On Day 22 of Cybersecurity Awareness Month, learn to remove unused credentials from apps in Microsoft Entra to prevent the misuse of credentials. Stay active for the upcoming blogs in our M365 Cybersecurity blog series.
With the introduction of Identity Secure Score recommendations, Microsoft Entra now provides a more comprehensive assessment of your tenant’s security. Similar to Microsoft Secure Score recommendations, it exclusively analyzes your tenant’s Entra ID configuration and compares it to M365 security best practices. If a recommendation is relevant to your tenant, it appears in the Recommendations section of the Microsoft Entra Identity overview page.
One important Microsoft Entra recommendation is to remove unused credentials from apps (currently in preview), identified as UnusedAppCreds in the Microsoft Graph Recommendations API. This recommendation appears if any application credentials in your tenant haven’t been used for over 30 days. Let’s explore this recommendation further!
Why Removing Unused Credentials Matters?
Applications often use credentials like certificates and secrets to prove their identity. These credentials are essential for accessing resources and services in Microsoft 365. However, unused or outdated credentials pose a significant security risk.
Risks Associated with Unused Credentials:
- Increased Attack Surface – Unused credentials can expand the attack surface of an organization, providing attackers with more entry points. If these credentials fell into the wrong hands, they can be used to gain unauthorized access to sensitive systems.
- Credential Theft and Exploitation – Stale credentials can be harvested through attacks like phishing or brute-force attempts, facilitating a wide range of malicious activities.
- Privilege Escalation – Unused credentials, especially those associated with administrative accounts that have elevated permissions, can be used to escalate and bypass security privileges.
- Neglect of Zero Trust Principles – A key component of the Zero Trust security model is minimizing the attack surface by enforcing the lease privilege. Keeping unused credentials violates this principle, as it gives access where it’s no longer required.
To manage expiring credentials and combat the vulnerabilities, Microsoft advises to Remove unused credentials from applications in Microsoft Entra. Implementing Microsoft Entra recommendations will help the organization increase the Identity Secure Score.
Where to Find ‘Remove Unused Credentials from Applications’ Recommendation?
To locate Microsoft Entra recommendations, follow the steps below:
- Sign in to the Microsoft Entra admin center.
- Navigate to the Overview section and slide to the Recommendations tab.
- Click on the ‘Review unused credentials from applications’ recommendation.
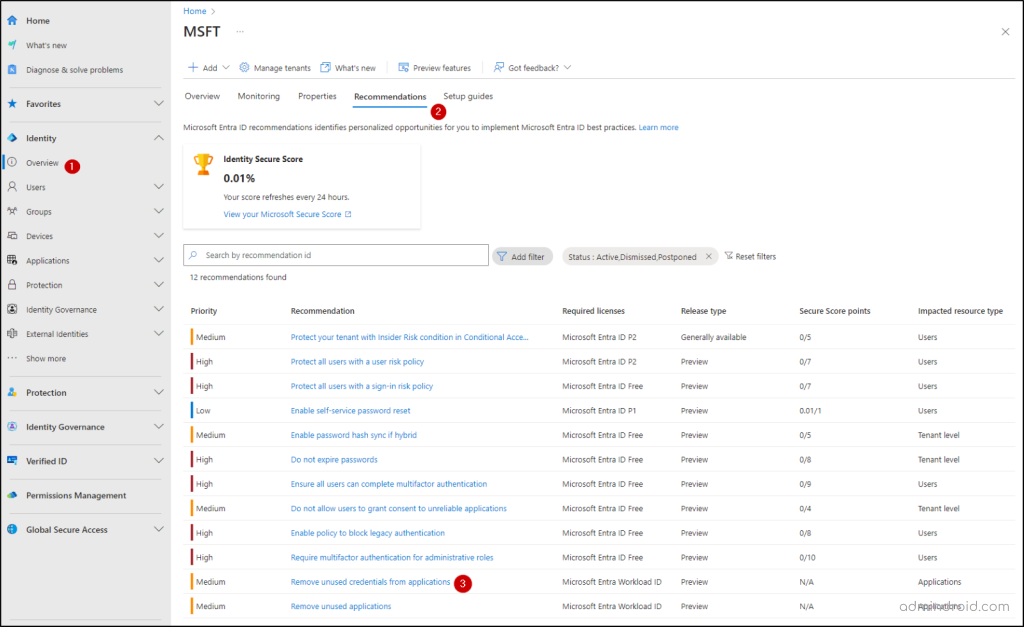
- In the recommendation, you will see a list of applications with unused credentials under the Impacted resources section.
- Click on More details for the relevant entry and take note of the Credential ID and Origin.
Note: It’s important to take note of the credential ID and origin, as you will need this information to proceed with removal.
Key Considerations Before Deleting Unused Credentials in Microsoft Entra
Before removing unused credentials from apps in Microsoft 365, keep the following precautions in mind:
- Backup Credentials: Before deletion, take note of or back up the credentials, especially if they are critical. This can help in case any removal leads to unexpected issues.
- Verify Usage: Ensure that the credentials are truly unused by checking recent activity or usage logs. Removing active credentials may disrupt app functionality.
- Coordinate with Application Owners: Confirm with the app owner or relevant team that the credentials are no longer needed to avoid interrupting app services.
How to Remove Unused Credentials from Apps in Entra?
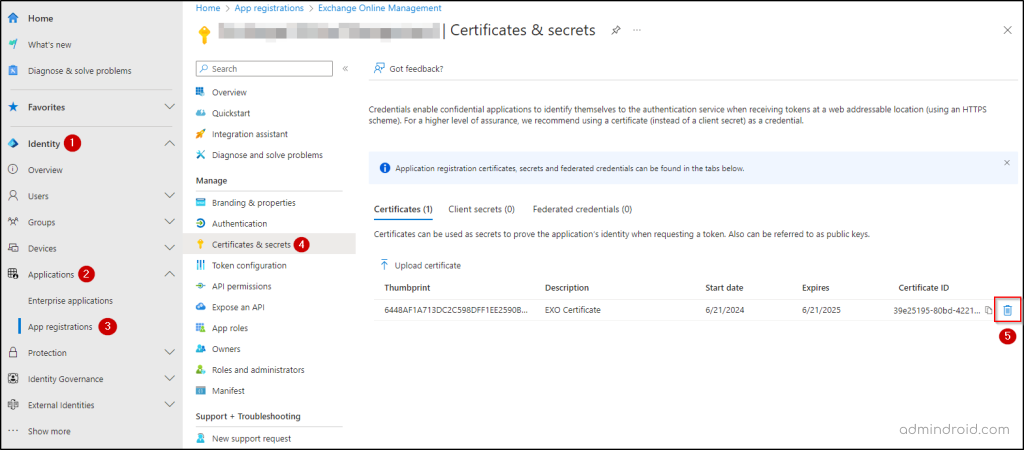
If the origin of the credential is an ‘Application’, follow the below mentioned steps to remove unused credentials from apps in Entra:
- Head to Identity –> Applications –> App registrations in the Microsoft Entra portal.
- There, you will find the application that was flagged in the recommendation.
- Once you have selected the appropriate application, go to the Certificates & Secrets section.
- Identify the unused credentials that have not been used for over 30 days and remove them from the app registration.
Points to Note:
- If the origin of the credential is a ‘Service Principal’, go to Identity –> Applications –> Enterprise applications –> Flagged Application –> Single sign-on –> SAML certificates. Find the unused credentials and remove them.
- If the credential’s origin is marked as ‘A service principal but no SAML certificates are found’, utilize the Microsoft Graph API to query specific properties and remove the credential from the Service Principal. Removing unused applications in Microsoft Entra eliminate the entry points of unauthorized data access, and service disruptions.
By following these steps, you can effectively manage unused and expiring app credentials, thereby improving Microsoft 365 app health and overall security posture!