As most organizations embrace cloud environments, identity-based attacks have become more aggressive and frequent than ever. Microsoft’s eye-opening Digital Defense Report 2024 reveals a staggering 600 million identity attacks every single day! These numbers highlight a harsh reality: your identity, and the identities of everyone in your Microsoft 365 organization, are prime targets!
To help you stay ahead of these relentless identity threats, Microsoft provides the Identity Threat Detection and Response (ITDR) dashboard. This centralized dashboard allows you to assess your identity security posture, identify vulnerabilities, and take action to strengthen your defenses.
So, buckle up—let’s dive into how Microsoft Defender’s ITDR dashboard helps you stand strong against the tide of identity threats!
What is Identity Threat Detection and Response?
Identity Threat Protection and Response (ITDR) is a cybersecurity solution that helps detect, investigate, and respond to threats targeting user identities. Imagine an attacker stealing a user’s password and trying to access data from a foreign country.
ITDR continuously monitors user behavior for suspicious activity, such as unusual login locations, or unrecognized devices and alerts security teams to potential threats. It allows you to investigate alerts, block attackers, and secure compromised accounts to defend against evolving identity attacks and protect your organization’s data.
To put ITDR into action, Microsoft 365 Defender offers a dedicated ITDR dashboard that brings these detection and response capabilities into a single view for security teams.
How Does the ITDR Dashboard Help Detect Identity Threats in Microsoft 365?
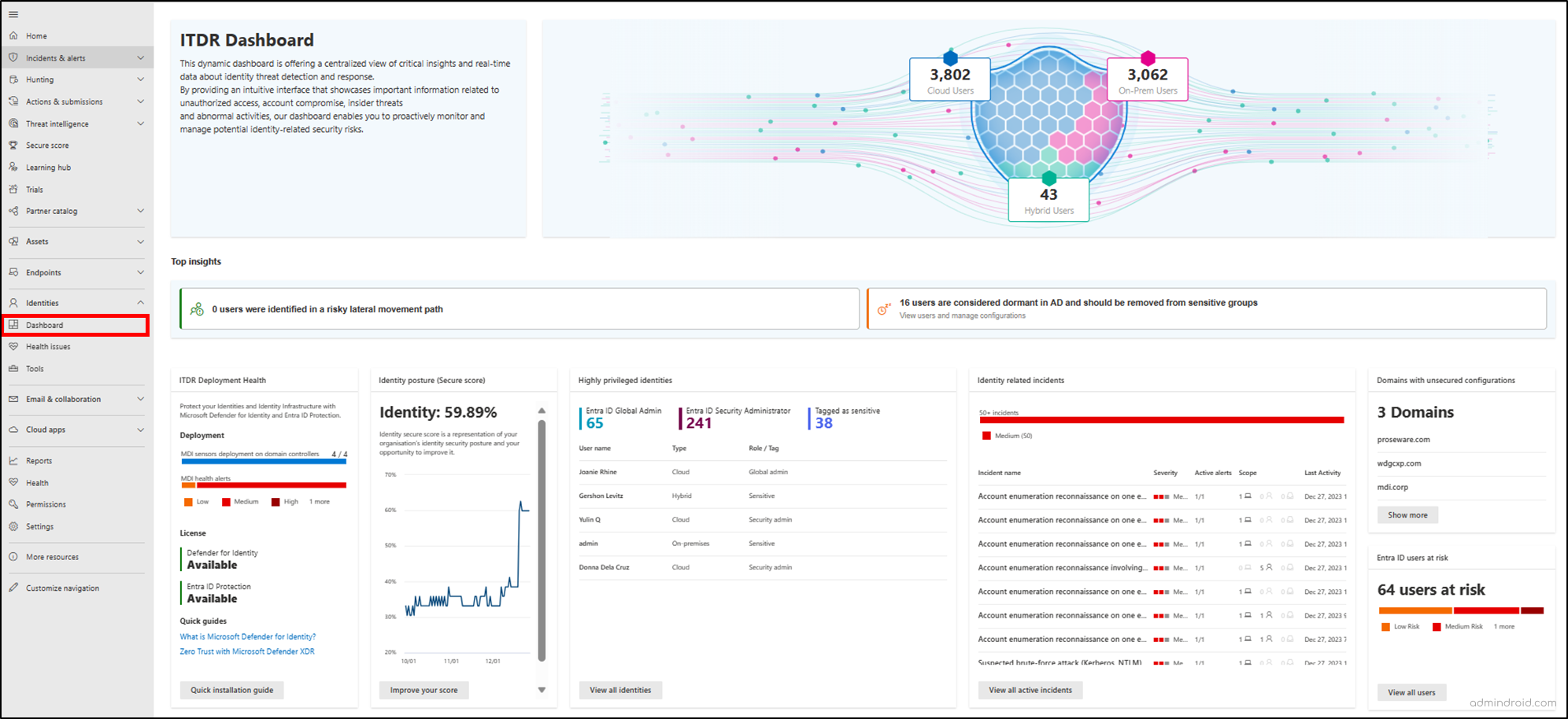
The Identity Threat Detection and Response (ITDR) dashboard plays a central role in Microsoft Defender for Identity and Defender XDR. It helps security teams quickly detect and respond to identity-based threats across Microsoft 365 and on-premises environments. Here’s how its capabilities support your organization in identifying and mitigating threats:
- Centralized Identity Threat View: Offers a unified, prioritized view of identity risks and recommendations for security operations teams.
- Insights into Suspicious Activity: Showcases detection data for risks such as lateral movement, credential theft, unusual admin actions, and risky sign-ins.
- Highlights At-Risk Identities: Flags users with high privileges, exposed tokens, or abnormal behavior.
- Correlates Multiple Signals: Links identity data with device, app, and network activity for deeper threat analysis.
- Enables Quick Response: The ITDR dashboard helps streamline identity threat detection while accelerating incident investigation and response.
Prerequisites to Access Identity Threat Detection and Response Dashboard
To access the Identity Threat Detection and Response dashboard in Microsoft Defender, ensure the following requirements are met:
- License Requirements: You must have a Microsoft Defender for Identity license and an Entra ID Protection license.
- Role Requirements: At a minimum, you must have the Security Reader role to access the dashboard. The Global Administrator role is required to take action on the suggested security recommendations.
How to Access Identity Threat Detection and Response Dashboard?
Here’s how to access the ITDR dashboard in Microsoft 365 to view and improve your identity security posture.
- Sign in to the Microsoft Defender portal.
- Go to Identities > Dashboard.
Key Insights Provided by the Microsoft Defender ITDR Dashboard
Without further delay, let’s explore the key insights provided by Microsoft Defender’s Identity Threat Detection and Response (ITDR) dashboard.
- Overview of identities
- Top insights on risky and dormant users
- ITDR deployment health status
- Microsoft Identity secure score
- High privileged entities list
- Identity related incidents
- Domains with unsecured configuration
- Entra ID active users at risk
1. Overview of User Identity Distribution Across Environments
The ITDR dashboard offers a visual breakdown of identities across Entra ID, on-premises Active Directory, and hybrid configurations. This helps security teams understand where identities reside and how they’re distributed across environments. Understanding how Active Directory and Microsoft 365 security features differ can further help teams manage these identities effectively and strengthen hybrid security.
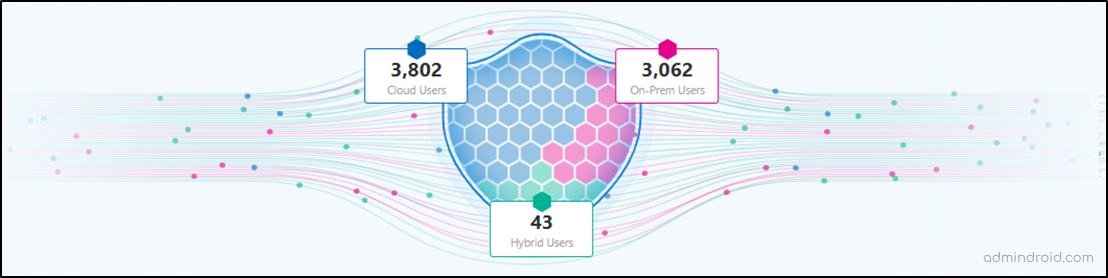
When you click on the respective card, you’re taken to the Microsoft Defender Advanced Hunting platform. There, you can run pre-defined queries using Kusto Query Language (KQL) to get detailed information about each user within a few clicks.
2. Top Insights on Risky and Dormant Users in ITDR
This section provides two key insights that help identify potential security risks and inactive accounts. These include Users Identified in a Risky Lateral Movement Path and Dormant Active Directory Users.
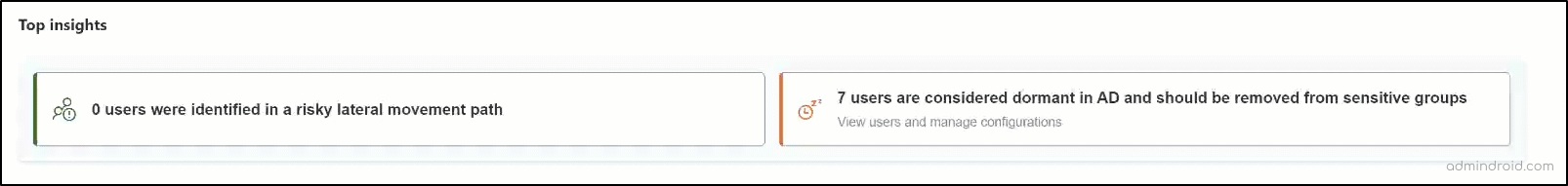
Users Identified in a Risky Lateral Movement Path
The Top Insights widget shows how many sensitive accounts are exposed through risky lateral movement paths. Lateral movement happens when attackers use non-sensitive accounts to eventually access sensitive ones across your network. These paths open up opportunities for attackers and increase security risks.
Based on the insights, you can take immediate actions—such as removing the entity from a group or revoking local administrator permissions assigned to the user account.
Dormant Active Directory Users
This card highlights user accounts that have been inactive for at least 180 days. It specifically lists unused accounts that still belong to sensitive groups, posing a potential security risk.
In response to these findings, consider removing inactive Active Directory users from sensitive groups in your on-premises environment to reduce security risks.
3. ITDR Deployment Health Status in Microsoft Defender
The ITDR Deployment Health section provides a quick overview of the Microsoft Defender for Identity sensors deployment status. It helps ensure that sensors are healthy and running as expected. This is an essential step for monitoring your on-premises Active Directory for threats and suspicious activity.
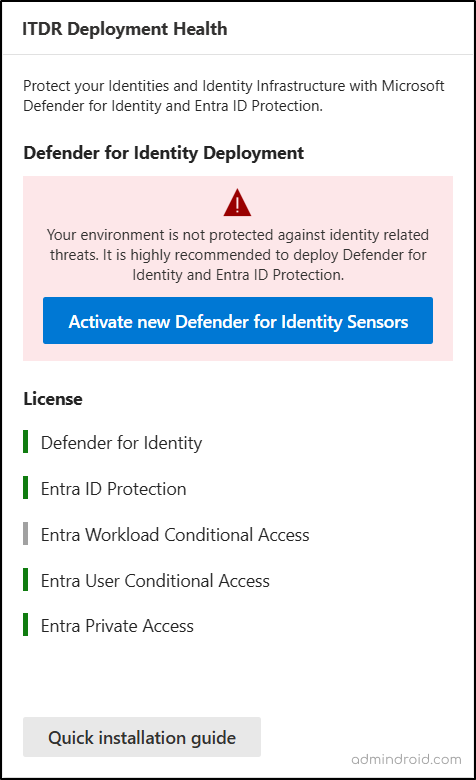
It also highlights deployment issues including disconnected sensors. It also shows the license status for Defender for Identity and Entra ID Protection, helping you identify gaps before they impact security.
4. Microsoft Entra Identity Secure Score
Identity Secure Score is Microsoft’s way of measuring how well your organization’s identity configurations align with recommended security best practices. It evaluates protections around user accounts, role assignments, password policies, MFA usage, and other identity-related configurations.
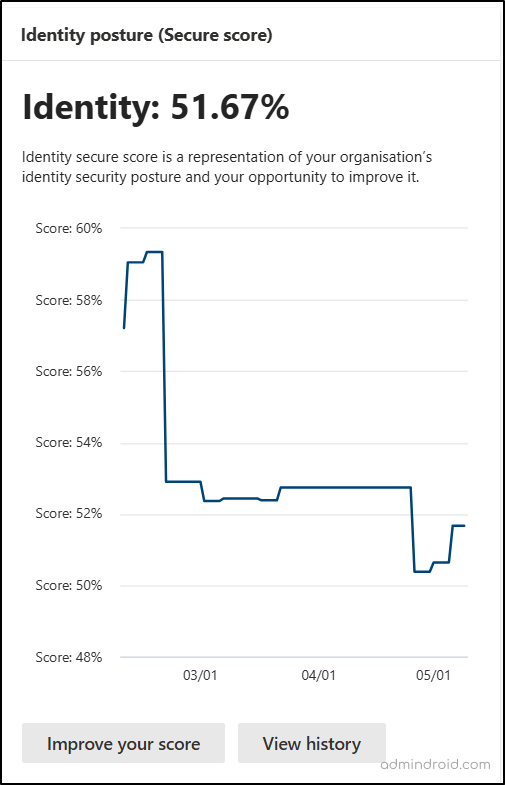
This section displays the Identity Secure Score of your organization, with options to Improve Your Score and View History. Clicking “Improve Your Score” shows recommended actions to boost your security, such as enabling MFA, minimizing global admins, and configuring sign-in risk policies. As you implement these improvements, the score updates automatically. The “View History” option allows you to track your Identity Secure Score progress over time.
5. High Privileged Identities in Microsoft Entra ID
The highly privileged identities list highlights sensitive user accounts in your Microsoft 365 and hybrid organizations. It lists global administrators, Entra ID security administrators, and accounts that are manually tagged as sensitive. For each priority account, it displays details like username, source, user type, and the assigned role or sensitivity tag.
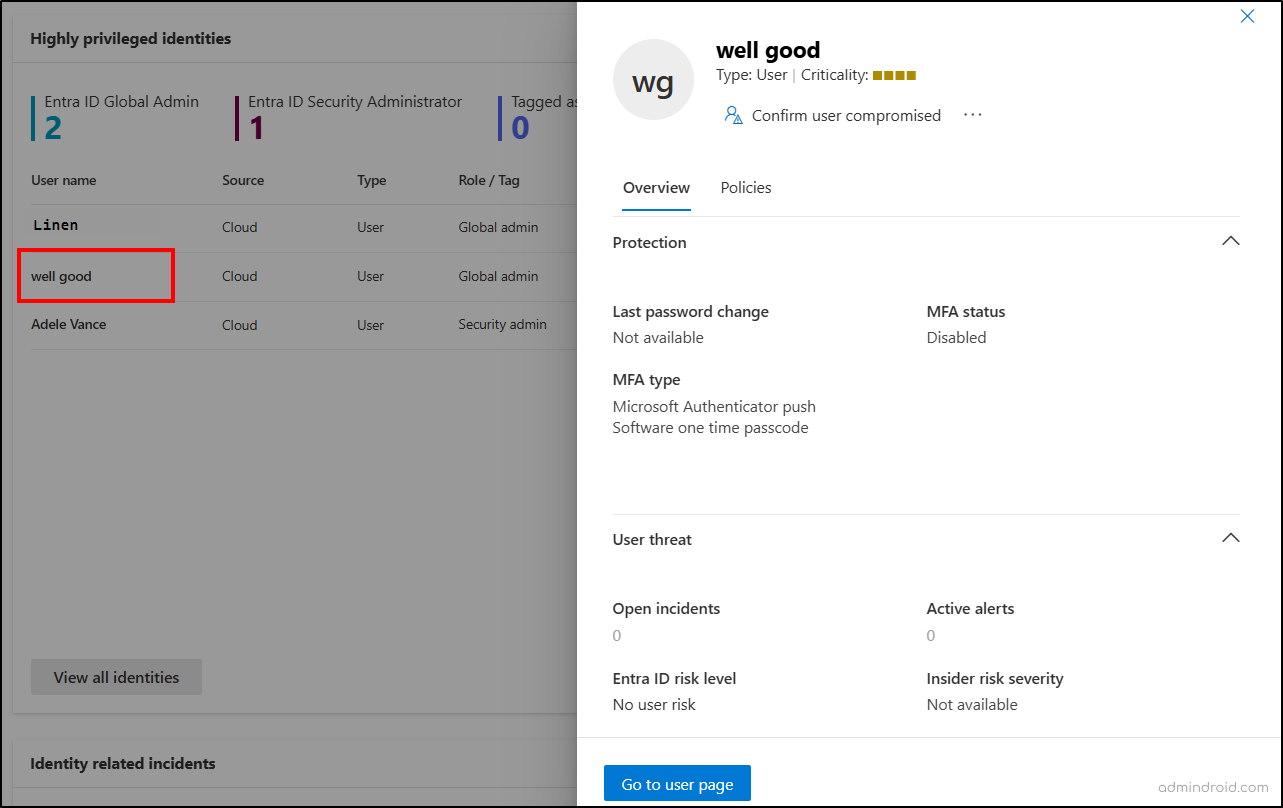
This insight helps you regularly monitor and review high-impact accounts in Microsoft 365 and Active Directory. When you select a user, you’ll see essential details such as their risk level, related actions, an account overview, and the Conditional Access policies applied to them.
6. Microsoft Identity Related Alerts and Incidents
This section displays alerts from both Defender for Identity and Microsoft Entra ID Protection, along with any related incidents from the past 30 days. By showing only relevant identity-based alerts, it ensures that critical incidents stand out and aren’t lost in a flood of notifications.
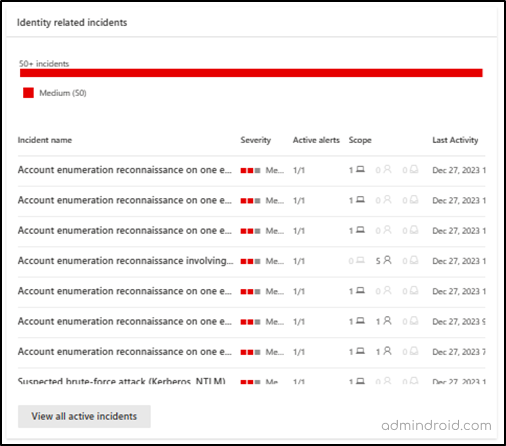
You can identify patterns and trends in these Microsoft 365 activity alerts to support a proactive response. Based on the detected risk level, you can configure automatic remediation actions. For example, requiring a password change or enforcing strong authentication through risk-based Conditional Access policies.
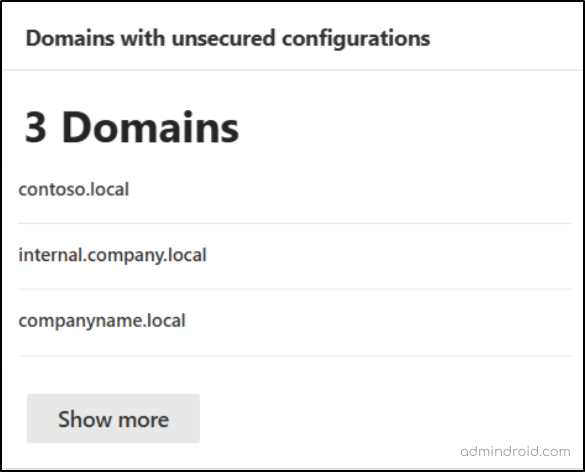
7. Active Directory Domains with Unsecured Configuration
Identifying Active Directory domains with unsecured configurations is critical, as these weaknesses act like open doors for attackers. To help mitigate this, Microsoft Defender for Identity continuously monitors your environment and flags any domains with settings that pose a security risk.
For instance, if LDAP signing is not enforced, attackers can exploit this to compromise domain accounts. This becomes even more dangerous when those accounts hold privileged access.
This dashboard lists the Active Directory domains with insecure configurations, giving administrators a clear starting point to strengthen security. With this insight, admins can take targeted action to apply security best practices and reduce the risk of identity compromise.
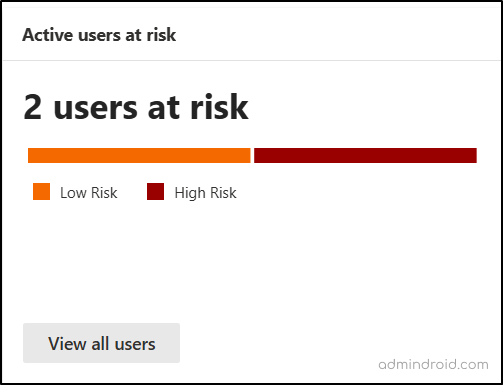
8. Active Risky Users in Microsoft Entra ID
Proactively identifying and managing Entra ID risky users is essential to maintaining a strong security posture and reducing vulnerabilities. This dashboard highlights active user accounts that may be exposed to threats, show unusual activity, or face a risk of compromise. It includes both high and low-risk users.
Final Impressions
Ultimately, securing your organization comes down to a clear vision and swift action. The ITDR dashboard is your strategic lens, exposing hidden identity risks from lateral movement to misconfigurations. It not only helps you see the whole picture and act decisively but also provides guided links for deeper insights.
Complementing this, further enhance your defenses with the Entra ID Protection dashboard, your proactive shield. These aren’t just tools; they’re your essential safeguards, empowering you to detect, investigate, and respond to identity threats with confidence. Strengthen your security posture, one insight at a time. Happy securing!