Securing user identities is no longer optional. Microsoft has steadily tightened security requirements, and the next milestone is the mandatory enforcement of multi-factor authentication (MFA) for all users. If you manage Microsoft 365 environments, you need to understand the phased rollout timeline and what it means for your organization.
In this post, we’ll walk through the updated time schedule, what’s changing, and how admins can prepare for a smooth transition.
Why MFA Enforcement Matters?
Cyberattacks often succeed because stolen credentials are enough to bypass defenses. Microsoft’s research shows that 99.9% of compromised accounts did not have MFA enabled. By adding an extra verification step, MFA blocks the majority of credential-based attacks even if usernames and passwords are leaked.
Mandatory enforcement also helps organizations to:
- Comply with standards such as PCI DSS, HIPAA, GDPR, and NIST.
- Defend against evolving M365 identity attacks like brute force and MFA fatigue.
Phased Rollout Timeline for MFA Enforcement
As an admin, you might have several questions in mind and that’s completely normal. To address such concerns, Microsoft has shared clarifications and announced a phased rollout plan to set up mandatory MFA. So far, two phases have been confirmed, focusing on enforcing MFA for admin platforms.
Even though these phases apply only to admin platforms, it’s still best to follow Entra ID’s recommendation: ‘Ensuring all users to complete multifactor authentication’.
January 2026 Update: Microsoft 365 Admin Center MFA Enforcement
Microsoft has clarified the enforcement stage for MFA in the Microsoft 365 admin center. Starting February 9, 2026, users will be unable to sign in to the Microsoft 365 admin center unless MFA is successfully completed.
This change represents a shift from gradual enforcement to a mandatory sign-in block. To avoid loss of access, admins should confirm that MFA is fully configured, and users should verify or add their MFA methods in advance.
The following Microsoft 365 admin center URLs are impacted by this change:
- https://portal.office.com/adminportal/home
- https://admin.cloud.microsoft
- https://admin.microsoft.com
Phase 1: Admin Portals
The first stage of enforcement began in October 2024. From that date, any account signing into following portals must complete MFA for any Create, Read, Update, or Delete (CRUD) operation. The rollout is happening gradually across tenants.
- Azure portal
- Microsoft Entra admin center
- Microsoft Intune admin center
Another important addition: From February 2025 onward, MFA enforcement for sign-ins to the Microsoft 365 admin center was planned to roll out gradually.
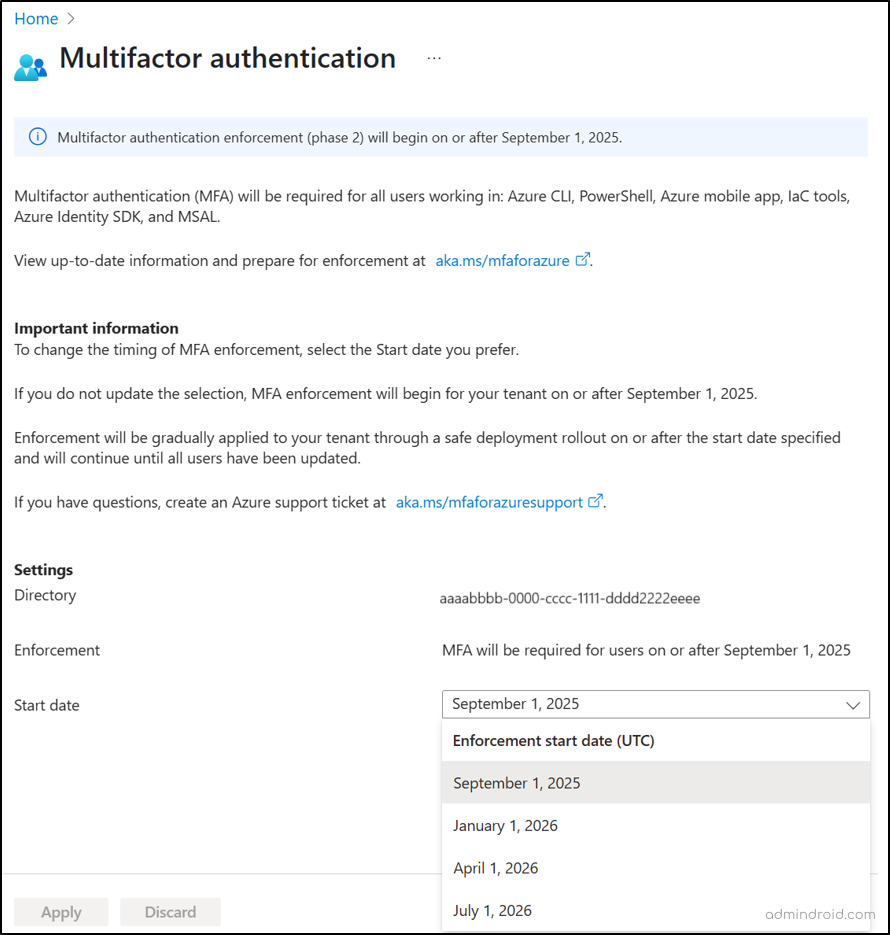
Phase 2: Developer & Automation Tools
Phase 2 kicks by October 1, 2025 (previously early 2025). At this stage, MFA enforcement expands beyond portals to cover:
- Azure CLI
- Azure PowerShell
- Azure mobile app
- Infrastructure as Code (IaC) tools
- REST API endpoints
Here’s the nuance: MFA will be required for Create, Update, or Delete operations, but Read-only operations remain exempt.
For both phased rollouts, MS will notify global admins about the expected enforcement date 60 days prior by email and Azure Service Notifications. The countdown for the enforcement begins only when the global admins receive their first notification from Microsoft as shown below.
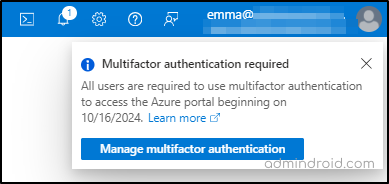
In addition, they will send periodic reminders to global admins between the first notification and the beginning of enforcement for their tenants.
Postpone Mandatory MFA Enforcement
Some organizations may need more time to prepare for this change. Microsoft allows tenants with complex environments or technical barriers to postpone enforcement of Phase 1 and Phase 2.
⚠️ Warning: Postponing increases risk, because accounts with portal access are high-value targets for attackers. It’s strongly recommended to enable MFA now.
Postpone Phase 1 MFA Enforcement
Any global administrator can visit https://aka.ms/managemfaforazure to postpone Phase 1 enforcement. If you haven’t previously signed into the Azure portal with MFA, you’ll be prompted to either complete MFA or postpone enforcement.
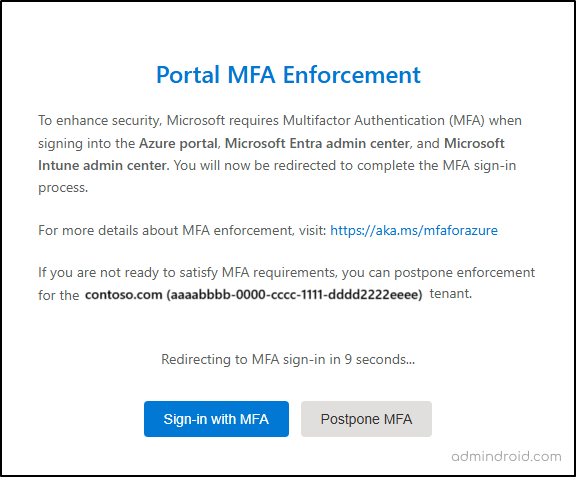
If you select Postpone MFA, the date of MFA enforcement will be one month in the future, or Sept 30, 2025 (UTC), whichever comes first. Then, you can choose Confirm postponement to proceed further.
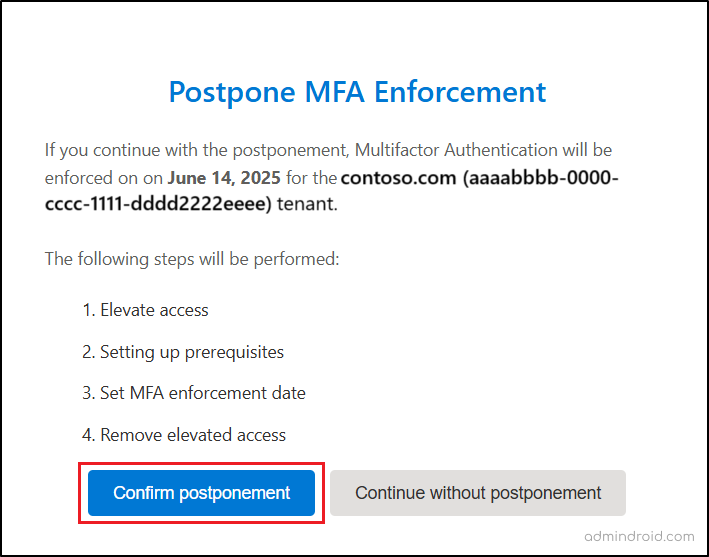
Note: You can revisit the same link to extend the postponed date up to September 30, 2025, if needed.
Postpone Phase 2 MFA Enforcement
You can request more time up to July 1st, 2026, to prepare for Phase 2 MFA enforcement at https://aka.ms/postponePhase2MFA.
Quick Timeline Summary: Microsoft MFA Enforcement Milestones
The table below highlights the key dates and phases of Microsoft’s mandatory MFA enforcement across admin portals and management tools.
| Date | Enforcement Change |
| October 2024 | MFA required for Azure, Microsoft Entra, and Intune admin portals for CRUD operations (Phase 1) |
| February 2025 | MFA enforcement for Microsoft 365 admin center sign-ins begins on a gradual rollout (Phase 1) |
| September 30, 2025 | Maximum postponement deadline for Phase 1 enforcement |
| October 1, 2025 | MFA enforced for Azure CLI, Azure PowerShell, REST APIs, and IaC tools for write operations (Phase 2) |
| February 9, 2026 | Access to the Microsoft 365 admin center without MFA will be blocked |
| July 1, 2026 | Maximum postponement deadline for Phase 2 enforcement |
Identify Azure Users Impacted for MFA Enforcement in Your Tenant
By utilizing the methods below, you can detect who is signing into Azure with and without MFA in your tenant. So, you can also decide to enforce MFA now, before the mandatory MFA enforcement from Microsoft.
- Export a list of users and their authentication methods using the Export-MsIdAzureMfaReport PowerShell command.
- You can use the Multifactor Authentication Gaps workbook in Entra ID.
- You can use the below App IDs in your queries:
- Azure / Entra / Intune portal: c44b4083-3bb0-49c1-b47d-974e53cbdf3c
- Azure CLI: 04b07795-8ddb-461a-bbee-02f9e1bf7b46
- Azure PowerShell: 1950a258-227b-4e31-a9cf-717495945fc2
- Azure mobile app: 0c1307d4-29d6-4389-a11c-5cbe7f65d7fa
Frequently Asked Questions on Mandatory MFA Enforcement
1. Will there be exceptions for service accounts and break-glass accounts?
Service principals, managed identities, workload identities, and similar token-based accounts used for automation are excluded. Break glass accounts (emergency accounts) will also need to be registered with MFA. Microsoft strongly suggests configuring different authentication methods for at least one of the emergency accounts in the organization. As previously said, admins are recommended to update break glass account with certificate-based authentication method or FIDO2.
2. Will students, guest users, and other end users be affected by the new enforcement policy?
Students, guest users, and other end users will only be affected if they are signing into Azure to manage Azure resources. This policy does not apply to apps, websites, or services hosted on Azure.
3. What are the supported MFA methods for authentication?
All supported MFA methods, such as Microsoft Authenticator, FIDO2 security keys, SMS, voice calls, etc., can be used. Also, external MFA solutions can be used to meet MFA requirements which are currently in public preview with external authentication methods.
4. How will the MFA enforcement be implemented?
The MFA requirement will be implemented by Azure and Microsoft Entra Sign-in logs will show it as a source. This will be implemented on top of any access policies configured in the tenant.
For instance, if security defaults are enabled or your tenant is using CA policies in MS Entra, your users will not see any change as the MFA is already required for Azure management. Likewise, if your tenant has any existing strong CA policies configured that require MFA for Azure, such as phishing-resistant MFA, those policies will continue to be enforced, and the users will not see any changes.
5. Will there be any exceptions for tenant-level MFA enforcement?
There will be no opt-out option, but an exception process will be available for cases with no alternative solution. Details about the exception process will be communicated through official notifications.
Despite these assurances, concerns about the enforcement method and the specifics of break glass accounts still linger. Fear not! The Azure team promises to keep you in the loop with additional details and rollout dates. So, let’s stay hopeful that Microsoft will address these concerns and empower customers with the control they need.
6. How to prepare for mandatory MFA enforcement?
To get ready for mandatory MFA, implement a Conditional Access policy that enforces MFA for all users. Previous policy exceptions or exclusions are no longer valid, but policies requiring stronger authentication methods, such as phishing-resistant MFA, remain in effect. Conditional Access requires a Microsoft Entra ID P1 or P2 license; if you don’t have one, you can turn on Security Defaults to enforce MFA across your tenant.
Final Thoughts
This shift reduces the chances of unauthorized access, making multi-factor authentication (MFA) essential for strengthening Microsoft 365 security and protecting sensitive data.
What are your thoughts on this change? Do you think Microsoft will extend these phases to eventually mandate MFA for all Microsoft 365 users across every activity? Share your concerns and perspectives in the comments below.