On Day 23 of Cybersecurity awareness month, learn to implement strong Microsoft 365 Password Policy and prevent suspicious attacks within your organization. Stay tuned for more blogs in the Cybersecurity blog series.
Recently, these words have been buzzing around a lot among organizations,
The company’s user data has been breached!
Password theft occurred!
MFA attacks have increased!
And this is where most issues really began, users tended to be broken out in the first step itself, while authenticating with PASSWORDS!
- Do our Microsoft 365 password complexity settings lack security and safety?
- Does the organization bear responsibility for not implementing the secured password policy in Entra?
- Or is it the users’ fault for having easily breakable and guessable passwords?
The answer to all the above questions is YES! Most organizations don’t take password security seriously, and users probably use easy-to-remember passwords. Therefore, brute-force attacks, password-spraying attacks, and similar threats continue to rise, which brings us to the critical question of how to prevent them.
Considering these points, let’s examine where passwords have failed and explore effective strategies to enhance your M365 password security.
⚠️Why do Passwords Fail?
You have a secret that can ruin your life. It’s not a well-kept secret, either. Just a simple string of characters that can reveal everything about you.
Yes, absolutely, pointing out the passwords! Passwords are intended to protect accounts, but where did they fall short? The best way to explain how to choose a good password is to show how they’re broken. So, let’s look at some weak spots where passwords failed to keep the data secure.
1. Is Microsoft Entra Password Expiration Policy a Good Approach?
Previously, organizations have used a password expiration policy in Entra ID to enforce strong password practices. This Entra ID password expiration setting asks users to periodically update their passwords and lets users set weaker, easily guessable passwords.
So, Microsoft suggested the best password expiry practice and demanded users stop changing their passwords frequently!
2. Easy-to-Remember and Guessable Passwords
Easy-to-remember and guessable passwords serve as prime entry points for hackers. For example, an Avast survey reveals that 83% of Americans are using weak passwords and reusing passwords to protect multiple accounts. Also, Google discovered that over 53% of users have set passwords that include their names, birthdays, and pets’ names. This results in more password-related breaches and eventually leads to a compromise of overall password security.
3. Sharing is Caring Doesn’t Work Here
Sharing is caring is best for Microsoft 365 collaboration and integration, but not when it comes to your account security. According to Google, 43% of users have shared their passwords with other users or reused them repeatedly, and some have shared them with other services or alternative email accounts.
4. Pen and Paper Don’t Help Much With Password Security
Even when people use much stronger passwords that are hard to remember, they fail at one point. Surprisingly, 42% of IT professionals use sticky notes to manage their Microsoft 365 passwords, including admins! 😵
So, having strong passwords and pasting them down doesn’t work well. And this reliance on pen and paper for password management, despite employing strong passwords, poses a considerable threat to overall data security.
5. Privileged Account Failures
Here comes the worst! Though Microsoft 365 privileged accounts are the most sensitive, admins don’t take much concern about password security and reuse passwords or share them with fellow admins for use.
Different Ways to Strengthen the Microsoft 365 Password Policy
Now, first things first: It’s the admin’s responsibility to implement a secure password complexity policy setting in Microsoft 365. So, what’s the best way to do that? Do we need third-party software? 🤔
No, Microsoft has you covered with its built-in feature – password protection for Microsoft Entra! 🚀
Let’s get into real talk on how this actually helps in improving our password security strategy! Basically, Microsoft 365 has default security rules in place. Alternatively, if these aren’t sufficient for your organization, you can customize additional password complexity settings in Microsoft 365.
- Default Office 365 Password Policy in Entra ID Password Protection.
- Customize the Entra ID Default Password Policy.
Microsoft 365 Default Password Policy
The default password policy in Entra password protection serves as a key security measure to prevent user identity breaches.
What is Entra ID Password Protection in Microsoft 365?
Password policy applies to all user accounts that are created & managed directly in Entra ID. It describes what a secure password should look like, when it should expire, how many attempts should be made before a lockout occurs, and what can be excluded from the organization’s Microsoft 365 password policy settings.
Note: However, note that the Entra ID password policy guards cloud-only Microsoft 365 accounts. For synced accounts from on-premises AD, activate the EnforceCloudPasswordPolicyForPasswordSyncedUsers cmdlet to extend its reach.
The following are the default Microsoft Entra password policies enabled. Users cannot change these settings. However, administrators can modify only a few Azure AD password settings.
| S.No | PROPERTIES | ENTRA ID PASSWORD REQUIREMENTS |
| 1. | Minimum password length | By default, Microsoft 365 has a recommended password length which is: Min – 8 Characters. Max – 256 Characters. |
| 2. | Characters allowed | 1. A – Z 2. a – z 3. 0 – 9 4. @ # $ % ^ & * – _ ! + = [ ] { } | \ : ‘ , . ? / ` ~ ” ( ) ; < > 5. blank space |
| 3. | Characters not allowed | Unicode characters. |
| 4. | Restrictions for passwords. | Should satisfy three out of the four of the following: 1. Lowercase characters. 2. Uppercase characters. 3. Numbers (0-9). 4. Symbols (Refer to the previous password character usage restrictions). |
| 5. | Default password expiration policy in Microsoft Entra. | Default count: 90 days Admins can change the default range: 1. Set password expiration policy for your organization using PowerShell: Set-MsolPasswordPolicy -ValidityPeriod 60 -DomainName <DomainName> 2. Set Microsoft 365 password expiration policy using Admin Center: Included a detailed description below. Click here to view. |
| 6. | Password expiration notification. | Default count: 14 days before the password expires. Admins can modify the value for password expiration notification emails. Set-MsolPasswordPolicy -ValidityPeriod 90 -NotificationDays 15 -DomainName <DomainName> |
| 7. | Password never expires. (Recommended setting by Microsoft) | Default: False (Not set) Modifications could be done: Admins can change the default value and set a password to never expire using PowerShell. Detailed steps are given below. |
| 8. | Password change history. | The last password cannot be used again when the user changes the password. (Will show error if attempted) |
| 9. | Password reset history. | The last password can be used if the user tries to reset the forgotten password. |
| 10. | Microsoft Entra account lockout threshold. | After 10 continuous failed login attempts, the account locks. (For detailed information – check below) |
| 11. | Account lockout duration. | It will be locked for 60 seconds(1 minute.) (Increases based on future login attempts) |
Change Entra Password Policy in Microsoft 365
Microsoft has pre-configured essential Entra password policies for secure implementation. However, admins can customize several settings to further strengthen your organization’s defenses. 💯Now, let’s delve into the detailed steps required to configure a Microsoft Entra password policy.
- Set the password to never expire in Microsoft 365.
- View Microsoft Entra password protection in Microsoft 365.
- Manage the Azure AD smart lockout values.
- Ban custom passwords in Microsoft 365.
Set Password to Never Expire in Microsoft 365
By default, Microsoft has set passwords to expire in 90 days and force a password change, but this led users to opt for weaker, easier-to-guess passwords. That’s why admins have started to disable password expiration in Microsoft 365. (Recommended approach by Microsoft, too!) To set the password never expire value, follow the path below.
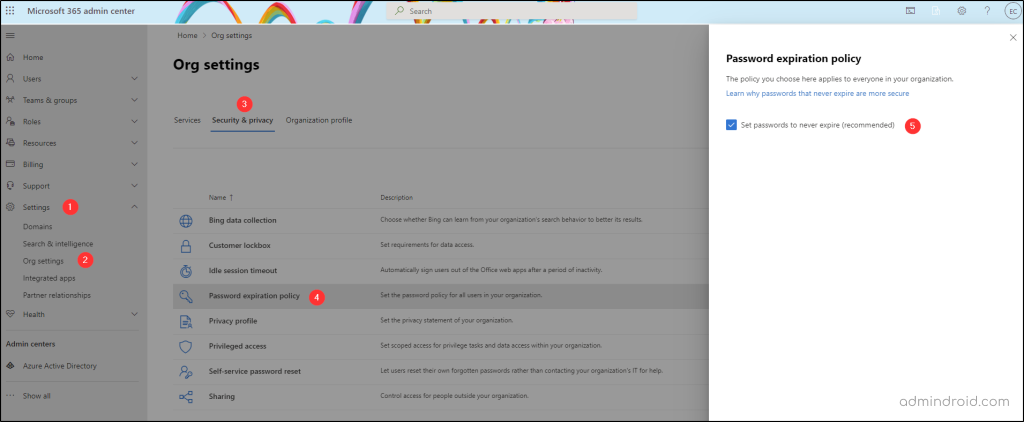
- Open the Microsoft 365 admin center and select Settings –> Org Settings.
- Then, click the Security and Privacy tab at the top. (Only the global admins can see this tab.)
- From the Security and Privacy tab, select the Password expiration policy.
- Here, admins can check the box “Set passwords to never expire,” ensuring users’ passwords remain unaffected by expiration dates previously configured.
Disable Password Expiration in Microsoft 365 Using PowerShell
PowerShell to the rescue! While the Microsoft 365 admin center is handy, PowerShell offers a faster, more flexible way to set user passwords to never expire. So, ditch the clicks, and let’s dive into the code!
Check the Password Expiration Policy Status of All Users
The first thing to do is check the password expiration policy setting status of all users, so you can make appropriate policy adjustments for maximum efficiency. And for that, you can use the below PowerShell script:
|
1 2 3 4 |
Connect-MgGraph -Scopes "User.ReadWrite.All","Group.ReadWrite.All" Get-MgUser -All -Property UserPrincipalName, PasswordPolicies | Select-Object UserprincipalName,@{ N="PasswordNeverExpires";E={$_.PasswordPolicies -contains "DisablePasswordExpiration"} } |
Set Passwords to Never Expire for Microsoft 365 Users Using PowerShell
Now that we’re aware of the Azure password expiration statuses, let’s proceed with disabling them based on specific user needs:
- Run the below cmdlet to set an individual user’s password to never expire in Azure AD.
|
1 |
Update-MgUser -UserId -PasswordPolicies DisablePasswordExpiration |
- Run the below cmdlet to disable password expiration for all users in Microsoft 365.
|
1 |
Get-MgUser -All | Update-MgUser -PasswordPolicies DisablePasswordExpiration |
That’s it! With a single cmdlet, you can break the chains of expiration for every user in Entra ID. Remember, great power comes with great responsibility! 🚀However, make sure to have strong password complexity requirements and multi-factor authentication in place.
Manage Password Policy in Microsoft Entra
Now that we’ve ensured users’ passwords won’t expire, it’s time to focus on the next crucial step: strengthening password security. 🚀Our built-in feature, Microsoft Entra password protection, comes to the rescue! 😌 So, to view the password protection in Microsoft Entra, follow the path below.
- Open the Microsoft Entra admin center.
- Select ‘Authentication Methods’ in the Entra ID dropdown.
- Click the ‘Password Protection’ section within the Manage menu.
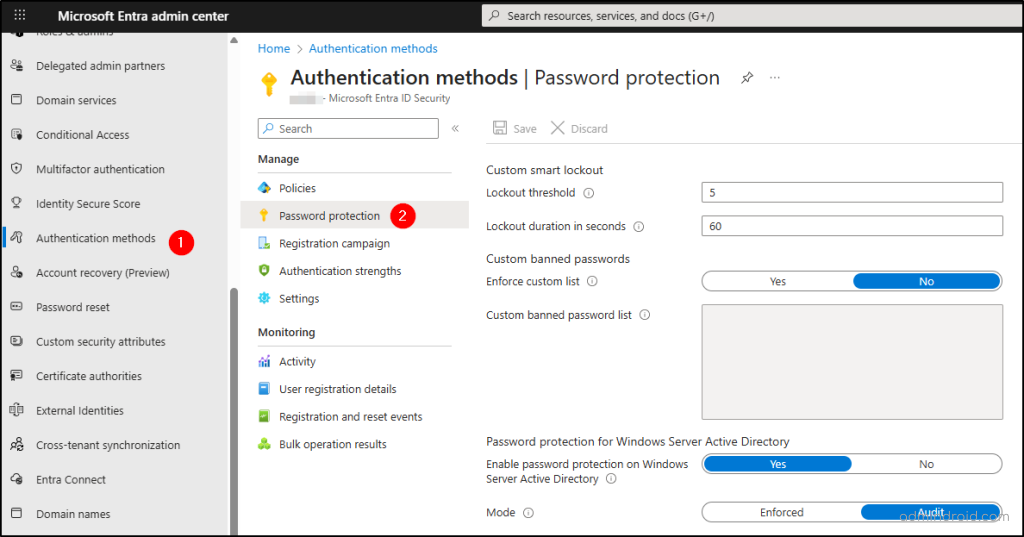
Voila! This section houses all password security settings, from custom-banned password lists to configuring smart lockout values. Let’s explore each setting in detail.
Manage the Entra ID Smart Lockout Values
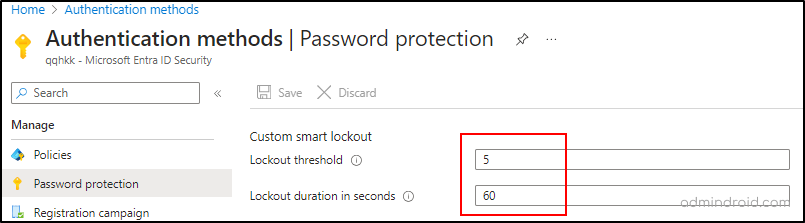
Regular lockouts often block genuine users, but smart lockout functions differently, factoring in location, IP address, password patterns, and more before locking an account. This intelligent system prevents password guessing by using cloud intelligence, distinguishing attackers from legitimate sign-ins.
Integrating Password Protection and Smart Lockout enhances an organization’s security measures. Basically, the smart lockout in Entra ID is enabled by default! However, Microsoft Entra ID P1 license is required to update lockout threshold values and durations.
Therefore, you can configure smart lockout in Microsoft Entra ID and protect your users from brute-force attacks.
Note: The lockout duration increases gradually if an account locks out repeatedly.
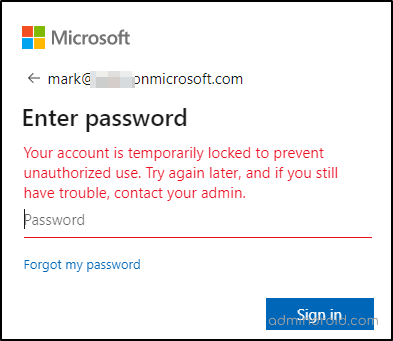
As soon as the smart lockout threshold is reached, you’ll see this error message:
Your account is temporarily locked to prevent unauthorized use. Try again later, and if you still have trouble, contact your admin.
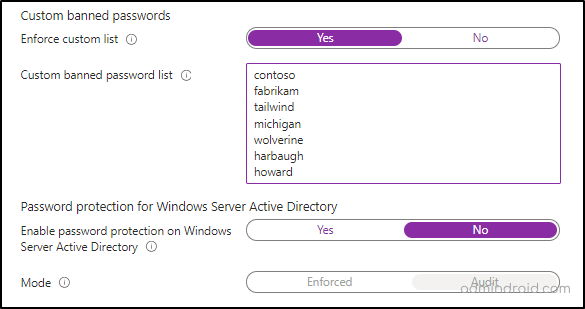
Ban Custom Passwords in Microsoft 365
By default, Microsoft creates a global banned password list based on current trends and breaches. Therefore, it is applied automatically to all cloud-only Microsoft 365 users without the option to enable or disable it. However, for added security beyond the global list, organizations can create their own custom banned password list using the Entra ID password protection feature.
To enhance security, enable custom-banned passwords in Microsoft Entra to prevent users from using easily guessable passwords.
Note: A Microsoft Entra ID P1 or P2 license is required when planning to create a custom banned password list.
6 Tips to Improve Microsoft 365 Password Security:
Strengthening your password policy requires more than just basic rules. Once the essentials are covered, consider the following measures to build a more resilient security posture.
Guidelines for Microsoft 365 Password Complexity:
- Educate users on password complexity: The first and foremost step that is to be carried out is educating your users. Make sure your users use different passwords for work and personal accounts.
- Avoid frequent forced password changes: Constantly requiring password updates often leads to weaker passwords. However, if a password expiration policy is set, ensure the process is automated by sending password expiration notifications using tools like Power Automate. This proactive approach ensures users are aware of upcoming expiration dates, helping to prevent account lockouts and enhance overall security.
- Prevent users from re-using old passwords:
- By default, Microsoft 365 cloud-only users cannot reuse their last password when changing it.
- If users are synchronized from the on-premises AD, then you can prevent them from reusing passwords by creating a custom password policy. Password protection works differently in on-premises environments vs Microsoft 365, so understanding these variations can help you enforce stronger password policies across both platforms.
- Enable and enforce MFA: Configuring multi-factor authentication significantly reduces the success rate of password-based attacks. Even strong password rules can fail, so using a second factor creates an additional barrier against unauthorized access.
- Guide users to limit password exposure:
- Strong password? Great! Now diversify! 💯Because sticking with one for everything might feel convenient, but it’s a hacker’s dream. Yeah, reusing the same strong password for multiple services & personal apps is more dangerous than you might think! ⚠️ Diversifying their credentials minimizes the damage if one account is compromised.
So, keep your accounts safe by using unique passwords – one for each service. That way, if one gets compromised, your others stay under lock and key.
Finally, now it’s time to wrap things up! Hopefully, we’ve covered the secured password strategy and ways to implement the password policy in great detail.
Authentication is similar to a lock; nobody gets in without the keys
So, get started now, implement the strongest password strategies, and encrypt your entry keys!






