On Day 22 of Cybersecurity awareness month, learn to utilize the Microsoft 365 alerting to effectively secure your organization today. Stay tuned for more blogs in the Cybersecurity blog series.
Should admins stay up to date? Do they really need to know what’s going on in the organization?
Of course, yes! Nowadays, cyber threats are increasing day-by-day tremendously. Cybercriminals are building longer ladders to break the security wall. So, admins need to review often and build security much stronger. To achieve this, first, admins need to know the suspicious activities that occur in the organization instantly. Research from IBM says, ‘In 2022, it took an average of 277 days to identify and contain a breach.’ Shortening the duration can save money. Thus, admins need to address the breach and respond to it asap to save costs and avoid damages. Microsoft 365 Alerting comes into play here. It helps admins beware of suspicious happenings in the organization at the right time and to monitor and review the alerts later. Let’s take a look at how it works and how it facilitates improving security.
How Microsoft 365 Alerts helps to improve Security?
Microsoft 365 triggers an alert whenever any suspicious activities occur in the organization. It helps admins to acknowledge and respond to risky happenings immediately. Then, admins can take action accordingly.
Threat is a mirror of security gaps. Cyber-threat is mainly a reflection of our weaknesses. An accurate vision on digital and behavioral gaps is crucial for consistent cyber resilience.
-Stephane Nappo
As he says, we should have an accurate vision of security gaps and elevate our security measures stronger than before. Thus, Microsoft 365 alerting helps to fill the security gap with instant monitoring of suspicious activities. But it is scattered in various places with some enhanced features. Don’t get confused! Let me explain them clearly, one by one.
Microsoft 365 Default Alert Policies
Microsoft provides 45 prebuilt alert policies to help admins to stay alerted of risky incidents, unusual activities, privilege assignments, etc., which are basic requirements when looking for security. It provides alert policies in three alert categories which include threat management, information governance, permissions, and mail flow.
These alert policies can be accessed through Microsoft Defender portal or Microsoft Purview portal. All the alert policies will be turned on by default. Admins can edit the ‘recipients’ and ‘daily notification limit’ of the alert policy. Other configurations can’t be edited as it is a default policy.
Note: You should ensure that you enable auditing for the default alert policies to generate alerts.
Microsoft 365 Custom Alert Policies
Every admin needs to customize any feature. When considering security, each organization may have different desires to improve its security. No worries! Microsoft has a provision for creating custom alerts for audit activities based on the needs. Admins can configure everything on their own based on their weakest link in the security chain. In Microsoft 365, admins can create
- Activity alerts in Microsoft 365 Defender portal
- Custom alerts in Microsoft Purview or Microsoft Defender portal
- Alert policies in Defender for Cloud Apps
Let’s see how they work and the difference between them in detail.
Microsoft 365 Activity Alerts
Activity alerts in the Microsoft Purview portal help to create alert policies for Microsoft 365 audit activities. Before creating activity alerts, ensure that you enabled auditing for your tenant.
Activity alerts are well suited for the bellow scenarios.
- If you want to monitor when a specific user performs a specific activity in your organization.
For example, you can get an alert whenever James deletes a file.
- If you want to monitor when a specific user performs certain actions.
For example, you can get an alert whenever James deletes a file, creates a site, or moves a file.
- Similarly, you can get alerts for multiple users performing a specific action or multiple actions based on your needs.
Thus, creating activity alerts will be helpful in monitoring specific users’ actions instantly in your organization. It may take up to 24 hours for alerts to get triggered after creating or updating an alert policy.
License Requirements for Microsoft 365 Activity Alerts
There is no license restriction for creating activity alerts. It will be available for business and enterprise subscriptions.
Note: Activity alerts are being deprecated. So, Microsoft recommends organizations to start using alert policies from the security and compliance center, instead of creating new activity alerts.
Now, let’s explore how to create custom alert policies in the compliance portal or Microsoft 365 defender portal.
Microsoft 365 Alert Policies in Security and Compliance Portal
Creating custom alert policies in the Compliance portal gives you more enhanced features than activity alerts. Additional to monitoring the user’s specific action, you can now get alerts whenever a bulk action happens in the organization within a specified time limit.
There are some scenarios in which Microsoft 365 custom alerts save you!
- Get an alert whenever a user performs a specific action.
For example, you can get an alert whenever a user deletes a file in the organization.
- Get an alert whenever a single user performs a bulk action within a specific time limit.
For example, you can get an alert whenever James deletes more than 15 files in 60 minutes.
- Get an alert whenever a bulk action happens in the organization. Here, it may be performed by a single user or multiple users.
For example, you can get an alert whenever more than 15 files are deleted in 60 minutes.
- Whenever a single user or multiple users performs an unusual activity. Microsoft has some activity volume restriction which is considered usual in the organization. When the activity goes beyond the usual level, it is considered unusual, and we can’t identify the unusual level for each activity.
Note: For these unusual alerts, it will take up to a week for the policy to generate anomaly alerts.
License Requirements for Microsoft 365 Advanced Alerts
- With Office 365 Business subscriptions, you can only create a single event alert.
- For creating advanced alerts like threshold and unusual activities, you should have enterprise E5/G5 subscriptions. For organizations having E1/F1/G1 or E3/F3/G3, you should have a Microsoft Defender for Office 365 P2 or a Microsoft E5 Compliance or an E5 eDiscovery and Audit add-on subscription.
Alerts in Office 365 Cloud App Security
Microsoft has renamed Microsoft Cloud App Security as Microsoft Defender for Cloud Apps. So, many have gotten confused with the name change, what to use, and when to use it. To avoid confusion, you should clearly understand the difference between Microsoft Defender for Cloud Apps and Office 365 Cloud App Security. This helps admins to beware of threats through advanced investigation and alerts. Basically, Office 365 Cloud App security is a subset of Microsoft Defender for Cloud Apps.
There are around 34 pre-built alert policies in Microsoft Defender for Cloud Apps for threat detection, like malware, ransomware, risky sign-ins, unusual admin activity, and more. You can access these via the Cloud app security portal or Defender portal.
Let’s see how these alerts help admins to stay protected from threats.
- It helps to detect anomalies in the Office 365 apps and alert admins instantly.
- You can get alerts for a specific user or multiple users or groups. Else, you can exclude specific users or groups according to your needs.
- It helps to monitor and control real-time sessions for Office 365 apps with Conditional Access App Control.
- It provides cloud platform security for Azure.
- Additional to prebuilt policies, you can create custom policies with required configurations to meet your organizational needs.
License Requirements for Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is only available for organizations with an Office 365 Enterprise E5 or Office 365 US Government G5 subscription.
How to View alerts in Microsoft 365?
- You can view the triggered alerts in the Microsoft Defender portal or Microsoft Purview portal through the Alerts page.
- To view triggered alerts, you should have respective RBAC permissions for each alert category.
- Alerts triggered by anomaly detection policies in Defender for Cloud Apps can also be viewed in the Microsoft Purview portal. Thus, admins can manage all generated alerts through the Microsoft Purview portal. Also with the required license and roles, you can make use of alert tuning policy in Microsoft 365 Defender for effective management of alerts in advance.
Drawbacks of Microsoft 365 Alerting
- For advanced alerts, you should have an enterprise license or add-on licenses.
- When creating custom policies in Defender or Purview portal, you can’t select specific groups, or usernames to generate alerts.
- Only a limited number of common activities are available for custom policy creation.
- Only few prebuilt categories are available for alert policies. Rest of the alerts will come under ‘Others’ category. Also, we can’t create custom labels to categorize the alerts.
To overcome the drawbacks of alerting in a native tool and to provide a better alerting experience, AdminDroid comes with advanced features, cutting-edge insights, and more. It is uniquely curated to solve all your alerting and reporting needs to securely manage your Microsoft 365 environment.
AdminDroid Alerting – Real Defender for Microsoft 365 Environment
AdminDroid Alerts lets you monitor suspicious activities happening in the organization and notify you instantly to take necessary action. Let’s dive into what AdminDroid alerts can do for you.
- Stay on top of cybersecurity attacks – Detect malware attacks happening in the organization before it’s too late.
- Identify unusual activities at the right time – Determine unusual behaviors like tremendous file deletions, anonymous user file activities, failed user logins, external file sharing, and more.
- Stay alerted on highly privileged role assignments – Identify instantly whenever highly privileged roles like global admins, exchange admins, compliance admins, etc., get assigned to users to achieve least privileged access in the organization.
- Detect unwanted data exposure – Prevent data loss by getting alerts on external file sharing, external user file activity, anonymous link creation, and more.
- Monitor critical configuration changes – Keep an eye on changes made in anti-malware, anti-spam, anti-phishing, EOP, and other threat policies.
- Safeguard your confidential information – Keep your sensitive information under wraps by monitoring anonymous file sharing, sensitive file accesses, and more.
How AdminDroid Tops the List in Microsoft 365 Alerting Tools?
AdminDroid’s advanced features make it the go-to solution for protecting your data and preventing data loss in every possible way. Here, let’s see some compelling reasons that will prove why AdminDroid reigns as the top choice.
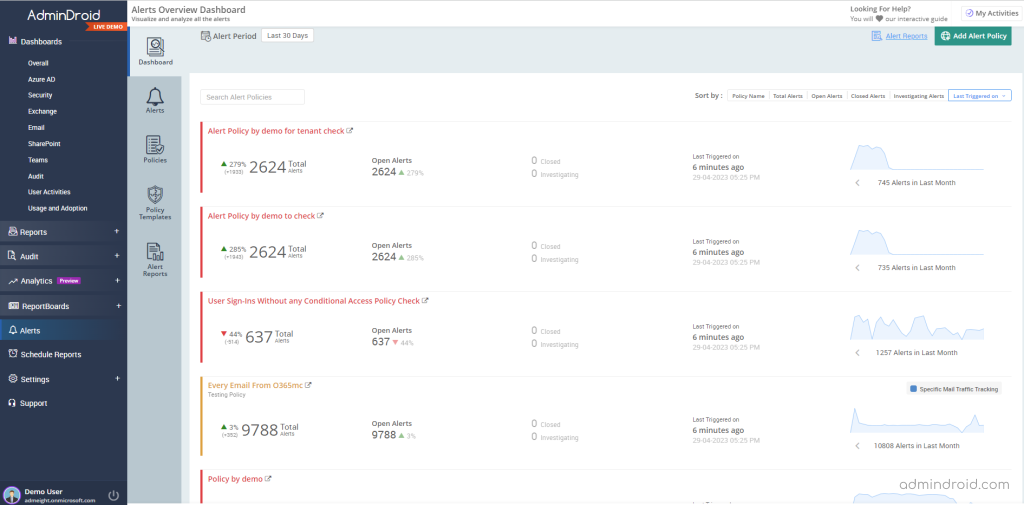
- Get an overview of total alerts, alert statuses, alert policy names, triggered time, etc., using Alert Dashboard.
- Manage all the triggered alerts in a single place with the Alerts tab. Categorize and visualize alerts based on their status, like open, closed, and investigating.
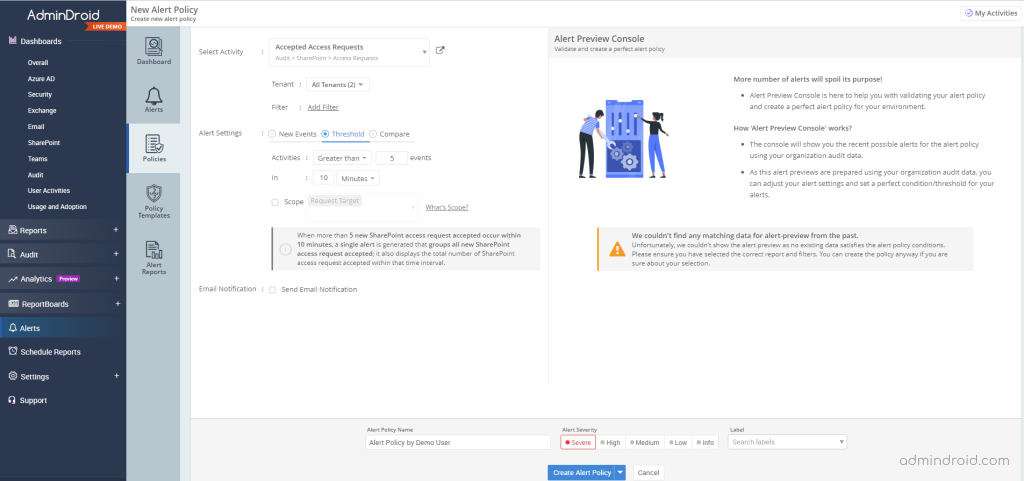
- Create customized alert policies to meet all alerting desires in the organization and alert the right people at the right time. Categorize alerts with labels and severity for better identification.
- Configure threshold limits to identify unusual activities based on your organization’s size and exposure.
- Determine how your organization handles the threats by comparing suspicious activities over time.
- Preview the alerts before deploying alert policies to make better decisions by using the Alert preview console.
- Visualize all your created alert policies and modify them whenever your organization’s requirements might change.
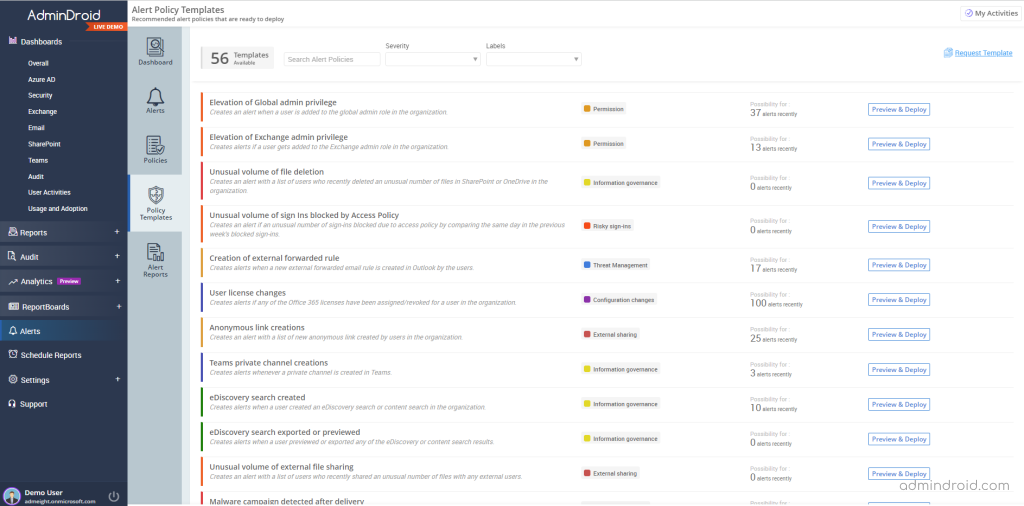
- Utilize 50+ prebuilt alert policy templates to deploy prominent policies suitable for almost every organization. Just deploy them, sit back, and get alerts effortlessly.
- Monitor AdminDroid alerts and alert policy activities like triggered alert summary, alert policy creation, modification, deletion, policy recipients, etc., with Alert reports.
AdminDroid Microsoft 365 alerting tool is truly a savior for securing organizations better than ever. It is not only destined for alerting but also for granular delegation, Microsoft 365 auditing, reporting, and more. Enhance your Microsoft 365 management with AdminDroid and be amazed by its numerous features. Check it out now!
Thus, we have seen how Microsoft 365 alerts are scattered in various places with enhanced features and how AdminDroid helps to manage them effectively. I hope this blog helps you to precisely understand the Microsoft alerting feature and know when to use these alerts in your organization. You can drop your queries in the comment section. Happy Alerting!