Over a quarter of the people have been suffocated from password breaching activity in this world filled with threats. Keeping that in mind, Microsoft introduced multi-factor authentication, which is a defense against identity attacks and other security risks💂.
Consequently, users have likely turned to MFA techniques such as SMS💬, voice calls, and Microsoft Authenticator app for two-step verification. Amidst the MFA methods, the Authenticator app emerged as a robust choice for security.
So, focusing on the Authenticator app, Microsoft rolled out upgrades such as location display 🌏 and MFA number matching to keep the app at the forefront of secure methods. Added to the queue, here comes the new update: Microsoft decided to suppress Authenticator notifications from risky sources to avoid risk-based user sign-ins. Also, MS is rolling out this update silently without giving a hint to the users.
Let’s delve into the blog below to get a complete overview of this latest announcement.
Suppressing Authenticator Notifications from Risky Sources
Taking a stride towards enhanced security, Microsoft’s recent update MC675138 has marked a significant milestone. In response to reducing MFA fatigue attacks caused by push notifications, Microsoft has taken a decisive step by putting an end to Authenticator notifications from risky sources.
Once the update is in place, the system will intelligently detect risky sources like unfamiliar IP addresses and locations, effectively distinguishing between malicious attempts and legitimate ones. Furthermore, it will then proceed to suppress authentication requests from risky sources in Microsoft Authenticator.
Note: This update applies to both passwordless (Phone sign-in) approach and MFA notifications to ensure sign-in protection.
But don’t fret – if you authenticate from unfamiliar locations, you won’t be blocked. Instead, your requests will be temporarily suppressed in the Authenticator app. Once you attempt further sign-ins from trusted IPs and locations, you’ll regain the ability to receive Azure MFA push notifications within the app.
When Can You Expect this Change?
This update is currently rolling out and is expected to be finished by the end of September 2023.
Additionally, it’s important to note that this rollout will occur without prior indication of its implementation. You’ll become aware when you attempt to log into your resources from unfamiliar locations, where you may not receive notifications in the Authenticator app.
How Does this Authenticator Notifications Suppression Affect M365 Users?
As said earlier, “termination of Authenticator notifications from risky sources” update will take place silently, users will not be explicitly notified. So, when they don’t receive notifications for their requests in the Authenticator app, they might begin reaching out to administrators, and help desk calls will be in queue.
To avoid this, it’s crucial to proactively educate your users via campaigns about this significant update. By doing so, they can prepare themselves to make login attempts from trusted IPs and familiar locations, preventing unnecessary confusion and inquiries.
Indeed, while this update is a step towards enhancing security, it’s important to acknowledge that there are also some potential drawbacks associated with it. Let’s know that in detail in the topic below.
Cons of Silencing Authenticator Notifications from Risky Sources
Just like a coin with two sides, this update brings forth both advantages and disadvantages. Some of the cons are,
- In a scenario with an organization of more users, there’s a likelihood that at least one out of a thousand users might need to authenticate via Microsoft Authenticator from an unknown location. Remote users fall under this situation. In such cases, this update could indeed prove disruptive, potentially creating a barrier for users trying to work smoothly from remote locations.
- Also, sudden business trips can present situations where immediate access to crucial resources becomes essential. At that time, this update will show its action by turning off the MS authenticator app notifications, as you are from an unknown location and IP.
How will you tackle this feature in such situations? No need to worry! We’ve come up with a few strategies to help you manage situations encountering notification suppression in exceptional cases.
3 Tips to Manage Authenticator Notifications Suppression in M365
Here are three tips for managing Authenticator notifications denials when users face unavoidable sign-ins from unknown IP addresses or locations. It’s crucial to apply these tips wisely; failure to do so could potentially expose you to security risks.
- Configure Conditional Access Policy: Consider a scenario where a user consistently logs in from a remote location and doesn’t receive notifications in the authenticator app because of this update. In this case, you can implement a Conditional Access policy in Microsoft Entra. To achieve this, you can gather the IP addresses from specific users/groups and can create a named location with IP ranges. Subsequently, you can include this named location within the CA policy.
Then, you can make use of the Intune policy results with CA policies, instead of requiring MFA from users as a temporary alternative. This will allow users to access resources from compliant devices alone, as they are unable to receive notifications in Microsoft Authenticator.
Note: This can be used only in case of urgent need, as you need not let them access resources without any security measures.
To configure a CA policy with the above conditions, follow the steps below,
1. At first, navigate to Microsoft Entra admin center 🡢 Protect & secure 🡢 Conditional Access 🡢 Policies 🡢 + New policy.
2. Give a suitable name for your CA Policy and add specific users and cloud apps in the respective blades as per your need.
3. Then, under the ‘Conditions’ blade, select the respected named location under the ‘Locations’ section.
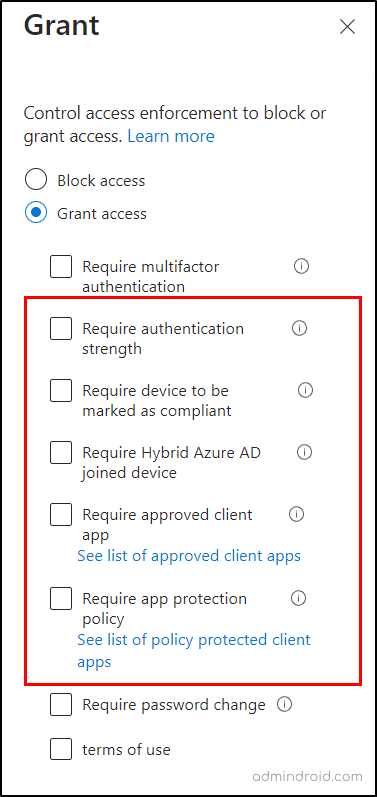
4. Now, move to the ‘Grant’ section, and check in the “Require device to be marked as compliant” check box.
Beyond leveraging compliant status, you can also harness other grant controls like “Require approved apps and app protection” or “Require Hybrid Azure AD joined device” based on your need.
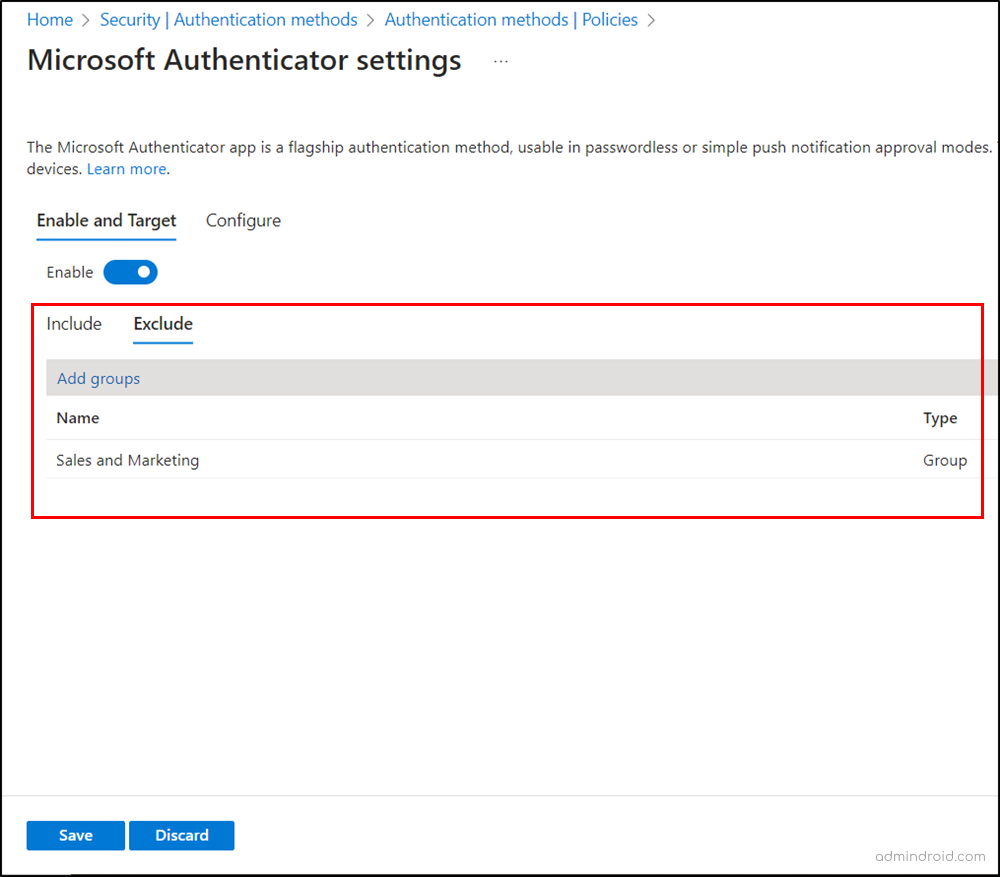
- Disable Microsoft Authenticator: You can temporarily exclude specific groups of users from using Multifactor Authenticator when they face notification suppression in critical situations. To do so, configure the authentication policy by following the navigation below.
Microsoft Entra admin center→ Protection → Authentication methods → Policies → Microsoft Authenticator → Toggle the bar to “Enable” → Exclude → select respective groups →Save
- Use Break Glass Accounts: As an admin, if you encounter notification suppression with the Authenticator app, you can use glass break accounts to access Microsoft 365 in unexceptional situations.
Note: Keep in mind that these break glass accounts must have MFA disabled.
I hope this blog has provided you with comprehensive insights into the recent “suppressing authenticator notification from risky sources” update. Furthermore, feel free to reach us in the comment section for any queries and suggestions.






