuthorizationPolicyId> -BlockMsolPowerShell $true |
Now, to restrict access to Microsoft Graph PowerShell and Graph Explorer, navigate to,
Microsoft Entra admin center -> Identity –> Applications —> Enterprise applications –> All applications -> Microsoft Graph PowerShell -> Properties -> Enabled for users to sign in? -> No.
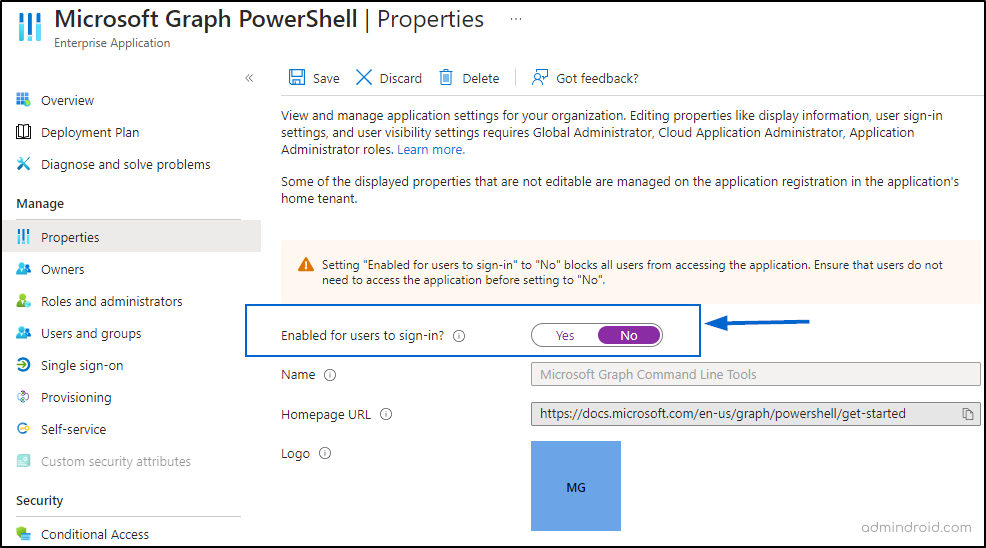
Similarly, you can also disable access to Exchange Online PowerShell. This reduces potential entry points for attackers and minimizes the damage in case of a security breach.
14. Non-Admin Access to Entra Portal:
❌ Risk: By default, Microsoft 365 environments may allow non-admin users to access certain areas of the Entra portal. This default behavior can be risky because non-admin users, who typically lack the necessary training and responsibilities for managing system settings, can view the data.
When non-admin users have access, they might inadvertently or maliciously view critical configurations, affecting the overall security and functionality of your Microsoft 365 environment. This risk is often overlooked until it results in significant security issues. To mitigate this, it’s crucial to manage and restrict access to the Entra portal based on user roles and their actual needs.
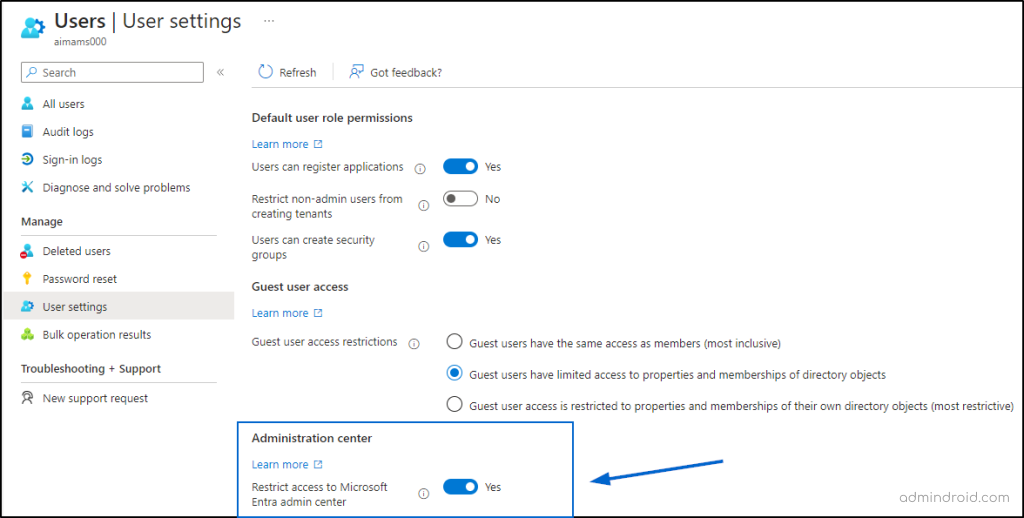
✅ Solution: Restrict Access to Entra Portal: Limit access to the Entra portal to only those users who require it for their role. Use role-based access controls (RBAC) to enforce this. To do this, navigate to,
Microsoft Entra admin center -> Users -> All users -> User settings -> Administration center -> Restrict access to Microsoft Entra admin center -> Yes.
15. User-Caused Errors
❌Risk: Default training and guidelines may not be comprehensive, leading to user errors that compromise security.
✅ Solution: Provide Comprehensive Training: Offer regular and in-depth security training to all users, focusing on best practices for safeguarding their accounts. Additionally, be aware while clicking external emails to avoid phishing attempts and other malicious activities.
We hope this blog has highlighted the key security risks associated with Microsoft 365. However, don’t stop here—It’s essential not only to monitor these issues but also to take action against them. Microsoft Secure Score can be a great starting point to lock down attack surfaces, as it offers a wealth of recommendations ranging from simple security settings to critical ones. Thank you for reading! If you have any questions or suggestions, leave a comment below.