Have you ever wondered how to better protect🔐 your sensitive files and documents in Microsoft SharePoint and OneDrive? These platforms are essential for collaboration and productivity, but they also require careful security measures to safeguard your valuable content. As the phrase goes, ‘SharePoint is Complex; Permissions are Challenging‘, enforcing strict security configurations in SharePoint Online is vital to protect sensitive data, meet compliance requirements, and prevent unauthorized access. In this blog, we’ll delve into the world of Conditional Access Policies for SharePoint and show you how they can help you secure your sites and OneDrive.
By implementing these policies, you can effectively restrict access to sensitive information, ensuring that only authorized individuals can view and work with your crucial files.
Let’s explore the various ways in which conditional access policies can be configured to fortify your SharePoint Online and OneDrive environments.
What is an Azure AD Conditional Access?
Conditional access policies in Azure AD are like basic if-then statements for controlling access to resources. In simpler terms, they determine what actions users must take in order to access certain Microsoft resources.
License Requirement for Conditional Access Policies
An Azure AD Premium P1 license is required for conditional access policies. Additionally, the ability to create these policies is limited to users who have the role of conditional access administrator, security administrator, or global administrator.
Why Do We Need a Conditional Access Policy?
Let’s say your organization wants to enforce an additional layer of security for accessing SharePoint, especially when employees are accessing it from outside the office network.
- In this scenario, you can set up a conditional access policy that states, “If an employee wants to access SharePoint from outside the office network, they must use multi-factor authentication”.
- With this policy in place, if an employee tries to access SharePoint from a location outside the office network, they will be prompted to provide an extra authentication factor.
Similarly, by integrating conditional access policies with sensitivity labels, authentication contexts, and other such features, organizations can establish highly specific access controls for their sensitive information.
We understand the importance of safeguarding your SharePoint environment, which is why we’ve come up with a collection of robust conditional access policies to take your SharePoint security to the next level!
- Apply granular Conditional Access Policies to SharePoint sites
- Block unmanaged devices from SharePoint and OneDrive
- Conditional Access Policy for external users in SharePoint Online
- Block a specific user’s SharePoint access using Conditional Access Policy
So, are you ready to explore? Then, here we go! 🚀
Apply Granular Conditional Access Policies to SharePoint Sites
Conditional access authentication context functions similarly to applying tags in Microsoft 365, enabling the labeling of critical resources and controlling access to them based on specified conditions.
Authentication context works with conditional access policies to control access to content within a SharePoint site. It allows organizations to achieve granular control over different Microsoft 365 services by protecting data and actions.
Note: To apply an authentication context to a SharePoint site or Labels to a SharePoint site, a Microsoft 365 E5 license is required.
How to Apply Conditional Access Policy to Individual SharePoint Sites?
Applying conditional access policy to a SharePoint site involves three of the following steps.
- Add an authentication context in Azure AD
First, add an authentication context in Azure AD by navigating to the Azure portal -> Azure Active Directory-> Conditional access ->Authentication context.
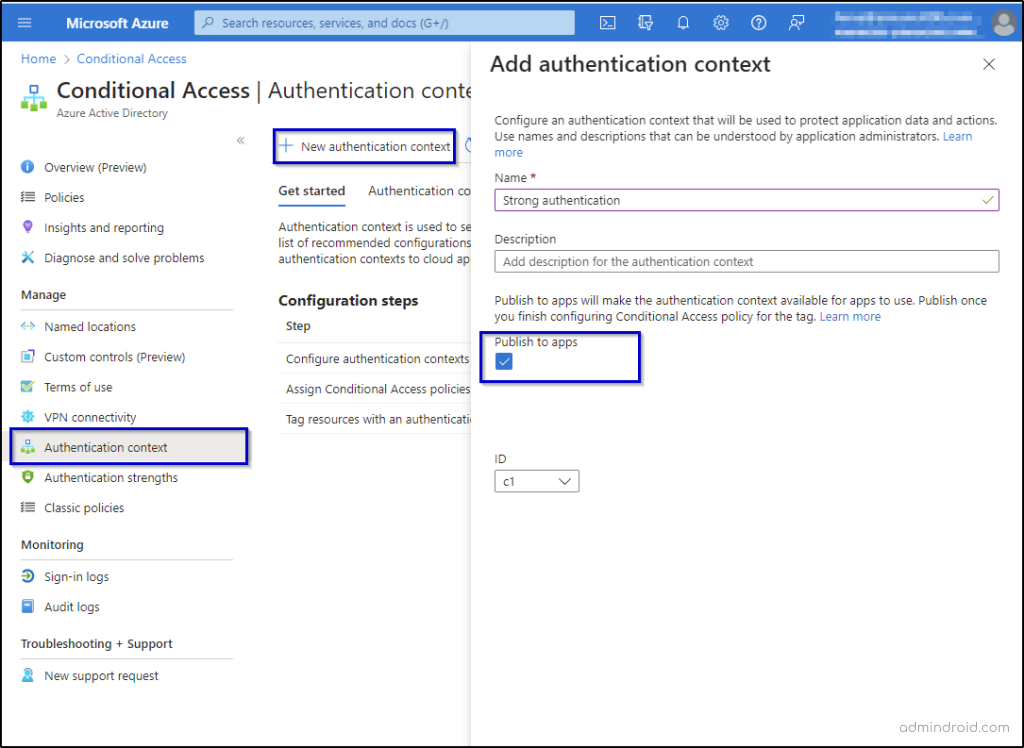
- Apply the Authentication Context to a SharePoint Site.
There are two ways in which you can apply authentication context to a SharePoint site.
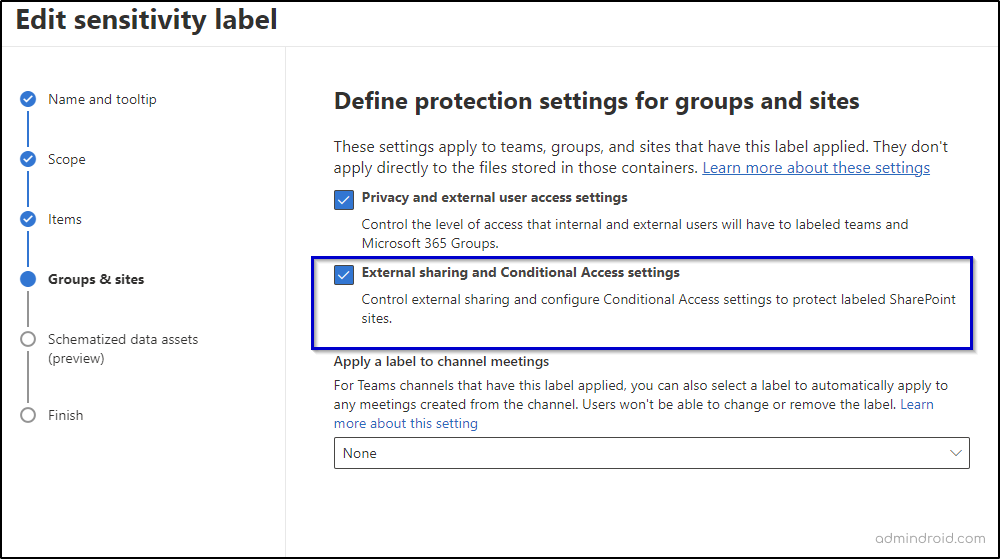
- By creating a sensitivity label with an authentication context and applying the label to the site.
- By adding the authentication context directly to the site.
To create a sensitivity label with an authentication context, navigate to the compliance portal and create or edit a sensitivity label. On the subsequent page of sensitivity label creation, include the authentication context you recently created.
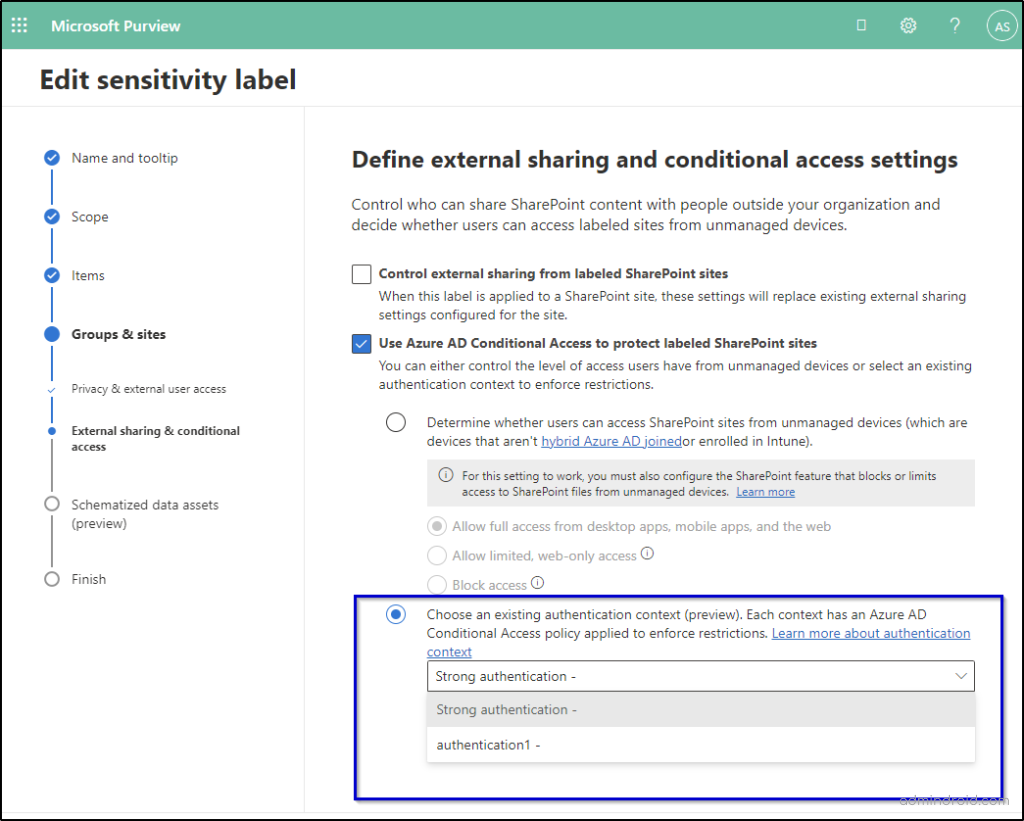
For applying authentication context directly to a SharePoint site, use the following PowerShell cmdlet.
|
1 2 3 4 |
Set-SPOSite -Identity https://*yourdomain*.sharepoint.com/sites/test ` -ConditionalAccessPolicy AuthenticationContext ` -AuthenticationContextName "Strong Authentication" |
- Create a Conditional Access Policy that Applies to the Authentication Context
Now, create a conditional access policy that targets the authentication context and configure necessary conditions and enable the policy.
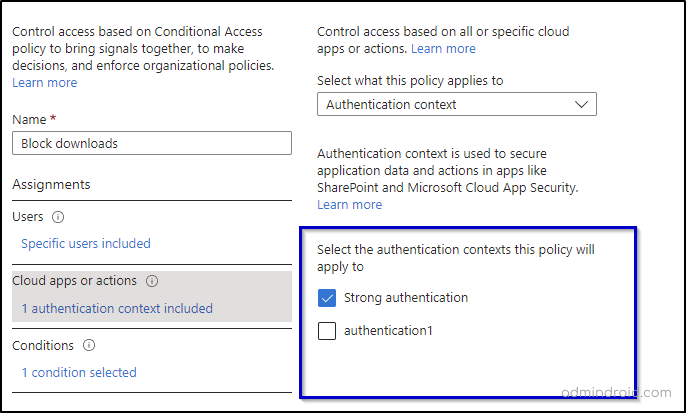
You can also require MFA for specific SharePoint sites using this method by selecting Grant access -> Require multifactor authentication from the ‘Access controls’. After completing the setup and enabling conditional access, the enhanced security measures will be promptly implemented on your SharePoint site.
Using authentication context in conditional access is considered a granular and strong method because it allows organizations to make access control decisions based on multiple factors and conditions, providing a higher level of security and control over user access.
Block Unmanaged Devices from SharePoint and OneDrive
Consider a company that uses SharePoint as its central document repository for sensitive financial information. Employees frequently access SharePoint from both company-issued devices and their personal devices. If an employee accesses SharePoint from their personal device, which lacks proper security measures, it increases the likelihood of unauthorized access.
To enforce restrictions on such devices, you can utilize the device-based conditional access policies in the following way, which will block unmanaged devices from accessing SharePoint and OneDrive. Let’s check how to configure a conditional access policy in Azure AD that restricts access to SharePoint from unmanaged devices below.
- Create a new conditional access policy by navigating to Azure portal ->Azure Active Directory -> Conditional Access -> Policies -> New policy and give a meaningful name to the policy.
- From the ‘Users or workload identities’ section, select users or groups based on your needs.
- Next, navigate to the ‘Cloud apps or actions’ section and choose the ‘Select apps’ option. Locate and select ‘Office 365 SharePoint Online‘ from the available options, then click on ‘Select’.
- Select the Condition as ‘Client apps’ and select ‘mobile apps and desktop clients.
- Choose ‘Grant access’ and check the ‘Require device to be marked as compliant’ and ‘Require Hybrid Azure AD joined device’ options.
- Save the policy.
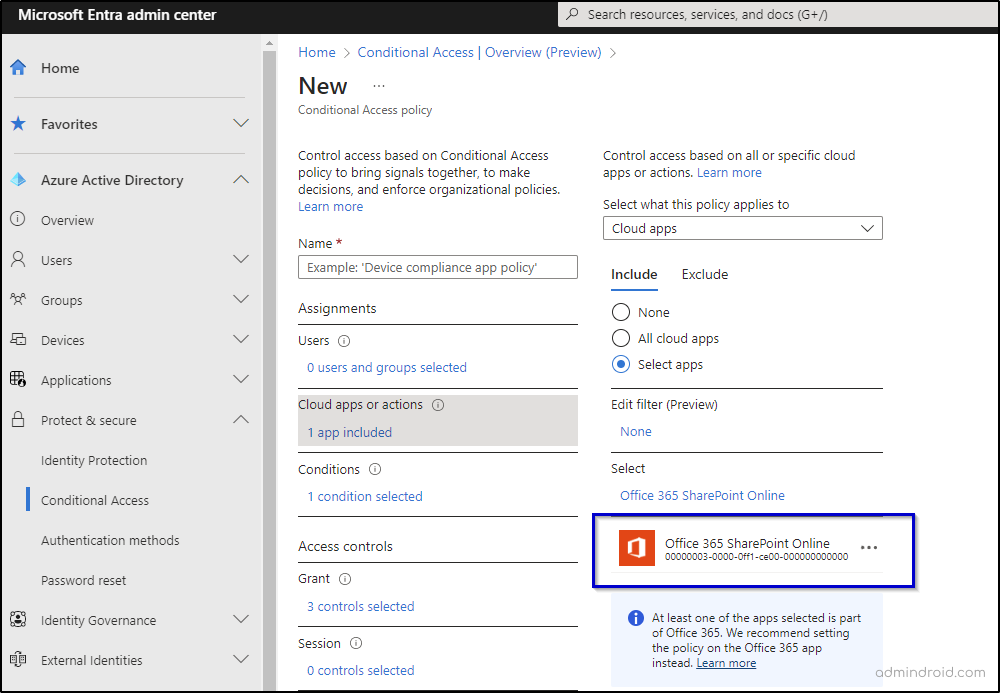
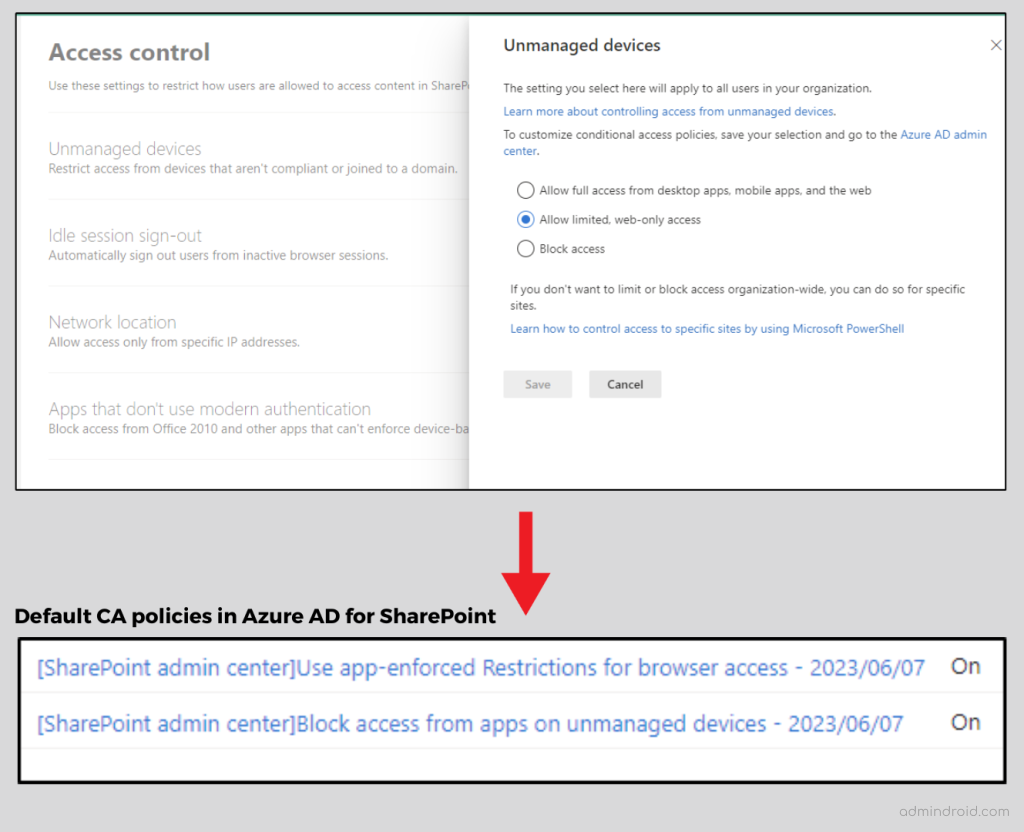
Additionally, if you use the access control settings within the SharePoint admin center to create policies that restrict access from unmanaged devices, Microsoft creates default policies in the Azure AD admin center and enables it right away for you. You can also customize them from the Azure AD admin center, if required.
Note: You can also utilize the predefined conditional access policy templates to quickly create a policy from scratch.
Conditional Access Policy for External Users in SharePoint Online
Integrating Azure Active Directory B2B with SharePoint and OneDrive significantly enhances security by mitigating potential risks associated with external users. In the native SharePoint Online external sharing experience, ad-hoc external users are prompted to create a Microsoft account for authentication without being subjected to any policies. However, with the integration of AAD B2B, a more robust security framework is established, reducing the chances of unmonitored external users causing damage to resources.
To apply conditional access policy to Ad-hoc users,
- Create a new conditional access policy and name it.
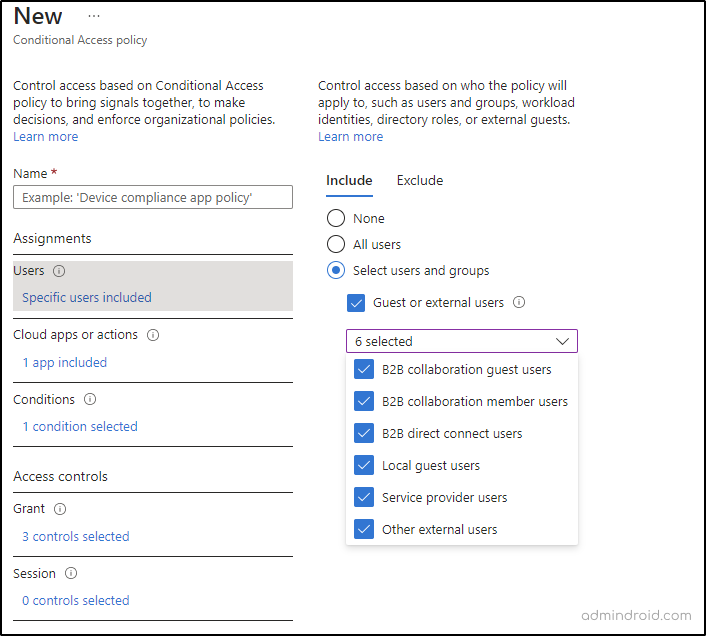
- Under the ‘Assignments’ section, navigate to ‘Users and Groups’. When selecting users for the policy, you will be presented with various external user types for configuring external user settings. Choose the appropriate type of external users from the available options.
✅B2B collaboration member users
✅B2B collaboration guest users
✅B2B direct connect users
✅Local guest users
✅Service provider users
✅Other external users
3. Select one or more options from the above and configure the policy by selecting the necessary conditions and access control.
4. Then, save and turn on the policy.
Thus, the conditional access policy applies to the various types of external users in Microsoft 365 and are subjected to any conditions demanded by CA policies such as MFA before accessing the SharePoint content. In addition to implementing the policy, it is crucial to monitor any changes made to the conditional access policy. This approach helps prevent policy violations.
Block a Specific User’s SharePoint Access Using Conditional Access Policy
There are several reasons why you might need to block access to SharePoint for specific users. Here are a few common scenarios:
Security and Confidentiality: If certain individuals are no longer authorized to access sensitive or confidential information stored in SharePoint, it’s crucial to block their access to protect data.
Departure or Role Change: For employee offboarding or role changes within the company, it’s important to revoke their access to SharePoint to prevent unauthorized access to company resources.
Collaboration Restrictions: SharePoint sites are often used for collaboration among specific teams or departments. If someone is no longer a member of that team or no longer needs access to the site, blocking their access helps maintain the integrity of the collaborative environment and ensures that only relevant people have access to the shared content. Note that blocking access to SharePoint also blocks the user from accessing Teams as a result.
This can be achieved easily by using the Azure AD conditional access policies. Let’s check how!
- Navigate to Azure Portal -> Azure Active Directory -> Conditional access.
- Create a new policy. I have named the policy ‘Block SharePoint Access’.
- Select the specific user you want to block under ‘Select users and groups’.
- Then select ‘cloud apps or actions’ and include ‘Office 365 SharePoint Online’.
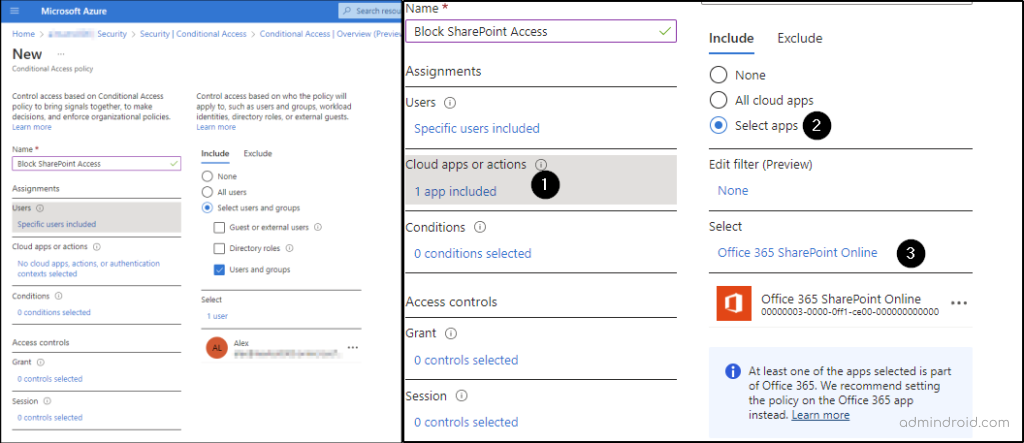
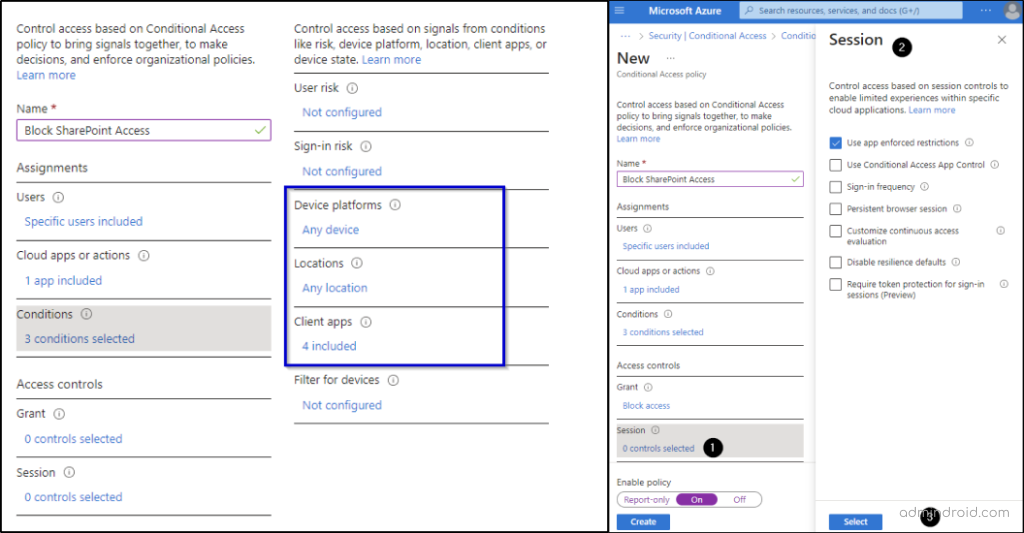
- Now select conditions. Here, I am selecting,
✅’Any device’ for Device platforms
✅‘Any locations’ for locations
✅All client apps
Such that the user won’t get a single reason to access SharePoint.
- Then set Grant to ‘Block access’.
- In the session controls session, set the session to ‘Use app enforced restrictions’.
This control allows organizations to make sure that Azure AD shares information about the device with specific cloud applications. Based on this information, the cloud app can customize the user’s experience, offering either a restricted or complete set of features.
8. Save the policy and turn it on right away.
Thus, the policy blocks the specific user from accessing SharePoint and OneDrive.
Other Conditional Access Policies for SharePoint
Below are a few other conditional access policies that you must know to keep your SharePoint environment secure.
Require MFA for User Access
- Requiring MFA ensures that users must provide an additional form of verification, typically in the form of a second factor, along with their username and password.
- This significantly reduces the risk of unauthorized access, even if user credentials are compromised.
Conditional Access Policies for Blocking Downloads in SharePoint
- Conditional access app control session controls enable admins to control user actions by blocking downloads on unmanaged devices.
- By implementing a conditional access policy to block downloads in SharePoint, organizations can prevent users from downloading sensitive content from specific cloud apps on non-compliant devices.
SharePoint Access Control Policy for Browser-Only Access
- The goal is to allow access to specific SharePoint sites using only a web browser, even from devices that are not managed or controlled by the organization.
- By implementing this control, users will be able to view and interact with the SharePoint sites, but they won’t be able to edit or download any files from those sites
- This control helps organizations maintain security and prevent unauthorized access or data leakage, especially when users are accessing SharePoint sites from personal or unmanaged devices.
Use App Enforced Restrictions in SharePoint
- App enforced restrictions in SharePoint refer to controls and limitations imposed on specific apps or extensions that are used within the SharePoint environment.
- By implementing app enforced restrictions, organizations can prevent unauthorized or potentially harmful apps from accessing, modifying, or deleting data within SharePoint.
By implementing these conditional access policies, you can effectively enhance the security of your SharePoint environment. This blog aims to provide you with comprehensive insights into the various methods of leveraging Azure AD conditional access policies to secure SharePoint and OneDrive.
If you require any additional support or have further queries, please feel free to reach out to us the comments section.